- Page 1 and 2:
SUSE Linux 10.1 April 07, 2006 Refe
- Page 3 and 4:
Contents About This Guide xi Part I
- Page 5 and 6:
8 Booting and Configuring a Linux S
- Page 7 and 8:
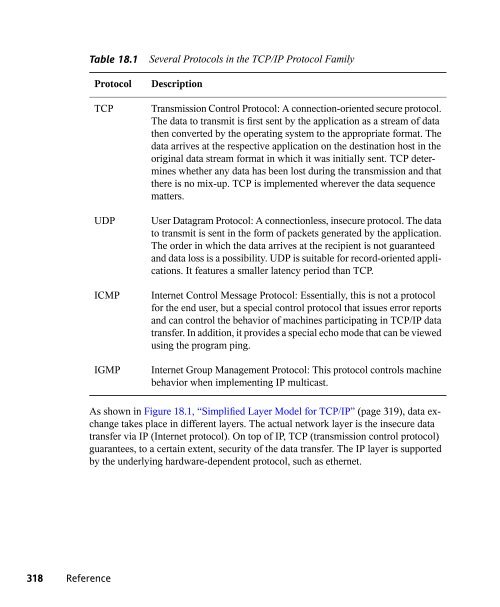
18.5 Managing Network Connections w
- Page 9 and 10:
29 The Proxy Server Squid 521 29.1
- Page 11 and 12:
About This Guide This manual gives
- Page 13:
• Dancing Penguins (Chapter Pengu
- Page 17 and 18:
Remote Installation SUSE Linux can
- Page 19 and 20:
3 When the boot screen of the targe
- Page 21 and 22:
1.1.3 Remote Installation via VNC
- Page 23 and 24:
• Valid static IP address to assi
- Page 25 and 26:
6 Finish the installation. 1.1.6 Re
- Page 27 and 28:
2 Start YaST → Miscellaneous →
- Page 29 and 30:
media over to this structure. Secon
- Page 31 and 32:
Announcing the NFS server via OpenS
- Page 33 and 34:
1.2.4 Manual Setup of an HTTP Insta
- Page 35 and 36:
7 Create a new folder under INSTALL
- Page 37 and 38:
# # "next server" defines the tftp
- Page 39 and 40:
1 Change to the directory of your i
- Page 41 and 42:
append initrd=initrd ramdisk_size=6
- Page 43 and 44:
Argument 5 Description Performs a l
- Page 45 and 46:
3 Open a terminal and enter the fol
- Page 47 and 48:
1.4.3 Using Custom Boot Options Usi
- Page 49 and 50:
Installation Scenario SSH—Dynamic
- Page 51 and 52:
To connect to the installation prog
- Page 53 and 54:
Advanced Disk Setup Sophisticated s
- Page 55 and 56:
etween different logical volumes ne
- Page 57 and 58:
If there are several volume groups,
- Page 59 and 60:
Figure 2.5 Creating Logical Volumes
- Page 61 and 62:
access is significantly faster in c
- Page 63 and 64:
Figure 2.7 File System Settings As
- Page 65 and 66:
Updating the System and Package Man
- Page 67 and 68:
a language and select Update in the
- Page 69 and 70:
• sysfs now complements the /proc
- Page 71 and 72:
(with different names). See the det
- Page 73 and 74:
Apache 1.3 Replaced with Apache 2 T
- Page 75 and 76:
3.2.2 From 9.1 to 9.2 Refer to the
- Page 77 and 78:
UTF-8. SUSE Linux offers standard t
- Page 79 and 80:
Old /usr/X11R6/bin/OOo-wrapper New
- Page 81 and 82:
The client configuration (/etc/krb5
- Page 83 and 84:
3.2.4 From 9.3 to 10.0 Refer to the
- Page 85 and 86:
File System Change Notification for
- Page 87 and 88:
TIP: Software Development Packages
- Page 89 and 90:
circumstances—impossible, even if
- Page 91 and 92:
The prepdeltarpm, writedeltarpm, an
- Page 93 and 94:
pm-4.1.1-191 wget-1.9.1-50 If only
- Page 95 and 96:
BUILD all the sources are unpacked,
- Page 97:
The build script offers a number of
- Page 101 and 102:
Security in Linux Masquerading and
- Page 103 and 104:
INPUT This chain is applied to pack
- Page 105 and 106:
server, for example, explicitly ope
- Page 107 and 108:
Figure 4.2 The YaST Firewall Config
- Page 109 and 110:
FW_DEV_INT (firewall, masquerading)
- Page 111 and 112:
that this would open all the user's
- Page 113 and 114:
4.2.5 The SSH Daemon (sshd)—Serve
- Page 115 and 116:
private keys for the duration of an
- Page 117 and 118:
Workstations In companies where alm
- Page 119 and 120:
Use vi -x filename to edit a new fi
- Page 121 and 122:
• apparmor-parser • libapparmor
- Page 123 and 124:
1 Determine the applications to pro
- Page 125 and 126:
3 Let AppArmor analyze the log file
- Page 127 and 128:
the cumbersome messages only useful
- Page 129 and 130:
4.5.1 Local Security and Network Se
