Nessus Scan Report - Columbia University
Nessus Scan Report - Columbia University
Nessus Scan Report - Columbia University
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
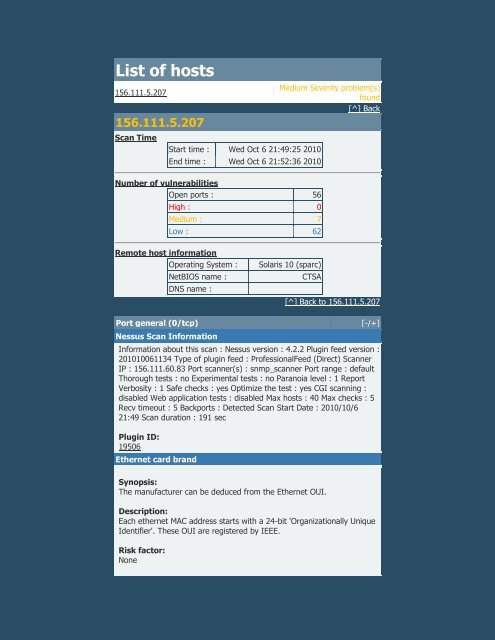
List of hosts156.111.5.207156.111.5.207<strong>Scan</strong> TimeStart time : Wed Oct 6 21:49:25 2010End time : Wed Oct 6 21:52:36 2010Number of vulnerabilitiesOpen ports : 56High : 0Medium : 7Low : 62Medium Severity problem(s)found[^] BackRemote host informationOperating System :NetBIOS name :DNS name :Solaris 10 (sparc)CTSA[^] Back to 156.111.5.207Port general (0/tcp) [-/+]<strong>Nessus</strong> <strong>Scan</strong> InformationInformation about this scan : <strong>Nessus</strong> version : 4.2.2 Plugin feed version :201010061134 Type of plugin feed : ProfessionalFeed (Direct) <strong>Scan</strong>nerIP : 156.111.60.83 Port scanner(s) : snmp_scanner Port range : defaultThorough tests : no Experimental tests : no Paranoia level : 1 <strong>Report</strong>Verbosity : 1 Safe checks : yes Optimize the test : yes CGI scanning :disabled Web application tests : disabled Max hosts : 40 Max checks : 5Recv timeout : 5 Backports : Detected <strong>Scan</strong> Start Date : 2010/10/621:49 <strong>Scan</strong> duration : 191 secPlugin ID:19506Ethernet card brandSynopsis:The manufacturer can be deduced from the Ethernet OUI.Description:Each ethernet MAC address starts with a 24-bit 'Organizationally UniqueIdentifier'. These OUI are registered by IEEE.Risk factor:None
See also:http://standards.ieee.org/faqs/OUI.htmlSee also:http://standards.ieee.org/regauth/oui/index.shtmlSolution:n/aPlugin output:The following card manufacturers were identified : 00:14:4f:3b:50:fa :Sun Microsystems, Inc. 00:14:4f:3b:50:fa : Sun Microsystems, Inc.Plugin ID:35716Port pop3 (110/tcp) [-/+]Service DetectionA POP3 server is running on this port.Plugin ID:22964POP Server DetectionSynopsis:A POP server is listening on the remote port.Description:The remote host is running a server that understands the Post OfficeProtocol (POP), used by email clients to retrieve messages from a server,possibly across a network link.Risk factor:NoneSee also:http://en.wikipedia.org/wiki/Post_Office_ProtocolSolution:Disable this service if you do not use it.Plugin output:Remote POP server banner : +OK POP3 ctsa 2006e.96 server readyPlugin ID:10185Port rpc-portmapper (111/tcp) [-/+]RPC Services Enumeration
Synopsis:An ONC RPC service is running on the remote host.Description:By sending a DUMP request to the portmapper, it was possible toenumerate the ONC RPC services running on the remote port. Using thisinformation, it is possible to connect and bind to each service by sendingan RPC request to the remote port.Risk factor:NoneSolution:n/aPlugin output:The following RPC services are available on UDP port 111 : - program:100000 (portmapper), version: 4 - program: 100000 (portmapper),version: 3 - program: 100000 (portmapper), version: 2Plugin ID:11111RPC portmapper Service DetectionSynopsis:An ONC RPC portmapper is running on the remote host.Description:The RPC portmapper is running on this port. The portmapper allowssomeone to get the port number of each RPC service running on theremote host by sending either multiple lookup requests or a DUMPrequest.Risk factor:NoneSolution:n/aPlugin ID:10223RPC Services EnumerationSynopsis:An ONC RPC service is running on the remote host.Description:By sending a DUMP request to the portmapper, it was possible toenumerate the ONC RPC services running on the remote port. Using thisinformation, it is possible to connect and bind to each service by sendingan RPC request to the remote port.
Risk factor:NoneSolution:n/aPlugin output:The following RPC services are available on TCP port 111 : - program:100000 (portmapper), version: 4 - program: 100000 (portmapper),version: 3 - program: 100000 (portmapper), version: 2Plugin ID:11111Port slinkysearch? (1225/tcp) [-/+]Port netbios-ns (137/udp) [-/+]Port netbios-dgm? (138/udp) [-/+]Port smb (139/tcp) [-/+]Port imap (143/tcp) [-/+]IMAP Service STARTTLS Command SupportSynopsis:The remote mail service supports encrypting traffic.Description:The remote IMAP service supports the use of the 'STARTTLS' commandto switch from a plaintext to an encrypted communications channel.Risk factor:NoneSee also:http://en.wikipedia.org/wiki/STARTTLSSee also:http://tools.ietf.org/html/rfc2595Solution:n/aPlugin output:Here is the IMAP server's SSL certificate that <strong>Nessus</strong> was able to collectafter sending a 'STARTTLS' command : ------------------------------ snip ------------------------------ Subject Name: Country: US State/Province: NewYork Locality: New York City Organization: <strong>Columbia</strong> <strong>University</strong>Organization Unit: CTSA Common Name: ctsa.cpmc.columbia.edu Email
Address: reidar@columbia.edu Issuer Name: Country: USState/Province: New York Locality: New York City Organization:<strong>Columbia</strong> <strong>University</strong> Organization Unit: CTSA Common Name:ctsa.cpmc.columbia.edu Email Address: reidar@columbia.edu SerialNumber: 00 8C 9A EC 4B D1 89 B3 A4 Version: 3 Signature Algorithm:SHA-1 With RSA Encryption Not Valid Before: Apr 10 19:50:32 2009 GMTNot Valid After: Apr 08 19:50:32 2019 GMT Public Key Info: Algorithm:RSA Encryption Public Key: 00 C8 CA 5D 7F 0F DC C6 C3 4B C5 AE 34B4 C2 08 75 4F CC 08 16 D1 59 B1 89 1F 2E 96 83 A6 DB 53 D4 4D 7710 83 85 5F F2 78 12 60 48 61 1B 69 E2 51 0F 41 48 91 44 0D B9 90 C720 7B DA 59 26 A0 39 9E DB 4A 8E 69 D2 66 02 A1 AA 31 E8 8A DF ADBE 50 F6 09 1E 7E A3 8F B1 1F D4 E7 47 5A FD E1 EA 1A 04 0E D9 73C3 11 C1 14 BD 94 13 79 5F B7 95 DE 9B EC 29 72 DA B3 9D 03 75 833A 8D FB EE C3 Exponent: 01 00 01 Signature: 00 72 AE E1 02 87 0F D7DD 52 75 23 F1 F0 75 CC 29 67 B4 F0 66 FA CC 1A 29 88 03 A5 08 269B 84 50 D1 B0 9F AD 9C 30 B5 B4 8F 40 89 65 E2 B2 8C 75 3E 37 CAFC F3 9C 5D 83 B8 EB F6 D1 B7 20 D6 3F E4 65 CB 26 1E 1B AE E4 B668 16 C2 27 BF 5B 9B 48 BB 8E E8 2B 78 46 D0 7D BA A8 A2 F0 39 3FFA D0 62 8F 6B BF 81 67 3E 6E 9D 72 73 49 87 9A 14 45 67 C5 86 FE9F 0B B2 BD BC F2 52 BF 55 D3 A7 Extension: Subject Key Identifier(2.5.29.14) Critical: 0 Subject Key Identifier: A8 0E 4D 77 AF DB D3 A231 2B F2 EE DC A7 A3 AF 61 62 AE 30 Extension: Authority KeyIdentifier (2.5.29.35) Critical: 0 Extension: Basic Constraints (2.5.29.19)Critical: 0 Data: 30 03 01 01 FF ------------------------------ snip ------------------------------Plugin ID:42085IMAP Service Banner RetrievalSynopsis:An IMAP server is running on the remote host.Description:An IMAP (Internet Message Access Protocol) server is installed andrunning on the remote host.Risk factor:NoneSolution:n/aPlugin output:The remote imap server banner is : * OK [CAPABILITY IMAP4REV1LITERAL+ SASL-IR LOGIN-REFERRALS STARTTLS LOGINDISABLED] ctsaIMAP4rev1 2006e.378 at Wed, 6 Oct 2010 21:50:14 -0400 (EDT)Plugin ID:11414Service DetectionAn IMAP server is running on this port.
Plugin ID:22964Port saiscm? (1501/tcp) [-/+]Port www (1581/tcp) [-/+]Service DetectionA web server is running on this port.Plugin ID:22964Port snmp (161/udp) [-/+]SNMP Agent Default Community Name (public)Synopsis:The community name of the remote SNMP server can be guessed.Description:It is possible to obtain the default community name of the remote SNMPserver. An attacker may use this information to gain more knowledgeabout the remote host, or to change the configuration of the remotesystem (if the default community allow such modifications).Risk factor:MediumCVSS Base Score:5.0CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:NSolution:Disable the SNMP service on the remote host if you do not use it, filterincoming UDP packets going to this port, or change the defaultcommunity string.Plugin output:The remote SNMP server replies to the following default communitystring : - publicPlugin ID:41028CVE:CVE-1999-0517BID:2112Other references:OSVDB:209
SNMP Request Network Interfaces EnumerationSynopsis:The list of network interfaces cards of the remote host can be obtainedvia SNMP.Description:It is possible to obtain the list of the network interfaces installed on theremote host by sending SNMP requests with the OID 1.3.6.1.2.1.2.1.0An attacker may use this information to gain more knowledge about thetarget host.Risk factor:NoneSolution:Disable the SNMP service on the remote host if you do not use it, orfilter incoming UDP packets going to this port.Plugin output:Interface 1 information : ifIndex : 1 ifDescr : lo0 ifPhysAddress :Interface 2 information : ifIndex : 2 ifDescr : ce0 ifPhysAddress :00144f3b50fa Interface 3 information : ifIndex : 3 ifDescr : ce0:3ifPhysAddress : 00144f3b50faPlugin ID:10551SNMP Query Installed Software DisclosureSynopsis:The list of software installed on the remote host can be obtained viaSNMP.Description:It is possible to obtain the list of installed software on the remote hostby sending SNMP requests with the OID 1.3.6.1.2.1.25.6.3.1.2 Anattacker may use this information to gain more knowledge about thetarget host.Risk factor:NoneSolution:Disable the SNMP service on the remote host if you do not use it, orfilter incoming UDP packets going to this port.Plugin output:SUNWocfd SUNWcsu SUNWcsr SUNWcsl SUNWcnetr SUNWckrSUNWkvm SUNWcar SUNWcakr FJSVvplu FJSVvplr FJSVhea SUNWcsdSUNWgssc SUNWgss SUNWzlib SUNWopenssl-libraries SUNWsshcuSUNWsshdr SUNWsshdu SUNWsshr SUNWsshu SUNWperl584coreSUNWperl584usr SUNWesu SUNWlibC SUNWlibmsr SUNWlibms SUNWicu
SUNWlexpt SUNWfontconfig-root SUNWfreetype2 SUNWfontconfigSUNWstsf SUNWstsfr SUNWwbsup SUNWinstall-patch-utils-rootSUNWswmt SUNWxwrtl SUNWxwice SUNWbzip SUNWxwfnt SUNWxwdvSUNWxwplr SUNWcpp SUNWdtcor SUNWxwplt SUNWctpls SUNWmfrunSUNWj3rt SUNWlxml SUNWlibpopt SUNWxorg-clientlibs SUNWpngSUNWTiff SUNWjpg SUNWgnome-base-libs-root SUNWgnome-base-libsshareSUNWgnome-base-libs SUNWgnome-component-rootSUNWgnome-component SUNWgnome-config-root SUNWgnome-configshareSUNWgnome-config SUNWgnome-vfs-root SUNWgnome-vfs-shareSUNWgcmn SUNWsmbar SUNWsmbau SUNWgnome-vfs SUNWlibexifSUNWgnome-a11y-base-libs SUNWgnome-audio SUNWgnome-libs-rootSUNWgnome-libs-share SUNWgnome-libs SUNWgnome-panel-rootSUNWgnome-panel-share SUNWgnome-panel SUNWswupclSUNWswupclr SUNWdtdmr SUNWtltk SUNWxwcft SUNWxwoptSUNWdtbas SUNWgzip SUNWj5rt SUNWocfr SUNWocf SUNWdtdteSUNWdtdmn SUNWdticn SUNWdthez SUNWfrhez SUNWib SUNWtavorSUNWj3dev SUNWtcatu SUNWtcatr SUNWdtim SUNWfrim SUNWeurfSUNWi15rf SUNWi15cs SUNWi1cs SUNWfriso1 SUNWadmlib-sysidSUNWadmr SUNWadmap SUNWmdr SUNWmdu SUNWadmc SUNWadmfrSUNWadmfw SUNWlur SUNWluu SUNWfrlu SUNWmoznspr SUNWmozillaSUNWfrmoz SUNWadmj SUNWwbapi SUNWaudit SUNWjsnmpSUNWwbcou SUNWjhrt SUNWmccom SUNWmcc SUNWmc SUNWwbmcSUNWmcdev SUNWfrsmc SUNWwbcor SUNWwbpro SUNWmgaSUNWmgapp SUNWrmui SUNWfrmui SUNWtcpd SUNWtcsh SUNWfrosSUNWtecla SUNWter SUNWpl5u SUNWtexi SUNWcpcu FJSVcpcuSUNWdtjxt SUNWjdsrm SUNWtftp SUNWkrbr SUNWkrbu SUNWtnetcSUNWbip SUNWrcmdc SUNWrcmds SUNWscpr SUNWscpu SUNWjmfSUNWdtscm SUNWdtdst SUNWpmu SUNWpmr SUNWpmowrSUNWpmowu SUNWfrpmw SUNWtftpr FJSVcsr SUNWfmd SUNWtiu8FJSVfmd SUNWpr SUNWtls SUNWmdb FJSVmdb SUNWspl SUNWfrsplSUNWprd SUNWtlsd SUNWfrwbc SUNWtlsu SUNWmdbr FJSVmdbrFJSVpiclu SUNWdtwm SUNWfrwm SUNW1251f SUNW1394SUNWproduct-registry-root SUNWwsr2 SUNWfrws2 SUNW1394hSUNWtoo SUNWtltkd SUNWwsrv SUNWfrwsv SUNW5xmft SUNWxwsvrSUNWfrxwsvr SUNWsadml SUNWfsadl SUNWtltkm SUNWGlib SUNWscguiSUNWfscgu SUNWtnamd SUNWGtkr SUNWtnamr SUNWtnetd SUNWfsfwSUNWGtku SUNWtnetr SUNWtnfc SUNWftltk SUNWPython-shareSUNWPython SUNWxwacx SUNWfwacx SUNWtnfd SUNWowbcpSUNWfwbcp SUNWwbdev SUNWfwdev SUNWfxplt SUNWtxfnt SUNWlxslSUNWgnome-help-viewer-share SUNWgnome-help-viewer SUNWgnomel10ndocument-deSUNWPython-devel SUNWTcl SUNWucbt SUNWudaplrSUNWudaplu SUNWipoib SUNWudapltu SUNWudapltr SUNWTiff-develSUNWudfr SUNWudf SUNWTiff-devel-share SUNWaudd SUNWusbSUNWusbs SUNWuedg SUNWTk SUNWugen SUNWugenu SUNWuiu8SUNWa2psr SUNWimagick SUNWbash SUNWpsutils SUNWa2psuSUNWdoc SUNWuium SUNWgnome-terminal-devel SUNWulcfSUNWgnome-terminal-devel-share SUNWgnome-terminal-rootSUNWgnome-terminal-share SUNWaccr SUNWusbu SUNWxi18nSUNWxim SUNWuxlcf SUNWgnome-text-editor-root SUNWgnome-texteditor-shareSUNWgnome-file-mgr-root SUNWgnome-file-mgr-shareSUNWpcr SUNWpcu SUNWscplp SUNWgnome-print-root SUNWgnomeprint-shareSUNWgnome-print SUNWgnome-file-mgr SUNWgnome-texteditorSUNWaccu SUNWvid SUNWgnome-text-editor-devel SUNWvld
SUNWvldu SUNWaclg SUNWvolr SUNWgnome-l10ndocument-esSUNWnfsckr SUNWnfscr SUNWnfscu SUNWvolu SUNWant SUNWbcpSUNWcslr SUNWacroread SUNWgnome-themes-share SUNWgnomethemesSUNWwbdoc SUNWwebminr SUNWwebminu SUNWacroreadpluginSUNWgnome-ui-designer-share SUNWgnome-ui-designerSUNWgnome-l10ndocument-extra SUNWxge SUNWgnome-user-docsSUNWafbcf SUNWgnome-l10ndocument-fr SUNWgnome-utility-appletsrootSUNWgnome-utility-applets-share SUNWgnome-utility-appletsSUNWafb SUNWafbr SUNWafbw SUNWgnome-vfs-devel SUNWgnomevfs-devel-shareSUNWapbas SUNWgnome-wm-root SUNWgnome-wmshareSUNWgnome-wm SUNWapch2r SUNWapch2u SUNWapch2dSUNWgnome-wm-devel SUNWgnome-l10ndocument-it SUNWrsgSUNWgnome-xml-share SUNWgnome-xml-root SUNWwgetrSUNWlibgcrypt SUNWgnutls SUNWwgetu SUNWgnutls-devel SUNWgpchSUNWgsfot SUNWgsfst SUNWhpijs SUNWgimpprint SUNWgscrSUNWapchr SUNWapchu SUNWapchd SUNWxcu4 SUNWsprotSUNWxcu4t SUNWxcu6 SUNWxilrl SUNWxildh SUNWgssdh SUNWgsskSUNWapmsc SUNWapoc SUNWapcj SUNWxilh SUNWgtar SUNWxilowSUNWbtool SUNWapct SUNWhea SUNWgnome-l10ndocument-jaSUNWapdc SUNWxilvl SUNWapdc-root SUNWhiu8 SUNWxorgcompatlinksSUNWxwinc SUNWxorg-headers SUNWhmd SUNWjafSUNWjmail SUNWxsrt SUNWxrgrt SUNWhmdu SUNWxrpcrt SUNWapocadapter-gconfSUNWi13rf SUNWxscreensaver-hacks SUNWarc SUNWarcrSUNWglrt SUNWxscreensaver-hacks-gl SUNWarrf SUNWi1of SUNWasacSUNWascmn SUNWgnome-l10ndocument-ko SUNWxwcsl SUNWasdbSUNWxwdim SUNWxwdem SUNWi2rf SUNWasdem SUNWxwdxmSUNWxwfa SUNWi4rf SUNWi5rf SUNWxwfs SUNWi7rf SUNWxwhlSUNWgnome-l10ndocument-ptBR SUNWxwkey SUNWxwman SUNWi8rfSUNWxwmod SUNWxwoft SUNWi9rf SUNWxwpft SUNWxwpsrSUNWxwpl SUNWgnome-l10ndocument-sv SUNWicud SUNWidnlSUNWidnd SUNWxwpmn SUNWidnu SUNWxwslb SUNWifbcf SUNWxwsrcSUNWifb SUNWifbr SUNWxwsrv SUNWfbc SUNWifbw SUNWluxopSUNWses SUNWssad SUNWifp SUNWxwxst SUNWxwxft SUNWifphSUNWnisr SUNWnisu SUNWypr SUNWiniu8 SUNWgnome-l10ndocumentzhCNSUNWypu SUNWzebrar SUNWinst SUNWzebrau SUNWzip SUNWipcSUNWzoner SUNWluzone SUNWpoolr SUNWpool SUNWzoneu SUNWzshSUNWipfr SUNWasdemdb SUNWzuluc SUNWipfu SUNWzulu SUNWzulurSUNWipmi TSIpgx TSIpgxw SUNWzuluw SUNWpapi SUNWippcoreSUNWipplr SUNWasjdoc SUNWipplu SUNWiqfs SUNWiquc SUNWiqumSUNWiqdoc SUNWgnome-l10ndocument-zhHK SUNWasman SMEvplrSUNWaspell-share SUNWaspell SMEvplu SUNWaspell-devel SUNWaspellen-shareSUNWaspell-en SUNWiqjx SUNWiqr SUNWasr SUNWiquSUNWast SUNWasu SUNWiscsir SUNWiscsiu SUNWloc SUNWislccSUNWisolc SUNWixgb SUNWj3cfg SUNWced SUNWgnomel10ndocument-zhTWSUNWj3dmo SUNWcg6 SUNWcpc SUNWcprSUNWasut SUNWcti2 SUNWj3rtx SUNWcvc SUNWj3dvx SUNWatfsrSUNWj3irt SUNWcvcr SUNWj3man SUNWatfsu SUNWefc SUNWdrcrSUNWauda SUNWdrr SUNWaudf SUNWgnome-l10nmessages-csSUNWaudh SUNWffb SUNWgnome-l10nmessages-de SUNWpicluSUNWfruid SUNWfruip SUNWciu8 SUNWjiu8 SUNWkiu8 SUNWautoefSUNWgnome-l10nmessages-es SUNWgfb SUNWav1394 SUNWj5cfgSUNWgnome-l10nmessages-extra SUNWj5dev SUNWglmr SUNWi2crSUNWbart SUNWidn SUNWjfb SUNWbindr SUNWbind SUNWkmp2r
SUNWgnome-l10nmessages-fr SUNWj5dmo SUNWbinutils SUNWgnomel10nmessages-huSUNWluxd SUNWgnome-l10nmessages-it SUNWbiprSUNWgccruntime SUNWbison SUNWm64 SUNWgnome-l10nmessages-jaSUNWbnur SUNWgnome-l10nmessages-ko SUNWm64xr SUNWpfbSUNWgnome-l10nmessages-pl SUNWgnome-l10nmessages-ptBRSUNWbnuu SUNWpstl SUNWgnome-l10nmessages-ru SUNWsckmSUNWbsr SUNWsckmr SUNWsckmu SUNWbsu SUNWgnomel10nmessages-svSUNWsfdr SUNWsfdrr SUNWgnome-l10nmessageszhCNSUNWcdrw SUNWj5rtx SUNWj5dmx SUNWsior SUNWgnomel10nmessages-zhHKSUNWstc SUNWcea SUNWus SUNWj5dvxSUNWgnome-l10nmessages-zhTW SUNWcedu SUNWwrsa SUNWj5manSUNWcfcl SUNWrsmo SUNWwrsm SUNWwrsd SUNWgttf SUNWcfclrSUNWcfpl SUNWwrsu SUNWcfplr SUNWcg6h SUNWlccom SUNWiiimuJSatsvu JSatsvr SUNWgttfe JSatsvw SUNWjai SUNW5ttf SUNWjaiimageioSUNWcnsr SUNWcnsu SUNWjato SUNW5ttfe SUNW5xfntSUNWabcp SUNWjatodoc SUNWjatodmo SUNWale SUNWman SUNWaledSUNWgxfnt SUNWhacx SUNWhadis SUNWauaos SUNWauadtSUNWauaow SUNWcacx SUNWhadma SUNWjavaapps SUNWcadisSUNWhbcp SUNWdtab SUNWhdab SUNWcadma SUNWcamosSUNWcamdt SUNWhdbas SUNWjaxp SUNWcamow SUNWcasuSUNWnfssu SUNWdclnt SUNWhsmc SUNWhmga SUNWhdcl SUNWhddstSUNWjcom SUNWcbcp SUNWcstl SUNWjdic SUNWhddte SUNWcdabSUNWdtezt SUNWhdezt SUNWhdft SUNWcdbas SUNWjds-registrationSUNWdhcsr SUNWdhcsu SUNWdhcm SUNWhdhcm SUNWdtheSUNWhdhe SUNWcsmc SUNWcmga SUNWcdcl SUNWjdsver SUNWlpmsgSUNWpsr SUNWpsu SUNWppm SUNWpsf SUNWmp SUNWctluSUNWdthev SUNWhdhev SUNWcxmft SUNWjfbcf SUNWcddst SUNWjfbrSUNWjfbw SUNWhdhez SUNWcddte SUNWjfca SUNWdcsr SUNWdcsuSUNWhdicn SUNWdfbh SUNWhdim SUNWjfcau SUNWhdt SUNWjhdocSUNWjhdem SUNWcdezt SUNWhdwm SUNWcdft SUNWdhcsbSUNWhepmw SUNWcdhcm SUNWjhdev SUNWfdl SUNWhfdl SUNWhimozSUNWcdhe SUNWdial SUNWjib SUNWcdhev SUNWhksmc SUNWhkmgaSUNWhkdcl SUNWhkdt SUNWhkleu SUNWhkeue SUNWdialhSUNWfsmgtu SUNWfsmgtr SUNWdmgtr SUNWhkezt SUNWhkfntSUNWdmgtu SUNWcdhez SUNWcdicn SUNWlvma SUNWlvmr SUNWlvmgSUNWhklvmg SUNWjmfmp3 SUNWdpl SUNWcdim SUNWcdt SUNWhkpltSUNWjpg-devel SUNWjpg-devel-share SUNWcdwm SUNWhkrmuiSUNWjre-config SUNWhkttf SUNWdtct SUNWjre-config-pluginSUNWhkxe SUNWcepmw SUNWdtdem SUNWhkxwsvr SUNWjssSUNWladm SUNWhladm SUNWi2cs SUNWceuos SUNWceudt SUNWhleuSUNWjxmft SUNWhleu2 SUNWceuow SUNWhleue SUNWkdcrSUNWhlvma SUNWkdcu SUNWcfdl SUNWhlvmg SUNWkey SUNWmconrSUNWmctag SUNWmcon SUNWhmcon SUNWciqu SUNWhmctgSUNWciquc SUNWdthed SUNWkoi8f SUNWcjaf SUNWcjmail SUNWcladmSUNWhmoz SUNWhos SUNWcleu SUNWcleu2 SUNWkxmft SUNWolrteSUNWhorte SUNWcleue SUNWlcl SUNWless SUNWpdas SUNWhpdasSUNWdtinc SUNWclvma SUNWclvmg SUNWdtlog SUNWdtma SUNWlibCfSUNWcmcon SUNWllc SUNWdtmad SUNWcmctg SUNWpprorSUNWpprou SUNWhpprou SUNWlibexif-devel SUNWdtmaz SUNWhrmuiSUNWdtrc SUNWlibgcrypt-devel SUNWlibmr SUNWlibm SUNWcmozSUNWdtrp SUNWhsadl SUNWlibpopt-devel SUNWlibpopt-devel-shareSUNWcorte SUNWlibsasl SUNWhscgu SUNWlibusb SUNWlibusbugenSUNWcos SUNWllcr SUNWefcl SUNWhsfw SUNWefcr SUNWlldap
SUNWefcu SUNWerid SUNWcpdas SUNWeuodf SUNWhtltk SUNWcpprouSUNWluxl SUNWcrmui SUNWcsadl SUNWluxopr SUNWcscgu SUNWhttfSUNWeuxwe SUNWcsfw SUNWctltk SUNWcttf SUNWevolution-libs-shareSUNWevolution-libs SUNWevolution-root SUNWevolution-shareSUNWevolution SUNWhttfe SUNWhudc SUNWcttfe SUNWevolution-develSUNWhufnt SUNWcudc SUNWhwbc SUNWevolution-devel-shareSUNWcufnt SUNWevolution-exchange-share SUNWevolution-exchangeSUNWcwbc SUNWhwbcp SUNWevolution-exchange-root SUNWm64cfSUNWm64w SUNWcwbcp SUNWhwdev SUNWcwdev SUNWcwsr2SUNWhwsr2 SUNWcwsrv SUNWevolution-libs-devel SUNWhwsrvSUNWcxe SUNWcxfnt SUNWhxe SUNWhxfnt SUNWcxman SUNWcxpltSUNWcxwsvr SUNWdbcp SUNWdesmc SPZHgc SUNWdmgp SUNWddclSUNWddhcm SUNWmcex SUNWhxman SUNWevolution-socs-connectshareSUNWevolution-socs-connect SUNWdebas SUNWdedisSUNWdedma SUNWhxplt SUNWfac SUNWdedst SUNWhxwsvrSUNWdedte SUNWdehe SUNWdehed SUNWfchbar SUNWfchbaSUNWdehev SUNWi13cs SUNWfctl SUNWfcip SPJAgc SUNWmcosSUNWfcmdb SUNWfcp SUNWdehez SUNWmcosx SUNWdeim SUNWfcsmSUNWdeiso1 SUNWdelu SUNWi5cs SUNWdemoz SUNWi7cs SUNWmdarSUNWdeos SUNWsmapi SUNWmdau SUNWdepmw SUNWffbcf SUNWi9csSUNWmdbdm SUNWdespl SUNWibcp SUNWdewbc SUNWffbwSUNWmddr SPROgc SUNWitsmc SUNWimgp SUNWidcl SUNWdewmSUNWdews2 SUNWdewsv SUNWdexwsvr SUNWmfdev SUNWidhcmSUNWffiltersr SUNWdfdl SUNWmfman SUNWffiltersu SUNWdladmSUNWdlvma SUNWdlvmg SUNWifdl SUNWdmcon SUNWflexruntimeSUNWflexlex SUNWiiimr SUNWdmctg SUNWdorte SUNWdpdasSUNWiladm SUNWdpprou SUNWilvma SUNWdrmui SUNWdsadlSUNWilvmg SUNWdscgu SUNWimcon SUNWdsfw SUNWdtltkSUNWdwacx SUNWdwbcp SUNWdwdev SUNWmibii SUNWfontconfigdocsSUNWdxplt SUNWsasnm SUNWsadmi SUNWsacom SUNWmiprSUNWimctg SUNWmipu SUNWessmc SUNWemgp SUNWedcl SUNWmkcdSUNWedhcm SUNWfppd SUNWmlib SUNWeeuos SUNWeeudtSUNWeeuow SUNWindt SUNWefdl SUNWeladm SUNWelvmaSUNWelvmg SUNWinfnt SUNWemcon SUNWfsexam-root SUNWfsexamSUNWemctg SUNWinleu SUNWeorte SUNWinplt SUNWfss SUNWepdasSUNWepprou SUNWftdur SUNWermui SUNWftduu SUNWftpr SUNWinttfSUNWesadl SUNWesbas SUNWftpu SUNWescgu SUNWiorte SUNWesdisSUNWipdas SUNWfwdcu SUNWfwdc SUNWipprou SUNWesdmaSUNWfwdcd SUNWesdst SUNWgcc SUNWirmui SUNWesdte SUNWisadlSUNWesfw SUNWeshe SUNWiscgu SUNWeshed SUNWeshev SUNWisfwSPZHscl SUNWitbas SUNWmlibe SUNWged SUNWgedu SUNWgfbcfSUNWeshez SUNWmlibh SUNWitdis SUNWmlibk SUNWmlibl SUNWitdmaSUNWmozchat SUNWmozdom-inspector SUNWmozjs-debuggerSUNWmozmail SUNWmoznss SUNWmozpsm SUNWmozspellSUNWmozapoc-adapter SUNWitdst SUNWgfbr SUNWgfbw SUNWesimSUNWitdte SUNWggrp SUNWesiso1 SUNWeslu SUNWithe SUNWesmozSUNWithed SUNWithev SUNWmozgm SUNWesos SUNWgldoc SUNWithezSUNWglrtu SUNWglsrz SUNWgldp SUNWespmw SUNWitim SUNWitiso1SUNWitltk SUNWesspl SUNWitlu SUNWeswbc SUNWitmoz SUNWitosSUNWglrtx SUNWglsrx SUNWgldpx SUNWmozilla-devel SUNWitpmwSUNWglh SUNWeswm SUNWglow SUNWitspl SUNWitwbc SUNWesws2SUNWeswsv SUNWitwm SUNWitws2 SUNWesxwsvr SUNWitwsvSUNWitxwsvr SUNWiwacx SUNWiwbcp SUNWiwdev SUNWetltk
SUNWixplt SUNWj3jmp SUNWeu8df SUNWj5jmp SUNWeulufSUNWeu8os SUNWjsmc SUNWjmga SUNWjadcl SUNWjadisSUNWmoznspr-devel SUNWjadma SUNWeudba SUNWjamoz SUNWglsrSUNWjasu SUNWeudbd SUNWmoznss-devel SUNWjbcp SUNWeuddaSUNWeudhr SUNWjcs3f SUNWjdab SUNWglt SUNWeudhs SUNWgm4SUNWjdbas SUNWgmake SUNWgnome-a11y-base-devel SUNWeudisSUNWeudiv SUNWgnome-a11y-base-devel-share SUNWmysqlrSUNWjddst SUNWeudlg SUNWmysqlu SUNWmysqlt SUNWgnome-a11ygok-shareSUNWgnome-a11y-libs SUNWgnome-a11y-libs-shareSUNWgnome-a11y-speech-share SUNWgnome-a11y-speechSUNWgnome-a11y-gok SUNWjddte SUNWgnome-a11y-gok-rootSUNWeudmg SUNWjdhcm SUNWeuezt SUNWjdhe SUNWjdhedSUNWeuhe SUNWeuhed SUNWjdhev SUNWncar SUNWewacxSUNWjdhez SUNWgnome-a11y-libs-devel-share SUNWgnome-audiodevelSUNWgnome-libs-devel-share SUNWgnome-libs-develSUNWgnome-a11y-libs-devel SUNWewdev SUNWexplt SUNWjdimSUNWncau SUNWfbcp SUNWfmgp SUNWfdcl SUNWjdma SUNWncftSUNWfdhcm SPJAscl SUNWgnome-a11y-poke-share SUNWgnome-a11ypokeSUNWjdoc SUNWffdl SUNWgnome-a11y-reader SUNWfladmSUNWflvma SUNWjdwm SUNWflvmg SUNWgnome-a11y-reader-develSUNWnfsskr SUNWnfssr SUNWgnome-a11y-reader-root SUNWfmconSUNWject SUNWfmctg SUNWjedev SUNWjedt SUNWntpr SUNWjeeztSUNWforte SUNWjfpre SUNWgnome-a11y-reader-share SUNWfpdasSUNWjeman SUNWntpu SUNWfpprou SUNWfrbas SUNWfrdisSUNWpmowm SUNWjepmm SUNWgnome-a11y-speech-develSUNWjepmw SUNWfrdma SUNWjeudc SUNWocfh SUNWfrdstSUNWgnome-archive-mgr-root SUNWgnome-archive-mgr-shareSUNWgnome-archive-mgr SUNWjfdl SUNWfrdte SUNWjfpr SPZHccSUNWogg-vorbis SUNWfrhe SUNWfrhed SUNWogg-vorbis-develSUNWfrhev SUNWjfpu SUNWogg-vorbis-devel-share SUNWgnome-audiodevel-shareSUNWgnome-audio-root SUNWgnome-audio-shareSUNWjfpue SUNWjfxmn SUNWjiqu SUNWgnome-base-libs-devel-shareSUNWgnome-base-libs-devel SUNWjiquc SUNWopensp SUNWopenjadeSUNWjjaf SUNWjjmail SUNWjladm SUNWjlvma SUNWopenjade-develSUNWjlvmg SUNWopenjade-root SUNWjman SUNWjmaneSUNWopenjade-share SUNWjmcon SUNWjmctg SUNWjmfrnSUNWopensp-devel SUNWopensp-root SUNWgnome-calculator-rootSUNWgnome-calculator-share SUNWgnome-calculator SUNWopenspshareSUNWopenssl-commands SUNWjorte SUNWpcmci SUNWpcmcuSUNWpcmem SUNWopenssl-include SUNWjos SUNWgnome-cameraSUNWgnome-camera-devel SUNWgnome-camera-share SUNWopensslmanSUNWjpdas SUNWjpprou SUNWgnome-cd-root SUNWgnome-cdshareSUNWgnome-freedb-libs-root SUNWgnome-freedb-libs-shareSUNWgnome-freedb-libs SUNWgnome-cd SUNWjrmui SUNWopensslrSUNWgnome-cd-burner CSKruby SUNWjsadl SUNWosdem SUNWgnomecd-burner-rootSUNWjscag SUNWjwncr SUNWgnome-cd-burner-shareSUNWjsfw SUNWpamsc SUNWjtlmn SUNWgnome-character-map-shareSUNWgnome-character-map SUNWjtltk SUNWjwacx SUNWjwbcSUNWpcelx SUNWjwbcp SUNWperl-xml-parser SUNWgnome-commondevelSUNWjwbd SUNWgnome-common-devel-share SUNWjwncuSUNWjwncx SUNWpcsclite SUNWgnome-component-devel-shareSUNWgnome-component-devel SUNWjwndt SUNWpcsclite-develSUNWjwnsr SUNWpcser SUNWjwnsu SUNWpd SUNWgnome-config-
devel SUNWjws2 SUNWgnome-config-devel-share SUNWjwsvSUNWgnome-config-editor-share SUNWgnome-config-editor SUNWpduSUNWjxcft SUNWkadma SUNWperl-xml-parser-devel-shareSUNWgnome-desktop-prefs-root SUNWgnome-desktop-prefs-shareSUNWgnome-desktop-prefs SUNWgnome-desktop-prefs-develSUNWperl584man SUNWjxfa SUNWjxplt SUNWjxfnt SUNWpfbcfSUNWgnome-dialog SUNWpfbw SUNWgnome-dialog-share SUNWphxSUNWpiclh SUNWjxim SUNWpiclr SUNWjxoft SUNWgnome-dictionaryrootSUNWgnome-dictionary-share SUNWgnome-dictionarySUNWgnome-display-mgr-root SUNWgnome-display-mgr-shareSUNWgnome-session SUNWgnome-dtlogin-integration SUNWgnomedisplay-mgrSUNWpkgcmdsr SUNWpkgcmdsu SUNWpl5v SUNWpl5mSUNWjxpmn SUNWpl5p SUNWjxumn SUNWgnome-file-mgr-develSUNWjxwsvr SUNWkacx SUNWkadis SUNWplowr SUNWkbcpSUNWgnome-fonts SUNWpmgr SUNWkdab SUNWpng-devel SUNWkdbasSUNWpng-devel-share SUNWksmc SUNWkmga SUNWkdcl SUNWgnomefun-applets-rootSUNWgnome-fun-applets-share SUNWgnome-funappletsSUNWkdcst SUNWkddst SUNWpppd SUNWpppdr SUNWkddteSUNWgnome-games SUNWpppdu SUNWpppdt SUNWpppg SUNWkdeztSUNWppro-plugin-sunos-base SUNWgnome-games-root SUNWkdftSUNWkdhcm SUNWkdhe SUNWpsdpr SUNWpsm-lpd SUNWgnomegames-shareSUNWkdhev SUNWkdhez SUNWqfed SUNWkdicnSUNWqfedu SUNWkdim SUNWqlc SUNWkdt SUNWqos SUNWqosuSUNWkdwm SUNWqus SUNWgnome-hex-editor-root SUNWkpdasSUNWgnome-hex-editor-share SUNWgnome-hex-editor SUNWgnomehex-editor-develSUNWkepmw SUNWqusu SUNWrcapr SUNWrcapuSUNWkfdl SUNWkladm SUNWrcmdr SUNWgnome-im-client SUNWkleuSUNWgnome-im-client-share SUNWrmodu SUNWrmwbr SUNWgnomeimg-editor-shareSUNWgnome-img-editor SUNWrmwbu SUNWkleueSUNWroute SUNWkos SUNWgnome-img-editor-devel SUNWrpcibSUNWklvma SUNWrpm SUNWklvmg SUNWgnome-img-editor-develshareSUNWkmcon SUNWrsgk SUNWkmctg SUNWrsm SUNWrtvcSUNWrtvcl SUNWgnome-img-editor-root SUNWrtvcu SUNWkomozSUNWsbp2 SUNWscbcp SUNWgnome-img-viewer-root SUNWgnomeimg-viewer-shareSUNWgnome-img-viewer SUNWkorte SUNWscmhdlrSUNWkpprou SUNWkrmui SUNWscsa1394 SUNWgnome-internetapplets-rootSUNWgnome-internet-applets-share SUNWgnome-internetappletsSUNWserr SUNWksadl SUNWseru SUNWgnome-intranet-appletsrootSUNWgnome-intranet-applets-share SUNWgnome-intranet-appletsSUNWkscgu SUNWserweb SUNWgnome-media-root SUNWgnomemedia-shareSUNWgnome-media SUNWksfw SUNWsfdoc SUNWgnomejdshelp-shareSUNWgnome-jdshelp SUNWsfinf SUNWktltk SUNWkttfSUNWsfman SUNWsfwdemo SUNWkttfe SUNWsfwhea SUNWgnomemedia-develSUNWslpr SUNWgnome-media-devel-share SUNWgnomemedia-playerSUNWgnome-media-player-root SUNWslpu SUNWgnomemedia-player-shareSUNWsmagt SUNWgnome-mm-applets-rootSUNWgnome-mm-applets-share SUNWgnome-mm-applets SUNWgnomepanel-devel-shareSUNWgnome-panel-devel SUNWkxe SUNWsmbacSUNWkudc SUNWgnome-pdf-viewer-root SUNWgnome-pdf-viewer-shareSUNWgnome-pdf-viewer SUNWkuxft SUNWgnome-perf-meterSUNWsmcmd SUNWgnome-perf-meter-root SUNWgnome-perf-metershareSUNWgnome-print-devel SUNWgnome-print-devel-shareSUNWgnome-project SUNWsmdoc SUNWgnome-project-devel
