Intel SGX Enclave Support in Windows 10 Fall Update (Threshold 2)
1ks6upt
1ks6upt
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
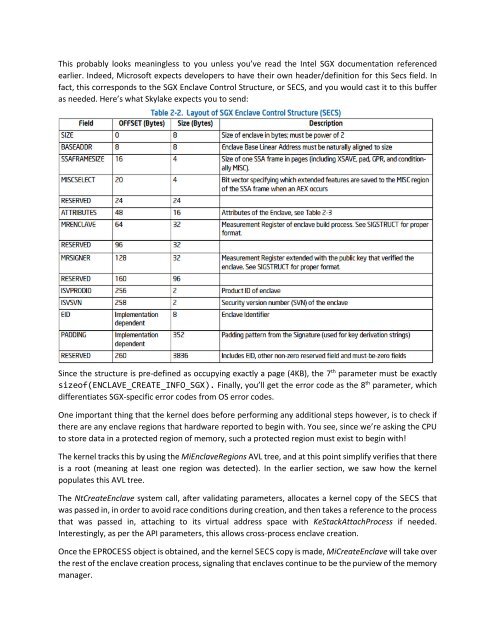
This probably looks mean<strong>in</strong>gless to you unless you’ve read the <strong>Intel</strong> <strong>SGX</strong> documentation referenced<br />
earlier. Indeed, Microsoft expects developers to have their own header/def<strong>in</strong>ition for this Secs field. In<br />
fact, this corresponds to the <strong>SGX</strong> <strong>Enclave</strong> Control Structure, or SECS, and you would cast it to this buffer<br />
as needed. Here’s what Skylake expects you to send:<br />
S<strong>in</strong>ce the structure is pre-def<strong>in</strong>ed as occupy<strong>in</strong>g exactly a page (4KB), the 7 th parameter must be exactly<br />
sizeof(ENCLAVE_CREATE_INFO_<strong>SGX</strong>). F<strong>in</strong>ally, you’ll get the error code as the 8 th parameter, which<br />
differentiates <strong>SGX</strong>-specific error codes from OS error codes.<br />
One important th<strong>in</strong>g that the kernel does before perform<strong>in</strong>g any additional steps however, is to check if<br />
there are any enclave regions that hardware reported to beg<strong>in</strong> with. You see, s<strong>in</strong>ce we’re ask<strong>in</strong>g the CPU<br />
to store data <strong>in</strong> a protected region of memory, such a protected region must exist to beg<strong>in</strong> with!<br />
The kernel tracks this by us<strong>in</strong>g the Mi<strong>Enclave</strong>Regions AVL tree, and at this po<strong>in</strong>t simplify verifies that there<br />
is a root (mean<strong>in</strong>g at least one region was detected). In the earlier section, we saw how the kernel<br />
populates this AVL tree.<br />
The NtCreate<strong>Enclave</strong> system call, after validat<strong>in</strong>g parameters, allocates a kernel copy of the SECS that<br />
was passed <strong>in</strong>, <strong>in</strong> order to avoid race conditions dur<strong>in</strong>g creation, and then takes a reference to the process<br />
that was passed <strong>in</strong>, attach<strong>in</strong>g to its virtual address space with KeStackAttachProcess if needed.<br />
Interest<strong>in</strong>gly, as per the API parameters, this allows cross-process enclave creation.<br />
Once the EPROCESS object is obta<strong>in</strong>ed, and the kernel SECS copy is made, MiCreate<strong>Enclave</strong> will take over<br />
the rest of the enclave creation process, signal<strong>in</strong>g that enclaves cont<strong>in</strong>ue to be the purview of the memory<br />
manager.