- Page 2 and 3:
Voice over 802.11
- Page 4 and 5:
Voice over 802.11Frank OhrtmanArtec
- Page 6:
To Michelle Otte
- Page 9 and 10:
viii Voice over 802.11MIB 17DCF 18P
- Page 11 and 12:
x Voice over 802.116 Vo802.11: Rang
- Page 13 and 14:
xii Voice over 802.11Factors Affect
- Page 15 and 16:
xiv Voice over 802.11Web Provisioni
- Page 17 and 18:
1Overview of Vo802.11An understandi
- Page 19 and 20:
Overview of Vo802.11 3technology sp
- Page 21 and 22:
2802.11: Alternative AccessWhat, te
- Page 23 and 24:
802.11: Alternative Access 7comply
- Page 25 and 26:
802.11: Alternative Access 9Applica
- Page 27 and 28:
802.11: Alternative Access 11the 2.
- Page 29 and 30:
802.11: Alternative Access 13(CDMA)
- Page 31 and 32:
802.11: Alternative Access 15Table
- Page 33 and 34:
802.11: Alternative Access 17Table
- Page 35 and 36:
802.11: Alternative Access 19multip
- Page 37 and 38:
802.11: Alternative Access 21connec
- Page 39 and 40:
802.11: Alternative Access 23networ
- Page 41 and 42:
3Voice over Internet ProtocolWhat I
- Page 43 and 44:
Voice over Internet Protocol 27smal
- Page 45 and 46:
Voice over Internet Protocol 29chan
- Page 47 and 48:
Voice over Internet Protocol 31in t
- Page 49 and 50:
Voice over Internet Protocol 33Tabl
- Page 51 and 52:
Voice over Internet Protocol 35call
- Page 53 and 54:
Voice over Internet Protocol 37MCUs
- Page 55 and 56:
Voice over Internet Protocol 39In t
- Page 57 and 58:
Voice over Internet Protocol 41of a
- Page 59 and 60:
Voice over Internet Protocol 43comm
- Page 61 and 62:
Voice over Internet Protocol 45Dela
- Page 63 and 64:
Voice over Internet Protocol 47•
- Page 65 and 66:
4Switching TDM and VoIP NetworksAs
- Page 67 and 68:
Switching TDM and VoIP Networks 518
- Page 69 and 70: Switching TDM and VoIP Networks 53T
- Page 71 and 72: Switching TDM and VoIP Networks 55T
- Page 73 and 74: Switching TDM and VoIP Networks 57a
- Page 75 and 76: Switching TDM and VoIP Networks 59c
- Page 77 and 78: Switching TDM and VoIP Networks 61A
- Page 79 and 80: Switching TDM and VoIP Networks 63M
- Page 81 and 82: Switching TDM and VoIP Networks 65T
- Page 83 and 84: Switching TDM and VoIP Networks 67A
- Page 85 and 86: Switching TDM and VoIP Networks 69o
- Page 87 and 88: Switching TDM and VoIP Networks 71C
- Page 89 and 90: Switching TDM and VoIP Networks 73i
- Page 91 and 92: Switching TDM and VoIP Networks 75S
- Page 93 and 94: 5Objections to Vo802.11To properly
- Page 95 and 96: Objections to Vo802.11 79Objections
- Page 97: Objections to Vo802.11 81References
- Page 100 and 101: 84 Voice over 802.11stretch the ran
- Page 102 and 103: 86 Voice over 802.11that area, the
- Page 104 and 105: 88 Voice over 802.11wireless wide-a
- Page 106 and 107: 90 Voice over 802.11As a high-frequ
- Page 108 and 109: 92 Voice over 802.11XNormaltrafficf
- Page 110 and 111: 94 Voice over 802.11Second, when en
- Page 112 and 113: 96 Voice over 802.11References[1] O
- Page 114 and 115: 98 Voice over 802.11security [1]. T
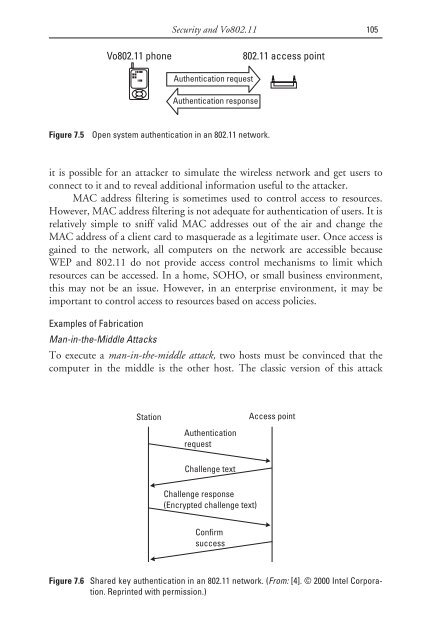
- Page 116 and 117: 100 Voice over 802.11MAC Address Fi
- Page 118 and 119: ❘❙❚❘❙❚❘❙❚❘❙
- Page 122 and 123: 106 Voice over 802.11occurs when an
- Page 124 and 125: ❘❙❚❘❙❚❘❙❚❘❙
- Page 126 and 127: ❘❙❚❘❙❚❘❙❚❘❙
- Page 128 and 129: ❘❙❚❘❙❚❘❙❚❘❙
- Page 130 and 131: 114 Voice over 802.11Table 7.2A Ran
- Page 132 and 133: 116 Voice over 802.11EAP-TLS, passw
- Page 134 and 135: 118 Voice over 802.11RADIUS servers
- Page 136 and 137: 120 Voice over 802.11port authentic
- Page 138 and 139: 122 Voice over 802.11IPsecIPsec VPN
- Page 140 and 141: 124 Voice over 802.11How Kerberos W
- Page 142 and 143: 126 Voice over 802.11military intel
