2010/2011 Computer CrIme and SeCurIty Survey - Gatton College ...
2010/2011 Computer CrIme and SeCurIty Survey - Gatton College ...
2010/2011 Computer CrIme and SeCurIty Survey - Gatton College ...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
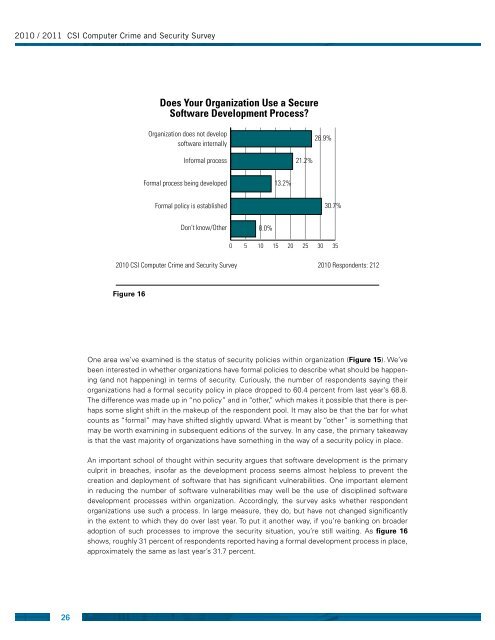
<strong>2010</strong> / <strong>2011</strong> CSI <strong>Computer</strong> Crime <strong>and</strong> Security <strong>Survey</strong>Does Your Organization Use a SecureSoftware Development Process?Organization does not developsoftware internally26.9%Informal process21.2%Formal process being developed13.2%Formal policy is established30.7%Don’t know/Other8.0%0 5 10 15 20 25 30 35<strong>2010</strong> CSI <strong>Computer</strong> Crime <strong>and</strong> Security <strong>Survey</strong> <strong>2010</strong> Respondents: 212Figure 16One area we’ve examined is the status of security policies within organization (Figure 15). We’vebeen interested in whether organizations have formal policies to describe what should be happening(<strong>and</strong> not happening) in terms of security. Curiously, the number of respondents saying theirorganizations had a formal security policy in place dropped to 60.4 percent from last year’s 68.8.The difference was made up in “no policy” <strong>and</strong> in “other,” which makes it possible that there is perhapssome slight shift in the makeup of the respondent pool. It may also be that the bar for whatcounts as “formal” may have shifted slightly upward. What is meant by “other” is something thatmay be worth examining in subsequent editions of the survey. In any case, the primary takeawayis that the vast majority of organizations have something in the way of a security policy in place.An important school of thought within security argues that software development is the primaryculprit in breaches, insofar as the development process seems almost helpless to prevent thecreation <strong>and</strong> deployment of software that has significant vulnerabilities. One important elementin reducing the number of software vulnerabilities may well be the use of disciplined softwaredevelopment processes within organization. Accordingly, the survey asks whether respondentorganizations use such a process. In large measure, they do, but have not changed significantlyin the extent to which they do over last year. To put it another way, if you’re banking on broaderadoption of such processes to improve the security situation, you’re still waiting. As figure 16shows, roughly 31 percent of respondents reported having a formal development process in place,approximately the same as last year’s 31.7 percent.26