www.tacti
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
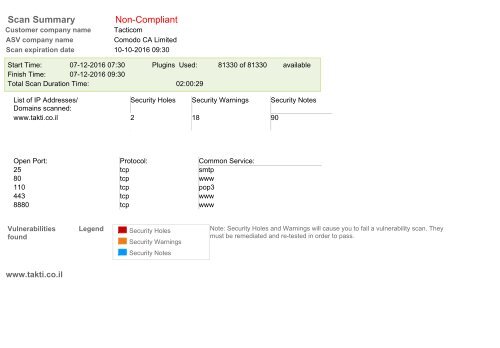
Scan Summary<br />
Customer company name<br />
ASV company name<br />
Scan expiration date<br />
Non-Compliant<br />
Tacticom<br />
Comodo CA Limited<br />
10-10-2016 09:30<br />
Start Time: 07-12-2016 07:30<br />
Finish Time: 07-12-2016 09:30<br />
Total Scan Duration Time:<br />
Plugins Used: 81330 of 81330 available<br />
02:00:29<br />
List of IP Addresses/<br />
Security Holes Security Warnings Security Notes<br />
Domains scanned:<br />
<strong>www</strong>.takti.co.il 2 18 90<br />
Open Port: Protocol: Common Service:<br />
25 tcp smtp<br />
80 tcp <strong>www</strong><br />
110 tcp pop3<br />
443 tcp <strong>www</strong><br />
8880 tcp <strong>www</strong><br />
Vulnerabilities<br />
found<br />
Legend<br />
Security Holes<br />
Security Warnings<br />
Note: Security Holes and Warnings will cause you to fail a vulnerability scan. They<br />
must be remediated and re-tested in order to pass.<br />
Security Notes<br />
<strong>www</strong>.takti.co.il
Security Hole found on port/service "80 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Automatic Failure as listed by the PCI SSC (This must be resolved for your device to be compliant)<br />
"CGI Generic SQL Injection (blind)"<br />
Category<br />
"CGI abuses "<br />
Priority "Urgent<br />
Synopsis A CGI application hosted on the remote web server is potentially prone to SQL injection attack.<br />
Description By sending specially crafted parameters to one or more CGI scripts hosted on the remote web server, Nessus was<br />
able to get a very different response, which suggests that it may have been able to modify the behavior of the<br />
application and directly access the underlying database.<br />
An attacker may be able to exploit this issue to bypass authentication, read confidential data, modify the remote<br />
database, or even take control of the remote operating system.<br />
Note that this script is experimental and may be prone to false positives.<br />
See also:<br />
http://<strong>www</strong>.securiteam.com/securityreviews/5DP0N1P76E.html<br />
http://<strong>www</strong>.securitydocs.com/library/2651<br />
http://projects.webappsec.org/SQL-Injection<br />
Risk factor HIGH / CVSS BASE SCORE :7.5 CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P<br />
Plugin<br />
output Using the GET HTTP method, Nessus found that :<br />
+ The following resources may be vulnerable to blind SQL injection :<br />
+ The 'NewNameMade' parameter of the /BuildaGate5/general2/company_search_tree.php CGI :<br />
/BuildaGate5/general2/company_search_tree.php?cstFlag=1&z=&framesource=&<br />
framemode=&ItemID=&FromRec=&FF=&DataCardTemplate=&Daf=&BANNER=&BuyerID=3
1<br />
0291408&CNumber=&CardPrice=&Clubtmp1=&Referral=tree&SearchType=All&Site<br />
Nam<br />
e=takti&ValuePage=&comefrom=&NewNameMade=0zz1&z=&framesource=&framemo<br />
de=&I<br />
temID=&FromRec=&FF=&DataCardTemplate=&Daf=&BANNER=&BuyerID=31029140<br />
8&CNumb<br />
er=&CardPrice=&Clubtmp1=&Referral=tree&SearchType=All&SiteName=ta<br />
kti&Value<br />
Page=&comefrom=&NewNameMade=0yy<br />
-------- output --------<br />
<br />
Security Hole found on port/service "443 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Automatic Failure as listed by the PCI SSC (This must be resolved for your device to be compliant)<br />
"CGI Generic SQL Injection (blind)"<br />
Category<br />
"CGI abuses "<br />
Priority "Urgent<br />
Synopsis A CGI application hosted on the remote web server is potentially prone to SQL injection attack.<br />
Description By sending specially crafted parameters to one or more CGI scripts hosted on the remote web server, Nessus was<br />
able to get a very different response, which suggests that it may have been able to modify the behavior of the<br />
application and directly access the underlying database.<br />
An attacker may be able to exploit this issue to bypass authentication, read confidential data, modify the remote<br />
database, or even take control of the remote operating system.<br />
Note that this script is experimental and may be prone to false positives.<br />
See also:<br />
http://<strong>www</strong>.securiteam.com/securityreviews/5DP0N1P76E.html<br />
http://<strong>www</strong>.securitydocs.com/library/2651<br />
http://projects.webappsec.org/SQL-Injection<br />
Risk factor HIGH / CVSS BASE SCORE :7.5 CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:P<br />
Plugin<br />
output Using the GET HTTP method, Nessus found that :<br />
+ The following resources may be vulnerable to blind SQL injection :<br />
+ The 'NewNameMade' parameter of the /BuildaGate5/general2/company_search_tree.php CGI :<br />
/BuildaGate5/general2/company_search_tree.php?cstFlag=1&z=&framesource=&
framemode=&ItemID=&FromRec=&FF=&DataCardTemplate=&Daf=&BANNER=&BuyerID=3<br />
1<br />
0291408&CNumber=&CardPrice=&Clubtmp1=&Referral=tree&SearchType=All&Site<br />
Nam<br />
e=takti&ValuePage=&comefrom=&NewNameMade=0zz1&z=&framesource=&framemo<br />
de=&I<br />
temID=&FromRec=&FF=&DataCardTemplate=&Daf=&BANNER=&BuyerID=31029140<br />
8&CNumb<br />
er=&CardPrice=&Clubtmp1=&Referral=tree&SearchType=All&SiteName=ta<br />
kti&Value<br />
Page=&comefrom=&NewNameMade=0yy<br />
-------- output --------<br />
<br />
Security Warning found on port/service "443 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Automatic Failure as listed by the PCI SSC (This must be resolved for your device to be compliant)<br />
"SSL Version 2 (v2) Protocol Detection"<br />
Category<br />
"Service detection "<br />
Priority "Medium Priority<br />
Synopsis The remote service encrypts traffic using a protocol with known weaknesses.<br />
Description The remote service accepts connections encrypted using SSL 2.0 and/or SSL 3.0. These versions of SSL are affected<br />
by several cryptographic flaws. An attacker can exploit these flaws to conduct man-in-the-middle attacks or to decrypt<br />
communications between the affected service and clients.<br />
NIST has determined that SSL 3.0 is no longer acceptable for secure communications. As of the date of enforcement<br />
found in PCI DSS v3.1, any version of SSL will not meet the PCI SSC'S definition of 'strong cryptography'.<br />
See also:<br />
http://<strong>www</strong>.schneier.com/paper-ssl.pdf<br />
http://support.microsoft.com/kb/187498<br />
http://<strong>www</strong>.nessus.org/u?247c4540<br />
https://<strong>www</strong>.openssl.org/~bodo/ssl-poodle.pdf<br />
http://<strong>www</strong>.nessus.org/u?5d15ba70<br />
https://<strong>www</strong>.imperialviolet.org/2014/10/14/poodle.html<br />
https://tools.ietf.org/html/draft-ietf-tls-downgrade-scsv-00<br />
Risk factor MEDIUM / CVSS BASE SCORE :5.0 CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N<br />
Plugin<br />
output<br />
- SSLv3 is enabled and the server supports at least one cipher.
Solution Consult the application's documentation to disable SSL 2.0 and 3.0.<br />
Use TLS 1.1 (with approved cipher suites) or higher instead.
Security Warning found on port/service "25 / tcp / smtp"<br />
Status<br />
Plugin<br />
Automatic Failure as listed by the PCI SSC (This must be resolved for your device to be compliant)<br />
"SSL Version 2 (v2) Protocol Detection"<br />
Category<br />
"Service detection "<br />
Priority "Medium Priority<br />
Synopsis The remote service encrypts traffic using a protocol with known weaknesses.<br />
Description The remote service accepts connections encrypted using SSL 2.0 and/or SSL 3.0. These versions of SSL are affected<br />
by several cryptographic flaws. An attacker can exploit these flaws to conduct man-in-the-middle attacks or to decrypt<br />
communications between the affected service and clients.<br />
NIST has determined that SSL 3.0 is no longer acceptable for secure communications. As of the date of enforcement<br />
found in PCI DSS v3.1, any version of SSL will not meet the PCI SSC'S definition of 'strong cryptography'.<br />
See also:<br />
http://<strong>www</strong>.schneier.com/paper-ssl.pdf<br />
http://support.microsoft.com/kb/187498<br />
http://<strong>www</strong>.nessus.org/u?247c4540<br />
https://<strong>www</strong>.openssl.org/~bodo/ssl-poodle.pdf<br />
http://<strong>www</strong>.nessus.org/u?5d15ba70<br />
https://<strong>www</strong>.imperialviolet.org/2014/10/14/poodle.html<br />
https://tools.ietf.org/html/draft-ietf-tls-downgrade-scsv-00<br />
Risk factor MEDIUM / CVSS BASE SCORE :5.0 CVSS2#AV:N/AC:L/Au:N/C:P/I:N/A:N<br />
Plugin<br />
output<br />
- SSLv2 is enabled and the server supports at least one cipher.<br />
- SSLv3 is enabled and the server supports at least one cipher.
Solution Consult the application's documentation to disable SSL 2.0 and 3.0.<br />
Use TLS 1.1 (with approved cipher suites) or higher instead.
Security Warning found on port/service "80 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Automatic Failure as listed by the PCI SSC (This must be resolved for your device to be compliant)<br />
"CGI Generic Cross-Site Scripting (comprehensive test)"<br />
Category<br />
"CGI abuses : XSS "<br />
Priority "Medium Priority<br />
Synopsis The remote web server is prone to cross-site scripting attacks.<br />
Description The remote web server hosts CGI scripts that fail to adequately sanitize request strings of malicious JavaScript. By<br />
leveraging this issue, an attacker may be able to cause arbitrary HTML and script code to be executed in a user's<br />
browser within the security context of the affected site. These XSS are likely to be 'non-persistent' or 'reflected'.<br />
See also:<br />
http://en.wikipedia.org/wiki/Cross_site_scripting#Non-persistent<br />
http://<strong>www</strong>.nessus.org/u?9717ad85<br />
http://projects.webappsec.org/Cross-Site+Scripting<br />
Risk factor MEDIUM / CVSS BASE SCORE :4.3 CVSS2#AV:N/AC:M/Au:N/C:N/I:P/A:N<br />
Plugin<br />
output Using the GET HTTP method, Nessus found that :<br />
+ The following resources may be vulnerable to cross-site scripting (comprehensive test) :<br />
+ The 'FromRec' parameter of the /BuildaGate5/general2/company_search_tree.php CGI :<br />
/BuildaGate5/general2/company_search_tree.php?FromRec=>>>>>>>>>>foo"bar'<br />
207
Security Warning found on port/service "443 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Automatic Failure as listed by the PCI SSC (This must be resolved for your device to be compliant)<br />
"CGI Generic Cross-Site Scripting (comprehensive test)"<br />
Category<br />
"CGI abuses : XSS "<br />
Priority "Medium Priority<br />
Synopsis The remote web server is prone to cross-site scripting attacks.<br />
Description The remote web server hosts CGI scripts that fail to adequately sanitize request strings of malicious JavaScript. By<br />
leveraging this issue, an attacker may be able to cause arbitrary HTML and script code to be executed in a user's<br />
browser within the security context of the affected site. These XSS are likely to be 'non-persistent' or 'reflected'.<br />
See also:<br />
http://en.wikipedia.org/wiki/Cross_site_scripting#Non-persistent<br />
http://<strong>www</strong>.nessus.org/u?9717ad85<br />
http://projects.webappsec.org/Cross-Site+Scripting<br />
Risk factor MEDIUM / CVSS BASE SCORE :4.3 CVSS2#AV:N/AC:M/Au:N/C:N/I:P/A:N<br />
Plugin<br />
output Using the GET HTTP method, Nessus found that :<br />
+ The following resources may be vulnerable to cross-site scripting (comprehensive test) :<br />
+ The 'FromRec' parameter of the /BuildaGate5/general2/company_search_tree.php CGI :<br />
/BuildaGate5/general2/company_search_tree.php?FromRec=>>>>>>>>>>foo"bar'<br />
207
Security Warning found on port/service "25 / tcp / smtp"<br />
Status<br />
Plugin<br />
Fail (This must be resolved for your device to be compliant).<br />
"SSL/TLS EXPORT_RSA
Kx={key exchange}<br />
Au={authentication}<br />
Enc={symmetric encryption method}<br />
Mac={message authentication code}<br />
{export flag}<br />
Addition<br />
Information<br />
CVE:<br />
http://cgi.nessus.org/cve.php3?cve=CVE-2015-0204<br />
BID : 71936 Other references { cert : 243585osvdb : 116794 }<br />
Solution Reconfigure the service to remove support for EXPORT_RSA cipher suites.
Security Warning found on port/service "110 / tcp / pop3"<br />
Status<br />
Plugin<br />
Fail (This must be resolved for your device to be compliant).<br />
"SSL Certificate Expiry"<br />
Category<br />
"General "<br />
Priority "Medium Priority<br />
Synopsis The remote server's SSL certificate has already expired.<br />
Description This plugin checks expiry dates of certificates associated with SSL- enabled services on the target and reports<br />
whether any have already expired.<br />
Risk factor MEDIUM / CVSS BASE SCORE :5.0 CVSS2#AV:N/AC:L/Au:N/C:N/I:P/A:N<br />
Plugin<br />
output The SSL certificate has already expired :<br />
Subject : C=US, ST=Virginia, L=Herndon, O=Parallels, OU=Parallels Panel, CN=Parallels Panel,<br />
emailAddress=info@parallels.com<br />
Issuer : C=US, ST=Virginia, L=Herndon, O=Parallels, OU=Parallels Panel, CN=Parallels Panel,<br />
emailAddress=info@parallels.com<br />
Not valid before : Apr 13 06:20:36 2015 GMT<br />
Not valid after : Apr 12 06:20:36 2016 GMT<br />
Solution Purchase or generate a new SSL certificate to replace the existing one.
Security Warning found on port/service "25 / tcp / smtp"<br />
Status<br />
Plugin<br />
Fail (This must be resolved for your device to be compliant).<br />
"SSL Certificate Expiry"<br />
Category<br />
"General "<br />
Priority "Medium Priority<br />
Synopsis The remote server's SSL certificate has already expired.<br />
Description This plugin checks expiry dates of certificates associated with SSL- enabled services on the target and reports<br />
whether any have already expired.<br />
Risk factor MEDIUM / CVSS BASE SCORE :5.0 CVSS2#AV:N/AC:L/Au:N/C:N/I:P/A:N<br />
Plugin<br />
output The SSL certificate has already expired :<br />
Subject : C=US, ST=Virginia, L=Herndon, O=Parallels, OU=Parallels Panel, CN=Parallels Panel,<br />
emailAddress=info@parallels.com<br />
Issuer : C=US, ST=Virginia, L=Herndon, O=Parallels, OU=Parallels Panel, CN=Parallels Panel,<br />
emailAddress=info@parallels.com<br />
Not valid before : Apr 13 06:20:36 2015 GMT<br />
Not valid after : Apr 12 06:20:36 2016 GMT<br />
Solution Purchase or generate a new SSL certificate to replace the existing one.
Security Warning found on port/service "443 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Fail (This must be resolved for your device to be compliant).<br />
"SSL DROWN Attack Vulnerability (Decrypting RSA with Obsolete and Weakened eNcryption)"<br />
Category<br />
"Misc. "<br />
Priority "Medium Priority<br />
Synopsis The remote host may be affected by a vulnerability that allows a remote attacker to potentially decrypt captured<br />
Description TLS traffic.<br />
The remote host supports SSLv2 and therefore may be affected by a vulnerability that allows a cross-protocol<br />
Bleichenbacher padding oracle attack known as DROWN (Decrypting RSA with Obsolete and Weakened eNcryption).<br />
This vulnerability exists due to a flaw in the Secure Sockets Layer Version 2 (SSLv2) implementation, and it allows<br />
captured TLS traffic to be decrypted. A man-in-the-middle attacker can exploit this to decrypt the TLS connection by<br />
utilizing previously captured traffic and weak cryptography along with a series of specially crafted connections to an<br />
SSLv2 server that uses the same private key.<br />
See also:<br />
https://drownattack.com/<br />
https://drownattack.com/drown-attack-paper.pdf<br />
Risk factor MEDIUM / CVSS BASE SCORE :4.0 CVSS2#AV:N/AC:H/Au:N/C:P/I:P/A:N<br />
Plugin<br />
output<br />
Addition<br />
Information<br />
The remote host supports SSLv2 and may be affected by SSL DROWN.<br />
CVE:<br />
http://cgi.nessus.org/cve.php3?cve=CVE-2016-0800<br />
Other references { cert : 583776osvdb : 135149 }<br />
Solution Disable SSLv2 and export grade cryptography cipher suites. Ensure that private keys are not used anywhere with<br />
server software that supports SSLv2 connections.
Security Warning found on port/service "25 / tcp / smtp"<br />
Status<br />
Plugin<br />
Fail (This must be resolved for your device to be compliant).<br />
"SSL DROWN Attack Vulnerability (Decrypting RSA with Obsolete and Weakened eNcryption)"<br />
Category<br />
"Misc. "<br />
Priority "Medium Priority<br />
Synopsis The remote host may be affected by a vulnerability that allows a remote attacker to potentially decrypt captured<br />
Description TLS traffic.<br />
The remote host supports SSLv2 and therefore may be affected by a vulnerability that allows a cross-protocol<br />
Bleichenbacher padding oracle attack known as DROWN (Decrypting RSA with Obsolete and Weakened eNcryption).<br />
This vulnerability exists due to a flaw in the Secure Sockets Layer Version 2 (SSLv2) implementation, and it allows<br />
captured TLS traffic to be decrypted. A man-in-the-middle attacker can exploit this to decrypt the TLS connection by<br />
utilizing previously captured traffic and weak cryptography along with a series of specially crafted connections to an<br />
SSLv2 server that uses the same private key.<br />
See also:<br />
https://drownattack.com/<br />
https://drownattack.com/drown-attack-paper.pdf<br />
Risk factor MEDIUM / CVSS BASE SCORE :4.0 CVSS2#AV:N/AC:H/Au:N/C:P/I:P/A:N<br />
Plugin<br />
output<br />
The remote host is affected by SSL DROWN and supports the following<br />
vulnerable cipher suites :<br />
Low Strength Ciphers (= 112-bit key)<br />
SSLv2
RC4-MD5 Kx=RSA Au=RSA Enc=RC4(128) Mac=MD5<br />
The fields above are :<br />
{OpenSSL ciphername}<br />
Kx={key exchange}<br />
Au={authentication}<br />
Enc={symmetric encryption method}<br />
Mac={message authentication code}<br />
{export flag}<br />
Addition<br />
Information<br />
CVE:<br />
http://cgi.nessus.org/cve.php3?cve=CVE-2016-0800<br />
Other references { cert : 583776osvdb : 135149 }<br />
Solution Disable SSLv2 and export grade cryptography cipher suites. Ensure that private keys are not used anywhere with<br />
server software that supports SSLv2 connections.
Security Warning found on port/service "25 / tcp / smtp"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"Postfix < 2.0 Multiple Vulnerabilities"<br />
Category<br />
"SMTP problems "<br />
Priority "Medium Priority<br />
Synopsis The remote server is vulnerable to a denial of service.<br />
Description The remote host is running a version of Postfix that is as old as or older than 1.1.12.<br />
There are two vulnerabilities in this version that could allow an attacker to remotely disable it, or to be used as a DDoS<br />
agent against arbitrary hosts.<br />
Risk factor CVE-2003-0468 - Medium / CVSS BASE SCORE :5.0 CVSS2#(AV:N/AC:L/Au:N/C:N/I:N/A:P), CVE-2003-0540 - Medium /<br />
CVSS BASE SCORE :5.0 CVSS2#(AV:N/AC:L/Au:N/C:N/I:N/A:P)<br />
Addition<br />
Information<br />
CVE:<br />
http://cgi.nessus.org/cve.php3?cve=CVE-2003-0468<br />
http://cgi.nessus.org/cve.php3?cve=CVE-2003-0540<br />
BID : 8362, 8361 Other references { rhsa : 2003:251-01osvdb : 10545, 10544, 6551suse : SUSE-SA:2003:033 }<br />
Solution Upgrade to Postfix 2.0.<br />
This vulnerability has been classified as a denial of service vulnerability. This does not cause the scan to be non-compliant and is not<br />
required to be patched. We still recommend resolving this issue.
Security Warning found on port/service "110 / tcp / pop3"<br />
Status<br />
Plugin<br />
Fail (This must be resolved for your device to be compliant).<br />
"SSL Certificate with Wrong Hostname"<br />
Category<br />
Priority<br />
"General "<br />
"Medium Priority<br />
Synopsis The SSL certificate for this service is for a different host.<br />
Description The commonName (CN) of the SSL certificate presented on this service is for a different machine.<br />
Risk factor MEDIUM / CVSS BASE SCORE :5.0 CVSS2#AV:N/AC:L/Au:N/C:N/I:P/A:N<br />
Plugin<br />
output The identities known by Nessus are :<br />
mail.takti.co.il<br />
takti.co.il<br />
webmail.takti.co.il<br />
<strong>www</strong>.takti.co.il<br />
The Common Name in the certificate is :<br />
Parallels Panel<br />
Solution Purchase or generate a proper certificate for this service.
Security Warning found on port/service "25 / tcp / smtp"<br />
Status<br />
Plugin<br />
Fail (This must be resolved for your device to be compliant).<br />
"SSL Certificate with Wrong Hostname"<br />
Category<br />
Priority<br />
"General "<br />
"Medium Priority<br />
Synopsis The SSL certificate for this service is for a different host.<br />
Description The commonName (CN) of the SSL certificate presented on this service is for a different machine.<br />
Risk factor MEDIUM / CVSS BASE SCORE :5.0 CVSS2#AV:N/AC:L/Au:N/C:N/I:P/A:N<br />
Plugin<br />
output The identities known by Nessus are :<br />
mail.takti.co.il<br />
takti.co.il<br />
webmail.takti.co.il<br />
<strong>www</strong>.takti.co.il<br />
The Common Name in the certificate is :<br />
Parallels Panel<br />
Solution Purchase or generate a proper certificate for this service.
Security Warning found on port/service "110 / tcp / pop3"<br />
Status<br />
Plugin<br />
Fail (This must be resolved for your device to be compliant).<br />
"SSL Self-Signed Certificate"<br />
Category<br />
"General "<br />
Priority "Medium Priority<br />
Synopsis The SSL certificate chain for this service ends in an unrecognized self-signed certificate.<br />
Description The X.509 certificate chain for this service is not signed by a recognized certificate authority. If the remote host is a<br />
public host in production, this nullifies the use of SSL as anyone could establish a man-in-the-middle attack against the<br />
remote host.<br />
Note that this plugin does not check for certificate chains that end in a certificate that is not self-signed, but is signed<br />
by an unrecognized certificate authority.<br />
Risk factor MEDIUM / CVSS BASE SCORE :6.4 CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:N<br />
Plugin<br />
output<br />
The following certificate was found at the top of the certificate<br />
chain sent by the remote host, but is self-signed and was not<br />
found in the list of known certificate authorities :<br />
|-Subject : C=US/ST=Virginia/L=Herndon/O=Parallels/OU=Parallels Panel/CN=Parallels Panel/E=info@parallels.com<br />
Solution Purchase or generate a proper certificate for this service.
Security Warning found on port/service "25 / tcp / smtp"<br />
Status<br />
Plugin<br />
Fail (This must be resolved for your device to be compliant).<br />
"SSL Self-Signed Certificate"<br />
Category<br />
"General "<br />
Priority "Medium Priority<br />
Synopsis The SSL certificate chain for this service ends in an unrecognized self-signed certificate.<br />
Description The X.509 certificate chain for this service is not signed by a recognized certificate authority. If the remote host is a<br />
public host in production, this nullifies the use of SSL as anyone could establish a man-in-the-middle attack against the<br />
remote host.<br />
Note that this plugin does not check for certificate chains that end in a certificate that is not self-signed, but is signed<br />
by an unrecognized certificate authority.<br />
Risk factor MEDIUM / CVSS BASE SCORE :6.4 CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:N<br />
Plugin<br />
output<br />
The following certificate was found at the top of the certificate<br />
chain sent by the remote host, but is self-signed and was not<br />
found in the list of known certificate authorities :<br />
|-Subject : C=US/ST=Virginia/L=Herndon/O=Parallels/OU=Parallels Panel/CN=Parallels Panel/E=info@parallels.com<br />
Solution Purchase or generate a proper certificate for this service.
