MONSOON – ANALYSIS OF AN APT CAMPAIGN
2aWUb2X
2aWUb2X
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
Forcepoint Security Labs | Special Investigations<br />
SUMMARY <strong>OF</strong> OBSERVATIONS<br />
KEY FEATURES<br />
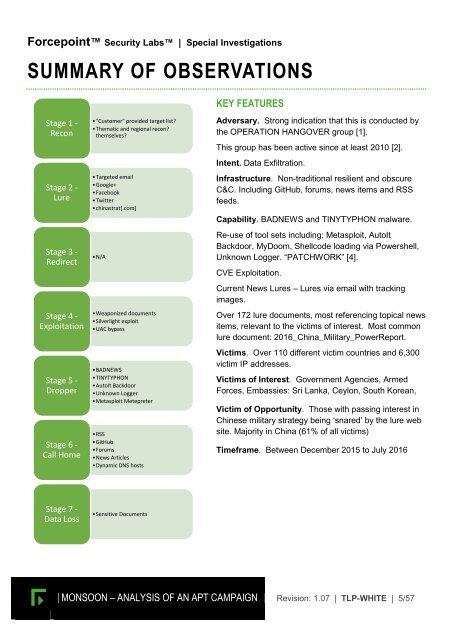
Stage 1 -<br />
Recon<br />
Stage 2 -<br />
Lure<br />
Stage 3 -<br />
Redirect<br />
Stage 4 -<br />
Exploitation<br />
Stage 5 -<br />
Dropper<br />
Stage 6 -<br />
Call Home<br />
•"Customer" provided target list?<br />
•Thematic and regional recon?<br />
themselves?<br />
•Targeted email<br />
•Google+<br />
•Facebook<br />
•Twitter<br />
•chinastrat[.com]<br />
•N/A<br />
•Weaponized documents<br />
•Silverlight exploit<br />
•UAC bypass<br />
•BADNEWS<br />
•TINYTYPHON<br />
•AutoIt Backdoor<br />
•Unknown Logger<br />
•Metasploit Metepreter<br />
•RSS<br />
•GitHub<br />
•Forums<br />
•News Articles<br />
•Dynamic DNS hosts<br />
Adversary. Strong indication that this is conducted by<br />
the OPERATION H<strong>AN</strong>GOVER group [1].<br />
This group has been active since at least 2010 [2].<br />
Intent. Data Exfiltration.<br />
Infrastructure. Non-traditional resilient and obscure<br />
C&C. Including GitHub, forums, news items and RSS<br />
feeds.<br />
Capability. BADNEWS and TINYTYPHON malware.<br />
Re-use of tool sets including: Metasploit, AutoIt<br />
Backdoor, MyDoom, Shellcode loading via Powershell,<br />
Unknown Logger. “PATCHWORK” [4].<br />
CVE Exploitation.<br />
Current News Lures <strong>–</strong> Lures via email with tracking<br />
images.<br />
Over 172 lure documents, most referencing topical news<br />
items, relevant to the victims of interest. Most common<br />
lure document: 2016_China_Military_PowerReport.<br />
Victims. Over 110 different victim countries and 6,300<br />
victim IP addresses.<br />
Victims of Interest. Government Agencies, Armed<br />
Forces, Embassies: Sri Lanka, Ceylon, South Korean,<br />
Victim of Opportunity. Those with passing interest in<br />
Chinese military strategy being ‘snared’ by the lure web<br />
site. Majority in China (61% of all victims)<br />
Timeframe. Between December 2015 to July 2016<br />
Stage 7 -<br />
Data Loss<br />
•Sensitive Documents<br />
<strong>MONSOON</strong> <strong>–</strong> <strong><strong>AN</strong>ALYSIS</strong> <strong>OF</strong> <strong>AN</strong> <strong>APT</strong> <strong>CAMPAIGN</strong> Revision: 1.07 | TLP-WHITE | 5/57