SUNWgnome-project-devel-share SUNWgnome-project-shareSUNWsmmgr SUNWgnome-ps-viewer SUNWgnome-ps-viewer-rootSUNWgnome-ps-viewer-share SUNWgnome-removable-mediaSUNWgnome-removable-media-share SUNWsndmr SUNWgnome-searchtool-rootSUNWgnome-search-tool-share SUNWgnome-search-toolSUNWkwbc SUNWkwsrv SUNWgnome-session-root SUNWkwbcpSUNWgnome-session-share SUNWgnome-sound-recorder-rootSUNWgnome-sound-recorder-share SUNWgnome-sound-recorderSUNWgnome-spell-share SUNWgnome-spell SUNWgnome-sys-suspendSUNWgnome-sys-suspend-share SUNWgnome-terminal SUNWsndmuSUNWkwdev SUNWkwsr2 SUNWkxfnt SUNWkxfte SUNWkxmanSUNWkxplt SUNWkxwsvr SUNWlocaledefsrc SUNWmeaos SUNWmeadtSUNWmeaow SUNWnafos SUNWnafdt SUNWnafow SUNWnamosSUNWnamdt SUNWnamow SUNWneuos SUNWneudt SUNWneuowSUNWplmoz SUNWplow SUNWplow1 SUNWplxwsvr SUNWptmozSUNWptxwsvr SUNWrumoz SUNWruxwsvr SUNWsamos SUNWsamdtSUNWsamow SUNWsvsmc SUNWsmgp SUNWsdcl SUNWsdhcmSUNWseuos SUNWseudt SUNWseuow SUNWsfdl SUNWsladmSUNWslvma SUNWslvmg SUNWsmcon SUNWsmctg SUNWsorteSUNWspdas SUNWspprou SUNWsrmui SUNWssadl SUNWsscguSUNWssfw SUNWstardict SUNWstardict-root SUNWstltk SUNWsunpinyinSUNWsvbas SUNWdc SUNWsvdis SUNWsvdma SUNWsvdst SUNWsvdteSUNWsvhe SUNWsvhed SUNWsvhev SUNWsvhez SUNWsvimSUNWsviso1 SUNWsvlu SUNWsvmoz SUNWsvos SUNWsvpmwSUNWsvspl SUNWsvwbc SUNWsvwm SUNWsvws2 SUNWsvwsvSUNWsvxwsvr SUNWswacx SUNWswdev SUNWsxplt SUNWtdbasSUNWtddst SUNWtddte SUNWtdft SUNWtdwm SUNWtleu SUNWtxpltSUNWudct SUNWvbcp SUNWvwbcp SUNWweuos SUNWweudtSUNWweuow SUNWsolnm SUNWsom SUNWsogm SUNWspnegoSUNWsra SUNWsrh SUNWvts SUNWvtsmn SUNWvtsr SUNWvtstsSUNWccccrr SUNWccccr SUNWccsign SUNWcsmauth SUNWccfwSUNWbreg SUNWcctpx SUNWccccfg SUNWccfwctrl SUNWccinvSUNWupdatemgru SUNWupdatemgrr SUNWzfskr SUNWzfsr SUNWzfsuCSWpkgget CSWcommon CSWzlib CSWosslrt CSWbdb44 CSWiconvCSWkrb5lib CSWlibmm CSWlibnet CSWgcrypt CSWlibxml2 CSWreadlineCSWunixodbc CSWphp5 CSWmysql5rt CSWap2modphp5 CSWexpatCSWgdbm CSWggettext CSWgsed CSWbdb4 CSWsasl CSWoldaprtCSWperl CSWncurses CSWapache2c CSWap2prefork CSWapache2SMClgcc346 SMCliconv SMCgcc SMCzlib SMCncurs SMCmysql SFWmphpSFWmyjdb SMCsudo CSWpmnetdaemon CSWpmplrpc CSWpmdbiSMCossl SMCwget SUNWpostgr-libs SUNWpostgr SUNWpostgr-serverdataSUNWpostgr-server SMCreadl SMCsamba CSWphp5mysqlCSWossldevel CSWosslutils CSWossl CSWsqlite3 CSWapache2rtCSWsunmath CSWglib2 CSWlibpopt CSWlibidl CSWorbit2 CSWbonobo2CSWftype2 CSWfconfig CSWgpgerr CSWopencdk CSWgnutls CSWjpegCSWlibatk CSWrenderdev CSWlibxrender CSWpng CSWlibcairo CSWtiffCSWlibcups CSWlibxft2 CSWpango CSWgtk2 CSWgconf2 CSWbzip2CSWlibdbus CSWdbusglib CSWfam CSWgnomevfs2 CSWlibartCSWaudiofile CSWesound CSWlibglade2 CSWlibgnomeCSWlibgnomecanvas CSWlibbonoboui CSWgnomekeyringCSWlibgnomeui SMCimap SFWglib2 SFWatk SFWcairo SFWpangoSFWgtk2 SFWdbus SFWdbus-glib SFWfirefox SUNWcbreg SUNWdbregSUNWebreg SUNWfbreg SUNWhbreg SUNWibreg SUNWjbreg
SUNWkbreg SUNWsbreg SUNWcupdatemgru SUNWdupdatemgruSUNWeupdatemgru SUNWfupdatemgru SUNWhupdatemgru SPJAccSUNWiupdatemgru SUNWjupdatemgru SUNWkupdatemgruSUNWsupdatemgru SPROdwrfb SPROmrdwf SPJAmrdwf SPZHmrdwfSPROdwrfx SPROlang SPJAlang SPZHlang SPROlangx SPROsbld SPJAsbldSPZHsbld SPROsbldx SPROlcxs SPROrdbkb SPROrdbkx SPROild SPJAildSPZHild SPROildx SPROcc SPROutool SPJAutool SPZHutool SPROsvcSPJAsvc SPZHsvc SPROmrcc SPJAmrcc SPZHmrcc SPROmrcomSPJAmrcom SPZHmrcom SPROmrild SPJAmrild SPZHmrild SPROmr3mSPJAmr3m SPZHmr3m SPROmrtcv SPJAmrtcv SPZHmrtcv SPROmrdmkSPJAmrdmk SPZHmrdmk SPROmride SPJAmride SPZHmride SPROm9xsSPROm9xsx SPROm9xpx SPROsunms SPROsmsx SPROsmpx SPROmrsbeSPJAmrsbe SPZHmrsbe SPROsbe SPROsnit SPJAsnit SPZHsnit SPROpnsnSPROfd SPJAfd SPROcpl SPJAcpl SPZHcpl SPROcplx SPROcmplSPROtlbn7 SPROtll7 SPROtl7x SPROtll7x SPROscl SPROsclx SPROmrstdSPZHmrstd SPROmrcpl SPJAmrcpl SPZHmrcpl SPROstl4h SPROstl4aSPROstl4o SPROstl4x SPROstl4y SPROftool SPJAftool SPZHftool SPROl90SPROl90x SPROl90s SPROl90sx SPROf90 SPJAf90 SPZHf90 SPROmrftnSPJAmrftn SPZHmrftn SPROl77s SPROl77sx SPROlgc SPROgcx SPROlgcxSPROlklnt SPJAlklnt SPZHlklnt SPROmrmp SPJAmrmp SPZHmrmpSPROdbx SPJAdbx SPZHdbx SPROdbxx SPROjdbx SPJAjdbx SPZHjdbxSMCperl SMCpine CSVNclnt CSVNsrvr CSVNxtrs SMCjpeg SMClungifSMCxaw3d SMCxpm SMCemacs SMCsasl SMCtetex CSWdiffutilsCSWpkgutil CSWneon CSWsvn SMCexpat TIVsmCapi TIVsmCbaSUNWj6rt SUNWj6dev SUNWj6cfg SUNWj6man SUNWj6dmo SUNWj6rtxSUNWj6dvx SUNWj6dmx SUNWj6jmpPlugin ID:19763SNMP Query Running Process List DisclosureSynopsis:The list of processes running on the remote host can be obtained viaSNMP.Description:It is possible to obtain the list of running processes on the remote hostby sending SNMP requests with the OID 1.3.6.1.2.1.25.4.2.1.2 Anattacker may use this information to gain more knowledge about thetarget host.Risk factor:NoneSolution:Disable the SNMP service on the remote host if you do not use it, orfilter incoming UDP packets going to this port.Plugin output:sched init pageout fsflush svc.startd svc.configd syseventd picld kcfdnscd devfsadmd cron rpcbind nfs4cbd nfsmapid sac statd lockd utmpdinetd ttymon nmbd smbd smbd vold mountd nfsd sshd sshd sshd -bash
mount automountd automountd syslogd sendmail sendmail fmd snmpddtlogin sh sh dataserver backupserver httpd dsmc dsmcad smbd smbdxfs sh rpc.ttdbserverd smbd ttymon smbd ex ex perl httpd smbd saselssrv sshd sshd -csh -csh bash bash smbd smbd smbd sshd sshd -cshhttpd smbd httpd smbd sshd sshd -csh httpd smbd -csh java httpd httpdhttpd httpd httpd httpd httpd httpd perl httpd httpd httpd httpd httpdhttpd httpd imapd imapd httpd sendmail in.ftpd in.ftpdPlugin ID:10550SNMP Supported Protocols DetectionSynopsis:This plugin reports all the protocol versions successfully negotiated withthe remote SNMP agent.Description:Extend the SNMP settings data already gathered by testing for SNMPversions other than the highest negotiated.Risk factor:NoneSolution:n/aPlugin output:This host supports SNMP version SNMPv1. This host supports SNMPversion SNMPv2c.Plugin ID:40448SNMP Protocol Version DetectionSynopsis:This plugin reports the protocol version negotiated with the remoteSNMP agent.Description:By sending an SNMP 'get-next-request', it is possible to determine theprotocol version of the remote SNMP agent.Risk factor:NoneSee also:http://en.wikipedia.org/wiki/Simple_Network_Management_ProtocolSolution:Disable the SNMP service on the remote host if you do not use it, orfilter incoming UDP packets going to this port.