Security Warning found on port/service "443 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Fail (This must be resolved for your device to be compliant).<br />
"SSL Certificate Cannot Be Trusted"<br />
Category<br />
"General "<br />
Priority "Medium Priority<br />
Synopsis The SSL certificate for this service cannot be trusted.<br />
Description The server's X.509 certificate does not have a signature from a known public certificate authority. This situation<br />
can occur in three different ways, each of which results in a break in the chain below which certificates cannot be<br />
trusted.<br />
First, the top of the certificate chain sent by the server might not be descended from a known public certificate<br />
authority. This can occur either when the top of the chain is an unrecognized, self-signed certificate, or when<br />
intermediate certificates are missing that would connect the top of the certificate chain to a known public certificate<br />
authority.<br />
Second, the certificate chain may contain a certificate that is not valid at the time of the scan. This can occur either<br />
when the scan occurs before one of the certificate's 'notBefore' dates, or after one of the certificate's 'notAfter' dates.<br />
Third, the certificate chain may contain a signature that either didn't match the certificate's information, or could not<br />
be verified. Bad signatures can be fixed by getting the certificate with the bad signature to be re-signed by its issuer.<br />
Signatures that could not be verified are the result of the certificate's issuer using a signing algorithm that Nessus<br />
either does not support or does not recognize.<br />
If the remote host is a public host in production, any break in the chain makes it more difficult for users to verify the<br />
authenticity and identity of the web server. This could make it easier to carry out man-in-the-middle attacks against<br />
the remote host.<br />
Risk factor MEDIUM / CVSS BASE SCORE :6.4 CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:N<br />
Plugin<br />
output<br />
The following certificate was at the top of the certificate<br />
chain sent by the remote host, but is signed by an unknown
certificate authority :<br />
|-Subject : CN=<strong>www</strong>.takti.co.il<br />
|-Issuer : C=US/O=GeoTrust Inc./CN=RapidSSL SHA256 CA<br />
Solution Purchase or generate a proper certificate for this service.
Security Warning found on port/service "110 / tcp / pop3"<br />
Status<br />
Plugin<br />
Fail (This must be resolved for your device to be compliant).<br />
"SSL Certificate Cannot Be Trusted"<br />
Category<br />
"General "<br />
Priority "Medium Priority<br />
Synopsis The SSL certificate for this service cannot be trusted.<br />
Description The server's X.509 certificate does not have a signature from a known public certificate authority. This situation<br />
can occur in three different ways, each of which results in a break in the chain below which certificates cannot be<br />
trusted.<br />
First, the top of the certificate chain sent by the server might not be descended from a known public certificate<br />
authority. This can occur either when the top of the chain is an unrecognized, self-signed certificate, or when<br />
intermediate certificates are missing that would connect the top of the certificate chain to a known public certificate<br />
authority.<br />
Second, the certificate chain may contain a certificate that is not valid at the time of the scan. This can occur either<br />
when the scan occurs before one of the certificate's 'notBefore' dates, or after one of the certificate's 'notAfter' dates.<br />
Third, the certificate chain may contain a signature that either didn't match the certificate's information, or could not<br />
be verified. Bad signatures can be fixed by getting the certificate with the bad signature to be re-signed by its issuer.<br />
Signatures that could not be verified are the result of the certificate's issuer using a signing algorithm that Nessus<br />
either does not support or does not recognize.<br />
If the remote host is a public host in production, any break in the chain makes it more difficult for users to verify the<br />
authenticity and identity of the web server. This could make it easier to carry out man-in-the-middle attacks against<br />
the remote host.<br />
Risk factor MEDIUM / CVSS BASE SCORE :6.4 CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:N<br />
Plugin<br />
output<br />
The following certificate was part of the certificate chain<br />
sent by the remote host, but has expired :
|-Subject : C=US/ST=Virginia/L=Herndon/O=Parallels/OU=Parallels Panel/CN=Parallels Panel/E=info@parallels.com<br />
|-Not After : Apr 12 06:20:36 2016 GMT<br />
The following certificate was at the top of the certificate<br />
chain sent by the remote host, but is signed by an unknown<br />
certificate authority :<br />
|-Subject : C=US/ST=Virginia/L=Herndon/O=Parallels/OU=Parallels Panel/CN=Parallels Panel/E=info@parallels.com<br />
|-Issuer : C=US/ST=Virginia/L=Herndon/O=Parallels/OU=Parallels Panel/CN=Parallels Panel/E=info@parallels.com<br />
Solution Purchase or generate a proper certificate for this service.
Security Warning found on port/service "25 / tcp / smtp"<br />
Status<br />
Plugin<br />
Fail (This must be resolved for your device to be compliant).<br />
"SSL Certificate Cannot Be Trusted"<br />
Category<br />
"General "<br />
Priority "Medium Priority<br />
Synopsis The SSL certificate for this service cannot be trusted.<br />
Description The server's X.509 certificate does not have a signature from a known public certificate authority. This situation<br />
can occur in three different ways, each of which results in a break in the chain below which certificates cannot be<br />
trusted.<br />
First, the top of the certificate chain sent by the server might not be descended from a known public certificate<br />
authority. This can occur either when the top of the chain is an unrecognized, self-signed certificate, or when<br />
intermediate certificates are missing that would connect the top of the certificate chain to a known public certificate<br />
authority.<br />
Second, the certificate chain may contain a certificate that is not valid at the time of the scan. This can occur either<br />
when the scan occurs before one of the certificate's 'notBefore' dates, or after one of the certificate's 'notAfter' dates.<br />
Third, the certificate chain may contain a signature that either didn't match the certificate's information, or could not<br />
be verified. Bad signatures can be fixed by getting the certificate with the bad signature to be re-signed by its issuer.<br />
Signatures that could not be verified are the result of the certificate's issuer using a signing algorithm that Nessus<br />
either does not support or does not recognize.<br />
If the remote host is a public host in production, any break in the chain makes it more difficult for users to verify the<br />
authenticity and identity of the web server. This could make it easier to carry out man-in-the-middle attacks against<br />
the remote host.<br />
Risk factor MEDIUM / CVSS BASE SCORE :6.4 CVSS2#AV:N/AC:L/Au:N/C:P/I:P/A:N<br />
Plugin<br />
output<br />
The following certificate was part of the certificate chain<br />
sent by the remote host, but has expired :
|-Subject : C=US/ST=Virginia/L=Herndon/O=Parallels/OU=Parallels Panel/CN=Parallels Panel/E=info@parallels.com<br />
|-Not After : Apr 12 06:20:36 2016 GMT<br />
The following certificate was at the top of the certificate<br />
chain sent by the remote host, but is signed by an unknown<br />
certificate authority :<br />
|-Subject : C=US/ST=Virginia/L=Herndon/O=Parallels/OU=Parallels Panel/CN=Parallels Panel/E=info@parallels.com<br />
|-Issuer : C=US/ST=Virginia/L=Herndon/O=Parallels/OU=Parallels Panel/CN=Parallels Panel/E=info@parallels.com<br />
Solution Purchase or generate a proper certificate for this service.
Security Warning found on port/service "25 / tcp / smtp"<br />
Status<br />
Plugin<br />
Fail (This must be resolved for your device to be compliant).<br />
"SSL Weak Cipher Suites Supported"<br />
Category<br />
"General "<br />
Priority "Medium Priority<br />
Synopsis The remote service supports the use of weak SSL ciphers.<br />
Description The remote host supports the use of SSL ciphers that offer weak encryption.<br />
Note: This is considerably easier to exploit if the attacker is on the same physical network.<br />
See also:<br />
http://<strong>www</strong>.openssl.org/docs/apps/ciphers.html<br />
Risk factor MEDIUM / CVSS BASE SCORE :4.3 CVSS2#AV:N/AC:M/Au:N/C:P/I:N/A:N<br />
Plugin<br />
output Here is the list of weak SSL ciphers supported by the remote server :<br />
Low Strength Ciphers (
DES-CBC-SHA Kx=RSA Au=RSA Enc=DES-CBC(56) Mac=SHA1<br />
The fields above are :<br />
{OpenSSL ciphername}<br />
Kx={key exchange}<br />
Au={authentication}<br />
Enc={symmetric encryption method}<br />
Mac={message authentication code}<br />
{export flag}<br />
Solution Reconfigure the affected application, if possible to avoid the use of weak ciphers.
Security Notes found on port/service "0 / tcp / "<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"Additional DNS Hostnames"<br />
Category<br />
"General "<br />
Priority "Low Priority<br />
Synopsis Potential virtual hosts have been detected.<br />
Description Hostnames different from the current hostname have been collected by miscellaneous plugins. Different web<br />
servers may be hosted on name- based virtual hosts.<br />
See also:<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
http://en.wikipedia.org/wiki/Virtual_hosting<br />
The following hostnames point to the remote host:<br />
- takti.co.il<br />
- mail.takti.co.il<br />
- webmail.takti.co.il<br />
Solution If you want to test them, re-scan using the special vhost syntax, such as :<br />
<strong>www</strong>.example.com[192.0.32.10]
Security Notes found on port/service "8880 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"HyperText Transfer Protocol (HTTP) Information"<br />
Category<br />
"Web Servers "<br />
Priority "Low Priority<br />
Synopsis Some information about the remote HTTP configuration can be extracted.<br />
Description This test gives some information about the remote HTTP protocol - the version used, whether HTTP Keep-Alive and<br />
HTTP pipelining are enabled, etc...<br />
