Information security awareness initiatives: Current practice and the ...
Information security awareness initiatives: Current practice and the ...
Information security awareness initiatives: Current practice and the ...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
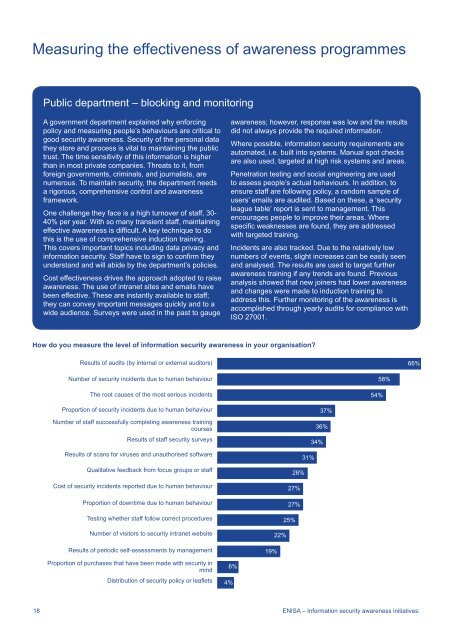
Measuring <strong>the</strong> effectiveness of <strong>awareness</strong> programmesPublic department – blocking <strong>and</strong> monitoringA government department explained why enforcingpolicy <strong>and</strong> measuring people’s behaviours are critical togood <strong>security</strong> <strong>awareness</strong>. Security of <strong>the</strong> personal data<strong>the</strong>y store <strong>and</strong> process is vital to maintaining <strong>the</strong> publictrust. The time sensitivity of this information is higherthan in most private companies. Threats to it, fromforeign governments, criminals, <strong>and</strong> journalists, arenumerous. To maintain <strong>security</strong>, <strong>the</strong> department needsa rigorous, comprehensive control <strong>and</strong> <strong>awareness</strong>framework.One challenge <strong>the</strong>y face is a high turnover of staff, 30-40% per year. With so many transient staff, maintainingeffective <strong>awareness</strong> is difficult. A key technique to dothis is <strong>the</strong> use of comprehensive induction training.This covers important topics including data privacy <strong>and</strong>information <strong>security</strong>. Staff have to sign to confirm <strong>the</strong>yunderst<strong>and</strong> <strong>and</strong> will abide by <strong>the</strong> department’s policies.Cost effectiveness drives <strong>the</strong> approach adopted to raise<strong>awareness</strong>. The use of intranet sites <strong>and</strong> emails havebeen effective. These are instantly available to staff;<strong>the</strong>y can convey important messages quickly <strong>and</strong> to awide audience. Surveys were used in <strong>the</strong> past to gauge<strong>awareness</strong>; however, response was low <strong>and</strong> <strong>the</strong> resultsdid not always provide <strong>the</strong> required information.Where possible, information <strong>security</strong> requirements areautomated, i.e. built into systems. Manual spot checksare also used, targeted at high risk systems <strong>and</strong> areas.Penetration testing <strong>and</strong> social engineering are usedto assess people’s actual behaviours. In addition, toensure staff are following policy, a r<strong>and</strong>om sample ofusers’ emails are audited. Based on <strong>the</strong>se, a ‘<strong>security</strong>league table’ report is sent to management. Thisencourages people to improve <strong>the</strong>ir areas. Wherespecific weaknesses are found, <strong>the</strong>y are addressedwith targeted training.Incidents are also tracked. Due to <strong>the</strong> relatively lownumbers of events, slight increases can be easily seen<strong>and</strong> analysed. The results are used to target fur<strong>the</strong>r<strong>awareness</strong> training if any trends are found. Previousanalysis showed that new joiners had lower <strong>awareness</strong><strong>and</strong> changes were made to induction training toaddress this. Fur<strong>the</strong>r monitoring of <strong>the</strong> <strong>awareness</strong> isaccomplished through yearly audits for compliance withISO 27001.How do you measure <strong>the</strong> level of information <strong>security</strong> <strong>awareness</strong> in your organisation?Results of audits (by internal or external auditors)66%Number of <strong>security</strong> incidents due to human behaviourThe root causes of <strong>the</strong> most serious incidents54%58%Proportion of <strong>security</strong> incidents due to human behaviourNumber of staff successfully completing <strong>awareness</strong> trainingcoursesResults of staff <strong>security</strong> surveysResults of scans for viruses <strong>and</strong> unauthorised softwareQualitative feedback from focus groups or staffCost of <strong>security</strong> incidents reported due to human behaviourProportion of downtime due to human behaviourTesting whe<strong>the</strong>r staff follow correct proceduresNumber of visitors to <strong>security</strong> intranet websiteResults of periodic self-assessments by managementProportion of purchases that have been made with <strong>security</strong> inmindDistribution of <strong>security</strong> policy or leaflets6%4%37%36%34%31%28%27%27%25%22%19%18 ENISA – <strong>Information</strong> <strong>security</strong> <strong>awareness</strong> <strong>initiatives</strong>: