Best Practices For Department Server and Enterprise System ...
Best Practices For Department Server and Enterprise System ...
Best Practices For Department Server and Enterprise System ...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
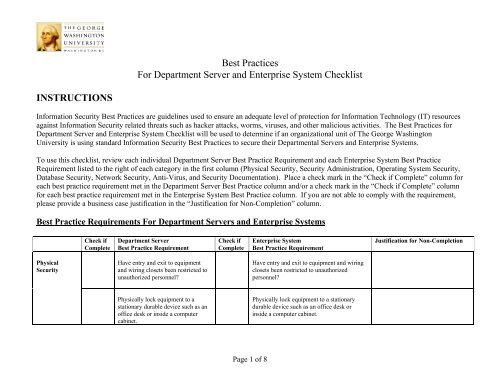
<strong>Best</strong> <strong>Practices</strong><strong>For</strong> <strong>Department</strong> <strong>Server</strong> <strong>and</strong> <strong>Enterprise</strong> <strong>System</strong> ChecklistINSTRUCTIONSInformation Security <strong>Best</strong> <strong>Practices</strong> are guidelines used to ensure an adequate level of protection for Information Technology (IT) resourcesagainst Information Security related threats such as hacker attacks, worms, viruses, <strong>and</strong> other malicious activities. The <strong>Best</strong> <strong>Practices</strong> for<strong>Department</strong> <strong>Server</strong> <strong>and</strong> <strong>Enterprise</strong> <strong>System</strong> Checklist will be used to determine if an organizational unit of The George WashingtonUniversity is using st<strong>and</strong>ard Information Security <strong>Best</strong> <strong>Practices</strong> to secure their <strong>Department</strong>al <strong>Server</strong>s <strong>and</strong> <strong>Enterprise</strong> <strong>System</strong>s.To use this checklist, review each individual <strong>Department</strong> <strong>Server</strong> <strong>Best</strong> Practice Requirement <strong>and</strong> each <strong>Enterprise</strong> <strong>System</strong> <strong>Best</strong> PracticeRequirement listed to the right of each category in the first column (Physical Security, Security Administration, Operating <strong>System</strong> Security,Database Security, Network Security, Anti-Virus, <strong>and</strong> Security Documentation). Place a check mark in the “Check if Complete” column foreach best practice requirement met in the <strong>Department</strong> <strong>Server</strong> <strong>Best</strong> Practice column <strong>and</strong>/or a check mark in the “Check if Complete” columnfor each best practice requirement met in the <strong>Enterprise</strong> <strong>System</strong> <strong>Best</strong> Practice column. If you are not able to comply with the requirement,please provide a business case justification in the “Justification for Non-Completion” column.<strong>Best</strong> Practice Requirements <strong>For</strong> <strong>Department</strong> <strong>Server</strong>s <strong>and</strong> <strong>Enterprise</strong> <strong>System</strong>sCheck ifComplete<strong>Department</strong> <strong>Server</strong><strong>Best</strong> Practice RequirementCheck ifComplete<strong>Enterprise</strong> <strong>System</strong><strong>Best</strong> Practice RequirementJustification for Non-CompletionPhysicalSecurityHave entry <strong>and</strong> exit to equipment<strong>and</strong> wiring closets been restricted tounauthorized personnel?Have entry <strong>and</strong> exit to equipment <strong>and</strong> wiringclosets been restricted to unauthorizedpersonnel?Physically lock equipment to astationary durable device such as anoffice desk or inside a computercabinet.Physically lock equipment to a stationarydurable device such as an office desk orinside a computer cabinet.Page 1 of 8
Ensure that each user isauthenticated before access isgranted.Have process in place to clean upaccounts once the user no longerrequires access to the database.Enable auditing <strong>and</strong> logging featureson the system to capture pertinentinformation pertaining to all useractivities.Have a security assessmentperformed on the system, includingpenetration testing.Install host-based security tools suchas Intrusion Detection <strong>and</strong> FileIntegrity Checkers for informationthat contain mission critical data<strong>and</strong>/or confidential data.Disable all unnecessary services onsystem.Ensure that each user is authenticated beforeaccess is granted.Have process in place to clean up accountsonce the user no longer requires access to thedatabase.Enable auditing <strong>and</strong> logging features on thesystem to capture pertinent informationpertaining to all user activities.Have a security assessment performed on thesystem, including penetration testing.Install host-based security tools such asIntrusion Detection <strong>and</strong> File IntegrityCheckers for information that containmission critical data <strong>and</strong>/or confidential data.Disable all unnecessary services on system.Operating<strong>System</strong>SecurityUse Minimum SecurityConfiguration Benchmarks – fromthe Center for Internet Security(supported by NSA, DISA, DHS,<strong>and</strong> NIST <strong>and</strong> security experts frommore than 100 other organizations).Use Minimum Security ConfigurationBenchmarks – from the Center for InternetSecurity (supported by NSA, DISA, DHS,<strong>and</strong> NIST <strong>and</strong> security experts from morethan 100 other organizations).Page 3 of 8
