Information and Security
Information and Security
Information and Security
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
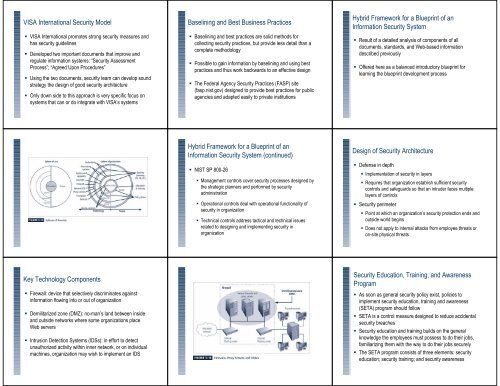
VISA International <strong>Security</strong> Model VISA International promotes strong security measures <strong>and</strong>has security guidelines Developed two important documents that improve <strong>and</strong>regulate information systems: “<strong>Security</strong> AssessmentProcess”; “Agreed Upon Procedures” Using the two documents, security team can develop soundstrategy the design of good security architecture Only down side to this approach is very specific focus onsystems that can or do integrate with VISA’s systemsBaselining <strong>and</strong> Best Business Practices Baselining <strong>and</strong> best practices are solid methods forcollecting security practices, but provide less detail than acomplete methodology Possible to gain information by baselining <strong>and</strong> using bestpractices <strong>and</strong> thus work backwards to an effective design The Federal Agency <strong>Security</strong> Practices (FASP) site(fasp.nist.gov) designed to provide best practices for publicagencies <strong>and</strong> adapted easily to private institutionsHybrid Framework for a Blueprint of an<strong>Information</strong> <strong>Security</strong> System Result of a detailed analysis of components of alldocuments, st<strong>and</strong>ards, <strong>and</strong> Web-based informationdescribed previously Offered here as a balanced introductory blueprint forlearning the blueprint development processFigure 5-15 – Spheres of <strong>Security</strong>Hybrid Framework for a Blueprint of an<strong>Information</strong> <strong>Security</strong> System (continued) NIST SP 800-26 Management controls cover security processes designed bythe strategic planners <strong>and</strong> performed by securityadministration Operational controls deal with operational functionality ofsecurity in organization Technical controls address tactical <strong>and</strong> technical issuesrelated to designing <strong>and</strong> implementing security inorganizationDesign of <strong>Security</strong> Architecture Defense in depth Implementation of security in layers Requires that organization establish sufficient securitycontrols <strong>and</strong> safeguards so that an intruder faces multiplelayers of controls <strong>Security</strong> perimeter Point at which an organization’s security protection ends <strong>and</strong>outside world begins Does not apply to internal attacks from employee threats oron-site physical threatsKey Technology Components Firewall: device that selectively discriminates againstinformation flowing into or out of organization Demilitarized zone (DMZ): no-man’s l<strong>and</strong> between inside<strong>and</strong> outside networks where some organizations placeWeb servers Intrusion Detection Systems (IDSs): in effort to detectunauthorized activity within inner network, or on individualmachines, organization may wish to implement an IDSFigure 5-18 – Key Components<strong>Security</strong> Education, Training, <strong>and</strong> AwarenessProgram As soon as general security policy exist, policies toimplement security education, training <strong>and</strong> awareness(SETA) program should follow SETA is a control measure designed to reduce accidentalsecurity breaches <strong>Security</strong> education <strong>and</strong> training builds on the generalknowledge the employees must possess to do their jobs,familiarizing them with the way to do their jobs securely The SETA program consists of three elements: securityeducation; security training; <strong>and</strong> security awareness