- Page 131 and 132:
In the seventies, it was argued tha
- Page 133 and 134:
serious consequences, especially if
- Page 135 and 136:
tory by accident, you would not be
- Page 137 and 138:
DNS Poisoning DNS poisoning means t
- Page 139 and 140:
Finally, remember that it is import
- Page 141 and 142:
Access Control Lists in Linux POSIX
- Page 143 and 144:
5.2 Advantages of ACLs Traditionall
- Page 145 and 146:
Table 5.1 ACL Entry Types Type owne
- Page 147 and 148:
Before creating the directory, use
- Page 149 and 150:
The output of the getfacl confirms
- Page 151 and 152:
default:mask::r-x default:other::--
- Page 153 and 154:
System Monitoring Utilities A numbe
- Page 155 and 156:
grep 5674 tester 1u CHR 136,5 7 /de
- Page 157 and 158:
AENC 0 TrmIOP 0 Response Data Forma
- Page 159 and 160:
tester@linux:~> ps -p `pidof sshd`
- Page 161 and 162:
6.11 Kernel Ring Buffer: dmesg The
- Page 163 and 164:
NMI: 0 LOC: 0 ERR: 0 MIS: 0 Some of
- Page 165 and 166:
13476w nice : 0:02:20.91 0.9% page
- Page 167 and 168:
fstat64(3, {st_mode=S_IFREG|0755, s
- Page 169:
Entry point address: 0x8049b60 Star
- Page 173 and 174:
32-Bit and 64-Bit Applications in a
- Page 175 and 176:
Most Open Source programs use an au
- Page 177 and 178:
Booting and Configuring a Linux Sys
- Page 179 and 180:
during the entire boot process. Thi
- Page 181 and 182:
8.2 The init Process The program in
- Page 183 and 184:
telinit 0 or shutdown -h now The sy
- Page 185 and 186:
Option force-reload status Descript
- Page 187 and 188:
Example 8.1 A Minimal INIT INFO Blo
- Page 189 and 190:
This YaST dialog allows the selecti
- Page 191 and 192:
oth the current selection and the c
- Page 193 and 194:
The Boot Loader This chapter descri
- Page 195 and 196:
disks, CD drives, and DVD drives de
- Page 197 and 198:
The command root simplifies the spe
- Page 199 and 200:
timeout 8 After eight seconds witho
- Page 201 and 202:
Because the order of IDE, SCSI, and
- Page 203 and 204:
Error 32: Must be authenticated Pre
- Page 205 and 206:
NOTE: Custom Boot Loader If you wan
- Page 207 and 208:
9.3.5 Security Settings Using this
- Page 209 and 210:
3 Copy the kernel, the files stage2
- Page 211 and 212:
about the installation, configurati
- Page 213 and 214:
Special Features of SUSE Linux This
- Page 215 and 216:
A number of packages install shell
- Page 217 and 218:
10.1.5 The Command ulimit With the
- Page 219 and 220:
10.1.8 Man Pages and Info Pages For
- Page 221 and 222:
etc/termcap /usr/lib/terminfo/x/xte
- Page 223 and 224:
LANG=en_US.UTF-8 This is the defaul
- Page 225:
• Unicode-Howto, by Bruno Haible:
- Page 228 and 229:
228 Reference source developers may
- Page 230 and 231:
230 Reference desired. During the i
- Page 232 and 233:
232 Reference In the Printer Config
- Page 234 and 235:
234 Reference 11.4.2 Network Printe
- Page 236 and 237:
236 Reference lpadmin -p queue -v d
- Page 238 and 239:
238 Reference 11.6.1 CUPS Server an
- Page 240 and 241:
and 240 Reference Order Deny,Allow
- Page 242 and 243:
242 Reference PPD Files from Printe
- Page 244 and 245:
244 Reference If the PPD file is pr
- Page 246 and 247:
246 Reference If a broadcasting CUP
- Page 248 and 249:
248 Reference 11.7.7 CUPS Browsing:
- Page 251 and 252:
Dynamic Kernel Device Management wi
- Page 253 and 254:
aliases provided by the modules. If
- Page 255 and 256:
and the assignment keys are assigne
- Page 257:
lib/udev/* Helper programs called f
- Page 260 and 261:
260 Reference journal In the contex
- Page 262 and 263:
262 Reference Solidity Being quite
- Page 264 and 265:
264 Reference changes, run the mkin
- Page 266 and 267:
13.3 Some Other Supported File Syst
- Page 268 and 269: File System XFS 268 Reference NFSv2
- Page 271 and 272: The X Window System The X Window Sy
- Page 273 and 274: Touchscreen For a description of th
- Page 275 and 276: Type Device Screen ServerLayout Mea
- Page 277 and 278: The first resolution found is the D
- Page 279 and 280: Manual specification of modelines i
- Page 281 and 282: 14.3.2 Xft From the outset, the pro
- Page 283 and 284: fc-list ":lang=he:scalable=true" fa
- Page 285 and 286: OpenGL Driver DRI Supported Hardwar
- Page 287: drivers, SUSE cannot offer any inst
- Page 290 and 291: TIP 290 Reference The server runs a
- Page 292 and 293: 292 Reference 15.2.1 Configuring SS
- Page 294 and 295: 294 Reference In the following exam
- Page 296 and 297: 296 Reference You can also export t
- Page 298 and 299: 298 Reference 2 Open the server's c
- Page 300 and 301: 300 Reference This entry tells you
- Page 302 and 303: 302 Reference 16.1 Structure of a P
- Page 304 and 305: 304 Reference Example 16.1 PAM Conf
- Page 306 and 307: 306 Reference which may define limi
- Page 308 and 309: 308 Reference 16.3.4 limits.conf Sy
- Page 310 and 311: 310 Reference The Xen virtualizatio
- Page 312 and 313: 312 Reference The next dialog start
- Page 314 and 315: 314 Reference There is a problem bo
- Page 317: Basic Networking Linux offers the n
- Page 321 and 322: 18.1 IP Addresses and Routing The d
- Page 323 and 324: Address Type Broadcast Address Loca
- Page 325 and 326: Autoconfiguration IPv6 makes the ne
- Page 327 and 328: An IPv6 address is made up of eight
- Page 329 and 330: On top of this basic structure, IPv
- Page 331 and 332: However, the configuration and main
- Page 333 and 334: 18.3 Name Resolution DNS assists in
- Page 335 and 336: Manual Configuration of an Undetect
- Page 337 and 338: servers use the card's hardware add
- Page 339 and 340: In the last dialog, specify additio
- Page 341 and 342: Figure 18.6 ISDN Interface Configur
- Page 343 and 344: 18.4.4 Cable Modem In some countrie
- Page 345 and 346: Idle Time-Out (seconds) defines a p
- Page 347 and 348: To disable any active network conne
- Page 349 and 350: slot) or vpid-0x8086-0x1014-0x0549
- Page 351 and 352: Configuration Stage Command Functio
- Page 353 and 354: Precede comments with # signs. YaST
- Page 355 and 356: multi on/off nospoof on spoofalert
- Page 357 and 358: protocols rpc services shadow Netwo
- Page 359 and 360: 18.7 smpppd as Dial-up Assistant Mo
- Page 361: If smpppd is active, you can now tr
- Page 364 and 365: 364 Reference service:scanner.sane:
- Page 366 and 367: 366 Reference introductory HTML doc
- Page 368 and 369:
368 Reference (not expired) zone da
- Page 370 and 371:
370 Reference Figure 20.2 DNS Serve
- Page 372 and 373:
372 Reference Logging To set what t
- Page 374 and 375:
374 Reference Zone Editor (NS Recor
- Page 376 and 377:
376 Reference Figure 20.8 DNS Serve
- Page 378 and 379:
378 Reference The options entry is
- Page 380 and 381:
380 Reference 127.0.0.1 to permit r
- Page 382 and 383:
382 Reference type master; By speci
- Page 384 and 385:
384 Reference root@world.cosmos the
- Page 386 and 387:
386 Reference Example 20.7 Reverse
