Classification of Security attack in Vehicular Adhoc network: A survey
Classification of Security attack in Vehicular Adhoc network: A survey
Classification of Security attack in Vehicular Adhoc network: A survey
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
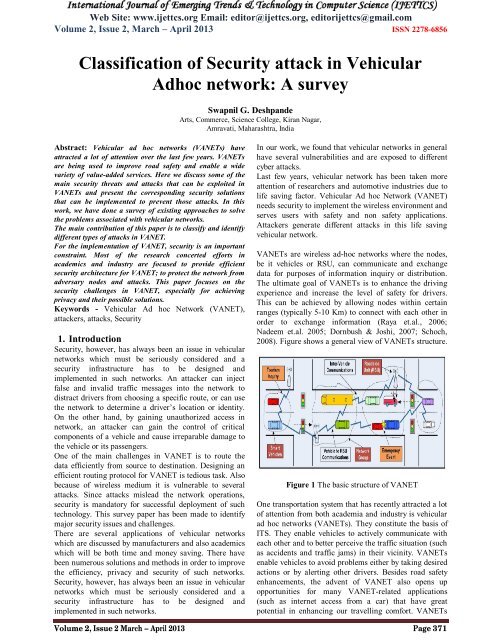
Web Site: www.ijettcs.org Email: editor@ijettcs.org, editorijettcs@gmail.comVolume 2, Issue 2, March – April 2013 ISSN 2278-6856do not depend on fixed <strong>in</strong>frastructures and their nodes(known as mobile nodes) and may form <strong>network</strong>s on thefly for a variety <strong>of</strong> environments. Ow<strong>in</strong>g to the nature <strong>of</strong>these k<strong>in</strong>ds <strong>of</strong> mobile nodes, VANETs can be challengedwith frequent topology changes as well as physical threats(that create potential vulnerabilities for potential<strong>attack</strong>ers). A successful <strong>attack</strong> on VANETs can havecatastrophic results (such as the loss <strong>of</strong> lives) or may leadto f<strong>in</strong>ancial losses (for payment services). Thereforesecur<strong>in</strong>g VANETs is crucial to the design,implementation and operation <strong>of</strong> these <strong>network</strong>s [1].Nowadays, transportation systems play an important part<strong>in</strong> our daily activities. Today major concern is to providesafety <strong>of</strong> users and safe their lives <strong>in</strong> road accidents.Safety and non safety potential applications <strong>of</strong> VANETare to ensure the safety <strong>of</strong> human life on the road.<strong>Security</strong> is the ma<strong>in</strong> concern <strong>of</strong> these applications where awrong message (due to <strong>in</strong>secure environment) maydirectly affect the human lives.Safety and non safety messages are forwarded betweenthe Vehicle to Vehicle (V2V) and Vehicle toInfrastructure (V2I) on this communication medium.Maxim Raya et.al [2] described the <strong>attack</strong>er model.Insider, malicious, active, and local is some example <strong>of</strong>serious level <strong>attack</strong>s. Types <strong>of</strong> <strong>attack</strong>s can be differentdepend<strong>in</strong>g on the behaviour <strong>of</strong> <strong>attack</strong>ers. Our focus po<strong>in</strong>tis too safe the communication medium by controll<strong>in</strong>g<strong>attack</strong>ers. Active and passive safety applications [3] areused to provide safety to users. The role <strong>of</strong> active safety ishigh and it sends warn<strong>in</strong>g messages to other vehicles. If<strong>attack</strong>ers change these messages then accidents become apart <strong>of</strong> the <strong>network</strong> and users’ life can be on risk.Each vehicle comprises <strong>of</strong> hardware unit for determ<strong>in</strong><strong>in</strong>gcorrect location <strong>in</strong>formation us<strong>in</strong>g GPS. Roadside Units(RSUs) are placed across the road for <strong>in</strong>frastructurecommunication. The number <strong>of</strong> RSU to be used dependsupon the communication protocol.Several factors like the type <strong>of</strong> the road, daytime, weather,traffic density and even the driver himself affect themovements <strong>of</strong> vehicles on a road. Hence, the <strong>network</strong>topology change frequently, and the rout<strong>in</strong>g protocol usedhas to adapt itself to these <strong>in</strong>stantaneous changescont<strong>in</strong>uously.1.1. ScopeThe scope <strong>of</strong> this work is to study different types <strong>of</strong>vehicular <strong>network</strong> security issues and theircountermeasures. The purpose <strong>of</strong> this paper is to f<strong>in</strong>d andstudy these vulnerabilities thoroughly and to present asolution to secur<strong>in</strong>g vehicular <strong>network</strong>s fromunauthorized and malicious