Enabling Enterprise Resilience through Security Automation ...
Enabling Enterprise Resilience through Security Automation ...
Enabling Enterprise Resilience through Security Automation ...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
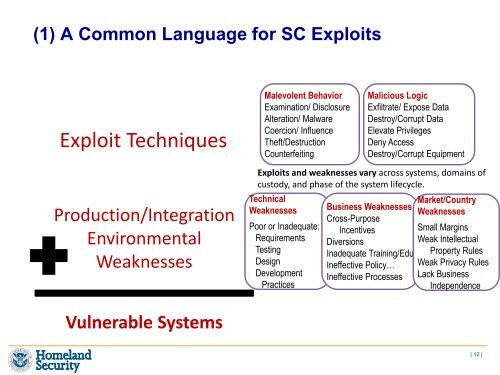
(1) A Common Language for SC ExploitsExploit TechniquesMalevolent BehaviorExamination/ DisclosureAlteration/ MalwareCoercion/ InfluenceTheft/DestructionCounterfeitingMalicious LogicExfiltrate/ Expose DataDestroy/Corrupt DataElevate PrivilegesDeny AccessDestroy/Corrupt EquipmentProduction/IntegrationEnvironmentalWeaknessesExploits and weaknesses vary across systems, domains ofcustody, and phase of the system lifecycle.TechnicalWeaknessesPoor or Inadequate:RequirementsTestingDesignDevelopmentPracticesBusiness WeaknessesCross-PurposeIncentivesDiversionsInadequate Training/EduIneffective Policy…Ineffective ProcessesMarket/CountryWeaknessesSmall MarginsWeak IntellectualProperty RulesWeak Privacy RulesLack BusinessIndependenceVulnerable Systems| 12 |