- Page 388 and 389:
388 Reference secret ";ejIkuCyyGJww
- Page 391 and 392:
Using NIS As soon as multiple UNIX
- Page 393 and 394:
3 Determine basic NIS setup options
- Page 395 and 396:
Figure 21.4 NIS Server Maps Setup 7
- Page 397 and 398:
c Set This host is also a NIS clien
- Page 399 and 400:
Sharing File Systems with NFS As me
- Page 401 and 402:
22.3 Exporting File Systems with Ya
- Page 403 and 404:
For these services to be started by
- Page 405 and 406:
DHCP The purpose of the dynamic hos
- Page 407 and 408:
Figure 23.1 DHCP Server: Card Selec
- Page 409 and 410:
Figure 23.3 DHCP Server: Dynamic DH
- Page 411 and 412:
23.3 The DHCP Server dhcpd The core
- Page 413 and 414:
To identify a client configured wit
- Page 415 and 416:
Time Synchronization with NTP The N
- Page 417 and 418:
24.1.2 Complex NTP Client Configura
- Page 419 and 420:
about one hour until the time is st
- Page 421 and 422:
LDAP—A Directory Service The Ligh
- Page 423 and 424:
slapd A stand-alone LDAPv3 server t
- Page 425 and 426:
Figure 25.1 Structure of an LDAP Di
- Page 427 and 428:
Line 2 gives brief description of t
- Page 429 and 430:
• who determines who should be gr
- Page 431 and 432:
25.3.2 Database-Specific Directives
- Page 433 and 434:
Example 25.7 Example for an LDIF Fi
- Page 435 and 436:
Import the modified file into the L
- Page 437 and 438:
When manually configuring additiona
- Page 439 and 440:
2 Enter the IP address of the LDAP
- Page 441 and 442:
Use Configure User Management Setti
- Page 443 and 444:
Figure 25.5 YaST: Configuration of
- Page 445 and 446:
Figure 25.6 YaST: Additional LDAP S
- Page 447 and 448:
The Apache HTTP Server With a share
- Page 449 and 450:
If you have not received error mess
- Page 451 and 452:
| |- loadmodule.conf . . | |- uid.c
- Page 453 and 454:
It is common practice to use virtua
- Page 455 and 456:
IP-Based Virtual Hosts This alterna
- Page 457 and 458:
26.2.2 Configuring Apache with YaST
- Page 459 and 460:
The default SUSE Linux Alias /icons
- Page 461 and 462:
Summary This is the final step of t
- Page 463 and 464:
Figure 26.4 HTTP Server Configurati
- Page 465 and 466:
TIP: Additional Flags If you specif
- Page 467 and 468:
mod_alias Provides Alias and Redire
- Page 469 and 470:
mod_status Provides information on
- Page 471 and 472:
Configuration File: /etc/apache2/co
- Page 473 and 474:
26.5.1 Apache Configuration In SUSE
- Page 475 and 476:
26.6 Setting Up a Secure Web Server
- Page 477 and 478:
Choose RSA ( R , the default), beca
- Page 479 and 480:
Getting an Officially Signed Certif
- Page 481 and 482:
26.7.1 Up-to-Date Software If there
- Page 483 and 484:
First, rcapache2 (described in Sect
- Page 485:
26.9.3 Development More information
- Page 488 and 489:
488 Reference WARNING: Risk of Data
- Page 490 and 491:
490 Reference The effort put into t
- Page 492 and 493:
492 Reference Unison reports confli
- Page 494 and 495:
27.2.11 Protection against Data Los
- Page 496 and 497:
496 Reference unison -testserver /h
- Page 498 and 499:
27.4.2 Using CVS The synchronizatio
- Page 500 and 501:
Other options can be listed with sv
- Page 502 and 503:
'C' 'I' '?' '!' '~' 502 Reference O
- Page 504 and 505:
504 Reference It is then possible t
- Page 506 and 507:
506 Reference Now the folders under
- Page 509 and 510:
Samba Using Samba, a Unix machine c
- Page 511 and 512:
To stop or start running Samba serv