This test is informational only and does not denote any security problem.<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
Protocol version : HTTP/1.1<br />
SSL : no<br />
Keep-Alive : no<br />
Options allowed : (Not implemented)<br />
Headers :<br />
Server: sw-cp-server<br />
Date: Tue, 12 Jul 2016 08:05:19 GMT<br />
Content-Type: text/html<br />
Transfer-Encoding: chunked<br />
Connection: keep-alive<br />
Expires: Fri, 28 May 1999 00:00:00 GMT<br />
Last-Modified: Tue, 12 Jul 2016 08:05:19 GMT<br />
Cache-Control: no-store, no-cache, must-revalidate<br />
Cache-Control: post-check=0, pre-check=0<br />
Pragma: no-cache<br />
P3P: CP="NON COR CURa ADMa OUR NOR UNI COM NAV STA"
Security Notes found on port/service "443 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"HyperText Transfer Protocol (HTTP) Information"<br />
Category<br />
"Web Servers "<br />
Priority "Low Priority<br />
Synopsis Some information about the remote HTTP configuration can be extracted.<br />
Description This test gives some information about the remote HTTP protocol - the version used, whether HTTP Keep-Alive and<br />
HTTP pipelining are enabled, etc...<br />
This test is informational only and does not denote any security problem.<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
Protocol version : HTTP/1.1<br />
SSL : yes<br />
Keep-Alive : no<br />
Options allowed : (Not implemented)<br />
Headers :<br />
Server: nginx<br />
Date: Tue, 12 Jul 2016 08:05:18 GMT
Content-Type: text/html; charset=utf-8<br />
Transfer-Encoding: chunked<br />
Connection: keep-alive<br />
Expires: Thu, 19 Nov 1981 08:52:00 GMT<br />
Pragma: no-cache<br />
Cache-Control: private, max-age=10800, pre-check=10800<br />
X-Frame-Options: SAMEORIGIN<br />
X-XSS-Protection: 1; mode=block<br />
X-Content-Type-Options: nosniff<br />
X-WebKit-CSP: default-src 'self'<br />
X-Permitted-Cross-Domain-Policies: master-only<br />
Strict-Transport-Security: max-age=15768000;includeSubDomains<br />
MS-Author-Via: DAV
Security Notes found on port/service "80 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"HyperText Transfer Protocol (HTTP) Information"<br />
Category<br />
"Web Servers "<br />
Priority "Low Priority<br />
Synopsis Some information about the remote HTTP configuration can be extracted.<br />
Description This test gives some information about the remote HTTP protocol - the version used, whether HTTP Keep-Alive and<br />
HTTP pipelining are enabled, etc...<br />
This test is informational only and does not denote any security problem.<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
Protocol version : HTTP/1.1<br />
SSL : no<br />
Keep-Alive : no<br />
Options allowed : (Not implemented)<br />
Headers :<br />
Server: nginx<br />
Date: Tue, 12 Jul 2016 08:05:17 GMT<br />
Content-Type: text/html; charset=utf-8<br />
Transfer-Encoding: chunked<br />
Connection: keep-alive<br />
Expires: Thu, 19 Nov 1981 08:52:00 GMT<br />
Pragma: no-cache<br />
Cache-Control: private, max-age=10800, pre-check=10800<br />
X-Frame-Options: SAMEORIGIN<br />
X-XSS-Protection: 1; mode=block<br />
X-Content-Type-Options: nosniff<br />
X-WebKit-CSP: default-src 'self'
X-Permitted-Cross-Domain-Policies: master-only<br />
Strict-Transport-Security: max-age=15768000;includeSubDomains<br />
MS-Author-Via: DAV
Security Notes found on port/service "443 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"SSL Certificate Information"<br />
Category<br />
Priority<br />
"General "<br />
"Low Priority<br />
Synopsis This plugin displays the SSL certificate.<br />
Description This plugin connects to every SSL-related port and attempts to extract and dump the X.509 certificate.<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
Subject Name:<br />
Common Name: <strong>www</strong>.takti.co.il<br />
Issuer Name:<br />
Country: US<br />
Organization: GeoTrust Inc.<br />
Common Name: RapidSSL SHA256 CA<br />
Serial Number: 22 AB 2A 41 C6 A4 5B 71 35 92 69 0F 1B 14 C2 11<br />
Version: 3<br />
Signature Algorithm: SHA-256 With RSA Encryption<br />
Not Valid Before: Jul 04 00:00:00 2016 GMT<br />
Not Valid After: Sep 02 23:59:59 2019 GMT<br />
Public Key Info:<br />
Algorithm: RSA Encryption
Key Length: 2048 bits<br />
Public Key: 00 BC AE FF C7 18 D7 45 3A 66 2D 28 CC 72 CF D0 76 3E 17 DF<br />
E2 CC 69 3D 03 20 75 6E 69 52 7F 20 D7 22 3C 1C DF 41 CF 9D<br />
11 0B DF 0E 15 D4 49 BF 80 8D 52 0D 29 1D 6E 6E C8 70 B5 CC<br />
3B 28 08 DA 9E A2 4D 8E D6 98 02 79 0A 12 5F 45 EA 4F 12 3A<br />
82 8E 96 3A D2 62 C4 B2 E7 A5 E3 93 5F C4 CD E3 C3 82 1E 4C<br />
84 76 58 DC FB A1 28 60 6B 70 35 E7 5A F7 DC 75 EB 80 7C F4<br />
5D D5 B1 2A 17 37 DD 64 0A 07 90 20 84 A6 6F 4B 6E E1 5B 94<br />
8E 47 2E 48 46 79 52 6B 04 2F 54 7F 32 89 11 54 32 BC A5 78<br />
66 4F 0E 16 A0 69 92 7D F2 44 63 F3 26 2C 4B BD D5 2D C9 3D<br />
3C 8D 43 64 AC 30 AD 80 CA E1 74 8D A6 26 EE 2D 69 7E C1 15<br />
33 A1 13 FD EC EA 99 A8 3B 1F 3D B7 ED CA 07 B0 B2 7B E9 4A<br />
41 2B 14 6A 3C E5 39 76 36 13 25 76 7B 01 0E 80 91 15 84 32<br />
3D 14 A6 02 B8 F0 03 A5 60 B1 42 C1 A4 AB 56 14 7F<br />
Exponent: 01 00 01<br />
Signature Length: 256 bytes / 2048 bits<br />
Signature: 00 5B 3C C2 55 62 1E 6B 2E 5A 16 90 41 01 0A 94 D3 00 10 1E<br />
C2 A2 28 7E AF C8 94 AE A9 90 9E CE 18 65 09 08 FA 5A 9C C1<br />
0B 98 3B D6 EC EC 76 27 98 FA FD 0C 08 57 3F AA 41 DD 5B EA<br />
42 B2 70 38 AA 11 DB 6A 96 03 EE B4 C5 FF 00 2F D1 1B DE 53<br />
60 BA B7 6C C8 D2 B2 C6 EB 19 E7 65 31 CD 37 33 28 29 72 6B<br />
BC 17 D5 3E 8E 3E E4 A6 F1 9F 99 69 64 72 EC 3C 11 2B A5 7F<br />
07 75 29 61 69 6C 30 C4 C3 71 B0 59 64 4B 09 75 1A 10 F5 3F<br />
81 19 81 00 FC E4 60 96 44 DD 97 B2 F0 AD BD E9 4B F5 53 7F<br />
8D 59 B0 FA 68 68 09 F2 52 FC 0D 49 12 89 31 A2 33 00 1E EE<br />
39 1E 3E F6 9C 44 BF A5 49 4A B9 47 E1 38 E9 1E E3 09 D0 4B<br />
42 98 3C DA D1 5C 51 9D 5F 68 91 40 87 B2 72 46 AB D1 D1 37<br />
E2 5A 82 BF F0 21 15 D3 B0 44 29 BE C8 E1 C4 44 F3 54 68 7A<br />
48 FD 71 25 38 9A 31 4C E8 D3 73 C4 20 3C 8E 04 86<br />
Extension: Subject Alternative Name (2.5.29.17)<br />
Critical: 0<br />
DNS: <strong>www</strong>.takti.co.il
DNS: takti.co.il<br />
Extension: Basic Constraints (2.5.29.19)<br />
Critical: 0<br />
Extension: CRL Distribution Points (2.5.29.31)<br />
Critical: 0<br />
URI: http://gp.symcb.com/gp.crl<br />
Extension: Policies (2.5.29.32)<br />
Critical: 0<br />
Policy ID #1: 2.23.140.1.2.1<br />
Qualifier ID #1: Certification Practice Statement (1.3.6.1.5.5.7.2.1)<br />
CPS URI: https://<strong>www</strong>.rapidssl.com/legal<br />
Extension: Authority Key Identifier (2.5.29.35)<br />
Critical: 0<br />
Key Identifier: 97 C2 27 50 9E C2 C9 EC 0C 88 32 C8 7C AD E2 A6 01 4F DA 6F<br />
Extension: Key Usage (2.5.29.15)<br />
Critical: 1<br />
Key Usage: Digital Signature, Key Encipherment<br />
Extension: Extended Key Usage (2.5.29.37)<br />
Critical: 0<br />
Purpose#1: Web Server Authentication (1.3.6.1.5.5.7.3.1)<br />
Purpose#2: Web Client Authentication (1.3.6.1.5.5.7.3.2)
Extension: Authority Information Access (1.3.6.1.5.5.7.1.1)<br />
Critical: 0<br />
Method#1: Online Certificate Status Protocol<br />
URI: http://gp.symcd.com<br />
Method#2: Certificate Authority Issuers<br />
URI: http://gp.symcb.com/gp.crt<br />
Extension: 1.3.6.1.4.1.11129.2.4.2<br />
Critical: 0<br />
Data: 04 82 01 E2 01 E0 00 77 00 DD EB 1D 2B 7A 0D 4F A6 20 8B 81<br />
AD 81 68 70 7E 2E 8E 9D 01 D5 5C 88 8D 3D 11 C4 CD B6 EC BE<br />
CC 00 00 01 55 B4 DA 4D 3A 00 00 04 03 00 48 30 46 02 21 00<br />
C5 24 07 C3 61 83 31 12 B6 34 6F 53 40 CB A0 4E F4 99 D9 96<br />
09 79 5F B7 32 E0 17 91 88 3F 9B EC 02 21 00 F4 58 87 EC B9<br />
70 81 24 06 28 66 21 05 44 C9 6C 8F C6 48 2A E6 E6 4A 75 EC<br />
15 89 11 58 F9 ED D9 00 75 00 A4 B9 09 90 B4 18 58 14 87 BB<br />
13 A2 CC 67 70 0A 3C 35 98 04 F9 1B DF B8 E3 77 CD 0E C8 0D<br />
DC 10 00 00 01 55 B4 DA 4D 6E 00 00 04 03 00 46 30 44 02 20<br />
51 A7 4A BC F4 96 66 1C EF A5 69 50 15 EF 39 62 5B D8 D9 47<br />
36 1D 6A 5B C5 62 B2 3A 15 A0 92 B4 02 20 7F AA 15 0A BC 1D<br />
F0 09 B4 E9 1C AC 05 66 E7 B8 94 66 1A 91 89 97 94 12 D1 B3<br />
84 2B F3 9D 2E 19 00 76 00 68 F6 98 F8 1F 64 82 BE 3A 8C EE<br />
B9 28 1D 4C FC 71 51 5D 67 93 D4 44 D1 0A 67 AC BB 4F 4F FB<br />
C4 00 00 01 55 B4 DA 4D 6A 00 00 04 03 00 47 30 45 02 21 00<br />
9F F4 24 E9 6A 38 85 EF 8A D6 65 FB 87 54 30 AF F0 01 05 40<br />
89 9E E6 C9 BC 50 9B 77 D0 30 99 EC 02 20 2D C1 4B 73 01 E0<br />
49 32 B1 F0 47 12 3C AD 29 42 43 4B 1F 76 66 AF F7 26 38 77<br />
A7 8F 89 B0 40 71 00 76 00 EE 4B BD B7 75 CE 60 BA E1 42 69<br />
1F AB E1 9E 66 A3 0F 7E 5F B0 72 D8 83 00 C4 7B 89 7A A8 FD<br />
CB 00 00 01 55 B4 DA 4F 35 00 00 04 03 00 47 30 45 02 21 00<br />
E1 31 92 AF C0 43 8A 52 00 6D AA 08 F0 34 7D 39 36 8F 89 07<br />
84 7C 48 EE F5 92 1D AE 74 26 F8 49 02 20 45 EE 43 19 1F 7F
2B 1C 97 13 1F CF 9F 50 BE 71 F3 BA 68 1A 3A 7A F1 7A 1A E5<br />
AE 9F 5E 0F F5 AA<br />
Fingerprints :<br />
SHA-256 Fingerprint: E4 24 F0 B2 D0 73 A5 D1 CC 86 C7 97 86 E2 94 57 69 C4 B4 68<br />
DA 3E D0 06 6A 9A 3C 93 91 83 DC A1<br />
SHA-1 Fingerprint: 86 5C 6B E8 4D 80 B2 91 11 50 61 9C 09 30 EF 84 A7 A2 1A 9C<br />
MD5 Fingerprint: 47 AB AE 17 9E 2D BD 33 7E 2C A3 88 E8 5D 01 95
Security Notes found on port/service "110 / tcp / pop3"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"SSL Certificate Information"<br />
Category<br />
Priority<br />
"General "<br />
"Low Priority<br />
Synopsis This plugin displays the SSL certificate.<br />
Description This plugin connects to every SSL-related port and attempts to extract and dump the X.509 certificate.<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
Subject Name:<br />
Country: US<br />
State/Province: Virginia<br />
Locality: Herndon<br />
Organization: Parallels<br />
Organization Unit: Parallels Panel<br />
Common Name: Parallels Panel<br />
Email Address: info@parallels.com<br />
Issuer Name:<br />
Country: US<br />
State/Province: Virginia<br />
Locality: Herndon<br />
Organization: Parallels<br />
Organization Unit: Parallels Panel<br />
Common Name: Parallels Panel<br />
Email Address: info@parallels.com<br />
Serial Number: 55 2B 60 34
Version: 1<br />
Signature Algorithm: SHA-1 With RSA Encryption<br />
Not Valid Before: Apr 13 06:20:36 2015 GMT<br />
Not Valid After: Apr 12 06:20:36 2016 GMT<br />
Public Key Info:<br />
Algorithm: RSA Encryption<br />
Key Length: 2048 bits<br />
Public Key: 00 A6 AD 66 0F 5D A6 09 2C 92 16 06 ED 1E D4 95 D2 10 34 BA<br />
FE 8C A9 25 25 66 15 01 CE 32 8B C2 CE BD 17 87 B1 DD AB 88<br />