access.2. <strong>Vehicular</strong> Ad Hoc Networks (VANET)The ma<strong>in</strong> idea beh<strong>in</strong>d VANET is provid<strong>in</strong>gcommunication among vehicles and also among vehiclesand a number <strong>of</strong> fixed equipment located on the road.The ma<strong>in</strong> <strong>in</strong>tention with VANET’s is to enhancevehicles’ passengers’ safety and comfort by distribut<strong>in</strong>gtraffic, speed control, road and weather conditions amongnearby vehicles. Among its applications collisionwarn<strong>in</strong>gs, road sign alarms and automatic toll/park<strong>in</strong>gpayment can be mentioned.VANETs consist <strong>of</strong> a number <strong>of</strong> On-Board Units (OBU)which are located <strong>in</strong>side the vehicles and a number <strong>of</strong>Road-Side Units (RSU) which form the <strong>in</strong>frastructure <strong>of</strong>the <strong>network</strong>. OBU is a wireless gateway which can beconnected to other OBUs and RSUs. Each vehicleequipped with the OBU can become a part <strong>of</strong> the <strong>network</strong>and will be able to send, relay and receive messagesthroughout the <strong>network</strong>. Due to its ad hoc nature, therewon’t be any centralized servers and vehicles are <strong>in</strong>charge <strong>of</strong> <strong>network</strong> management themselves [1].Besides safety applications VANET also provide comfortapplications to the road users.Communication <strong>in</strong> VANET is divided <strong>in</strong>to two differentcategories:• Vehicle-to-Vehicle (V2V) Communication, were thenearby vehicles will communicate traffic and roadconditions to one another• Vehicle-to-Infrastructure (V2I) Communication, werevehicles communicate their gathered <strong>in</strong>formation to thenearest RSU <strong>in</strong> order to distribute the <strong>in</strong>formation fasterand more effectively.2.1 <strong>Security</strong> Requirements Of VANETIn order to have a secure and dependable vehicular<strong>network</strong>, a number <strong>of</strong> security requirements must beconsidered. Some <strong>of</strong> these security requirements are thesame for all <strong>network</strong>s but some are valid and specific tovehicular <strong>network</strong>s only.With respect to the mentioned <strong>attack</strong>s and vulnerabilitiessecur<strong>in</strong>g vehicular communications <strong>in</strong> all aspects is amust. Here we provide a list <strong>of</strong> some general securityrequirements that must be taken <strong>in</strong>to consideration <strong>in</strong>order to mitigate vulnerabilities and <strong>attack</strong>s aga<strong>in</strong>stVANETs.As far as security requirements are concerned theapplications <strong>of</strong> VANET are focused on safety messag<strong>in</strong>g,cooperative driv<strong>in</strong>g, toll application etc. Therefore the<strong>in</strong>tegrity, liability <strong>of</strong> message, liability <strong>of</strong> the user has tobe ensured and at the same time privacy has to be lookedupon. A secure VANET system should satisfy follow<strong>in</strong>grequirements:2.1.1 AuthenticationDespite the lack <strong>of</strong> need for confidentiality, <strong>network</strong>nodes must be authenticated <strong>in</strong> order to be able to sendmessages through the <strong>network</strong>. Before react<strong>in</strong>g tomessages and events a vehicle must verify the legitimacy<strong>of</strong> the message and its sender, therefore there is a need forauthentication. Without authentication, illegitimate andmalicious users can <strong>in</strong>ject false messages <strong>in</strong>to the <strong>network</strong>and confuse other vehicles by distribut<strong>in</strong>g falseVolume 2, Issue 2 March – April 2013 Page 372
