MONSOON – ANALYSIS OF AN APT CAMPAIGN
monsoon-analysis-apt-campaign?utm_source=Labs&utm_medium=blog&utm_content=monsoon_whitepaper&utm_campaign=monsoon
monsoon-analysis-apt-campaign?utm_source=Labs&utm_medium=blog&utm_content=monsoon_whitepaper&utm_campaign=monsoon
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
Forcepoint Security Labs | Special Investigations<br />
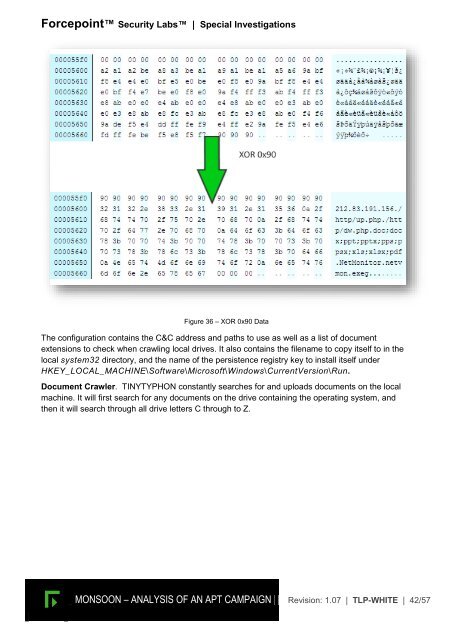
Figure 36 <strong>–</strong> XOR 0x90 Data<br />
The configuration contains the C&C address and paths to use as well as a list of document<br />
extensions to check when crawling local drives. It also contains the filename to copy itself to in the<br />
local system32 directory, and the name of the persistence registry key to install itself under<br />
HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run.<br />
Document Crawler. TINYTYPHON constantly searches for and uploads documents on the local<br />
machine. It will first search for any documents on the drive containing the operating system, and<br />
then it will search through all drive letters C through to Z.<br />
<strong>MONSOON</strong> <strong>–</strong> <strong><strong>AN</strong>ALYSIS</strong> <strong>OF</strong> <strong>AN</strong> <strong>APT</strong> <strong>CAMPAIGN</strong> Revision: 1.07 | TLP-WHITE | 42/57