61 EA 30 02 F5 5A EE 98 88 0C 52 C3 E0 A0 2A 9D FC 06 1F FD<br />
BE FD 46 20 C0 A9 48 BB 2A B3 FD B3 E6 90 48 44 45 F1 60 BC<br />
CE FA 8A CF E7 44 11 D0 71 20 53 28 28 E4 0C CF A1 57 41 E8<br />
AA 0F A2 55 6E DE B0 1D DC EB 9A 86 21 55 23 31 7D 11 4E 3A<br />
CC 7F 51 8E 68 8E B2 B7 F0 7A A5 7B C0 C9 CC 6F 9D 99 A0 DD<br />
EB 81 C1 20 93 1B 18 70 BE C9 C1 5E FE D3 38 60 07 81 67 F6<br />
A0 1D 9C 96 5F D3 8C 32 E7 5C 3A 2C FA 5E 92 B9 85 1D 84 F7<br />
49 20 9C D1 98 B8 8E BE E1 D6 72 45 E8 50 20 82 09 4E 8A 0B<br />
C7 2D F6 8D 10 FB 31 37 B7 D0 68 DB 02 37 0B 57 0F 62 1C 57<br />
C1 16 3F 24 6A 1F C0 55 10 92 6C 0B 21 0E 41 67 1A 86 EC 9E<br />
EE CF C8 BF 19 3D 68 89 06 D0 43 56 B6 B6 AF 3F E7<br />
Exponent: 01 00 01<br />
Signature Length: 256 bytes / 2048 bits<br />
Signature: 00 40 63 59 39 62 79 E0 E2 5A 04 8B EB CA 6D 60 A9 2E AB D5<br />
8F DB 56 8A C8 19 B1 62 8E 7A 88 85 F6 C1 E5 18 C1 6B C9 6A<br />
30 76 B1 DA 92 38 E8 CF D6 A3 94 D2 72 10 89 C8 89 60 C4 52<br />
D2 79 6E 99 BD CA 45 B1 00 56 8B F0 11 41 46 53 F3 D0 FA 42<br />
32 44 6D D2 46 E1 D0 06 DE 8D 2D 82 78 DF 89 32 D2 10 57 73<br />
4A B8 CB 69 1B 1B 4E FD F0 DD 15 3B F2 B5 E2 FE F4 75 2A FD<br />
6F CB A2 3D 6F DD EA 96 D2 CA 74 61 0D 41 35 1C 38 A2 C1 83
D0 91 64 EC E2 0B 0B 3D B6 90 98 2A 02 B7 AA EB 06 B8 3E 7B<br />
5D A7 F3 80 DC 39 84 39 34 1B 1D 66 FD 98 D6 DC 6D 33 EF 6C<br />
12 70 62 AF 74 17 7C 94 9D FB 9A 41 21 AC 5A 4B 9F 43 36 7C<br />
CE E6 73 4B BB 23 74 88 1D 96 9A 28 EA 1D B7 A5 F5 D3 FA 68<br />
BE 42 E6 4D 11 DF F9 DD D2 5D E7 DB CD 90 05 25 E0 17 14 6A<br />
21 67 C3 68 BF 8B D8 1F 49 D0 EF 1B 57 12 03 70 2A<br />
Fingerprints :<br />
SHA-256 Fingerprint: C5 C8 36 35 9D C3 F8 73 AD 99 34 58 B7 11 3B 16 CF EC 94 70<br />
BB B2 F2 63 42 F2 3D CA D1 43 89 CB<br />
SHA-1 Fingerprint: 8B 46 C6 56 3E 40 0D 0E 59 07 1C BF 0E DF 78 17 74 64 08 E8<br />
MD5 Fingerprint: 18 7A 3A 34 56 8D BA 40 01 E6 CE 61 BA B4 5A A2
Security Notes found on port/service "25 / tcp / smtp"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"SSL Certificate Information"<br />
Category<br />
Priority<br />
"General "<br />
"Low Priority<br />
Synopsis This plugin displays the SSL certificate.<br />
Description This plugin connects to every SSL-related port and attempts to extract and dump the X.509 certificate.<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
Subject Name:<br />
Country: US<br />
State/Province: Virginia<br />
Locality: Herndon<br />
Organization: Parallels<br />
Organization Unit: Parallels Panel<br />
Common Name: Parallels Panel<br />
Email Address: info@parallels.com<br />
Issuer Name:<br />
Country: US<br />
State/Province: Virginia<br />
Locality: Herndon<br />
Organization: Parallels<br />
Organization Unit: Parallels Panel<br />
Common Name: Parallels Panel<br />
Email Address: info@parallels.com<br />
Serial Number: 55 2B 60 34
Version: 1<br />
Signature Algorithm: SHA-1 With RSA Encryption<br />
Not Valid Before: Apr 13 06:20:36 2015 GMT<br />
Not Valid After: Apr 12 06:20:36 2016 GMT<br />
Public Key Info:<br />
Algorithm: RSA Encryption<br />
Key Length: 2048 bits<br />
Public Key: 00 A6 AD 66 0F 5D A6 09 2C 92 16 06 ED 1E D4 95 D2 10 34 BA<br />
FE 8C A9 25 25 66 15 01 CE 32 8B C2 CE BD 17 87 B1 DD AB 88<br />
61 EA 30 02 F5 5A EE 98 88 0C 52 C3 E0 A0 2A 9D FC 06 1F FD<br />
BE FD 46 20 C0 A9 48 BB 2A B3 FD B3 E6 90 48 44 45 F1 60 BC<br />
CE FA 8A CF E7 44 11 D0 71 20 53 28 28 E4 0C CF A1 57 41 E8<br />
AA 0F A2 55 6E DE B0 1D DC EB 9A 86 21 55 23 31 7D 11 4E 3A<br />
CC 7F 51 8E 68 8E B2 B7 F0 7A A5 7B C0 C9 CC 6F 9D 99 A0 DD<br />
EB 81 C1 20 93 1B 18 70 BE C9 C1 5E FE D3 38 60 07 81 67 F6<br />
A0 1D 9C 96 5F D3 8C 32 E7 5C 3A 2C FA 5E 92 B9 85 1D 84 F7<br />
49 20 9C D1 98 B8 8E BE E1 D6 72 45 E8 50 20 82 09 4E 8A 0B<br />
C7 2D F6 8D 10 FB 31 37 B7 D0 68 DB 02 37 0B 57 0F 62 1C 57<br />
C1 16 3F 24 6A 1F C0 55 10 92 6C 0B 21 0E 41 67 1A 86 EC 9E<br />
EE CF C8 BF 19 3D 68 89 06 D0 43 56 B6 B6 AF 3F E7<br />
Exponent: 01 00 01<br />
Signature Length: 256 bytes / 2048 bits<br />
Signature: 00 40 63 59 39 62 79 E0 E2 5A 04 8B EB CA 6D 60 A9 2E AB D5<br />
8F DB 56 8A C8 19 B1 62 8E 7A 88 85 F6 C1 E5 18 C1 6B C9 6A<br />
30 76 B1 DA 92 38 E8 CF D6 A3 94 D2 72 10 89 C8 89 60 C4 52<br />
D2 79 6E 99 BD CA 45 B1 00 56 8B F0 11 41 46 53 F3 D0 FA 42<br />
32 44 6D D2 46 E1 D0 06 DE 8D 2D 82 78 DF 89 32 D2 10 57 73<br />
4A B8 CB 69 1B 1B 4E FD F0 DD 15 3B F2 B5 E2 FE F4 75 2A FD<br />
6F CB A2 3D 6F DD EA 96 D2 CA 74 61 0D 41 35 1C 38 A2 C1 83
D0 91 64 EC E2 0B 0B 3D B6 90 98 2A 02 B7 AA EB 06 B8 3E 7B<br />
5D A7 F3 80 DC 39 84 39 34 1B 1D 66 FD 98 D6 DC 6D 33 EF 6C<br />
12 70 62 AF 74 17 7C 94 9D FB 9A 41 21 AC 5A 4B 9F 43 36 7C<br />
CE E6 73 4B BB 23 74 88 1D 96 9A 28 EA 1D B7 A5 F5 D3 FA 68<br />
BE 42 E6 4D 11 DF F9 DD D2 5D E7 DB CD 90 05 25 E0 17 14 6A<br />
21 67 C3 68 BF 8B D8 1F 49 D0 EF 1B 57 12 03 70 2A<br />
Fingerprints :<br />
SHA-256 Fingerprint: C5 C8 36 35 9D C3 F8 73 AD 99 34 58 B7 11 3B 16 CF EC 94 70<br />
BB B2 F2 63 42 F2 3D CA D1 43 89 CB<br />
SHA-1 Fingerprint: 8B 46 C6 56 3E 40 0D 0E 59 07 1C BF 0E DF 78 17 74 64 08 E8<br />
MD5 Fingerprint: 18 7A 3A 34 56 8D BA 40 01 E6 CE 61 BA B4 5A A2
Security Notes found on port/service "110 / tcp / pop3"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"POP Server Detection"<br />
Category<br />
"Service detection "<br />
Priority "Low Priority<br />
Synopsis A POP server is listening on the remote port.<br />
Description The remote host is running a server that understands the Post Office Protocol (POP), used by email clients to<br />
retrieve messages from a server, possibly across a network link.<br />
See also:<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output Remote POP server banner :<br />
http://en.wikipedia.org/wiki/Post_Office_Protocol<br />
+OK Hello there. <br />
Solution Disable this service if you do not use it.
Security Notes found on port/service "110 / tcp / pop3"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"OpenSSL AES-NI Padding Oracle MitM Information Disclosure"<br />
Category<br />
"General "<br />
Priority "Low Priority<br />
Synopsis It was possible to obtain sensitive information from the remote host with TLS-enabled services.<br />
Description The remote host is affected by a man-in-the-middle (MitM) information disclosure vulnerability due to an error in the<br />
implementation of ciphersuites that use AES in CBC mode with HMAC-SHA1 or HMAC-SHA256.<br />
The implementation is specially written to use the AES acceleration available in x86/amd64 processors (AES-NI). The<br />
error messages returned by the server allow allow a man-in-the-middle attacker to conduct a padding oracle attack,<br />
resulting in the ability to decrypt network traffic.<br />
See also:<br />
https://blog.filippo.io/luckyminus20/<br />
http://<strong>www</strong>.nessus.org/u?37b909b6<br />
https://<strong>www</strong>.openssl.org/news/secadv/20160503.txt<br />
Risk factor LOW / CVSS BASE SCORE :2.6 CVSS2#AV:N/AC:H/Au:N/C:P/I:N/A:N<br />
Plugin<br />
output<br />
Addition<br />
Information<br />
Nessus was able to trigger a RECORD_OVERFLOW alert in the<br />
remote service by sending a crafted SSL "Finished" message.<br />
CVE:<br />
http://cgi.nessus.org/cve.php3?cve=CVE-2016-2107<br />
Other references { osvdb : 137896edb-id : 39768iava : 2016-A-0113 }<br />
Solution Upgrade to OpenSSL version 1.0.1t / 1.0.2h or later.
Security Notes found on port/service "443 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"OpenSSL AES-NI Padding Oracle MitM Information Disclosure"<br />
Category<br />
"General "<br />
Priority "Low Priority<br />
Synopsis It was possible to obtain sensitive information from the remote host with TLS-enabled services.<br />
Description The remote host is affected by a man-in-the-middle (MitM) information disclosure vulnerability due to an error in the<br />
implementation of ciphersuites that use AES in CBC mode with HMAC-SHA1 or HMAC-SHA256.<br />
The implementation is specially written to use the AES acceleration available in x86/amd64 processors (AES-NI). The<br />
error messages returned by the server allow allow a man-in-the-middle attacker to conduct a padding oracle attack,<br />
resulting in the ability to decrypt network traffic.<br />
See also:<br />
https://blog.filippo.io/luckyminus20/<br />
http://<strong>www</strong>.nessus.org/u?37b909b6<br />
https://<strong>www</strong>.openssl.org/news/secadv/20160503.txt<br />
Risk factor LOW / CVSS BASE SCORE :2.6 CVSS2#AV:N/AC:H/Au:N/C:P/I:N/A:N<br />
Plugin<br />
output<br />
Addition<br />
Information<br />
Nessus was able to trigger a RECORD_OVERFLOW alert in the<br />
remote service by sending a crafted SSL "Finished" message.<br />
CVE:<br />
http://cgi.nessus.org/cve.php3?cve=CVE-2016-2107<br />
Other references { osvdb : 137896edb-id : 39768iava : 2016-A-0113 }<br />
Solution Upgrade to OpenSSL version 1.0.1t / 1.0.2h or later.
Security Notes found on port/service "25 / tcp / smtp"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"OpenSSL AES-NI Padding Oracle MitM Information Disclosure"<br />
Category<br />
"General "<br />
Priority "Low Priority<br />
Synopsis It was possible to obtain sensitive information from the remote host with TLS-enabled services.<br />
Description The remote host is affected by a man-in-the-middle (MitM) information disclosure vulnerability due to an error in the<br />
implementation of ciphersuites that use AES in CBC mode with HMAC-SHA1 or HMAC-SHA256.<br />
The implementation is specially written to use the AES acceleration available in x86/amd64 processors (AES-NI). The<br />
error messages returned by the server allow allow a man-in-the-middle attacker to conduct a padding oracle attack,<br />
resulting in the ability to decrypt network traffic.<br />
See also:<br />
https://blog.filippo.io/luckyminus20/<br />
http://<strong>www</strong>.nessus.org/u?37b909b6<br />
https://<strong>www</strong>.openssl.org/news/secadv/20160503.txt<br />
Risk factor LOW / CVSS BASE SCORE :2.6 CVSS2#AV:N/AC:H/Au:N/C:P/I:N/A:N<br />
Plugin<br />
output<br />
Addition<br />
Information<br />
Nessus was able to trigger a RECORD_OVERFLOW alert in the<br />
remote service by sending a crafted SSL "Finished" message.<br />
CVE:<br />
http://cgi.nessus.org/cve.php3?cve=CVE-2016-2107<br />
Other references { osvdb : 137896edb-id : 39768iava : 2016-A-0113 }<br />
Solution Upgrade to OpenSSL version 1.0.1t / 1.0.2h or later.