Web Site: www.ijettcs.org Email: editor@ijettcs.org, editorijettcs@gmail.comVolume 2, Issue 2, March – April 2013 ISSN 2278-6856<strong>in</strong>formation. With authentication, vehicles can simplydrop messages from unauthenticated users.2.1.2 AuthorizationAuthorization is on a higher level implemented by accesscontrol which itself is def<strong>in</strong>ed by <strong>network</strong> policies.Authorization def<strong>in</strong>es the role <strong>of</strong> a node <strong>in</strong> the <strong>network</strong>which <strong>in</strong>cludes the types <strong>of</strong> messages a node can read orwrite on the <strong>network</strong>, actions it is allowed to take andgenerally the protocols that it can execute.2.1.3 Data ConsistencyIn addition to authenticat<strong>in</strong>g the sender, the consistency<strong>of</strong> messages with similar ones regard<strong>in</strong>g time andlocation must also be considered, because false messagesfrom legitimate senders are not impossible. It is extremelyimportant for warn<strong>in</strong>g messages to meet the time andlocation constra<strong>in</strong>ts. A warn<strong>in</strong>g message must be shownto the driver before it is too late to react and also beforepass<strong>in</strong>g the correspond<strong>in</strong>g geographic location <strong>of</strong> thewarn<strong>in</strong>g.2.1.4 ConfidentialityS<strong>in</strong>ce security <strong>in</strong> vehicular <strong>network</strong>s is related to safety,all <strong>network</strong> users should normally have full access to<strong>network</strong> data, i.e. traffic <strong>in</strong>formation, road conditions, etc.<strong>in</strong> order to make <strong>in</strong>formed decisions. S<strong>in</strong>ce messages <strong>in</strong>VANETs don't conta<strong>in</strong> any sensitive <strong>in</strong>formation and arenot confidential, there is no need for encryption andconfidentiality is not an important issue. Therefore,vehicular <strong>network</strong>s do not have to be protected aga<strong>in</strong>steavesdropp<strong>in</strong>g. However, <strong>network</strong> data should be sentfrom authenticated sources and this can be done by sourceauthentication.2.1.5 IntegrityAll messages which are sent and received on the <strong>network</strong>should be protected aga<strong>in</strong>st alteration <strong>attack</strong>s. A securevehicular <strong>network</strong> should provide protection aga<strong>in</strong>stmessage alteration. A message can be altered <strong>in</strong> severalways dur<strong>in</strong>g its transit from source to dest<strong>in</strong>ations and allpossible <strong>attack</strong>s must be considered.When it comes to <strong>in</strong>tegrity there are three ma<strong>in</strong> threatsdirectly related to message contents. System threatsregard<strong>in</strong>g <strong>in</strong>tegrity <strong>in</strong>clude (1) wrong or forged messages,(2) messages which are modified dur<strong>in</strong>g transmission and(3) replayed messages.2.1.6 AvailabilityS<strong>in</strong>ce vehicular <strong>network</strong>s require real-time responses,they are vulnerable to DoS <strong>attack</strong>s. In order to rema<strong>in</strong>operational, protocols and services must be resilientaga<strong>in</strong>st denial <strong>of</strong> service <strong>attack</strong>s. The communicationchannel must be available at all times, it must also bereliable otherwise <strong>attack</strong>ers can launch DoS <strong>attack</strong>s. Such<strong>attack</strong>s can disrupt the entire <strong>network</strong> which will lead t<strong>of</strong>ailure <strong>in</strong> deliver<strong>in</strong>g <strong>network</strong> messages to other vehicles<strong>in</strong> range. Therefore they must be securely designed and befault-tolerant <strong>in</strong> order to work under faulty conditions.There are a couple <strong>of</strong> security measures such as channelmonitor<strong>in</strong>g which is a means to <strong>in</strong>crease channelavailability. Besides, new technologies are always