Volume 1 - Issue 8 - ICTACT.IN
Volume 1 - Issue 8 - ICTACT.IN
Volume 1 - Issue 8 - ICTACT.IN
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
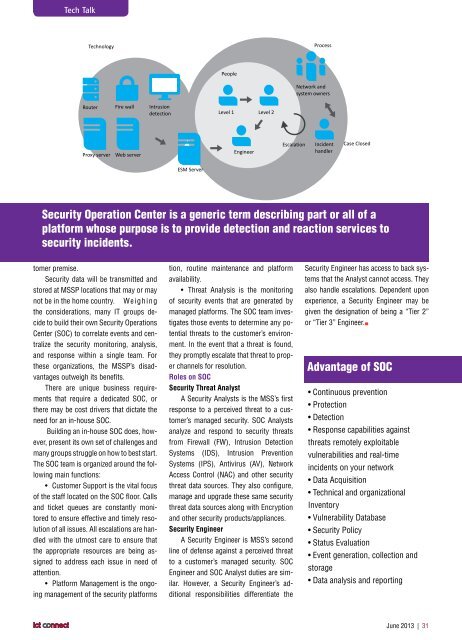
Tech TalkSecurity Operation Center is a generic term describing part or all of aplatform whose purpose is to provide detection and reaction services tosecurity incidents.• Store security data only at the customerpremise.Security data will be transmitted andstored at MSSP locations that may or maynot be in the home country. Weighingthe considerations, many IT groups decideto build their own Security OperationsCenter (SOC) to correlate events and centralizethe security monitoring, analysis,and response within a single team. Forthese organizations, the MSSP’s disadvantagesoutweigh its benefits.There are unique business requirementsthat require a dedicated SOC, orthere may be cost drivers that dictate theneed for an in-house SOC.Building an in-house SOC does, however,present its own set of challenges andmany groups struggle on how to best start.The SOC team is organized around the followingmain functions:• Customer Support is the vital focusof the staff located on the SOC floor. Callsand ticket queues are constantly monitoredto ensure effective and timely resolutionof all issues. All escalations are handledwith the utmost care to ensure thatthe appropriate resources are being assignedto address each issue in need ofattention.• Platform Management is the ongoingmanagement of the security platformsincluding platform and policy configuration,routine maintenance and platformavailability.• Threat Analysis is the monitoringof security events that are generated bymanaged platforms. The SOC team investigatesthose events to determine any potentialthreats to the customer’s environment.In the event that a threat is found,they promptly escalate that threat to properchannels for resolution.Roles on SOCSecurity Threat AnalystA Security Analysts is the MSS’s firstresponse to a perceived threat to a customer’smanaged security. SOC Analystsanalyze and respond to security threatsfrom Firewall (FW), Intrusion DetectionSystems (IDS), Intrusion PreventionSystems (IPS), Antivirus (AV), NetworkAccess Control (NAC) and other securitythreat data sources. They also configure,manage and upgrade these same securitythreat data sources along with Encryptionand other security products/appliances.Security EngineerA Security Engineer is MSS’s secondline of defense against a perceived threatto a customer’s managed security. SOCEngineer and SOC Analyst duties are similar.However, a Security Engineer’s additionalresponsibilities differentiate thetwo positions slightly. For example, a SOCSecurity Engineer has access to back systemsthat the Analyst cannot access. Theyalso handle escalations. Dependent uponexperience, a Security Engineer may begiven the designation of being a “Tier 2”or “Tier 3” Engineer.Advantage of SOC• Continuous prevention• Protection• Detection• Response capabilities againstthreats remotely exploitablevulnerabilities and real-timeincidents on your network• Data Acquisition• Technical and organizationalInventory• Vulnerability Database• Security Policy• Status Evaluation• Event generation, collection andstorage• Data analysis and reportingJune 2013 | 31