Image Stegnography by Skin Tone Detection - International Journal ...
Image Stegnography by Skin Tone Detection - International Journal ...
Image Stegnography by Skin Tone Detection - International Journal ...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
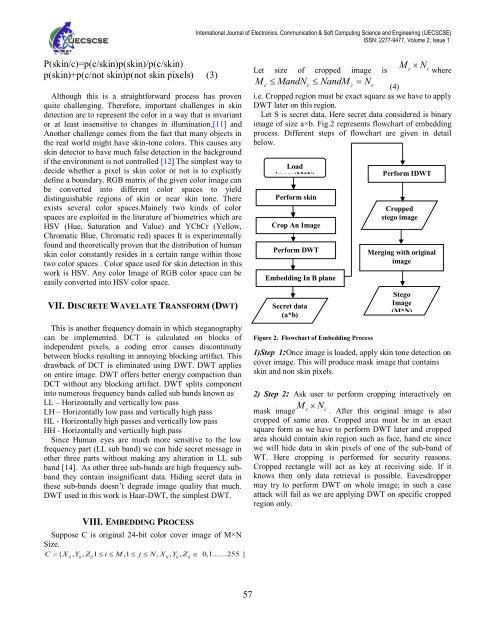
<strong>International</strong> <strong>Journal</strong> of Electronics, Communication & Soft Computing Science and Engineering (IJECSCSE)ISSN: 2277-9477, Volume 2, Issue 1P(skin/c)=p(c/skin)p(skin)/p(c/skin)p(skin)+p(c/not skin)p(not skin pixels) (3)Although this is a straightforward process has provenquite challenging. Therefore, important challenges in skindetection are to represent the color in a way that is invariantor at least insensitive to changes in illumination.[11] andAnother challenge comes from the fact that many objects inthe real world might have skin-tone colors. This causes anyskin detector to have much false detection in the backgroundif the environment is not controlled [12] The simplest way todecide whether a pixel is skin color or not is to explicitlydefine a boundary. RGB matrix of the given color image canbe converted into different color spaces to yielddistinguishable regions of skin or near skin tone. Thereexists several color spaces.Mainely two kinds of colorspaces are exploited in the literature of biometrics which areHSV (Hue, Saturation and Value) and YCbCr (Yellow,Chromatic Blue, Chromatic red) spaces It is experimentallyfound and theoretically proven that the distribution of humanskin color constantly resides in a certain range within thosetwo color spaces . Color space used for skin detection in thiswork is HSV. Any color <strong>Image</strong> of RGB color space can beeasily converted into HSV color space.VII. DISCRETE WAVELATE TRANSFORM (DWT)This is another frequency domain in which steganographycan be implemented. DCT is calculated on blocks ofindependent pixels, a coding error causes discontinuitybetween blocks resulting in annoying blocking artifact. Thisdrawback of DCT is eliminated using DWT. DWT applieson entire image. DWT offers better energy compaction thanDCT without any blocking artifact. DWT splits componentinto numerous frequency bands called sub bands known asLL – Horizontally and vertically low passLH – Horizontally low pass and vertically high passHL - Horizontally high passes and vertically low passHH - Horizontally and vertically high passSince Human eyes are much more sensitive to the lowfrequency part (LL sub band) we can hide secret message inother three parts without making any alteration in LL subband [14]. As other three sub-bands are high frequency subbandthey contain insignificant data. Hiding secret data inthese sub-bands doesn‟t degrade image quality that much.DWT used in this work is Haar-DWT, the simplest DWT.MLet size of cropped image iscNcwhereM MandN NandM Nc c c c(4)i.e. Cropped region must be exact square as we have to applyDWT later on this region.Let S is secret data. Here secret data considered is binaryimage of size a×b. Fig.2 represents flowchart of embeddingprocess. Different steps of flowchart are given in detailbelow.Loadimage(M*N)Perform skindetectionCrop An <strong>Image</strong>(Mc*Nc)Perform DWTEmbedding In B planeSecret data(a*b)Figure 2. Flowchart of Embedding ProcessPerform IDWTCroppedstego imageMerging with originalimageStego<strong>Image</strong>(M*N)1)Step 1:Once image is loaded, apply skin tone detection oncover image. This will produce mask image that containsskin and non skin pixels.2) Step 2: Ask user to perform cropping interactively onMmask imagecNc . After this original image is alsocropped of same area. Cropped area must be in an exactsquare form as we have to perform DWT later and croppedarea should contain skin region such as face, hand etc sincewe will hide data in skin pixels of one of the sub-band ofWT. Here cropping is performed for security reasons.Cropped rectangle will act as key at receiving side. If itknows then only data retrieval is possible. Eavesdroppermay try to perform DWT on whole image; in such a caseattack will fail as we are applying DWT on specific croppedregion only.VIII. EMBEDDING PROCESSSuppose C is original 24-bit color cover image of M×NSize.C { Xij, Yij , Zij1 i M ,1 j N, Xij, Yij , Zij0,1.......255 }57