IT Risk Advisory Brochure_V1 0.pdf - Riskpro
IT Risk Advisory Brochure_V1 0.pdf - Riskpro
IT Risk Advisory Brochure_V1 0.pdf - Riskpro
- No tags were found...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
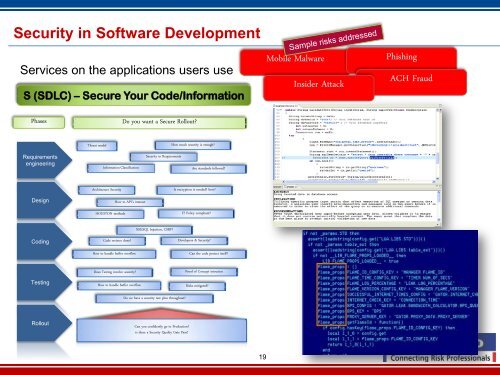
Security in Software DevelopmentServices on the applications users useS (SDLC) – Secure Your Code/InformationMobile MalwareInsider AttackPhishingACH FraudPhasesDo you want a Secure Rollout?Threat modelHow much security is enough?RequirementsengineeringInformation ClassificationSecurity in RequirementsAre standards followed?Architecture SecurityIs encryption is needed? how?DesignHow to API’s interactHOUSTON methods<strong>IT</strong> Policy compliant?XSS,SQL Injection, CSRF?CodingCode reviews done?How to handle buffer overflowDevelopers & Security?Can the code protect itself?TestingDoes Testing involve security?How to handle buffer overflowProof of Concept intrusion<strong>Risk</strong>s mitigated?Do we have a security test plan throughout?RolloutCan you confidently go to Production?is there a Security Quality Gate Pass?19