Countering Selfish Misbehavior in Multi-channel MAC Protocols
Countering Selfish Misbehavior in Multi-channel MAC Protocols
Countering Selfish Misbehavior in Multi-channel MAC Protocols
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
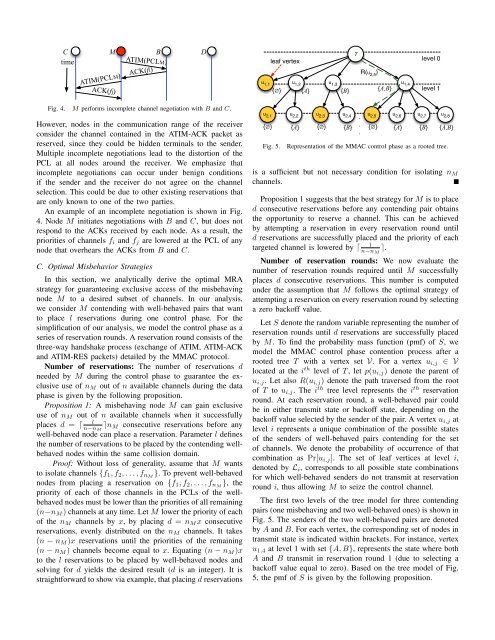
C M B DtimeATIM(PCLM)ACK(fj)ATIM(PCLM)ACK(fi)Fig. 4. M performs <strong>in</strong>complete <strong>channel</strong> negotiation with B and C.However, nodes <strong>in</strong> the communication range of the receiverconsider the <strong>channel</strong> conta<strong>in</strong>ed <strong>in</strong> the ATIM-ACK packet asreserved, s<strong>in</strong>ce they could be hidden term<strong>in</strong>als to the sender.<strong>Multi</strong>ple <strong>in</strong>complete negotiations lead to the distortion of thePCL at all nodes around the receiver. We emphasize that<strong>in</strong>complete negotiations can occur under benign conditionsif the sender and the receiver do not agree on the <strong>channel</strong>selection. This could be due to other exist<strong>in</strong>g reservations thatare only known to one of the two parties.An example of an <strong>in</strong>complete negotiation is shown <strong>in</strong> Fig.4. Node M <strong>in</strong>itiates negotiations with B and C, but does notrespond to the ACKs received by each node. As a result, thepriorities of <strong>channel</strong>s f i and f j are lowered at the PCL of anynode that overhears the ACKs from B and C.C. Optimal <strong>Misbehavior</strong> StrategiesIn this section, we analytically derive the optimal MRAstrategy for guarantee<strong>in</strong>g exclusive access of the misbehav<strong>in</strong>gnode M to a desired subset of <strong>channel</strong>s. In our analysis,we consider M contend<strong>in</strong>g with well-behaved pairs that wantto place l reservations dur<strong>in</strong>g one control phase. For thesimplification of our analysis, we model the control phase as aseries of reservation rounds. A reservation round consists of thethree-way handshake process (exchange of ATIM, ATIM-ACKand ATIM-RES packets) detailed by the M<strong>MAC</strong> protocol.Number of reservations: The number of reservations dneeded by M dur<strong>in</strong>g the control phase to guarantee the exclusiveuse of n M out of n available <strong>channel</strong>s dur<strong>in</strong>g the dataphase is given by the follow<strong>in</strong>g proposition.Proposition 1: A misbehav<strong>in</strong>g node M can ga<strong>in</strong> exclusiveuse of n M out of n available <strong>channel</strong>s when it successfullylplaces d = ⌈n−n M⌉n M consecutive reservations before anywell-behaved node can place a reservation. Parameter l def<strong>in</strong>esthe number of reservations to be placed by the contend<strong>in</strong>g wellbehavednodes with<strong>in</strong> the same collision doma<strong>in</strong>.Proof: Without loss of generality, assume that M wantsto isolate <strong>channel</strong>s {f 1 , f 2 , . . . , f nM }. To prevent well-behavednodes from plac<strong>in</strong>g a reservation on {f 1 , f 2 , . . . , f nM }, thepriority of each of those <strong>channel</strong>s <strong>in</strong> the PCLs of the wellbehavednodes must be lower than the priorities of all rema<strong>in</strong><strong>in</strong>g(n−n M ) <strong>channel</strong>s at any time. Let M lower the priority of eachof the n M <strong>channel</strong>s by x, by plac<strong>in</strong>g d = n M x consecutivereservations, evenly distributed on the n M <strong>channel</strong>s. It takes(n − n M )x reservations until the priorities of the rema<strong>in</strong><strong>in</strong>g(n − n M ) <strong>channel</strong>s become equal to x. Equat<strong>in</strong>g (n − n M )xto the l reservations to be placed by well-behaved nodes andsolv<strong>in</strong>g for d yields the desired result (d is an <strong>in</strong>teger). It isstraightforward to show via example, that plac<strong>in</strong>g d reservationsTleaf vertexlevel 0R(u 2,5)u 1,1 u 1,2 u 1,3 u 1,4{∅} {A} {B} {A,B}level 1u 2,1 u 2,2 u 2,3 u 2,4 u 2,5 u 2,6 u 2,7 u 2,8.