Bypassing NAC v2.0 - OSSIR
Bypassing NAC v2.0 - OSSIR
Bypassing NAC v2.0 - OSSIR
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
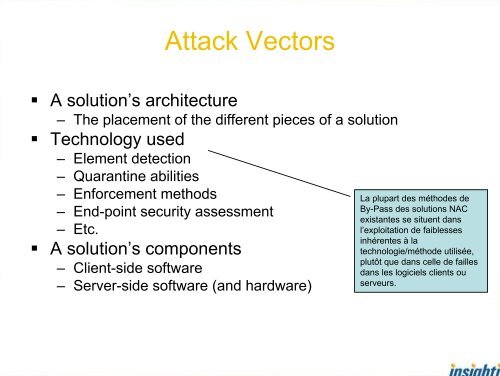
Attack Vectors• A solution’s architecture– The placement of the different pieces of a solution• Technology used– Element detection– Quarantine abilities– Enforcement methods– End-point security assessment– Etc.• A solution’s components– Client-side software– Server-side software (and hardware)La plupart des méthodes deBy-Pass des solutions <strong>NAC</strong>existantes se situent dansl’exploitation de faiblessesinhérentes à latechnologie/méthode utilisée,plutôt que dans celle de faillesdans les logiciels clients ouserveurs.