* Encode-and-hash P <strong>in</strong>to an <strong>in</strong>teger I [24] andcompute F1 = C -I mod r.. Discard the message if the redundancy of F1 is<strong>in</strong>correct.. Otherwise accept M1 (obta<strong>in</strong>ed from F1) and thesignature and reconstruct M |ttUID = M1 IM2.User Revocation/Addition: To revoke a <strong>user</strong>, sayUIDj, the s<strong>in</strong>k follows the steps below:* First, it hashes h, (UIDj PKUD)= i and decreasesvi by 1. It repeats this operation for all hl, I E [1, k].. From the updated count<strong>in</strong>g Bloom filter V, the s<strong>in</strong>kobta<strong>in</strong>s the correspond<strong>in</strong>g updated Bloom filter V'with V' = v'v ...vl_,. Here, v' = 1 only whenvi > 1, and vl = 0 otherwise.* The s<strong>in</strong>k further calculates VA = V' (DV and deletesV afterwards. Here D denotes bitwise exclusiveOR operation. Obviously, VA is an m-bit vectorwith at most k bits set to 1. Hence, VA can besimply represented by enumerat<strong>in</strong>g its 1-valued bits,requir<strong>in</strong>g k [log2 m] bits for <strong>in</strong>dex<strong>in</strong>g (k < k). Thisrepresentation is efficient for a small k as will beanalyzed <strong>in</strong> Section VI.B.. The s<strong>in</strong>k f<strong>in</strong>ally broadcasts VA after sign<strong>in</strong>g it. Themessage format follows (III) but with the s<strong>in</strong>k'spublic key omitted, as every sensor already has it.. Upon receiv<strong>in</strong>g and successfully authenticat<strong>in</strong>g thebroadcast message, every sensor node updates itsown Bloom filter accord<strong>in</strong>gly, that is, if vA,i = 1,then vi = 0, i C [0, m-1].BAS also supports simultaneous multi<strong>user</strong> revocation.Suppose that Nrev <strong>user</strong>s are revoked simultaneously.The s<strong>in</strong>k follows the same manner to construct VAwith k bits set 1. Now we have k < kNrev. Furthermore,the compressed message for represent<strong>in</strong>g VA nowcould achieve mH(p) bits theoretically, where H(p) =p log2 p -(1 p)log2 (1 -p) is the entropy functionand p = (1 - k is the probability of each bit be<strong>in</strong>g 0<strong>in</strong> VA. As po<strong>in</strong>ted out <strong>in</strong> [23], us<strong>in</strong>g arithmetic cod<strong>in</strong>gtechnique can efficiently approach this lower bound.BAS supports dynamic <strong>user</strong> addition <strong>in</strong> two ways.First, it enables a later b<strong>in</strong>d<strong>in</strong>g of network <strong>user</strong>s and their(ID, public key) pairs. In this approach, the s<strong>in</strong>k maygenerate more (ID, public key) pairs than needed dur<strong>in</strong>gsystem preparation. When a new network <strong>user</strong> jo<strong>in</strong>s theWSN, it will be assigned an unused ID and public keypair by the s<strong>in</strong>k. Second, BAS could add new network<strong>user</strong>s after the revocation of old members. This approach,however, could only add the same number of new <strong>user</strong>sas that of the revoked. This requirement ensures that theFig. 3. The m<strong>in</strong>imum probability of a false positive regard<strong>in</strong>g mprobability of a false positive never <strong>in</strong>creases <strong>in</strong> BAS.To do so, the s<strong>in</strong>k updates its count<strong>in</strong>g Bloom filterby hash<strong>in</strong>g the new <strong>user</strong>'s <strong>in</strong>formation <strong>in</strong>to the currentBloom filter. The s<strong>in</strong>k then obta<strong>in</strong>s a VA <strong>in</strong> the sameway as <strong>in</strong> the revocation case, and broadcasts it aftercompression. This time, if vA,i = 1, sensor nodes willset vi = 1, i c [0, m- 