2-Extended Analysis-Full
2-Extended Analysis-Full
2-Extended Analysis-Full
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
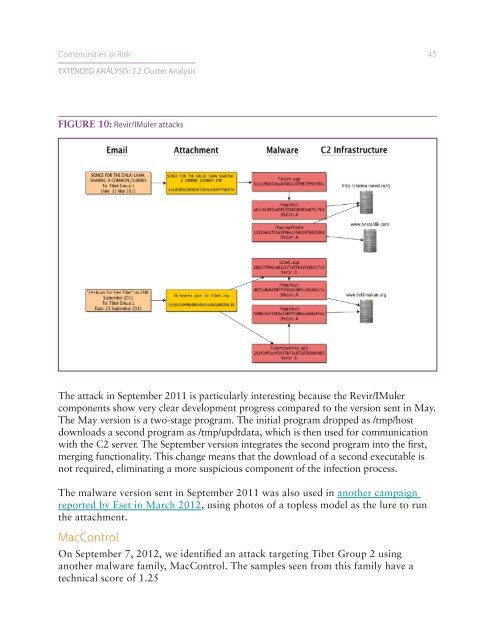
Communities @ Risk 45EXTENDED ANALYSIS: 2.2 Cluster <strong>Analysis</strong>FIGURE 10: Revir/IMuler attacksThe attack in September 2011 is particularly interesting because the Revir/IMulercomponents show very clear development progress compared to the version sent in May.The May version is a two-stage program. The initial program dropped as /tmp/hostdownloads a second program as /tmp/updtdata, which is then used for communicationwith the C2 server. The September version integrates the second program into the first,merging functionality. This change means that the download of a second executable isnot required, eliminating a more suspicious component of the infection process.The malware version sent in September 2011 was also used in another campaignreported by Eset in March 2012, using photos of a topless model as the lure to runthe attachment.MacControlOn September 7, 2012, we identified an attack targeting Tibet Group 2 usinganother malware family, MacControl. The samples seen from this family have atechnical score of 1.25