underdevelopment which will try to <strong>in</strong>crease availability <strong>in</strong>communication channels.Although availability can never be completelyguaranteed, yet there are still a couple <strong>of</strong> securitymeasures such as channel monitor<strong>in</strong>g which is a means to<strong>in</strong>crease channel availability. Besides, channel switch<strong>in</strong>gand us<strong>in</strong>g different communication technologies <strong>in</strong> case<strong>of</strong> jamm<strong>in</strong>g <strong>attack</strong>s can be helpful.2.1.7 Non RepudiationWhen a node sends out a message, it shouldn’t be able tolater deny send<strong>in</strong>g that message. In case <strong>of</strong> accidents or<strong>in</strong>vestigations, problem-caus<strong>in</strong>g drivers should be reliablyidentified, to correctly address the sequence and contents<strong>of</strong> exchanged messages. This can be done by sign<strong>in</strong>goutgo<strong>in</strong>g messages with an anonymous key exclusivelyrelated to the sender and also a time- stamp associated tothe message prevent<strong>in</strong>g the user to claim that a particularmessage has been replayed.In case <strong>of</strong> us<strong>in</strong>g digital signatures, each message is signedwith its private but anonymous key. Therefore the vehicleowner cannot claim that he hasn't sent the message.2.1.8 PrivacyDriver privacy is an important issue <strong>in</strong> vehicularcommunications. Drivers don’t want their personal andprivate <strong>in</strong>formation to be accessible by others. S<strong>in</strong>ce thevehicle <strong>in</strong>formation such as location, speed, time andother car data are transmitted via wirelesscommunication, there should not be possible to <strong>in</strong>fer thedriver's identity from this <strong>in</strong>formation. Among this<strong>in</strong>formation, driver's location and trac<strong>in</strong>g vehiclemovements are more sensitive and must be taken <strong>in</strong>toconsideration carefully .Regard<strong>in</strong>g this issue we come to another requirementcalled “anonymity” which is discussed below.2.1.9 AnonymityAnonymity def<strong>in</strong>es the requirement that <strong>network</strong> nodesmust not be able to <strong>in</strong>fer if a node performed or willperform some specific action <strong>in</strong> future. In order to preventsuch <strong>in</strong>ferences, there must be an equal probability <strong>of</strong>do<strong>in</strong>g a specific action by all nodes, or have strongprobabilistic anonymity, with the probabilities be<strong>in</strong>gequal for all nodes. By not requir<strong>in</strong>g a vehicle toauthenticate with its exact identity to other vehicles towhich it sends <strong>in</strong>formation.2.1.10 Real-time Constra<strong>in</strong>tsIn order to have vehicular <strong>network</strong>s secured, specificmeasures and techniques have been suggested. Althoughthese techniques seem applicable and useful, there is oneimportant issue that must be taken <strong>in</strong>to account, real-timeVolume 2, Issue 2 March – April 2013 Page 373
Web Site: www.ijettcs.org Email: editor@ijettcs.org, editorijettcs@gmail.comVolume 2, Issue 2, March – April 2013 ISSN 2278-6856constra<strong>in</strong>ts. Out-dated messages, e.g. out-dated traffic orroad/weather conditions, are <strong>of</strong> no use <strong>in</strong> vehicular<strong>network</strong>s and must be elim<strong>in</strong>ated <strong>in</strong> order to let the newlygenerated messages get to their dest<strong>in</strong>ations on time. Onthe other hand, solutions such as digital signatures andcertificates must be designed specifically for vehicular<strong>network</strong>s <strong>in</strong> order to fulfill real-time constra<strong>in</strong>ts <strong>of</strong> such<strong>network</strong>s.3. <strong>Security</strong> challenges <strong>in</strong> VANETsDespite the