1] to update their current Bloomfilters.B. M<strong>in</strong>imize the Probability of a False PositiveS<strong>in</strong>ce the Bloom filter provides probabilistic membershipverification only, it is important to make sure thatthe probability of a false positive is as small as possible.Theorem 1: Given the number of network <strong>user</strong>s Nand the storage space m bits for a s<strong>in</strong>gle Bloom filter,the m<strong>in</strong>imum probability of a false positive f that canbe achieved is 2 with k I<strong>in</strong> 2. that is,f(0.6185) NProof: s<strong>in</strong>ce f = (1-(1 )N)k (1_ ewe then have f = ekln( e_-k/m ). Let g =e-kNl<strong>in</strong>). Hence, m<strong>in</strong>imiz<strong>in</strong>g f is equivalentmiz<strong>in</strong>g g with respect to k. We f<strong>in</strong>d-kNITn)kkln(ltom<strong>in</strong>idln( ekNm)+ kN e-kNImdk m 1 - -kN1mIt is easy to check that the derivative is 0 when k<strong>in</strong>In 2. And it is not hard to show that this is a globalm<strong>in</strong>imum [23]. Note that <strong>in</strong> practice, k must be an<strong>in</strong>teger.D.w 9k. .n /N)h2Fig. 3 shows the probability of a false positive f asa function of TN' i.e., bits per element. We see that fdecreases sharply as Tn <strong>in</strong>creases. When NN~~~N <strong>in</strong>creasesfrom 8 to 96 bits, f decreases from 2.1 * 10-2 to9.3 *10-21. Obviously, f determ<strong>in</strong>es the security strengthof our design. For example, when Tn 92 bits, theadversary has to generate around 263.8 public/private keypairs on average before f<strong>in</strong>d<strong>in</strong>g a valid one to pass theBloom filter. This is almost computationally <strong>in</strong>feasible,228
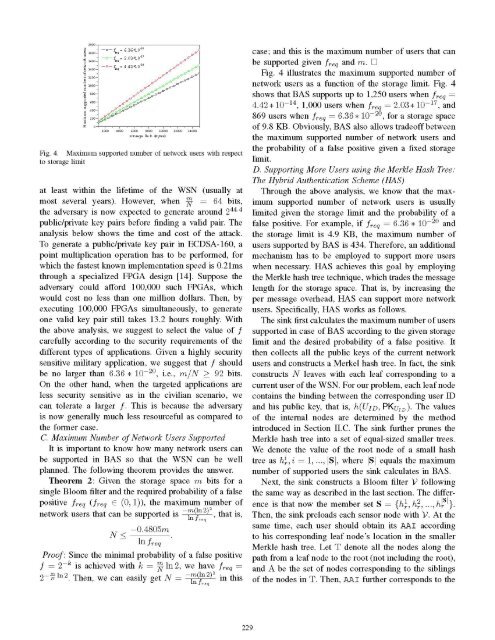
u-DO -Do -f 6636*10leq,'- f = 2.03*-7,f°ie= 4.4210o(C,DO*- C/Do-'-" ;DO-Fig. 4. Maximum supported number of network <strong>user</strong>s with respectto storage limitat least with<strong>in</strong> the lifetime of the WSN (usually atmost several years). However, when mN 64 bits,the adversary is now expected to generate around 244.4public/private key pairs before f<strong>in</strong>d<strong>in</strong>g a valid pair. Theanalysis below shows the time and cost of the attack.To generate a public/private key pair <strong>in</strong> ECDSA-160, apo<strong>in</strong>t multiplication operation has to be performed, forwhich the fastest known implementation speed is 0.21msthrough a specialized FPGA design [14]. Suppose theadversary could afford 100,000 such FPGAs, whichwould cost no less than one million dollars. Then, byexecut<strong>in</strong>g 100,000 FPGAs simultaneously, to generateone valid key pair still takes 13.2 hours roughly. Withthe above analysis, we suggest to select the value of fcarefully accord<strong>in</strong>g to the security requirements of thedifferent types of applications. Given a highly securitysensitive military application, we suggest that f shouldbe no larger than 6.36 * 10-20, i.e., m/N > 92 bits.On the other hand, when the targeted applications areless security sensitive as <strong>in</strong> the civilian scenario, wecan tolerate a larger f. This is because the adversaryis now generally much less resourceful as compared tothe former case.C. Maximum Number of Network Users SupportedIt is important to know how many network <strong>user</strong>s canbe supported <strong>in</strong> BAS so that the WSN can be wellplanned. The follow<strong>in</strong>g theorem provides the answer.Theorem 2: Given the storage space m bits for as<strong>in</strong>gle Bloom filter and the required probability of a falsepositive freq (freq C (0,1)), the maximum number ofnetwork <strong>user</strong>s that can be supported is m (In 2)2, that is,In f,,qN