Security Notes found on port/service "110 / tcp / pop3"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"SSL Certificate Signed Using SHA-1 Algorithm"<br />
Category<br />
"General "<br />
Priority "Low Priority<br />
Synopsis An SSL certificate in the certificate chain has been signed using the SHA-1 hashing algorithm.<br />
Description The remote service uses an SSL certificate chain that has been signed with SHA-1, a cryptographically weak<br />
hashing algorithm. This signature algorithm is known to be vulnerable to collision attacks. An attacker can exploit this<br />
to generate another certificate with the same digital signature, allowing an attacker to masquerade as the affected<br />
service.<br />
Note that this plugin reports all SSL certificate chains signed with SHA-1 that expire on or between January 1, 2016<br />
and December 31, 2016 as informational. This is in accordance with Google's gradual sunsetting of the SHA-1<br />
cryptographic hash algorithm.<br />
Note that certificates in the chain that are contained in the Nessus CA database have been ignored.<br />
See also:<br />
http://blog.chromium.org/2014/09/gradually-sunsetting-sha-1.html<br />
http://tools.ietf.org/html/rfc3279<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
The following certificates were part of the certificate chain sent by<br />
the remote host, but contain hashes that are considered to be weak.<br />
|-Subject : C=US/ST=Virginia/L=Herndon/O=Parallels/OU=Parallels Panel/CN=Parallels Panel/E=info@parallels.<br />
com<br />
|-Signature Algorithm : SHA-1 With RSA Encryption<br />
|-Valid From : Apr 13 06:20:36 2015 GMT<br />
|-Valid To : Apr 12 06:20:36 2016 GMT
Security Notes found on port/service "25 / tcp / smtp"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"SSL Certificate Signed Using SHA-1 Algorithm"<br />
Category<br />
"General "<br />
Priority "Low Priority<br />
Synopsis An SSL certificate in the certificate chain has been signed using the SHA-1 hashing algorithm.<br />
Description The remote service uses an SSL certificate chain that has been signed with SHA-1, a cryptographically weak<br />
hashing algorithm. This signature algorithm is known to be vulnerable to collision attacks. An attacker can exploit this<br />
to generate another certificate with the same digital signature, allowing an attacker to masquerade as the affected<br />
service.<br />
Note that this plugin reports all SSL certificate chains signed with SHA-1 that expire on or between January 1, 2016<br />
and December 31, 2016 as informational. This is in accordance with Google's gradual sunsetting of the SHA-1<br />
cryptographic hash algorithm.<br />
Note that certificates in the chain that are contained in the Nessus CA database have been ignored.<br />
See also:<br />
http://blog.chromium.org/2014/09/gradually-sunsetting-sha-1.html<br />
http://tools.ietf.org/html/rfc3279<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
The following certificates were part of the certificate chain sent by<br />
the remote host, but contain hashes that are considered to be weak.<br />
|-Subject : C=US/ST=Virginia/L=Herndon/O=Parallels/OU=Parallels Panel/CN=Parallels Panel/E=info@parallels.<br />
com<br />
|-Signature Algorithm : SHA-1 With RSA Encryption<br />
|-Valid From : Apr 13 06:20:36 2015 GMT<br />
|-Valid To : Apr 12 06:20:36 2016 GMT
Security Notes found on port/service "110 / tcp / pop3"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"OpenSSL Detection"<br />
Category<br />
"Service detection "<br />
Priority "Low Priority<br />
Synopsis The remote service appears to use OpenSSL to encrypt traffic.<br />
Description Based on its response to a TLS request with a specially crafted server name extension, it seems that the remote<br />
service is using the OpenSSL library to encrypt traffic.<br />
Note that this plugin can only detect OpenSSL implementations that have enabled support for TLS extensions (RFC<br />
4366).<br />
See also:<br />
http://<strong>www</strong>.openssl.org<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null
Security Notes found on port/service "443 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"OpenSSL Detection"<br />
Category<br />
"Service detection "<br />
Priority "Low Priority<br />
Synopsis The remote service appears to use OpenSSL to encrypt traffic.<br />
Description Based on its response to a TLS request with a specially crafted server name extension, it seems that the remote<br />
service is using the OpenSSL library to encrypt traffic.<br />
Note that this plugin can only detect OpenSSL implementations that have enabled support for TLS extensions (RFC<br />
4366).<br />
See also:<br />
http://<strong>www</strong>.openssl.org<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null
Security Notes found on port/service "25 / tcp / smtp"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"OpenSSL Detection"<br />
Category<br />
"Service detection "<br />
Priority "Low Priority<br />
Synopsis The remote service appears to use OpenSSL to encrypt traffic.<br />
Description Based on its response to a TLS request with a specially crafted server name extension, it seems that the remote<br />
service is using the OpenSSL library to encrypt traffic.<br />
Note that this plugin can only detect OpenSSL implementations that have enabled support for TLS extensions (RFC<br />
4366).<br />
See also:<br />
http://<strong>www</strong>.openssl.org<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null
Security Notes found on port/service "80 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"Service Detection"<br />
Category<br />
"Service detection "<br />
Priority "Low Priority<br />
Synopsis The remote service could be identified.<br />
Description Nessus was able to identify the remote service by its banner or by looking at the error message it sends when it<br />
receives an HTTP request.<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
A web server is running on this port.
Security Notes found on port/service "8880 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"Service Detection"<br />
Category<br />
"Service detection "<br />
Priority "Low Priority<br />
Synopsis The remote service could be identified.<br />
Description Nessus was able to identify the remote service by its banner or by looking at the error message it sends when it<br />
receives an HTTP request.<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
A web server is running on this port.
Security Notes found on port/service "443 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"Service Detection"<br />
Category<br />
"Service detection "<br />
Priority "Low Priority<br />
Synopsis The remote service could be identified.<br />
Description Nessus was able to identify the remote service by its banner or by looking at the error message it sends when it<br />
receives an HTTP request.<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
A web server is running on this port through TLSv1.
Security Notes found on port/service "443 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"Service Detection"<br />
Category<br />
"Service detection "<br />
Priority "Low Priority<br />
Synopsis The remote service could be identified.<br />
Description Nessus was able to identify the remote service by its banner or by looking at the error message it sends when it<br />
receives an HTTP request.<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
A TLSv1 server answered on this port.
Security Notes found on port/service "110 / tcp / pop3"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"Service Detection"<br />
Category<br />
"Service detection "<br />
Priority "Low Priority<br />
Synopsis The remote service could be identified.<br />
Description Nessus was able to identify the remote service by its banner or by looking at the error message it sends when it<br />
receives an HTTP request.<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
A POP3 server is running on this port.
Security Notes found on port/service "25 / tcp / smtp"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"Service Detection"<br />
Category<br />
"Service detection "<br />
Priority "Low Priority<br />
Synopsis The remote service could be identified.<br />
Description Nessus was able to identify the remote service by its banner or by looking at the error message it sends when it<br />
receives an HTTP request.<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
An SMTP server is running on this port.
Security Notes found on port/service "0 / tcp / "<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"TCP/IP Timestamps Supported"<br />
Category<br />
"General "<br />
Priority "Low Priority<br />
Synopsis The remote service implements TCP timestamps.<br />
Description The remote host implements TCP timestamps, as defined by RFC1323. A side effect of this feature is that the<br />
uptime of the remote host can sometimes be computed.<br />
See also:<br />
http://<strong>www</strong>.ietf.org/rfc/rfc1323.txt<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null
Security Notes found on port/service "25 / tcp / smtp"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"SSL Anonymous Cipher Suites Supported"<br />
Category<br />
"Service detection "<br />
Priority "Low Priority<br />
Synopsis The remote service supports the use of anonymous SSL ciphers.<br />
Description The remote host supports the use of anonymous SSL ciphers. While this enables an administrator to set up a<br />
service that encrypts traffic without having to generate and configure SSL certificates, it offers no way to verify the<br />
remote host's identity and renders the service vulnerable to a man-in-the-middle attack.<br />
Note: This is considerably easier to exploit if the attacker is on the same physical network.<br />
See also:<br />
http://<strong>www</strong>.openssl.org/docs/apps/ciphers.html<br />
Risk factor CVE-2007-1858 - Low / CVSS BASE SCORE :2.6 CVSS2#(AV:N/AC:H/Au:N/C:P/I:N/A:N)<br />
Plugin<br />
output Here is the list of SSL anonymous ciphers supported by the remote server :<br />
Low Strength Ciphers (= 112-bit key)<br />
TLSv1<br />
ADH-DES-CBC3-SHA Kx=DH Au=None Enc=3DES-CBC(168) Mac=SHA1<br />
ADH-AES128-SHA Kx=DH Au=None Enc=AES-CBC(128) Mac=SHA1<br />
ADH-AES256-SHA Kx=DH Au=None Enc=AES-CBC(256) Mac=SHA1<br />
ADH-CAMELLIA128-SHA Kx=DH Au=None Enc=Camellia-CBC(128) Mac=SHA1
ADH-CAMELLIA256-SHA Kx=DH Au=None Enc=Camellia-CBC(256) Mac=SHA1<br />
ADH-RC4-MD5 Kx=DH Au=None Enc=RC4(128) Mac=MD5<br />
ADH-SEED-SHA Kx=DH Au=None Enc=SEED-CBC(128) Mac=SHA1<br />
AECDH-DES-CBC3-SHA Kx=ECDH Au=None Enc=3DES-CBC(168) Mac=SHA1<br />
AECDH-AES128-SHA Kx=ECDH Au=None Enc=AES-CBC(128) Mac=SHA1<br />
AECDH-AES256-SHA Kx=ECDH Au=None Enc=AES-CBC(256) Mac=SHA1<br />
AECDH-RC4-SHA Kx=ECDH Au=None Enc=RC4(128) Mac=SHA1<br />
DH-AES128-SHA256 Kx=DH Au=None Enc=AES-CBC(128) Mac=SHA256<br />
DH-AES256-SHA256 Kx=DH Au=None Enc=AES-CBC(256) Mac=SHA256<br />
TLSv12<br />
DH-AES128-SHA256 Kx=DH Au=None Enc=AES-GCM(128) Mac=SHA256<br />
DH-AES256-SHA384 Kx=DH Au=None Enc=AES-GCM(256) Mac=SHA384<br />
The fields above are :<br />
{OpenSSL ciphername}<br />
Kx={key exchange}<br />
Au={authentication}<br />
Enc={symmetric encryption method}<br />
Mac={message authentication code}<br />
{export flag}<br />
Addition<br />
Information<br />
CVE:<br />
http://cgi.nessus.org/cve.php3?cve=CVE-2007-1858<br />
BID : 28482 Other references { osvdb : 34882 }<br />
Solution Reconfigure the affected application if possible to avoid use of weak ciphers.
Security Notes found on port/service "443 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"SSL Certificate Chain Not Sorted"<br />
Category<br />
"General "<br />
Priority "Low Priority<br />
Synopsis The X.509 certificate chain used by this service contains certificates that aren't in order.<br />
Description At least one of the X.509 certificates sent by the remote host is not in order. Some certificate authorities publish<br />
certificate bundles that are in descending instead of ascending order, which is incorrect according to RFC 4346,<br />
Section 7.4.2.<br />
Some SSL implementations, often those found in embedded devices, cannot handle unordered certificate chains.<br />
See also:<br />
http://<strong>www</strong>.ietf.org/rfc/rfc4346.txt<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output The certificate chain sent by the remote host is not in order :<br />
|-Subject : C=US/O=GeoTrust Inc./CN=RapidSSL SHA256 CA - G3<br />
|-Issuer : C=US/O=GeoTrust Inc./CN=GeoTrust Global CA<br />
|<br />
|--Subject : CN=<strong>www</strong>.takti.co.il<br />
|--Issuer : C=US/O=GeoTrust Inc./CN=RapidSSL SHA256 CA<br />
Solution Reorder the certificates in the certificate chain.
Security Notes found on port/service "110 / tcp / pop3"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"SSL / TLS Versions Supported"<br />
Category<br />
"General "<br />
Priority "Low Priority<br />
Synopsis The remote service encrypts communications.<br />
Description This plugin detects which SSL and TLS versions are supported by the remote service for encrypting<br />
communications.<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
This port supports TLSv1.0/TLSv1.1/TLSv1.2.
Security Notes found on port/service "443 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"SSL / TLS Versions Supported"<br />
Category<br />
"General "<br />
Priority "Low Priority<br />
Synopsis The remote service encrypts communications.<br />
Description This plugin detects which SSL and TLS versions are supported by the remote service for encrypting<br />
communications.<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
This port supports SSLv2/SSLv3/TLSv1.0/TLSv1.1/TLSv1.2.
Security Notes found on port/service "25 / tcp / smtp"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"SSL / TLS Versions Supported"<br />
Category<br />
"General "<br />
Priority "Low Priority<br />
Synopsis The remote service encrypts communications.<br />
Description This plugin detects which SSL and TLS versions are supported by the remote service for encrypting<br />
communications.<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
This port supports SSLv2/SSLv3/TLSv1.0/TLSv1.1/TLSv1.2.