various benefits <strong>of</strong>fered by VANETs, they<strong>in</strong>troduce several security challenges to the researchcommunity. These security challenges are mostlyconcerned with the trade-<strong>of</strong>f between authentication andnonrepudiation versus privacy dur<strong>in</strong>g communicationwith<strong>in</strong> VANET environments. Another security challengeis delay sensitivity because significant delays prohibit theuse <strong>of</strong> security protocols that have high overheads or relyon multiple stages <strong>of</strong> full-duplex communication betweennodes [4,5].The use <strong>of</strong> traditional authentication mechanisms toaddress some security threats (such as illusion <strong>attack</strong>s)without affect<strong>in</strong>g privacy <strong>in</strong> VANETs poses a newchallenge for those VANET applications that need toauthenticate nodes <strong>in</strong> VANETs [6,7].The other challenge is the restriction <strong>in</strong>troduced by thetransitory nature <strong>of</strong> <strong>in</strong>teractions <strong>in</strong> a VN to usereputation-based schemes [8].Another VANET security challenge is the forward<strong>in</strong>g <strong>of</strong>event-related messages on very large ad hoc <strong>network</strong>s <strong>of</strong>highly mobile nodes <strong>in</strong> such a way that the <strong>in</strong>formationcan be trusted by receiv<strong>in</strong>g nodes because by do<strong>in</strong>g so weimprove traffic safety and mobility [9].All these challenges need to be addressed to provide asecure VANET <strong>in</strong>frastructure where nodes (vehicles) cancommunicate securely with each other and <strong>in</strong>frastructureunits.Table 1 Summary <strong>of</strong> security <strong>attack</strong>s <strong>in</strong> VANETs11 This <strong>survey</strong> paperidentify majorsecurity issues andchallenges associatedwith different rout<strong>in</strong>gprotocols.Third Type: Tim<strong>in</strong>gAttackForth Type: SocialAttackFifth Type:Monitor<strong>in</strong>g AttackFirst Type: Attacks onavailability1.Black Hole Attack2.Malware3.BroadcastTamper<strong>in</strong>g4.Spamm<strong>in</strong>g5.Greedy Drivers6.Denial <strong>of</strong> ServiceSecond Type: Attackson Authentication/identification1.Masquerad<strong>in</strong>g2.Replay Attack3.Global Position<strong>in</strong>gSystem (GPS)Spo<strong>of</strong><strong>in</strong>g4.Tunnel<strong>in</strong>g5.Sybil AttackRef.ObjectiveNo.10 In this paper, wepropose five differentclasses <strong>of</strong> <strong>attack</strong>s andevery class isexpected to providebetter perspective forthe VANET security.The ma<strong>in</strong>contribution <strong>of</strong> thispaper is the proposedsolution forclassification andidentification <strong>of</strong>different <strong>attack</strong>s <strong>in</strong>VANET.Types <strong>of</strong> AttackFirst Type: NetworkAttack1. Denial <strong>of</strong> service(DOS) Attack2.Distributed Denial <strong>of</strong>service (DDOS) Attack3.Sybil Attack4.Node ImpersonationAttackSecond Type:Application Attack(AP)12 This paper aims todescribe and analyzethe mostrepresentative6.Message Tamper<strong>in</strong>g7.ID DisclosureThird Type: Attackson confidentialityFourth Type: Attackson privacyFifth Type: Attacks onnon-repudiationSixth Type: Attackson data trustFirst Type : Attackson identification andauthenticationVolume 2, Issue 2 March – April 2013 Page 374
