Security Jiujitsu
conf2015_DVeuve_Splunk_SecurityCompliance_SecurityJiujitsuBuildingCorrelation
conf2015_DVeuve_Splunk_SecurityCompliance_SecurityJiujitsuBuildingCorrelation
- No tags were found...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
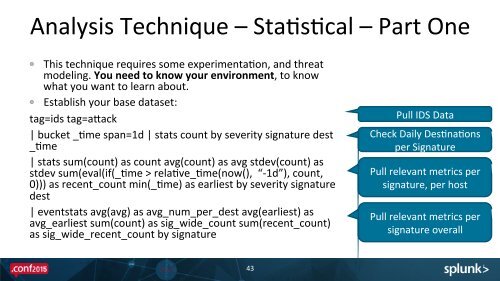
Analysis Technique – StaEsEcal – Part One <br />
This technique requires some experimentaEon, and threat <br />
modeling. You need to know your environment, to know <br />
what you want to learn about. <br />
Establish your base dataset: <br />
tag=ids tag=auack <br />
| bucket _Eme span=1d | stats count by severity signature dest <br />
_Eme <br />
| stats sum(count) as count avg(count) as avg stdev(count) as <br />
stdev sum(eval(if(_Eme > relaEve_Eme(now(), “-‐1d”), count, <br />
0))) as recent_count min(_Eme) as earliest by severity signature <br />
dest <br />
| eventstats avg(avg) as avg_num_per_dest avg(earliest) as <br />
avg_earliest sum(count) as sig_wide_count sum(recent_count) <br />
as sig_wide_recent_count by signature <br />
Pull IDS Data <br />
Check Daily DesEnaEons <br />
per Signature <br />
Pull relevant metrics per <br />
signature, per host <br />
Pull relevant metrics per <br />
signature overall <br />
43