Security Notes found on port/service "443 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"SSL Perfect Forward Secrecy Cipher Suites Supported"<br />
Category<br />
"General "<br />
Priority "Low Priority<br />
Synopsis The remote service supports the use of SSL Perfect Forward Secrecy ciphers, which maintain confidentiality even if<br />
Description the key is stolen.<br />
The remote host supports the use of SSL ciphers that offer Perfect Forward Secrecy (PFS) encryption. These cipher<br />
suites ensure that recorded SSL traffic cannot be broken at a future date if the server's private key is compromised.<br />
See also:<br />
http://<strong>www</strong>.openssl.org/docs/apps/ciphers.html<br />
http://en.wikipedia.org/wiki/Diffie-Hellman_key_exchange<br />
http://en.wikipedia.org/wiki/Perfect_forward_secrecy<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output Here is the list of SSL PFS ciphers supported by the remote server :<br />
High Strength Ciphers (>= 112-bit key)<br />
TLSv1<br />
ECDHE-RSA-DES-CBC3-SHA Kx=ECDH Au=RSA Enc=3DES-CBC(168) Mac=SHA1<br />
ECDHE-RSA-AES128-SHA Kx=ECDH Au=RSA Enc=AES-CBC(128) Mac=SHA1<br />
ECDHE-RSA-AES256-SHA Kx=ECDH Au=RSA Enc=AES-CBC(256) Mac=SHA1<br />
ECDHE-RSA-AES128-SHA256 Kx=ECDHE Au=RSA Enc=AES-CBC(128) Mac=SHA256<br />
ECDHE-RSA-AES256-SHA384 Kx=ECDHE Au=RSA Enc=AES-CBC(256) Mac=SHA384<br />
TLSv12<br />
ECDHE-RSA-AES128-SHA256 Kx=ECDHE Au=RSA Enc=AES-GCM(128) Mac=SHA256<br />
ECDHE-RSA-AES256-SHA384 Kx=ECDHE Au=RSA Enc=AES-GCM(256) Mac=SHA384
The fields above are :<br />
{OpenSSL ciphername}<br />
Kx={key exchange}<br />
Au={authentication}<br />
Enc={symmetric encryption method}<br />
Mac={message authentication code}<br />
{export flag}
Security Notes found on port/service "110 / tcp / pop3"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"SSL Perfect Forward Secrecy Cipher Suites Supported"<br />
Category<br />
"General "<br />
Priority "Low Priority<br />
Synopsis The remote service supports the use of SSL Perfect Forward Secrecy ciphers, which maintain confidentiality even if<br />
Description the key is stolen.<br />
The remote host supports the use of SSL ciphers that offer Perfect Forward Secrecy (PFS) encryption. These cipher<br />
suites ensure that recorded SSL traffic cannot be broken at a future date if the server's private key is compromised.<br />
See also:<br />
http://<strong>www</strong>.openssl.org/docs/apps/ciphers.html<br />
http://en.wikipedia.org/wiki/Diffie-Hellman_key_exchange<br />
http://en.wikipedia.org/wiki/Perfect_forward_secrecy<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output Here is the list of SSL PFS ciphers supported by the remote server :<br />
High Strength Ciphers (>= 112-bit key)<br />
TLSv1<br />
EDH-RSA-DES-CBC3-SHA Kx=DH Au=RSA Enc=3DES-CBC(168) Mac=SHA1<br />
DHE-RSA-AES128-SHA Kx=DH Au=RSA Enc=AES-CBC(128) Mac=SHA1<br />
DHE-RSA-AES256-SHA Kx=DH Au=RSA Enc=AES-CBC(256) Mac=SHA1<br />
DHE-RSA-CAMELLIA128-SHA Kx=DH Au=RSA Enc=Camellia-CBC(128) Mac=SHA1<br />
DHE-RSA-CAMELLIA256-SHA Kx=DH Au=RSA Enc=Camellia-CBC(256) Mac=SHA1<br />
DHE-RSA-AES128-SHA256 Kx=DH Au=RSA Enc=AES-CBC(128) Mac=SHA256<br />
DHE-RSA-AES256-SHA256 Kx=DH Au=RSA Enc=AES-CBC(256) Mac=SHA256<br />
TLSv12<br />
DHE-RSA-AES128-SHA256 Kx=DH Au=RSA Enc=AES-GCM(128) Mac=SHA256
DHE-RSA-AES256-SHA384 Kx=DH Au=RSA Enc=AES-GCM(256) Mac=SHA384<br />
The fields above are :<br />
{OpenSSL ciphername}<br />
Kx={key exchange}<br />
Au={authentication}<br />
Enc={symmetric encryption method}<br />
Mac={message authentication code}<br />
{export flag}
Security Notes found on port/service "25 / tcp / smtp"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"SSL Perfect Forward Secrecy Cipher Suites Supported"<br />
Category<br />
"General "<br />
Priority "Low Priority<br />
Synopsis The remote service supports the use of SSL Perfect Forward Secrecy ciphers, which maintain confidentiality even if<br />
Description the key is stolen.<br />
The remote host supports the use of SSL ciphers that offer Perfect Forward Secrecy (PFS) encryption. These cipher<br />
suites ensure that recorded SSL traffic cannot be broken at a future date if the server's private key is compromised.<br />
See also:<br />
http://<strong>www</strong>.openssl.org/docs/apps/ciphers.html<br />
http://en.wikipedia.org/wiki/Diffie-Hellman_key_exchange<br />
http://en.wikipedia.org/wiki/Perfect_forward_secrecy<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output Here is the list of SSL PFS ciphers supported by the remote server :<br />
Low Strength Ciphers (= 112-bit key)<br />
TLSv1<br />
EDH-RSA-DES-CBC3-SHA Kx=DH Au=RSA Enc=3DES-CBC(168) Mac=SHA1<br />
DHE-RSA-AES128-SHA Kx=DH Au=RSA Enc=AES-CBC(128) Mac=SHA1<br />
DHE-RSA-AES256-SHA Kx=DH Au=RSA Enc=AES-CBC(256) Mac=SHA1<br />
DHE-RSA-CAMELLIA128-SHA Kx=DH Au=RSA Enc=Camellia-CBC(128) Mac=SHA1
DHE-RSA-CAMELLIA256-SHA Kx=DH Au=RSA Enc=Camellia-CBC(256) Mac=SHA1<br />
DHE-RSA-SEED-SHA Kx=DH Au=RSA Enc=SEED-CBC(128) Mac=SHA1<br />
ECDHE-RSA-DES-CBC3-SHA Kx=ECDH Au=RSA Enc=3DES-CBC(168) Mac=SHA1<br />
ECDHE-RSA-AES128-SHA Kx=ECDH Au=RSA Enc=AES-CBC(128) Mac=SHA1<br />
ECDHE-RSA-AES256-SHA Kx=ECDH Au=RSA Enc=AES-CBC(256) Mac=SHA1<br />
ECDHE-RSA-RC4-SHA Kx=ECDH Au=RSA Enc=RC4(128) Mac=SHA1<br />
DHE-RSA-AES128-SHA256 Kx=DH Au=RSA Enc=AES-CBC(128) Mac=SHA256<br />
DHE-RSA-AES256-SHA256 Kx=DH Au=RSA Enc=AES-CBC(256) Mac=SHA256<br />
ECDHE-RSA-AES128-SHA256 Kx=ECDHE Au=RSA Enc=AES-CBC(128) Mac=SHA256<br />
ECDHE-RSA-AES256-SHA384 Kx=ECDHE Au=RSA Enc=AES-CBC(256) Mac=SHA384<br />
TLSv12<br />
DHE-RSA-AES128-SHA256 Kx=DH Au=RSA Enc=AES-GCM(128) Mac=SHA256<br />
DHE-RSA-AES256-SHA384 Kx=DH Au=RSA Enc=AES-GCM(256) Mac=SHA384<br />
ECDHE-RSA-AES128-SHA256 Kx=ECDHE Au=RSA Enc=AES-GCM(128) Mac=SHA256<br />
ECDHE-RSA-AES256-SHA384 Kx=ECDHE Au=RSA Enc=AES-GCM(256) Mac=SHA384<br />
The fields above are :<br />
{OpenSSL ciphername}<br />
Kx={key exchange}<br />
Au={authentication}<br />
Enc={symmetric encryption method}<br />
Mac={message authentication code}<br />
{export flag}
Security Notes found on port/service "8880 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"HTTP Server Type and Version"<br />
Category<br />
Priority<br />
"Web Servers "<br />
"Low Priority<br />
Synopsis A web server is running on the remote host.<br />
Description This plugin attempts to determine the type and the version of the remote web server.<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
The remote web server type is :<br />
sw-cp-server
Security Notes found on port/service "80 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"HTTP Server Type and Version"<br />
Category<br />
Priority<br />
"Web Servers "<br />
"Low Priority<br />
Synopsis A web server is running on the remote host.<br />
Description This plugin attempts to determine the type and the version of the remote web server.<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
The remote web server type is :<br />
nginx
Security Notes found on port/service "443 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"HTTP Server Type and Version"<br />
Category<br />
Priority<br />
"Web Servers "<br />
"Low Priority<br />
Synopsis A web server is running on the remote host.<br />
Description This plugin attempts to determine the type and the version of the remote web server.<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
The remote web server type is :<br />
nginx
Security Notes found on port/service "80 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"Web Server Harvested Email Addresses"<br />
Category<br />
Priority<br />
"Web Servers "<br />
"Low Priority<br />
Synopsis Email addresses were harvested from the web server.<br />
Description Nessus harvested HREF mailto: links and extracted email addresses by crawling the remote web server.<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
The following email address has been gathered :<br />
- 'callme@takti.co.il', referenced from :<br />
/<br />
/BuildaGate5/general2/company_search_tree.php
Security Notes found on port/service "443 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"Web Server Harvested Email Addresses"<br />
Category<br />
Priority<br />
"Web Servers "<br />
"Low Priority<br />
Synopsis Email addresses were harvested from the web server.<br />
Description Nessus harvested HREF mailto: links and extracted email addresses by crawling the remote web server.<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
The following email address has been gathered :<br />
- 'callme@takti.co.il', referenced from :<br />
/<br />
/BuildaGate5/general2/company_search_tree.php
Security Notes found on port/service "110 / tcp / pop3"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"SSL Certificate commonName Mismatch"<br />
Category<br />
"General "<br />
Priority "Low Priority<br />
Synopsis The SSL certificate commonName does not match the host name.<br />
Description This service presents an SSL certificate for which the 'commonName' (CN) does not match the host name on which<br />
the service listens.<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output The host name known by Nessus is :<br />
<strong>www</strong>.takti.co.il<br />
The Common Name in the certificate is :<br />
parallels panel<br />
Solution If the machine has several names, make sure that users connect to the service through the DNS host name that<br />
matches the common name in the certificate.
Security Notes found on port/service "25 / tcp / smtp"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"SSL Certificate commonName Mismatch"<br />
Category<br />
"General "<br />
Priority "Low Priority<br />
Synopsis The SSL certificate commonName does not match the host name.<br />
Description This service presents an SSL certificate for which the 'commonName' (CN) does not match the host name on which<br />
the service listens.<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output The host name known by Nessus is :<br />
<strong>www</strong>.takti.co.il<br />
The Common Name in the certificate is :<br />
parallels panel<br />
Solution If the machine has several names, make sure that users connect to the service through the DNS host name that<br />
matches the common name in the certificate.