DatabaseSecurityThere are currently minimumsecurity configurations for 14 typesof systems. There are also toolsavailable to test systems against thebenchmarks -http://www.cisecurity.org/index.htmlHave a security assessmentperformed on the system that willcontain the database.Establish accounts for eachindividual user <strong>and</strong> grant theappropriate level of access necessaryto perform job.Ensure that each user isauthenticated before access isgranted.Have process in place to clean upaccounts once the user no longerrequires access to the database.Update patches, subject to changemanagement process, on the systemas they become available <strong>and</strong> afterpatches have been tested in a nonproductionenvironmentEncrypt information stored in thedatabase.There are currently minimum securityconfigurations for 14 types of systems.There are also tools available to test systemsagainst the benchmarks -http://www.cisecurity.org/index.htmlHave a security assessment performed on thesystem that will contain the database.Establish accounts for each individual user<strong>and</strong> grant the appropriate level of accessnecessary to perform job.Ensure that each user is authenticated beforeaccess is granted.Have process in place to clean up accountsonce the user no longer requires access to thedatabase.Update patches, subject to changemanagement process, on the system as theybecome available <strong>and</strong> after patches have beentested in a non-production environmentEncrypt information stored in the database.Page 4 of 8
Enable auditing <strong>and</strong> logging featureson the system to capture pertinentinformation pertaining to all useractivities.Enable auditing <strong>and</strong> logging features on thesystem to capture pertinent informationpertaining to all user activities.NetworkSecurityMonitor network for malicious<strong>and</strong>/or abnormal activityApply patches to network devices,operating systems, <strong>and</strong> software onnetwork subject to changemanagement process.Monitor network for malicious <strong>and</strong>/orabnormal activityApply patches to network devices, operatingsystems, <strong>and</strong> software on network subject tochange management process.Encrypt transmissions that containsensitive <strong>and</strong>/or confidentialinformation.Regularly review logs from networkdevices such as VPN, Routers, IDS,IPS, <strong>and</strong> Firewalls for suspiciousactivity.Update IDS/IPS signatures regularlyEnsure strong passwords are set <strong>and</strong>changed regularly on routers.Remove default passwords from allnetworking devices.Disable all unnecessary services onnetwork devices.Encrypt transmissions that contain sensitive<strong>and</strong>/or confidential information.Regularly review logs from network devicessuch as VPN, Routers, IDS, IPS, <strong>and</strong>Firewalls for suspicious activity.Update IDS/IPS signatures regularlyEnsure strong passwords are set <strong>and</strong> changedregularly on routers.Remove default passwords from allnetworking devices.Disable all unnecessary services on networkdevices.Page 5 of 8
Use stronger more secure protocolsto security network devices such asSSH instead of telnet.Use stronger more secure protocols tosecurity network devices such as SSH insteadof telnet.Anti-VirusHave a security assessmentperformed at least annually onnetwork devices such as routers <strong>and</strong>firewall.Download Anti-Virus softwareprogram <strong>and</strong> instructions fromhttp://helpdesk.gwu.edu/nav/Have a security assessment performed atleast annually on network devices such asrouters <strong>and</strong> firewall.Download Anti-Virus software program <strong>and</strong>instructions fromhttp://helpdesk.gwu.edu/nav/Update Anti-Virus Definitionsregularly.Update Anti-Virus Definitions regularly.Scan system regularly for virus,worm, <strong>and</strong> Trojan activity.Scan system regularly for virus, worm, <strong>and</strong>Trojan activity.SecurityDocumentationDocument description of systemssoftware <strong>and</strong> hardware.Document contingency plan forsystem in the event the systembecomes unavailable.Document <strong>and</strong> maintain backupprocedures for system.Document description of systems software<strong>and</strong> hardware.Document contingency plan for system in theevent the system becomes unavailable.Document <strong>and</strong> maintain backup proceduresfor system.Page 6 of 8
Keep user manuals from vendors forsystems that were pre-built ordevelop documentation on systemsthat have been developed in house.Keep software license catalog ofsystem software <strong>and</strong> applications onh<strong>and</strong>.Keep risk <strong>and</strong> security assessmentsfor system on h<strong>and</strong>.Keep user manuals from vendors for systemsthat were pre-built or develop documentationon systems that have been developed inhouse.Keep software license catalog of systemsoftware <strong>and</strong> applications on h<strong>and</strong>.Keep risk <strong>and</strong> security assessments forsystem on h<strong>and</strong>.BEST PRACTICE CHECKLIST SIGN-OFF1) I have reviewed the <strong>Department</strong> <strong>Server</strong> <strong>and</strong>/or the <strong>Enterprise</strong> <strong>System</strong> against this <strong>Best</strong> Practice checklist.2) <strong>Best</strong> Practice requirements that could not be met for a business justifiable reason has been documented in the “Justification for Non-Completion” column of this document.<strong>System</strong> Administrator Sign-offName:_____________________________Signature:_____________________________<strong>System</strong> Owner Sign-offName:_____________________________Signature:_____________________________Page 7 of 8
Title:_____________________________Date:_____________________________Title:_____________________________Date:_____________________________Page 8 of 8