MONSOON – ANALYSIS OF AN APT CAMPAIGN
2aWUb2X
2aWUb2X
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
Forcepoint Security Labs | Special Investigations<br />
No further commands were receive any after this.<br />
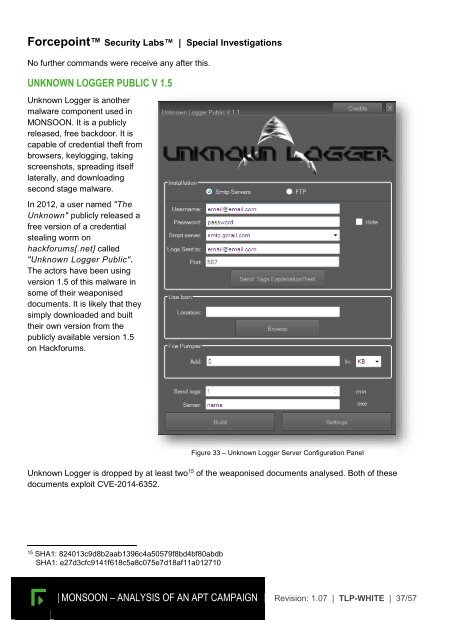
UNKNOWN LOGGER PUBLIC V 1.5<br />
Unknown Logger is another<br />
malware component used in<br />
<strong>MONSOON</strong>. It is a publicly<br />
released, free backdoor. It is<br />
capable of credential theft from<br />
browsers, keylogging, taking<br />
screenshots, spreading itself<br />
laterally, and downloading<br />
second stage malware.<br />
In 2012, a user named "The<br />
Unknown" publicly released a<br />
free version of a credential<br />
stealing worm on<br />
hackforums[.net] called<br />
"Unknown Logger Public".<br />
The actors have been using<br />
version 1.5 of this malware in<br />
some of their weaponised<br />
documents. It is likely that they<br />
simply downloaded and built<br />
their own version from the<br />
publicly available version 1.5<br />
on Hackforums.<br />
Figure 33 <strong>–</strong> Unknown Logger Server Configuration Panel<br />
Unknown Logger is dropped by at least two 15 of the weaponised documents analysed. Both of these<br />
documents exploit CVE-2014-6352.<br />
15<br />
SHA1: 824013c9d8b2aab1396c4a50579f8bd4bf80abdb<br />
SHA1: e27d3cfc9141f618c5a8c075e7d18af11a012710<br />
<strong>MONSOON</strong> <strong>–</strong> <strong><strong>AN</strong>ALYSIS</strong> <strong>OF</strong> <strong>AN</strong> <strong>APT</strong> <strong>CAMPAIGN</strong> Revision: 1.07 | TLP-WHITE | 37/57