2010/2011 Computer CrIme and SeCurIty Survey - Gatton College ...
2010/2011 Computer CrIme and SeCurIty Survey - Gatton College ...
2010/2011 Computer CrIme and SeCurIty Survey - Gatton College ...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
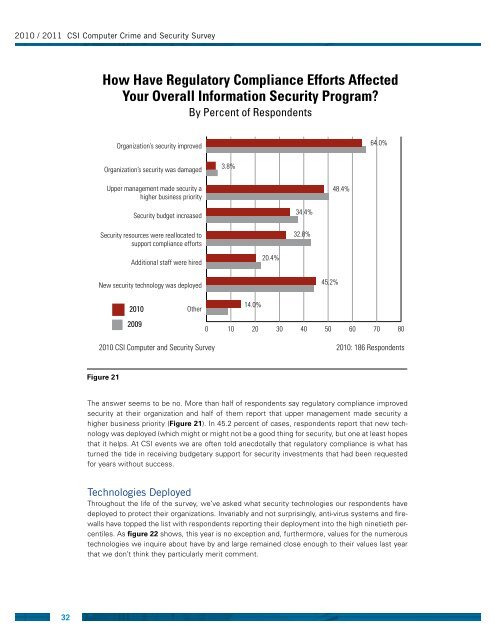
<strong>2010</strong> / <strong>2011</strong> CSI <strong>Computer</strong> Crime <strong>and</strong> Security <strong>Survey</strong>How Have Regulatory Compliance Efforts AffectedYour Overall Information Security Program?By Percent of RespondentsOrganization’s security improved64.0%Organization’s security was damaged3.8%Upper management made security ahigher business priority48.4%Security budget increasedSecurity resources were reallocated tosupport compliance efforts34.4%32.8%Additional staff were hired20.4%New security technology was deployed45.2%<strong>2010</strong>2009Other14.0%0 10 20 30 40 50 60 70 80<strong>2010</strong> CSI <strong>Computer</strong> <strong>and</strong> Security <strong>Survey</strong> <strong>2010</strong>: 186 RespondentsFigure 21The answer seems to be no. More than half of respondents say regulatory compliance improvedsecurity at their organization <strong>and</strong> half of them report that upper management made security ahigher business priority (Figure 21). In 45.2 percent of cases, respondents report that new technologywas deployed (which might or might not be a good thing for security, but one at least hopesthat it helps. At CSI events we are often told anecdotally that regulatory compliance is what hasturned the tide in receiving budgetary support for security investments that had been requestedfor years without success.Technologies DeployedThroughout the life of the survey, we’ve asked what security technologies our respondents havedeployed to protect their organizations. Invariably <strong>and</strong> not surprisingly, anti-virus systems <strong>and</strong> firewallshave topped the list with respondents reporting their deployment into the high ninetieth percentiles.As figure 22 shows, this year is no exception <strong>and</strong>, furthermore, values for the numeroustechnologies we inquire about have by <strong>and</strong> large remained close enough to their values last yearthat we don’t think they particularly merit comment.32