How Imperva SecureSphere Helps Address TRM Guidelines for ...
How Imperva SecureSphere Helps Address TRM Guidelines for ...
How Imperva SecureSphere Helps Address TRM Guidelines for ...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
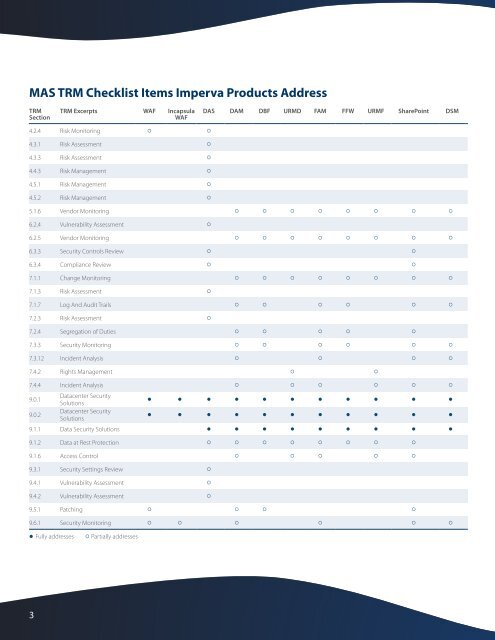
MAS <strong>TRM</strong> Checklist Items <strong>Imperva</strong> Products <strong>Address</strong><strong>TRM</strong>Section<strong>TRM</strong> Excerpts WAF IncapsulaWAFDAS DAM DBF URMD FAM FFW URMF SharePoint DSM4.2.4 Risk Monitoring ◦ ◦4.3.1 Risk Assessment ◦4.3.3 Risk Assessment ◦4.4.3 Risk Management ◦4.5.1 Risk Management ◦4.5.2 Risk Management ◦5.1.6 Vendor Monitoring ◦ ◦ ◦ ◦ ◦ ◦ ◦ ◦6.2.4 Vulnerability Assessment ◦6.2.5 Vendor Monitoring ◦ ◦ ◦ ◦ ◦ ◦ ◦ ◦6.3.3 Security Controls Review ◦ ◦6.3.4 Compliance Review ◦ ◦7.1.1 Change Monitoring ◦ ◦ ◦ ◦ ◦ ◦ ◦ ◦7.1.3 Risk Assessment ◦7.1.7 Log And Audit Trails ◦ ◦ ◦ ◦ ◦ ◦7.2.3 Risk Assessment ◦7.2.4 Segregation of Duties ◦ ◦ ◦ ◦ ◦7.3.3 Security Monitoring ◦ ◦ ◦ ◦ ◦ ◦7.3.12 Incident Analysis ◦ ◦ ◦ ◦7.4.2 Rights Management ◦ ◦7.4.4 Incident Analysis ◦ ◦ ◦ ◦ ◦ ◦9.0.1Datacenter SecuritySolutions• • • • • • • • • • •9.0.2Datacenter SecuritySolutions• • • • • • • • • • •9.1.1 Data Security Solutions • • • • • • • • •9.1.2 Data at Rest Protection ◦ ◦ ◦ ◦ ◦ ◦ ◦ ◦9.1.6 Access Control ◦ ◦ ◦ ◦ ◦9.3.1 Security Settings Review ◦9.4.1 Vulnerability Assessment ◦9.4.2 Vulnerability Assessment ◦9.5.1 Patching ◦ ◦ ◦ ◦9.6.1 Security Monitoring ◦ ◦ ◦ ◦ ◦ ◦• Fully addresses ◦ Partially addresses3