Web Site: www.ijettcs.org Email: editor@ijettcs.org, editorijettcs@gmail.comVolume 2, Issue 2, March – April 2013 ISSN 2278-6856VANET securitydevelopments1.Impersonation.1.1False attributepossession.2. Sybil.Second Type: Attackson privacy1.Identity reveal<strong>in</strong>g.2. Location track<strong>in</strong>g.Third Type: Attackson non-repudiationFourth Type: Attackson confidentialityFifth Type: Attacks onavailability1.Network Denial <strong>of</strong>Service (DoS)1.1Rout<strong>in</strong>g anomalies.13 In this paper, wehave classifieddifferent security<strong>attack</strong>s and logicallyorganized/represented <strong>in</strong> a more lucidmanner based on thelevel <strong>of</strong> effect <strong>of</strong> aparticular security<strong>attack</strong> on <strong>in</strong>telligentvehicular traffic.1.Malicious nodes2.Illusion <strong>attack</strong>Fifth Type: Location1.Forg<strong>in</strong>g positionsand Sybil <strong>attack</strong>s2.Position cheat<strong>in</strong>gand false positiondissem<strong>in</strong>at<strong>in</strong>gFirst Type: NetworkAttacks1.Denial <strong>of</strong> service(DOS) Attack2.Distributed Denial <strong>of</strong>service Attack3.Sybil Attack4.Node ImpersonationSecond Type:Application Attack2.Computation DoS.Third Type: Tim<strong>in</strong>gAttack1 This paper discussessome <strong>of</strong> the ma<strong>in</strong>security threats and<strong>attack</strong>s that can beexploited <strong>in</strong>VANETs and presentthe correspond<strong>in</strong>gsecurity solutionsthat can beimplemented tothwart those <strong>attack</strong>s.Sixth Type: Attackson data trustFirst Type:Anonymity1.Malicious VehicleSecond Type: Keymanagement1.Brute force <strong>attack</strong>:2. Misbehav<strong>in</strong>g andfaulty nodesThird Type: Privacy1.Malicious user2.Traffic analysis<strong>attack</strong>sFourth Type :Reputation14 F<strong>in</strong>ally, we outl<strong>in</strong>esome <strong>of</strong> the VANETresearch challengesthat still need to beaddressed to enablethe ubiquitousdeployment and widespread adoption <strong>of</strong>scalable, reliable,robust, and secureVANETarchitectures,protocols,technologies, andservices.Fourth Type: SocialAttackFifth Type:Monitor<strong>in</strong>g AttackFirst Type: Threats toavailability1.Denial <strong>of</strong> ServiceAttack2.BroadcastTamper<strong>in</strong>g3.Malware4.Spamm<strong>in</strong>g5.Black Hole AttackSecond Type: Threatsto authenticity1.Masquerad<strong>in</strong>gVolume 2, Issue 2 March – April 2013 Page 375
Web Site: www.ijettcs.org Email: editor@ijettcs.org, editorijettcs@gmail.comVolume 2, Issue 2, March – April 2013 ISSN 2278-68562.Replay Attack3.Global Position<strong>in</strong>gSystem (GPS)Spo<strong>of</strong><strong>in</strong>g4.Tunnel<strong>in</strong>g5.Position Fak<strong>in</strong>g6.Message Tamper<strong>in</strong>g7.MessageSuppression/Fabrication/ Alteration8.Key and/orCertificate Replication9.Sybil AttackThird Type: Threatsto confidentiality4. PROPERTIES OF ATTACKERSAttacker create problem <strong>in</strong> the <strong>network</strong> by gett<strong>in</strong>g fullaccess <strong>of</strong> communication medium DSRC. Here we arediscuss<strong>in</strong>g some properties and capability <strong>of</strong> the <strong>attack</strong>erswhich has been mentioned <strong>in</strong> studies.InsiderThis type <strong>of</strong> <strong>attack</strong>ers who is an authentic user <strong>of</strong> the<strong>network</strong> and have detail knowledge <strong>of</strong> <strong>network</strong>. Insider<strong>attack</strong>er might have access to <strong>in</strong>sider knowledge and thisknowledge will be used for understand<strong>in</strong>g the design andconfiguration <strong>of</strong> <strong>network</strong>. When they have all <strong>in</strong>formationabout the configuration then it’s easy for them to launch<strong>attack</strong>s and create more problem as compare to outsider<strong>attack</strong>er. It can create problem <strong>in</strong> the <strong>network</strong> bychang<strong>in</strong>g the certificate keys. We can simply say that<strong>in</strong>sider <strong>attack</strong>er is the right man do<strong>in</strong>g the wrong job <strong>in</strong>the <strong>network</strong>.OutsiderThe outsider <strong>attack</strong>er is considered as an authentic user <strong>of</strong>the <strong>network</strong>. It is a k<strong>in</strong>d <strong>of</strong> <strong>in</strong>truder which aims to misusethe protocols <strong>of</strong> the <strong>network</strong> and the range <strong>of</strong> such <strong>attack</strong>sare limited. Outsider <strong>attack</strong>er also has a limited diversityfor launch<strong>in</strong>g different k<strong>in</strong>d <strong>of</strong> <strong>attack</strong>s as compare to<strong>in</strong>sider <strong>attack</strong>er.Coverage areaCoverage area is the ma<strong>in</strong> property <strong>of</strong> <strong>attack</strong>er when theylaunch any k<strong>in</strong>d <strong>of</strong> <strong>attack</strong>s. Attacker could cover the ma<strong>in</strong>area <strong>of</strong> road, and it depends on the nature <strong>of</strong> the <strong>attack</strong>s.Basic level <strong>attack</strong>er has controlled one DSRC channelsand covers the range <strong>of</strong> at most 1000 meters but theextended level <strong>attack</strong>ers are more organized and covermore area us<strong>in</strong>g <strong>of</strong> hundred DSRC channels.Technical ExpertiseTechnical expertise <strong>of</strong> the <strong>attack</strong>er makes them strongerfor creat<strong>in</strong>g <strong>attack</strong>s <strong>in</strong> the <strong>network</strong>. It is difficult for<strong>attack</strong>er to mount <strong>attack</strong>s on cryptographic algorithms.Chance is low for <strong>attack</strong>er to compromise the<strong>in</strong>frastructure <strong>network</strong> and data capture from restrictedarea <strong>of</strong> <strong>network</strong>. Attacker hav<strong>in</strong>g ability to extracts theprogram code and secret keys <strong>of</strong> the comput<strong>in</strong>g platform<strong>of</strong> OBU and RSU by launch<strong>in</strong>g physical <strong>attack</strong>s.ResourcesBudget, manpower and tools are the three ma<strong>in</strong> keyresources and <strong>attack</strong>ers depend on it to achieve theirgoals. Need budget to borrow technical expert and spendtime to understand the configuration <strong>of</strong> specific <strong>network</strong>and then disturb <strong>network</strong> with launch<strong>in</strong>g <strong>of</strong> different k<strong>in</strong>d<strong>of</strong> <strong>attack</strong>s. Attacker can use different k<strong>in</strong>d <strong>of</strong> tools forlaunch<strong>in</strong>g <strong>attack</strong>s. These s<strong>of</strong>tware tools can develop byown self or buy from the market. Many bus<strong>in</strong>ess partiesmake setup their bus<strong>in</strong>ess nears the road and provide nonsafety application services (Internet, enterta<strong>in</strong>mentservices). One bus<strong>in</strong>ess party can be used their ownmaximum resources to create problems for other partiesand destroy their bus<strong>in</strong>ess with different k<strong>in</strong>d <strong>of</strong> <strong>attack</strong>s.5. Conclusion and Future workIn this paper various <strong>attack</strong>s <strong>in</strong> VANET have beenclassified. It has been observed that the classificationhelps to deal with different types <strong>of</strong> <strong>attack</strong> on VANET.Due to recent improvements <strong>in</strong> connect<strong>in</strong>g vehicles toexternal <strong>network</strong>s, proper security mechanisms must bedeveloped <strong>in</strong> parallel to reduce the risk <strong>of</strong> malicious andunauthorized behavior <strong>in</strong> the vehicular <strong>network</strong> doma<strong>in</strong>.Users require safety on road <strong>in</strong> future vehicular <strong>network</strong>and it could be possible by implement<strong>in</strong>g VANETapplications.We expect that the proposed <strong>attack</strong>s classes may helpfulto identify <strong>attack</strong>s and understand <strong>attack</strong>ers. It is difficultto control <strong>attack</strong>ers but <strong>in</strong> future