Authorized Economic Operator Security Vetting Items and Validation ...
Authorized Economic Operator Security Vetting Items and Validation ...
Authorized Economic Operator Security Vetting Items and Validation ...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
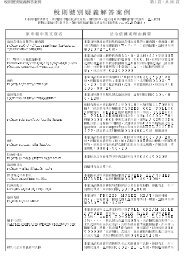
34<br />
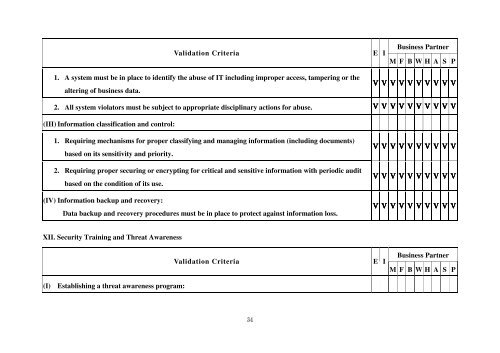
<strong>Validation</strong> Criteria<br />
E I<br />
Business Partner<br />
M F B W H A S P<br />
1. A system must be in place to identify the abuse of IT including improper access, tampering or the<br />
altering of business data.<br />
Ⅴ Ⅴ Ⅴ Ⅴ Ⅴ Ⅴ Ⅴ Ⅴ Ⅴ Ⅴ<br />
2. All system violators must be subject to appropriate disciplinary actions for abuse. Ⅴ Ⅴ Ⅴ Ⅴ Ⅴ Ⅴ Ⅴ Ⅴ Ⅴ Ⅴ<br />
(III) Information classification <strong>and</strong> control:<br />
1. Requiring mechanisms for proper classifying <strong>and</strong> managing information (including documents)<br />
based on its sensitivity <strong>and</strong> priority.<br />
2. Requiring proper securing or encrypting for critical <strong>and</strong> sensitive information with periodic audit<br />
based on the condition of its use.<br />
(IV) Information backup <strong>and</strong> recovery:<br />
Data backup <strong>and</strong> recovery procedures must be in place to protect against information loss.<br />
Ⅴ Ⅴ Ⅴ Ⅴ Ⅴ Ⅴ Ⅴ Ⅴ Ⅴ Ⅴ<br />
Ⅴ Ⅴ Ⅴ Ⅴ Ⅴ Ⅴ Ⅴ Ⅴ Ⅴ Ⅴ<br />
Ⅴ Ⅴ Ⅴ Ⅴ Ⅴ Ⅴ Ⅴ Ⅴ Ⅴ Ⅴ<br />
XII. <strong>Security</strong> Training <strong>and</strong> Threat Awareness<br />
(I) Establishing a threat awareness program:<br />
<strong>Validation</strong> Criteria<br />
E I<br />
Business Partner<br />
M F B W H A S P