- Page 145 and 146: 8Objections Due to Interference and
- Page 147 and 148: Objections Due to Interference and
- Page 149 and 150: Objections Due to Interference and
- Page 151 and 152: Objections Due to Interference and
- Page 153 and 154: Objections Due to Interference and
- Page 155 and 156: Objections Due to Interference and
- Page 157 and 158: Objections Due to Interference and
- Page 159 and 160: Objections Due to Interference and
- Page 161 and 162: Objections Due to Interference and
- Page 163 and 164: Station 1Station 2Station 3Station
- Page 165 and 166: Objections Due to Interference and
- Page 167 and 168: Objections Due to Interference and
- Page 169 and 170: Objections Due to Interference and
- Page 171 and 172:
9Engineering Vo802.11 Networks forM
- Page 173 and 174:
Engineering Vo802.11 Networks for M
- Page 175 and 176:
Engineering Vo802.11 Networks for M
- Page 177 and 178:
Engineering Vo802.11 Networks for M
- Page 179 and 180:
Engineering Vo802.11 Networks for M
- Page 181 and 182:
Engineering Vo802.11 Networks for M
- Page 183 and 184:
Engineering Vo802.11 Networks for M
- Page 185 and 186:
Engineering Vo802.11 Networks for M
- Page 187 and 188:
10Scalability in Wireless VoIP Netw
- Page 189 and 190:
Scalability in Wireless VoIP Networ
- Page 191 and 192:
Scalability in Wireless VoIP Networ
- Page 193 and 194:
Scalability in Wireless VoIP Networ
- Page 195 and 196:
Scalability in Wireless VoIP Networ
- Page 197 and 198:
Scalability in Wireless VoIP Networ
- Page 199 and 200:
11Vo802.11 ReliabilityA recurring o
- Page 201 and 202:
Vo802.11 Reliability 185Table 11.2T
- Page 203 and 204:
Vo802.11 Reliability 187A Vo802.11
- Page 205 and 206:
BackofficesystemBackofficesystemBac
- Page 207 and 208:
Vo802.11 Reliability 191network ava
- Page 209 and 210:
12Vo802.11 Features and Application
- Page 211 and 212:
Vo802.11 Features and Applications
- Page 213 and 214:
Vo802.11 Features and Applications
- Page 215 and 216:
Vo802.11 Features and Applications
- Page 217 and 218:
Vo802.11 Features and Applications
- Page 219 and 220:
Vo802.11 Features and Applications
- Page 221:
Vo802.11 Features and Applications
- Page 224 and 225:
208 Voice over 802.11Spectrum is ma
- Page 226 and 227:
210 Voice over 802.11Table 13.1Spec
- Page 228 and 229:
212 Voice over 802.11out there. Loo
- Page 230 and 231:
214 Voice over 802.11Laws on Antenn
- Page 232 and 233:
216 Voice over 802.11particularly b
- Page 234 and 235:
218 Voice over 802.11was compatible
- Page 236 and 237:
220 Voice over 802.11Vo802.11 as Pa
- Page 238 and 239:
222 Voice over 802.11The countless
- Page 240 and 241:
224 Voice over 802.11Vo802.11 deplo
- Page 242 and 243:
226 Voice over 802.11Table 14.3Cost
- Page 244 and 245:
228 Voice over 802.11Cost Savings w
- Page 246 and 247:
230 Voice over 802.11Table 14.9Cost
- Page 249 and 250:
15Conclusion: Vo802.11 Is the Futur
- Page 251 and 252:
Conclusion: Vo802.11 Is the Future
- Page 253 and 254:
Conclusion: Vo802.11 Is the Future
- Page 255 and 256:
Conclusion: Vo802.11 Is the Future
- Page 257 and 258:
Conclusion: Vo802.11 Is the Future
- Page 259 and 260:
Conclusion: Vo802.11 Is the Future
- Page 261:
Conclusion: Vo802.11 Is the Future
- Page 265 and 266:
Index802.11. See IEEE 802.11Access,
- Page 267 and 268:
Index 251Distributed coordination f
- Page 269 and 270:
Index 253examples, 101-3illustrated
- Page 271 and 272:
Index 255Power limits, 208-9point-t
- Page 273 and 274:
Index 257direct sequence (DSSS), 6,
- Page 275 and 276:
Recent Titles in the Artech HouseTe
- Page 277 and 278:
Performance Evaluation of Communica