Rafal Wojtczuk and Joanna Rutkowska - Black Hat
Rafal Wojtczuk and Joanna Rutkowska - Black Hat
Rafal Wojtczuk and Joanna Rutkowska - Black Hat
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
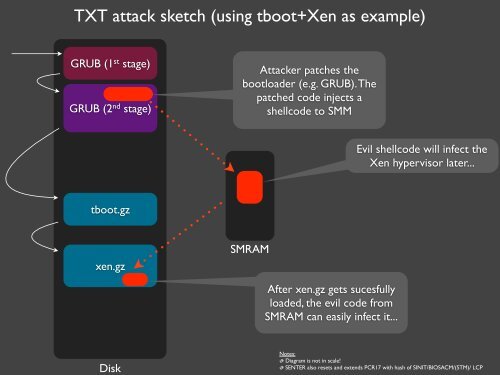
TXT attack sketch (using tboot+Xen as example)<br />
GRUB (1 st stage)<br />
GRUB (2 nd stage)<br />
Attacker patches the<br />
bootloader (e.g. GRUB). The<br />
patched code injects a<br />
shellcode to SMM<br />
Evil shellcode will infect the<br />
Xen hypervisor later...<br />
tboot.gz<br />
xen.gz<br />
SMRAM<br />
After xen.gz gets sucesfully<br />
loaded, the evil code from<br />
SMRAM can easily infect it...<br />
Disk<br />
Notes:<br />
Diagram is not in scale!<br />
SENTER also resets <strong>and</strong> extends PCR17 with hash of SINIT/BIOSACM/(STM)/ LCP