{∅} {A} {∅} {B}..{∅}Fig. 5.{A}{B}{A,B}Representation of the M<strong>MAC</strong> control phase as a rooted tree.is a sufficient but not necessary condition for isolat<strong>in</strong>g n M<strong>channel</strong>s.Proposition 1 suggests that the best strategy for M is to placed consecutive reservations before any contend<strong>in</strong>g pair obta<strong>in</strong>sthe opportunity to reserve a <strong>channel</strong>. This can be achievedby attempt<strong>in</strong>g a reservation <strong>in</strong> every reservation round untild reservations are successfully placed and the priority of eachtargeted <strong>channel</strong> is lowered by ⌈n−n M⌉.Number of reservation rounds: We now evaluate thenumber of reservation rounds required until M successfullyplaces d consecutive reservations. This number is computedunder the assumption that M follows the optimal strategy ofattempt<strong>in</strong>g a reservation on every reservation round by select<strong>in</strong>ga zero backoff value.Let S denote the random variable represent<strong>in</strong>g the number ofreservation rounds until d reservations are successfully placedby M. To f<strong>in</strong>d the probability mass function (pmf) of S, wemodel the M<strong>MAC</strong> control phase contention process after arooted tree T with a vertex set V. For a vertex u i,j ∈ Vlocated at the i th level of T , let p(u i,j ) denote the parent ofu i,j . Let also R(u i,j ) denote the path traversed from the rootof T to u i,j . The i th tree level represents the i th reservationround. At each reservation round, a well-behaved pair couldbe <strong>in</strong> either transmit state or backoff state, depend<strong>in</strong>g on thebackoff value selected by the sender of the pair. A vertex u i,j atlevel i represents a unique comb<strong>in</strong>ation of the possible statesof the senders of well-behaved pairs contend<strong>in</strong>g for the setof <strong>channel</strong>s. We denote the probability of occurrence of thatcomb<strong>in</strong>ation as Pr[u i,j ]. The set of leaf vertices at level i,denoted by L i , corresponds to all possible state comb<strong>in</strong>ationsfor which well-behaved senders do not transmit at reservationround i, thus allow<strong>in</strong>g M to seize the control <strong>channel</strong>.The first two levels of the tree model for three contend<strong>in</strong>gpairs (one misbehav<strong>in</strong>g and two well-behaved ones) is shown <strong>in</strong>Fig. 5. The senders of the two well-behaved pairs are denotedby A and B. For each vertex, the correspond<strong>in</strong>g set of nodes <strong>in</strong>transmit state is <strong>in</strong>dicated with<strong>in</strong> brackets. For <strong>in</strong>stance, vertexu 1,4 at level 1 with set {A, B}, represents the state where bothA and B transmit <strong>in</strong> reservation round 1 (due to select<strong>in</strong>g abackoff value equal to zero). Based on the tree model of Fig.5, the pmf of S is given by the follow<strong>in</strong>g proposition.l