Plugin output:<strong>Nessus</strong> has negotiated SNMP communications at SNMPv2c.Plugin ID:35296SNMP Query Routing Information DisclosureSynopsis:The list of IP routes on the remote host can be obtained via SNMP.Description:It is possible to obtain the routing information on the remote host bysending SNMP requests with the OID 1.3.6.1.2.1.4.21 An attacker mayuse this information to gain more knowledge about the networktopology.Risk factor:NoneSolution:Disable the SNMP service on the remote host if you do not use it, orfilter incoming UDP packets going to this port.Plugin output:69.86.246.247/255.255.255.255 127.0.0.1/255.255.255.255128.59.28.164/255.255.255.255 128.59.29.8/255.255.255.255137.187.22.50/255.255.255.255 137.187.22.51/255.255.255.255156.111.0.0/255.255.255.255 156.111.5.0/255.255.255.0156.111.5.1/255.255.255.255 156.111.5.28/255.255.255.255156.111.5.54/255.255.255.255 156.111.5.89/255.255.255.255156.111.5.207/255.255.255.255 156.111.5.255/255.255.255.255156.111.60.83/255.255.255.255 156.111.60.150/255.255.255.255156.111.70.150/255.255.255.255 156.111.204.50/255.255.255.255156.111.255.255/255.255.255.255 156.145.103.24/255.255.255.255156.145.104.15/255.255.255.255 156.145.104.38/255.255.255.255156.145.104.42/255.255.255.255 156.145.104.54/255.255.255.255156.145.104.60/255.255.255.255 156.145.104.67/255.255.255.255156.145.104.70/255.255.255.255 156.145.104.91/255.255.255.255156.145.104.95/255.255.255.255 156.145.104.103/255.255.255.255156.145.104.132/255.255.255.255 156.145.104.136/255.255.255.255156.145.104.149/255.255.255.255 156.145.104.177/255.255.255.255156.145.104.229/255.255.255.255 156.145.105.181/255.255.255.255156.145.109.22/255.255.255.255 156.145.113.37/255.255.255.255160.39.40.212/255.255.255.255 207.46.12.213/255.255.255.255224.0.0.0/240.0.0.0 255.255.255.255/255.255.255.255Plugin ID:34022SNMP Query System Information DisclosureSynopsis:The System Information of the remote host can be obtained via SNMP.
Description:It is possible to obtain the system information about the remote host bysending SNMP requests with the OID 1.3.6.1.2.1.1.1. An attacker mayuse this information to gain more knowledge about the target host.Risk factor:NoneSolution:Disable the SNMP service on the remote host if you do not use it, orfilter incoming UDP packets going to this port.Plugin output:System information : sysDescr : SunOS ctsa 5.10 Generic_141414-02sun4u sysObjectID : 1.3.6.1.4.1.8072.3.2.3 sysUptime : 2d 22h 18m 16ssysContact : "System administrator" sysName : ctsa sysLocation :"System administrators office" sysServices : 72Plugin ID:10800<strong>Nessus</strong> SNMP <strong>Scan</strong>nerSynopsis:SNMP information is enumerated to learn about other open ports.Description:This plugin runs an SNMP scan against the remote machine to find openports. See the section 'plugins options' to configure itRisk factor:NoneSolution:n/aPlugin output:<strong>Nessus</strong> snmp scanner was able to retrieve the open port list with thecommunity name: public It found 38 open TCP ports and 17 open UDPportsPlugin ID:14274Port unknown (16935/tcp) [-/+]Port xdmcp? (177/udp) [-/+]Port rpc-nfs (2049/tcp) [-/+]RPC Services Enumeration
Synopsis:An ONC RPC service is running on the remote host.Description:By sending a DUMP request to the portmapper, it was possible toenumerate the ONC RPC services running on the remote port. Using thisinformation, it is possible to connect and bind to each service by sendingan RPC request to the remote port.Risk factor:NoneSolution:n/aPlugin output:The following RPC services are available on UDP port 2049 : - program:100003 (nfs), version: 2 - program: 100003 (nfs), version: 3 - program:100227 (nfs_acl), version: 2 - program: 100227 (nfs_acl), version: 3Plugin ID:11111RPC Services EnumerationSynopsis:An ONC RPC service is running on the remote host.Description:By sending a DUMP request to the portmapper, it was possible toenumerate the ONC RPC services running on the remote port. Using thisinformation, it is possible to connect and bind to each service by sendingan RPC request to the remote port.Risk factor:NoneSolution:n/aPlugin output:The following RPC services are available on TCP port 2049 : - program:100003 (nfs), version: 2 - program: 100003 (nfs), version: 3 - program:100003 (nfs), version: 4 - program: 100227 (nfs_acl), version: 2 -program: 100227 (nfs_acl), version: 3Plugin ID:11111Port ftp (21/tcp) [-/+]Solaris FTP Daemon Long Command Cross-Site Request Forgery
Synopsis:The remote FTP server has a cross-site request forgery vulnerability.Description:The version of FTP running on the remote host has a cross-site requestforgery vulnerability. Long file names are not processed properly,resulting in the execution of arbitrary commands. If a user is logged intothe FTP server via web browser, a remote attacker could exploit this bytricking them into requesting a maliciously crafted web page, resulting inthe execution of arbitrary FTP commands.Risk factor:MediumCVSS Base Score:4.3CVSS2#AV:N/AC:M/Au:N/C:N/I:P/A:NSee also:http://archives.neohapsis.com/archives/fulldisclosure/2010-05/0283.htmlSee also:http://securityreason.com/achievement_securityalert/84Solution:There is no known solution at this time.Plugin ID:47040BID:40320Other references:OSVDB:64869, Secunia:39856Anonymous FTP EnabledSynopsis:Anonymous logins are allowed on the remote FTP server.Description:This FTP service allows anonymous logins. Any remote user may connectand authenticate without providing a password or unique credentials.This allows a user to access any files made available on the FTP server.Risk factor:MediumCVSS Base Score:5.0CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:NSolution:Disable anonymous FTP if it is not required. Routinely check the FTP
server to ensure sensitive content is not available.Plugin output:The contents of the remote FTP root are : total 80 lrwxrwxrwx 1 0 1 7Dec 31 2009 bin -> usr/bin drwxr-xr-x 2 0 1 512 Jul 13 2004 dev drwxrxr-x2 0 1 512 Jul 13 2004 etc dr-xr-xr-x 21 anonymou 1 512 Jul 122004 pub drwxr-xr-x 5 0 1 512 Jul 12 2004 usrPlugin ID:10079CVE:CVE-1999-0497Other references:OSVDB:69Service DetectionAn FTP server is running on this port.Plugin ID:22964FTP Supports Clear Text AuthenticationSynopsis:Authentication credentials might be intercepted.Description:The remote FTP server allows the user's name and password to betransmitted in clear text, which may be intercepted by a network sniffer,or a man-in-the-middle attack.Risk factor:LowCVSS Base Score:2.6CVSS2#AV:N/AC:H/Au:N/C:P/I:N/A:NSolution:Switch to SFTP (part of the SSH suite) or FTPS (FTP over SSL/TLS). Inthe latter case, configure the server such that control connections areencrypted.Plugin output:This FTP server does not support 'AUTH TLS'.Plugin ID:34324Other references:CWE:522, CWE:523FTP Server Detection
Synopsis:An FTP server is listening on this port.Description:It is possible to obtain the banner of the remote FTP server byconnecting to the remote port.Risk factor:NoneSolution:N/APlugin output:The remote FTP banner is : 220 ctsa FTP server ready.Plugin ID:10092Port ssh (22/tcp) [-/+]SSH Server Type and Version InformationSynopsis:An SSH server is listening on this port.Description:It is possible to obtain information about the remote SSH server bysending an empty authentication request.Risk factor:NoneSolution:n/aPlugin output:SSH version : SSH-2.0-Sun_SSH_1.1.1 SSH supported authentication :gssapi-keyex,gssapi-with-mic,publickey,password,keyboard-interactivePlugin ID:10267Service DetectionAn SSH server is running on this port.Plugin ID:22964Port telnet (23/tcp) [-/+]Telnet Server Detection
Synopsis:A Telnet server is listening on the remote port.Description:The remote host is running a Telnet server, a remote terminal server.Risk factor:NoneSolution:Disable this service if you do not use it.Plugin output:Here is the banner from the remote Telnet server : ------------------------------ snip ------------------------------ login: ------------------------------ snip ------------------------------Plugin ID:10281Service DetectionA telnet server is running on this port.Plugin ID:22964Unencrypted Telnet ServerSynopsis:The remote Telnet server transmits traffic in cleartext.Description:The remote host is running a Telnet server over an unencryptedchannel. Using Telnet over an unencrypted channel is not recommendedas logins, passwords and commands are transferred in cleartext. Anattacker may eavesdrop on a Telnet session and obtain credentials orother sensitive information. Use of SSH is prefered nowadays as itprotects credentials from eavesdropping and can tunnel additional datastreams such as the X11 session.Risk factor:LowCVSS Base Score:2.6CVSS2#AV:N/AC:H/Au:N/C:P/I:N/A:NSolution:Disable this service and use SSH instead.Plugin ID:42263
Port smtp (25/tcp) [-/+]SMTP Server DetectionSynopsis:An SMTP server is listening on the remote port.Description:The remote host is running a mail (SMTP) server on this port. SinceSMTP servers are the targets of spammers, it is recommended youdisable it if you do not use it.Risk factor:NoneSolution:Disable this service if you do not use it, or filter incoming traffic to thisport.Plugin output:Remote SMTP server banner : 220 ctsa.cpmc.columbia.edu ESMTPSendmail 8.13.8+Sun/8.13.8; Wed, 6 Oct 2010 21:50:20 -0400 (EDT)500 5.5.1 Command unrecognized: "GET / HTTP/1.0" 500 5.5.1Command unrecognized: ""Plugin ID:10263Service DetectionAn SMTP server is running on this port.Plugin ID:22964Port remoteware-cl? (3000/tcp) [-/+]Port unknown (30000/tcp) [-/+]Port telnet (3100/tcp) [-/+]Telnet Server DetectionSynopsis:A Telnet server is listening on the remote port.Description:The remote host is running a Telnet server, a remote terminal server.Risk factor:NoneSolution:Disable this service if you do not use it.
