$hell on Earth
shell-on-earth
shell-on-earth
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
Microsoft Edge Vulnerability to Kernel Executi<strong>on</strong> by<br />
Tencent Security Team Sniper<br />
Team Sniper’s chain was composed of an out-of-bounds access vulnerability exploited in Microsoft Edge,<br />
chained with a kernel exploit that achieved local privilege escalati<strong>on</strong>.<br />
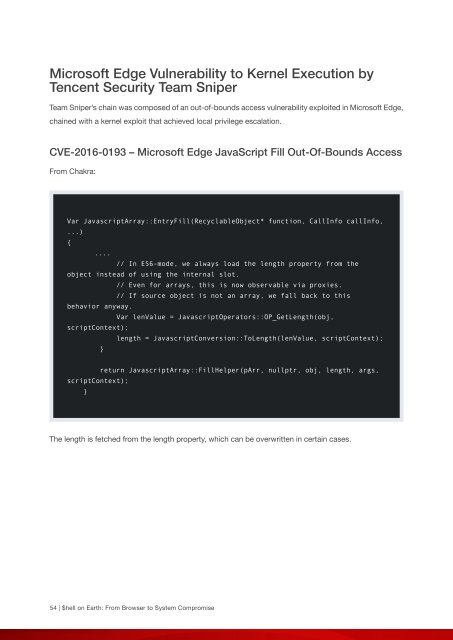
CVE-2016-0193 – Microsoft Edge JavaScript Fill Out-Of-Bounds Access<br />
From Chakra:<br />
Var JavascriptArray::EntryFill(RecyclableObject* functi<strong>on</strong>, CallInfo callInfo,<br />
...)<br />
{<br />
....<br />
// In ES6-mode, we always load the length property from the<br />
object instead of using the internal slot.<br />
// Even for arrays, this is now observable via proxies.<br />
// If source object is not an array, we fall back to this<br />
behavior anyway.<br />
Var lenValue = JavascriptOperators::OP_GetLength(obj,<br />
scriptC<strong>on</strong>text);<br />
length = JavascriptC<strong>on</strong>versi<strong>on</strong>::ToLength(lenValue, scriptC<strong>on</strong>text);<br />
}<br />
return JavascriptArray::FillHelper(pArr, nullptr, obj, length, args,<br />
scriptC<strong>on</strong>text);<br />
}<br />
The length is fetched from the length property, which can be overwritten in certain cases.<br />
54 | <str<strong>on</strong>g>$hell</str<strong>on</strong>g> <strong>on</strong> <strong>Earth</strong>: From Browser to System Compromise