- Page 2 and 3: DDoS Attacks: End-to-End Mitigation
- Page 4 and 5: Agenda • Introduction, DDoS Attac
- Page 6 and 7: Introduction • Do we still need t
- Page 8 and 9: Largest DDOS Attack in History 8
- Page 10 and 11: ATLAS Initiative: Attack Sizes "Las
- Page 12 and 13: DDoS Mitigation Mitigation implies
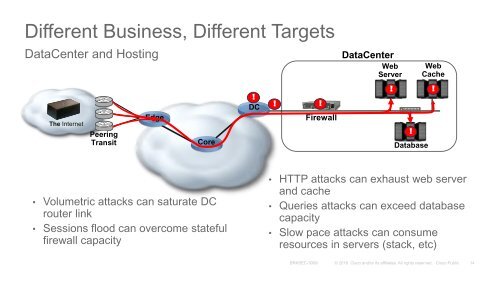
- Page 16 and 17: Different Business, Different Targe
- Page 18 and 19: Deployment Models In-the-Cloud / On
- Page 20 and 21: In-the-Cloud Services DNS-based DDo
- Page 22 and 23: In-the-Cloud Services DNS-based DDo
- Page 24 and 25: In-the-Cloud Services DNS-based DDo
- Page 26 and 27: In-the-Cloud Services DNS-based DDo
- Page 28 and 29: In-the-Cloud Services DNS-based DDo
- Page 30 and 31: In-the-Cloud Services DNS-based DDo
- Page 32 and 33: In-the-Cloud Services DNS-based DDo
- Page 34 and 35: In-the-Cloud Services DNS-based DDo
- Page 36 and 37: In-the-Cloud Services BGP-based “
- Page 38 and 39: In-the-Cloud Services BGP-based “
- Page 40 and 41: In-the-Cloud Services BGP-based “
- Page 42 and 43: In-the-Cloud Services BGP-based “
- Page 44 and 45: In-the-Cloud Services BGP-based “
- Page 46 and 47: In-the-Cloud Services DDoS Mitigati
- Page 48 and 49: On-Premises: Centralized vs Distrib
- Page 50 and 51: On-Premises: Centralized vs Distrib
- Page 52 and 53: Attack Detection: In-line Inspectio
- Page 54 and 55: Protecting your Infrastructure Infr
- Page 56 and 57: Introducing BGP FlowSpec 56
- Page 58 and 59: BGP FlowSpec Matching Criteria and
- Page 60 and 61: Amplification Attacks • Specific
- Page 62 and 63: Mitigating Amplification Attacks Se
- Page 64 and 65:
Mitigating L3 / L4 Stateless Volume
- Page 66 and 67:
Mitigating L3 / L4 Stateless Volume
- Page 68 and 69:
Mitigating SYN floods, HTTP, SSL an
- Page 70 and 71:
Mitigating SYN floods, HTTP, SSL an
- Page 72 and 73:
Mitigating SYN floods, HTTP and SSL
- Page 74 and 75:
Particular Case of Residential Subs
- Page 76 and 77:
Slow Pace Attacks DC and Enterprise
- Page 78 and 79:
Partnership • Cisco established p
- Page 80 and 81:
Arbor SP solution Portfolio Arbor N
- Page 82 and 83:
Arbor SP solution: Cisco vDDoS Prot
- Page 84 and 85:
Arbor SP solution Deployment and Us
- Page 86 and 87:
Demo 86
- Page 88 and 89:
Cisco Partnerships Radware DefenseP
- Page 90 and 91:
Understand 9300 Radware DDoS Soluti
- Page 92 and 93:
Security Services Architecture on F
- Page 94 and 95:
Demo 94
- Page 96 and 97:
Behavioral DOS - Network baselining
- Page 98 and 99:
BDOS Detection and Mitigation of a
- Page 100 and 101:
BDOS Detection and Mitigation of a
- Page 102 and 103:
Configuration Define Global Options
- Page 104 and 105:
Configuration Define Global Options
- Page 106 and 107:
BDOS Profile Three main tabs - •
- Page 108 and 109:
BDOS Profile Three main tabs - •
- Page 110 and 111:
BDOS Profile Three main tabs - •
- Page 112 and 113:
BDOS Profile Three main tabs - •
- Page 114 and 115:
DNS Mitigation Attack Escalation Bo
- Page 116 and 117:
DNS Mitigation Attack Escalation Bo
- Page 118 and 119:
DNS Mitigation Attack Escalation Bo
- Page 120 and 121:
SYN Flood Protection is adaptive Us
- Page 122 and 123:
Conclusion 122
- Page 124 and 125:
End-to-End Mitigation Summary • A
- Page 126 and 127:
End-to-End Mitigation Summary • S
- Page 128 and 129:
End-to-End Mitigation • Cisco off
- Page 130 and 131:
Complete Your Online Session Evalua
- Page 133 and 134:
VSM Internal Architecture SFP+ SFP+
- Page 135 and 136:
Enterprise Perimeter Protection Use
- Page 137 and 138:
Service Provider: Service Center DC