Plugin output:Here is the banner from the remote Telnet server : ------------------------------ snip ------------------------------ Username: ------------------------------snip ------------------------------Plugin ID:10281Unencrypted Telnet ServerSynopsis:The remote Telnet server transmits traffic in cleartext.Description:The remote host is running a Telnet server over an unencryptedchannel. Using Telnet over an unencrypted channel is not recommendedas logins, passwords and commands are transferred in cleartext. Anattacker may eavesdrop on a Telnet session and obtain credentials orother sensitive information. Use of SSH is prefered nowadays as itprotects credentials from eavesdropping and can tunnel additional datastreams such as the X11 session.Risk factor:LowCVSS Base Score:2.6CVSS2#AV:N/AC:H/Au:N/C:P/I:N/A:NSolution:Disable this service and use SSH instead.Plugin ID:42263Service DetectionA telnet server is running on this port.Plugin ID:22964Port rpc-fmproduct (32771/tcp) [-/+]RPC Services EnumerationSynopsis:An ONC RPC service is running on the remote host.Description:By sending a DUMP request to the portmapper, it was possible toenumerate the ONC RPC services running on the remote port. Using thisinformation, it is possible to connect and bind to each service by sendingan RPC request to the remote port.
Risk factor:NoneSolution:n/aPlugin output:The following RPC services are available on TCP port 32771 : - program:1073741824 (fmproduct), version: 1Plugin ID:11111Port rpc-status (32772/tcp) [-/+]RPC Services EnumerationSynopsis:An ONC RPC service is running on the remote host.Description:By sending a DUMP request to the portmapper, it was possible toenumerate the ONC RPC services running on the remote port. Using thisinformation, it is possible to connect and bind to each service by sendingan RPC request to the remote port.Risk factor:NoneSolution:n/aPlugin output:The following RPC services are available on TCP port 32772 : - program:100024 (status), version: 1 - program: 100133 (nsm_addrand), version:1Plugin ID:11111Port rpc-rusersd (32773/tcp) [-/+]RPC Services EnumerationSynopsis:An ONC RPC service is running on the remote host.Description:By sending a DUMP request to the portmapper, it was possible toenumerate the ONC RPC services running on the remote port. Using thisinformation, it is possible to connect and bind to each service by sendingan RPC request to the remote port.
Risk factor:NoneSolution:n/aPlugin output:The following RPC services are available on TCP port 32773 : - program:100002 (rusersd), version: 2 - program: 100002 (rusersd), version: 3Plugin ID:11111Port rpc-status (32774/udp) [-/+]RPC Services EnumerationSynopsis:An ONC RPC service is running on the remote host.Description:By sending a DUMP request to the portmapper, it was possible toenumerate the ONC RPC services running on the remote port. Using thisinformation, it is possible to connect and bind to each service by sendingan RPC request to the remote port.Risk factor:NoneSolution:n/aPlugin output:The following RPC services are available on UDP port 32774 : - program:100024 (status), version: 1 - program: 100133 (nsm_addrand), version:1Plugin ID:11111Port rpc-sgi_fam (32776/tcp) [-/+]RPC Services EnumerationSynopsis:An ONC RPC service is running on the remote host.Description:By sending a DUMP request to the portmapper, it was possible toenumerate the ONC RPC services running on the remote port. Using thisinformation, it is possible to connect and bind to each service by sendingan RPC request to the remote port.
Risk factor:NoneSolution:n/aPlugin output:The following RPC services are available on TCP port 32776 : - program:391002 (sgi_fam), version: 1 - program: 391002 (sgi_fam), version: 2Plugin ID:11111Port rpc-ttdbserverd (32777/tcp) [-/+]RPC Services EnumerationSynopsis:An ONC RPC service is running on the remote host.Description:By sending a DUMP request to the portmapper, it was possible toenumerate the ONC RPC services running on the remote port. Using thisinformation, it is possible to connect and bind to each service by sendingan RPC request to the remote port.Risk factor:NoneSolution:n/aPlugin output:The following RPC services are available on TCP port 32777 : - program:100083 (ttdbserverd), version: 1Plugin ID:11111Port rpc-mountd (32778/tcp) [-/+]RPC Services EnumerationSynopsis:An ONC RPC service is running on the remote host.Description:By sending a DUMP request to the portmapper, it was possible toenumerate the ONC RPC services running on the remote port. Using thisinformation, it is possible to connect and bind to each service by sendingan RPC request to the remote port.Risk factor:
NoneSolution:n/aPlugin output:The following RPC services are available on TCP port 32778 : - program:100005 (mountd), version: 1 - program: 100005 (mountd), version: 2 -program: 100005 (mountd), version: 3Plugin ID:11111Port rpc-rstatd (32779/udp) [-/+]RPC Services EnumerationSynopsis:An ONC RPC service is running on the remote host.Description:By sending a DUMP request to the portmapper, it was possible toenumerate the ONC RPC services running on the remote port. Using thisinformation, it is possible to connect and bind to each service by sendingan RPC request to the remote port.Risk factor:NoneSolution:n/aPlugin output:The following RPC services are available on UDP port 32779 : - program:100001 (rstatd), version: 2 - program: 100001 (rstatd), version: 3 -program: 100001 (rstatd), version: 4Plugin ID:11111Port rpc-rusersd (32780/udp) [-/+]RPC Services EnumerationSynopsis:An ONC RPC service is running on the remote host.Description:By sending a DUMP request to the portmapper, it was possible toenumerate the ONC RPC services running on the remote port. Using thisinformation, it is possible to connect and bind to each service by sendingan RPC request to the remote port.