- Page 513 and 514:
28.3.3 Configuring the Server Manua
- Page 515 and 516:
parameter with great care. This app
- Page 517 and 518:
28.4.1 Configuring a Samba Client w
- Page 519:
more online documentation and examp
- Page 522 and 523:
522 Reference 29.1 Some Facts about
- Page 524 and 525:
524 Reference 29.2.1 Hard Disks Spe
- Page 526 and 527:
526 Reference so, consider that Squ
- Page 528 and 529:
528 Reference end of the line. The
- Page 530 and 531:
530 Reference overwritten. The defa
- Page 532 and 533:
532 Reference redirect_program /usr
- Page 534 and 535:
534 Reference 29.5.2 Firewall Confi
- Page 536 and 537:
536 Reference 29.6 cachemgr.cgi The
- Page 538 and 539:
538 Reference squidGuard is a free
- Page 540 and 541:
540 Reference cat access.log.2 acce
- Page 543 and 544:
Mobile Computing with Linux Mobile
- Page 545 and 546:
Figure 30.1 Integrating a Laptop in
- Page 547 and 548:
SLP The service location protocol (
- Page 549 and 550:
Synchronizing E-Mail Use an IMAP ac
- Page 551 and 552:
30.2 Mobile Hardware SUSE Linux sup
- Page 553:
In the case of problems with power
- Page 556 and 557:
556 Reference 31.1 Controlling PCMC
- Page 558 and 559:
558 Reference a. The pcmcia_socket
- Page 560 and 561:
560 Reference Once the culprit has
- Page 562 and 563:
562 Reference 3 Set the following v
- Page 564 and 565:
564 Reference 32.1 Terminology The
- Page 566 and 567:
566 Reference • In GNOME, right-c
- Page 568 and 569:
568 Reference Figure 32.2 YaST: Con
- Page 570 and 571:
570 Reference switch, SCPM asks you
- Page 572 and 573:
572 Reference 32.4 Configuring SCPM
- Page 574 and 575:
574 Reference Checking for dependen
- Page 576 and 577:
576 Reference 32.5.2 Termination Du
- Page 578 and 579:
578 Reference 33.1 Power Saving Fun
- Page 580 and 581:
580 Reference (no-)allow-ints Allow
- Page 582 and 583:
582 Reference /proc/acpi/event All
- Page 584 and 585:
584 Reference in this file in this
- Page 586 and 587:
586 Reference such as powersaved, i
- Page 588 and 589:
588 Reference 33.4 Rest for the Har
- Page 590 and 591:
590 Reference /etc/sysconfig/powers
- Page 592 and 593:
592 Reference /etc/sysconfig/powers
- Page 594 and 595:
594 Reference increase as soon as t
- Page 596 and 597:
596 Reference 3 Copy the file DSDT.
- Page 598 and 599:
598 Reference Figure 33.1 Scheme Se
- Page 600 and 601:
600 Reference Figure 33.4 Battery C
- Page 603 and 604:
Wireless Communication There are se
- Page 605 and 606:
• Ralink RT2400, RT2500 • Texas
- Page 607 and 608:
WPA-EAP (according to IEEE 802.1x)
- Page 609 and 610:
Operating Mode A station can be int
- Page 611 and 612:
In Master mode, determine on which
- Page 613 and 614:
34.1.6 Troubleshooting If your WLAN
- Page 615 and 616:
Hardware The adapter and a suitable
- Page 617 and 618:
The Security Manager parameter is r
- Page 619 and 620:
Set the name under which the comput
- Page 621 and 622:
34.2.5 Examples This section featur
- Page 623 and 624:
34.2.6 Troubleshooting If you have
- Page 625 and 626:
34.3 Infrared Data Transmission IrD
- Page 627:
34.3.4 Troubleshooting If devices c
- Page 630 and 631:
network, 334 cellular phones, 552 c
- Page 632 and 633:
E e-mail synchronizing, 489, 549 ma
- Page 634 and 635:
layout, 220 mapping, 220 compose, 2
- Page 636 and 637:
encrypting, 117 partition table, 19
- Page 638 and 639:
passwords, 130-131 permissions, 131
- Page 640:
X.Org, 273 Xen, 309 overview, 309 X