work we will developsuch system to identify <strong>attack</strong>s <strong>in</strong> <strong>network</strong> with respect tosome specific type <strong>of</strong> <strong>attack</strong>. Implementation could beeasy <strong>of</strong> this future human life sav<strong>in</strong>g <strong>network</strong> if wecontrol <strong>attack</strong>ers and their <strong>attack</strong>s.In this work, we have analyzed the <strong>attack</strong>s that VANETscan be subjected to. Table provides a summary <strong>of</strong> thesecurity <strong>attack</strong>s we have identified that may be launchedon VANETs and the correspond<strong>in</strong>g security solutions tomitigate those <strong>attack</strong>s. I hope that this <strong>survey</strong> will enableVANET designers and developers to build more secureand robust VANET architectures, protocols andapplications <strong>in</strong> the future.Volume 2, Issue 2 March – April 2013 Page 376
Web Site: www.ijettcs.org Email: editor@ijettcs.org, editorijettcs@gmail.comVolume 2, Issue 2, March – April 2013 ISSN 2278-6856REFERENCES[1] J.T. Isaac S. Zeadally J.S. Ca´mara “<strong>Security</strong> <strong>attack</strong>sand solutions for vehicular ad hoc <strong>network</strong>s” IETCommunications 2009.[2] M. Raya, J. Pierre, Hubaux,”Secur<strong>in</strong>g vehicular adhoc Networks” Journal <strong>of</strong> Computer <strong>Security</strong>,vol.15,january 2007, pp: 39-68.[3] A.Weimerskirch,J.JHaas,Y.C.Hu,K.P.Laberteaux,”Data security <strong>in</strong>vehicular communication <strong>network</strong>s”,chapter no.09,pp309-310.[4] BURMESTER M., MAGKOS E.,CHRISSIKOPOULOS V.: ‘Strengthen<strong>in</strong>g Privacyprotection <strong>in</strong> VANETs’. IEEE Int. Conf. on Wireless& Mobile Comput<strong>in</strong>g, Network<strong>in</strong>g &Communication (WIMOB 2008), 2008, pp. 508–513[5] JAKUBIAK J., KOUCHERYAV Y.: ‘State <strong>of</strong> the artand research challenges for VANETs’. Fifth IEEEConsumer Communications and Network<strong>in</strong>g Conf.(CCNC 2008), 2008, pp. 912–916[6] XI Y., SHA K., SHI W., SCHWIEBERT L., ZHANGT.: ‘Enforc<strong>in</strong>g privacy us<strong>in</strong>g symmetric random keyset<strong>in</strong> vehicular <strong>network</strong>s’. Eighth Int. Symp. onAutonomous Decentralized Systems (ISADS 2007),2007, pp. 344–351[7] LO N., TSA H.: ‘Illusion <strong>attack</strong> on VANETapplications – a message plausibility problem’. IEEEGlobecom Workshops, 2007, pp. 1–8[8] PARNO B., PERRIG A.: ‘Challenges <strong>in</strong> secur<strong>in</strong>gvehicular <strong>network</strong>s’. Fourth Workshop on Hot Topics<strong>in</strong> Networks (HotNets-IV), 2005[9] FLORIAN D., LARS F., PRZEMYSLAW M.:‘VARS: a vehicle ad hoc <strong>network</strong> reputation system’.Int. Conf. on a World <strong>of</strong> Wireless, Mobile andMultimedia Networks (WOWMOM 2005), 2005, pp.454–456[10] Irshad Ahmed Sumra,Iftikhar Ahmad, HalabiHasbullah “Classes <strong>of</strong> Attacks <strong>in</strong> VANET”[11] Anup Dhamgaye, Nekita Chavhan “Survey onsecurity challenges <strong>in</strong> VANET” IJCSN InternationalJournal <strong>of</strong> Computer Science and Network, Vol 2,Issue 1, 2013 88[12] José María de Fuentes, Ana Isabel González-Tablas,Arturo Ribagorda “Overview <strong>of</strong> security issues <strong>in</strong><strong>Vehicular</strong> Ad-hoc Networks”[13] Adil Mudasir Malla Ravi Kant Sahu “<strong>Security</strong>Attacks with an Effective Solution for DOS Attacks<strong>in</strong> VANET” International Journal <strong>of</strong> ComputerApplications (0975 – 8887) Volume 66– No.22,March 2013[14] Sherali Zeadally · Ray Hunt · Yuh-Shyan Chen ·Angela Irw<strong>in</strong> · Aamir Hassan “<strong>Vehicular</strong> ad hoc<strong>network</strong>s (VANETS): status, results, and challenges”© Spr<strong>in</strong>ger Science+Bus<strong>in</strong>ess Media, LLC 2010Volume 2, Issue 2 March – April 2013 Page 377