Risk factor:NoneSolution:n/aPlugin output:The following RPC services are available on UDP port 32780 : - program:100002 (rusersd), version: 2 - program: 100002 (rusersd), version: 3Plugin ID:11111Port rpc-rquotad (32782/udp) [-/+]RPC Services EnumerationSynopsis:An ONC RPC service is running on the remote host.Description:By sending a DUMP request to the portmapper, it was possible toenumerate the ONC RPC services running on the remote port. Using thisinformation, it is possible to connect and bind to each service by sendingan RPC request to the remote port.Risk factor:NoneSolution:n/aPlugin output:The following RPC services are available on UDP port 32782 : - program:100011 (rquotad), version: 1Plugin ID:11111Port rpc-cmsd (32786/udp) [-/+]RPC Services EnumerationSynopsis:An ONC RPC service is running on the remote host.Description:By sending a DUMP request to the portmapper, it was possible toenumerate the ONC RPC services running on the remote port. Using thisinformation, it is possible to connect and bind to each service by sendingan RPC request to the remote port.Risk factor:
NoneSolution:n/aPlugin output:The following RPC services are available on UDP port 32786 : - program:100068 (cmsd), version: 2 - program: 100068 (cmsd), version: 3 -program: 100068 (cmsd), version: 4 - program: 100068 (cmsd), version:5Plugin ID:11111Port rpc-mountd (32787/udp) [-/+]RPC Services EnumerationSynopsis:An ONC RPC service is running on the remote host.Description:By sending a DUMP request to the portmapper, it was possible toenumerate the ONC RPC services running on the remote port. Using thisinformation, it is possible to connect and bind to each service by sendingan RPC request to the remote port.Risk factor:NoneSolution:n/aPlugin output:The following RPC services are available on UDP port 32787 : - program:100005 (mountd), version: 1 - program: 100005 (mountd), version: 2 -program: 100005 (mountd), version: 3Plugin ID:11111Port unknown (32789/tcp) [-/+]Port unknown (32791/tcp) [-/+]Port unknown (32856/udp) [-/+]Port rpc-nlockmgr (4045/tcp) [-/+]RPC Services EnumerationSynopsis:
An ONC RPC service is running on the remote host.Description:By sending a DUMP request to the portmapper, it was possible toenumerate the ONC RPC services running on the remote port. Using thisinformation, it is possible to connect and bind to each service by sendingan RPC request to the remote port.Risk factor:NoneSolution:n/aPlugin output:The following RPC services are available on UDP port 4045 : - program:100021 (nlockmgr), version: 1 - program: 100021 (nlockmgr), version: 2- program: 100021 (nlockmgr), version: 3 - program: 100021(nlockmgr), version: 4Plugin ID:11111RPC Services EnumerationSynopsis:An ONC RPC service is running on the remote host.Description:By sending a DUMP request to the portmapper, it was possible toenumerate the ONC RPC services running on the remote port. Using thisinformation, it is possible to connect and bind to each service by sendingan RPC request to the remote port.Risk factor:NoneSolution:n/aPlugin output:The following RPC services are available on TCP port 4045 : - program:100021 (nlockmgr), version: 1 - program: 100021 (nlockmgr), version: 2- program: 100021 (nlockmgr), version: 3 - program: 100021(nlockmgr), version: 4Plugin ID:11111Port cifs (445/tcp) [-/+]Samba Server Detection
Synopsis:An SMB server is running on the remote host.Description:The remote host is running Samba, a CIFS/SMB server for Unix.Risk factor:NoneSee also:http://www.samba.org/Solution:n/aPlugin ID:25240Port commplex-link? (5001/tcp) [-/+]Port rlogin (513/tcp) [-/+]rlogin Service DetectionSynopsis:The rlogin service is listening on the remote port.Description:The remote host is running the 'rlogin' service. This service is dangerousin the sense that it is not ciphered - that is, everyone can sniff the datathat passes between the rlogin client and the rloginserver. This includeslogins and passwords. Also, it may allow poorly authenticated loginswithout passwords. If the host is vulnerable to TCP sequence numberguessing (from any network) or IP spoofing (including ARP hijacking ona local network) then it may be possible to bypass authentication.Finally, rlogin is an easy way to turn file-write access into full loginsthrough the .rhosts or rhosts.equiv files. You should disable this serviceand use ssh instead.Risk factor:MediumCVSS Base Score:5.0CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:NSolution:Comment out the 'login' line in /etc/inetd.confPlugin ID:10205CVE:CVE-1999-0651
Other references:OSVDB:193Port shell? (514/tcp) [-/+]Port unknown (52412/udp) [-/+]Port smtp (587/tcp) [-/+]SMTP Server DetectionSynopsis:An SMTP server is listening on the remote port.Description:The remote host is running a mail (SMTP) server on this port. SinceSMTP servers are the targets of spammers, it is recommended youdisable it if you do not use it.Risk factor:NoneSolution:Disable this service if you do not use it, or filter incoming traffic to thisport.Plugin output:Remote SMTP server banner : 220 ctsa.cpmc.columbia.edu ESMTPSendmail 8.13.8+Sun/8.13.8; Wed, 6 Oct 2010 21:50:11 -0400 (EDT)500 5.5.1 Command unrecognized: "GET / HTTP/1.0" 500 5.5.1Command unrecognized: ""Plugin ID:10263Service DetectionAn SMTP server is running on this port.Plugin ID:22964Port unknown (60405/tcp) [-/+]Port xfs (7100/tcp) [-/+]X Font Service DetectionSynopsis:An X font service is listening on the remote host.Description:
The remote service is an X Window Font Service (xfs) daemon, whichserves font files to clients.Risk factor:NoneSee also:http://www.x.org/docs/FSProtocol/fsproto.pdfSee also:http://en.wikipedia.org/wiki/X_Font_ServerSolution:Limit incoming traffic to this port if desired or disable the service as theuse of server-supplied fonts is currently deprecated.Plugin output:<strong>Nessus</strong> was able to gather the following information from the remote XFont Server : - Protocol : 2.0 - Alternate servers : none - Max requestsize : 65536 bytes - Vendor release : 6000 - Vendor string : XConsortium - Available fonts (up to 15) : --courier-bold-o-normal--0-0-0-0-m-0-iso8859-1 --courier-bold-r-normal--0-0-0-0-m-0-iso8859-1 --courier-medium-o-normal--0-0-0-0-m-0-iso8859-1 --courier-medium-rnormal--0-0-0-0-m-0-iso8859-1--symbol-medium-r-normal--0-0-0-0-p-0--symbol --symbol-medium-r-normal--0-0-0-0-p-0-sun-fontspecific -itccourier-bold-o-normal--0-0-0-0-m-0-iso8859-1-itc-courier-bold-r-normal--0-0-0-0-m-0-iso8859-1 -itc-courier-medium-o-normal--0-0-0-0-m-0-iso8859-1 -itc-courier-medium-r-normal--0-0-0-0-m-0-iso8859-1 -linotype-helvetica-bold-o-normal--0-0-0-0-p-0-iso8859-1 -linotypehelvetica-bold-o-normal-sans-0-0-0-0-p-0-iso8859-1-linotype-helveticabold-r-normal--0-0-0-0-p-0-iso8859-1-linotype-helvetica-bold-r-normalsans-0-0-0-0-p-0-iso8859-1-linotype-helvetica-medium-o-normal--0-0-0-0-p-0-iso8859-1Plugin ID:26971Port finger (79/tcp) [-/+]Finger Recursive Request Arbitrary Site RedirectionSynopsis:It is possible to use the remote host to perform third-party host scans.Description:The remote finger service accepts redirect requests. That is, users canperform requests like : finger user@host@victim This allows an attackerto use this computer as a relay to gather information on a third-partynetwork. In addition, this type of syntax can be used to create a denialof service condition on the remote host.Risk factor:Medium
CVSS Base Score:5.0CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:NSolution:Disable the remote finger daemon (comment out the 'finger' line in/etc/inetd.conf and restart the inetd process) or upgrade it to a moresecure one.Plugin ID:10073CVE:CVE-1999-0105, CVE-1999-0106Other references:OSVDB:64, OSVDB:5769Finger Service Remote Information DisclosureSynopsis:It is possible to obtain information about the remote host.Description:The remote host is running the 'finger' service. The purpose of thisservice is to show who is currently logged into the remote system, andto give information about the users of the remote system. It providesuseful information to attackers, since it allows them to gain usernames,determine how used a machine is, and see when each user logged in forthe last time.Risk factor:MediumCVSS Base Score:5.0CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:NSolution:Comment out the 'finger' line in /etc/inetd.conf and restart the inetdprocessPlugin output:Here is the output we obtained for 'root' : Login Name TTY Idle WhenWhere root Super-User pts/1 Plugin ID:10068CVE:CVE-1999-0612Other references:OSVDB:11451
Service DetectionA finger daemon is running on this port.Plugin ID:22964Port www (80/tcp) [-/+]Multiple Web Server printenv CGI Information DisclosureSynopsis:The remote web server contains a CGI script that discloses information.Description:The remote web server contains the 'test-cgi' test script, which isincluded by default with some web servers. The printenv CGI returns itsenvironment variables. This gives an attacker information like theinstallation directory, the server IP address (which is interesting if NAT isimplemented), the server administrator's e-mail address, the server andmodules versions, the shell environment variables...Risk factor:MediumCVSS Base Score:5.0CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:NSolution:Remove printenv from /cgi-bin.Plugin output:The CGI was found under : http://ctsa.cpmc.columbia.edu/cgibin/printenvPlugin ID:10188Other references:OSVDB:11666Service DetectionA web server is running on this port.Plugin ID:22964Port ajp13 (8009/tcp) [-/+]AJP Connector DetectionSynopsis:There is an AJP connector listening on the remote host.
Description:The remote host is running an AJP (Apache JServ Protocol) connector, aservice by which a standalone web server such as Apache communicatesover TCP with a Java servlet container such as Tomcat.Risk factor:NoneSee also:http://tomcat.apache.org/connectors-doc/See also:http://tomcat.apache.org/connectors-doc/ajp/ajpv13a.htmlSolution:n/aPlugin output:The connector listing on this port supports the ajp13 protocol.Plugin ID:21186Port www (8080/tcp) [-/+]Service DetectionA web server is running on this port.Plugin ID:22964Port www (901/tcp) [-/+]Samba Web Administration Tool (SWAT) DetectionSynopsis:The remote host is running a web server for Samba administration.Description:The remote host is running SWAT, the Samba Web Administration Tool.SWAT is a web-based configuration tool for Samba administration thatalso allows for network-wide MS Windows network passwordmanagement.Risk factor:NoneSee also:http://www.samba.org/samba/docs/man/Samba-HOWTO-Collection/SWAT.htmlSolution:Either disable SWAT or limit access to authorized users and ensure that
it is set up with stunnel to encrypt network traffic.Plugin ID:10273Service DetectionA SWAT server is running on this port.Plugin ID:22964Service DetectionA web server is running on this port.Plugin ID:22964Port imap (993/tcp) [-/+]IMAP Service Banner RetrievalSynopsis:An IMAP server is running on the remote host.Description:An IMAP (Internet Message Access Protocol) server is installed andrunning on the remote host.Risk factor:NoneSolution:n/aPlugin output:The remote imap server banner is : * OK [CAPABILITY IMAP4REV1LITERAL+ SASL-IR LOGIN-REFERRALS AUTH=PLAIN AUTH=LOGIN] ctsaIMAP4rev1 2006e.378 at Wed, 6 Oct 2010 21:50:09 -0400 (EDT)Plugin ID:11414Service DetectionA TLSv1 server answered on this port.Plugin ID:22964Service DetectionAn IMAP server is running on this port through TLSv1.Plugin ID:22964[^] Back to 156.111.5.207