Security Notes found on port/service "443 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"SSL Cipher Block Chaining Cipher Suites Supported"<br />
Category<br />
"General "<br />
Priority "Low Priority<br />
Synopsis The remote service supports the use of SSL Cipher Block Chaining ciphers, which combine previous blocks with<br />
Description subsequent ones.<br />
The remote host supports the use of SSL ciphers that operate in Cipher Block Chaining (CBC) mode. These cipher<br />
suites offer additional security over Electronic Codebook (ECB) mode, but have the potential to leak information if<br />
used improperly.<br />
See also:<br />
http://<strong>www</strong>.openssl.org/docs/apps/ciphers.html<br />
http://<strong>www</strong>.nessus.org/u?cc4a822a<br />
http://<strong>www</strong>.openssl.org/~bodo/tls-cbc.txt<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output Here is the list of SSL CBC ciphers supported by the remote server :<br />
High Strength Ciphers (>= 112-bit key)<br />
TLSv1<br />
ECDHE-RSA-DES-CBC3-SHA Kx=ECDH Au=RSA Enc=3DES-CBC(168) Mac=SHA1<br />
ECDHE-RSA-AES128-SHA Kx=ECDH Au=RSA Enc=AES-CBC(128) Mac=SHA1<br />
ECDHE-RSA-AES256-SHA Kx=ECDH Au=RSA Enc=AES-CBC(256) Mac=SHA1<br />
DES-CBC3-SHA Kx=RSA Au=RSA Enc=3DES-CBC(168) Mac=SHA1<br />
AES128-SHA Kx=RSA Au=RSA Enc=AES-CBC(128) Mac=SHA1<br />
AES256-SHA Kx=RSA Au=RSA Enc=AES-CBC(256) Mac=SHA1<br />
CAMELLIA128-SHA Kx=RSA Au=RSA Enc=Camellia-CBC(128) Mac=SHA1<br />
CAMELLIA256-SHA Kx=RSA Au=RSA Enc=Camellia-CBC(256) Mac=SHA1<br />
ECDHE-RSA-AES128-SHA256 Kx=ECDHE Au=RSA Enc=AES-CBC(128) Mac=SHA256
ECDHE-RSA-AES256-SHA384 Kx=ECDHE Au=RSA Enc=AES-CBC(256) Mac=SHA384<br />
RSA-AES128-SHA256 Kx=RSA Au=RSA Enc=AES-CBC(128) Mac=SHA256<br />
RSA-AES256-SHA256 Kx=RSA Au=RSA Enc=AES-CBC(256) Mac=SHA256<br />
The fields above are :<br />
{OpenSSL ciphername}<br />
Kx={key exchange}<br />
Au={authentication}<br />
Enc={symmetric encryption method}<br />
Mac={message authentication code}<br />
{export flag}
Security Notes found on port/service "110 / tcp / pop3"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"SSL Cipher Block Chaining Cipher Suites Supported"<br />
Category<br />
"General "<br />
Priority "Low Priority<br />
Synopsis The remote service supports the use of SSL Cipher Block Chaining ciphers, which combine previous blocks with<br />
Description subsequent ones.<br />
The remote host supports the use of SSL ciphers that operate in Cipher Block Chaining (CBC) mode. These cipher<br />
suites offer additional security over Electronic Codebook (ECB) mode, but have the potential to leak information if<br />
used improperly.<br />
See also:<br />
http://<strong>www</strong>.openssl.org/docs/apps/ciphers.html<br />
http://<strong>www</strong>.nessus.org/u?cc4a822a<br />
http://<strong>www</strong>.openssl.org/~bodo/tls-cbc.txt<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output Here is the list of SSL CBC ciphers supported by the remote server :<br />
High Strength Ciphers (>= 112-bit key)<br />
TLSv1<br />
EDH-RSA-DES-CBC3-SHA Kx=DH Au=RSA Enc=3DES-CBC(168) Mac=SHA1<br />
DHE-RSA-AES128-SHA Kx=DH Au=RSA Enc=AES-CBC(128) Mac=SHA1<br />
DHE-RSA-AES256-SHA Kx=DH Au=RSA Enc=AES-CBC(256) Mac=SHA1<br />
DHE-RSA-CAMELLIA128-SHA Kx=DH Au=RSA Enc=Camellia-CBC(128) Mac=SHA1<br />
DHE-RSA-CAMELLIA256-SHA Kx=DH Au=RSA Enc=Camellia-CBC(256) Mac=SHA1<br />
DES-CBC3-SHA Kx=RSA Au=RSA Enc=3DES-CBC(168) Mac=SHA1<br />
AES128-SHA Kx=RSA Au=RSA Enc=AES-CBC(128) Mac=SHA1<br />
AES256-SHA Kx=RSA Au=RSA Enc=AES-CBC(256) Mac=SHA1<br />
CAMELLIA128-SHA Kx=RSA Au=RSA Enc=Camellia-CBC(128) Mac=SHA1
CAMELLIA256-SHA Kx=RSA Au=RSA Enc=Camellia-CBC(256) Mac=SHA1<br />
DHE-RSA-AES128-SHA256 Kx=DH Au=RSA Enc=AES-CBC(128) Mac=SHA256<br />
DHE-RSA-AES256-SHA256 Kx=DH Au=RSA Enc=AES-CBC(256) Mac=SHA256<br />
RSA-AES128-SHA256 Kx=RSA Au=RSA Enc=AES-CBC(128) Mac=SHA256<br />
RSA-AES256-SHA256 Kx=RSA Au=RSA Enc=AES-CBC(256) Mac=SHA256<br />
The fields above are :<br />
{OpenSSL ciphername}<br />
Kx={key exchange}<br />
Au={authentication}<br />
Enc={symmetric encryption method}<br />
Mac={message authentication code}<br />
{export flag}
Security Notes found on port/service "25 / tcp / smtp"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"SSL Cipher Block Chaining Cipher Suites Supported"<br />
Category<br />
"General "<br />
Priority "Low Priority<br />
Synopsis The remote service supports the use of SSL Cipher Block Chaining ciphers, which combine previous blocks with<br />
Description subsequent ones.<br />
The remote host supports the use of SSL ciphers that operate in Cipher Block Chaining (CBC) mode. These cipher<br />
suites offer additional security over Electronic Codebook (ECB) mode, but have the potential to leak information if<br />
used improperly.<br />
See also:<br />
http://<strong>www</strong>.openssl.org/docs/apps/ciphers.html<br />
http://<strong>www</strong>.nessus.org/u?cc4a822a<br />
http://<strong>www</strong>.openssl.org/~bodo/tls-cbc.txt<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output Here is the list of SSL CBC ciphers supported by the remote server :<br />
Low Strength Ciphers (
EXP-RC2-CBC-MD5 Kx=RSA(512) Au=RSA Enc=RC2-CBC(40) Mac=MD5 export<br />
DES-CBC-SHA Kx=RSA Au=RSA Enc=DES-CBC(56) Mac=SHA1<br />
High Strength Ciphers (>= 112-bit key)<br />
SSLv2<br />
DES-CBC3-MD5 Kx=RSA Au=RSA Enc=3DES-CBC(168) Mac=MD5<br />
IDEA-CBC-MD5 Kx=RSA Au=RSA Enc=IDEA-CBC(128) Mac=MD5<br />
RC2-CBC-MD5 Kx=RSA Au=RSA Enc=RC2-CBC(128) Mac=MD5<br />
TLSv1<br />
EDH-RSA-DES-CBC3-SHA Kx=DH Au=RSA Enc=3DES-CBC(168) Mac=SHA1<br />
DHE-RSA-AES128-SHA Kx=DH Au=RSA Enc=AES-CBC(128) Mac=SHA1<br />
DHE-RSA-AES256-SHA Kx=DH Au=RSA Enc=AES-CBC(256) Mac=SHA1<br />
DHE-RSA-CAMELLIA128-SHA Kx=DH Au=RSA Enc=Camellia-CBC(128) Mac=SHA1<br />
DHE-RSA-CAMELLIA256-SHA Kx=DH Au=RSA Enc=Camellia-CBC(256) Mac=SHA1<br />
DHE-RSA-SEED-SHA Kx=DH Au=RSA Enc=SEED-CBC(128) Mac=SHA1<br />
ADH-DES-CBC3-SHA Kx=DH Au=None Enc=3DES-CBC(168) Mac=SHA1<br />
ADH-AES128-SHA Kx=DH Au=None Enc=AES-CBC(128) Mac=SHA1<br />
ADH-AES256-SHA Kx=DH Au=None Enc=AES-CBC(256) Mac=SHA1<br />
ADH-CAMELLIA128-SHA Kx=DH Au=None Enc=Camellia-CBC(128) Mac=SHA1<br />
ADH-CAMELLIA256-SHA Kx=DH Au=None Enc=Camellia-CBC(256) Mac=SHA1<br />
ADH-SEED-SHA Kx=DH Au=None Enc=SEED-CBC(128) Mac=SHA1<br />
ECDHE-RSA-DES-CBC3-SHA Kx=ECDH Au=RSA Enc=3DES-CBC(168) Mac=SHA1<br />
ECDHE-RSA-AES128-SHA Kx=ECDH Au=RSA Enc=AES-CBC(128) Mac=SHA1<br />
ECDHE-RSA-AES256-SHA Kx=ECDH Au=RSA Enc=AES-CBC(256) Mac=SHA1<br />
AECDH-DES-CBC3-SHA Kx=ECDH Au=None Enc=3DES-CBC(168) Mac=SHA1<br />
AECDH-AES128-SHA Kx=ECDH Au=None Enc=AES-CBC(128) Mac=SHA1<br />
AECDH-AES256-SHA Kx=ECDH Au=None Enc=AES-CBC(256) Mac=SHA1<br />
DES-CBC3-SHA Kx=RSA Au=RSA Enc=3DES-CBC(168) Mac=SHA1<br />
AES128-SHA Kx=RSA Au=RSA Enc=AES-CBC(128) Mac=SHA1<br />
AES256-SHA Kx=RSA Au=RSA Enc=AES-CBC(256) Mac=SHA1<br />
CAMELLIA128-SHA Kx=RSA Au=RSA Enc=Camellia-CBC(128) Mac=SHA1<br />
CAMELLIA256-SHA Kx=RSA Au=RSA Enc=Camellia-CBC(256) Mac=SHA1
IDEA-CBC-SHA Kx=RSA Au=RSA Enc=IDEA-CBC(128) Mac=SHA1<br />
SEED-SHA Kx=RSA Au=RSA Enc=SEED-CBC(128) Mac=SHA1<br />
DHE-RSA-AES128-SHA256 Kx=DH Au=RSA Enc=AES-CBC(128) Mac=SHA256<br />
DHE-RSA-AES256-SHA256 Kx=DH Au=RSA Enc=AES-CBC(256) Mac=SHA256<br />
DH-AES128-SHA256 Kx=DH Au=None Enc=AES-CBC(128) Mac=SHA256<br />
DH-AES256-SHA256 Kx=DH Au=None Enc=AES-CBC(256) Mac=SHA256<br />
ECDHE-RSA-AES128-SHA256 Kx=ECDHE Au=RSA Enc=AES-CBC(128) Mac=SHA256<br />
ECDHE-RSA-AES256-SHA384 Kx=ECDHE Au=RSA Enc=AES-CBC(256) Mac=SHA384<br />
RSA-AES128-SHA256 Kx=RSA Au=RSA Enc=AES-CBC(128) Mac=SHA256<br />
RSA-AES256-SHA256 Kx=RSA Au=RSA Enc=AES-CBC(256) Mac=SHA256<br />
The fields above are :<br />
{OpenSSL ciphername}<br />
Kx={key exchange}<br />
Au={authentication}<br />
Enc={symmetric encryption method}<br />
Mac={message authentication code}<br />
{export flag}
Security Notes found on port/service "443 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"SSL Cipher Suites Supported"<br />
Category<br />
Priority<br />
"General "<br />
"Low Priority<br />
Synopsis The remote service encrypts communications using SSL.<br />
Description This plugin detects which SSL ciphers are supported by the remote service for encrypting communications.<br />
See also:<br />
https://<strong>www</strong>.openssl.org/docs/manmaster/apps/ciphers.html<br />
http://<strong>www</strong>.nessus.org/u?7d537016<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output Here is the list of SSL ciphers supported by the remote server :<br />
Each group is reported per SSL Version.<br />
SSL Version : TLSv12<br />
High Strength Ciphers (>= 112-bit key)<br />
ECDHE-RSA-DES-CBC3-SHA Kx=ECDH Au=RSA Enc=3DES-CBC(168) Mac=SHA1<br />
ECDHE-RSA-AES128-SHA Kx=ECDH Au=RSA Enc=AES-CBC(128) Mac=SHA1<br />
ECDHE-RSA-AES256-SHA Kx=ECDH Au=RSA Enc=AES-CBC(256) Mac=SHA1<br />
DES-CBC3-SHA Kx=RSA Au=RSA Enc=3DES-CBC(168) Mac=SHA1<br />
AES128-SHA Kx=RSA Au=RSA Enc=AES-CBC(128) Mac=SHA1<br />
AES256-SHA Kx=RSA Au=RSA Enc=AES-CBC(256) Mac=SHA1<br />
CAMELLIA128-SHA Kx=RSA Au=RSA Enc=Camellia-CBC(128) Mac=SHA1<br />
CAMELLIA256-SHA Kx=RSA Au=RSA Enc=Camellia-CBC(256) Mac=SHA1<br />
ECDHE-RSA-AES128-SHA256 Kx=ECDHE Au=RSA Enc=AES-CBC(128) Mac=SHA256<br />
ECDHE-RSA-AES256-SHA384 Kx=ECDHE Au=RSA Enc=AES-CBC(256) Mac=SHA384<br />
RSA-AES128-SHA256 Kx=RSA Au=RSA Enc=AES-CBC(128) Mac=SHA256<br />
RSA-AES256-SHA256 Kx=RSA Au=RSA Enc=AES-CBC(256) Mac=SHA256<br />
ECDHE-RSA-AES128-SHA256 Kx=ECDHE Au=RSA Enc=AES-GCM(128) Mac=SHA256
ECDHE-RSA-AES256-SHA384 Kx=ECDHE Au=RSA Enc=AES-GCM(256) Mac=SHA384<br />
RSA-AES128-SHA256 Kx=RSA Au=RSA Enc=AES-GCM(128) Mac=SHA256<br />
RSA-AES256-SHA384 Kx=RSA Au=RSA Enc=AES-GCM(256) Mac=SHA384<br />
SSL Version : TLSv11<br />
High Strength Ciphers (>= 112-bit key)<br />
ECDHE-RSA-DES-CBC3-SHA Kx=ECDH Au=RSA Enc=3DES-CBC(168) Mac=SHA1<br />
ECDHE-RSA-AES128-SHA Kx=ECDH Au=RSA Enc=AES-CBC(128) Mac=SHA1<br />
ECDHE-RSA-AES256-SHA Kx=ECDH Au=RSA Enc=AES-CBC(256) Mac=SHA1<br />
DES-CBC3-SHA Kx=RSA Au=RSA Enc=3DES-CBC(168) Mac=SHA1<br />
AES128-SHA Kx=RSA Au=RSA Enc=AES-CBC(128) Mac=SHA1<br />
AES256-SHA Kx=RSA Au=RSA Enc=AES-CBC(256) Mac=SHA1<br />
CAMELLIA128-SHA Kx=RSA Au=RSA Enc=Camellia-CBC(128) Mac=SHA1<br />
CAMELLIA256-SHA Kx=RSA Au=RSA Enc=Camellia-CBC(256) Mac=SHA1<br />
SSL Version : TLSv1<br />
High Strength Ciphers (>= 112-bit key)<br />
ECDHE-RSA-DES-CBC3-SHA Kx=ECDH Au=RSA Enc=3DES-CBC(168) Mac=SHA1<br />
ECDHE-RSA-AES128-SHA Kx=ECDH Au=RSA Enc=AES-CBC(128) Mac=SHA1<br />
ECDHE-RSA-AES256-SHA Kx=ECDH Au=RSA Enc=AES-CBC(256) Mac=SHA1<br />
DES-CBC3-SHA Kx=RSA Au=RSA Enc=3DES-CBC(168) Mac=SHA1<br />
AES128-SHA Kx=RSA Au=RSA Enc=AES-CBC(128) Mac=SHA1<br />
AES256-SHA Kx=RSA Au=RSA Enc=AES-CBC(256) Mac=SHA1<br />
CAMELLIA128-SHA Kx=RSA Au=RSA Enc=Camellia-CBC(128) Mac=SHA1<br />
CAMELLIA256-SHA Kx=RSA Au=RSA Enc=Camellia-CBC(256) Mac=SHA1<br />
SSL Version : SSLv3<br />
High Strength Ciphers (>= 112-bit key)<br />
ECDHE-RSA-DES-CBC3-SHA Kx=ECDH Au=RSA Enc=3DES-CBC(168) Mac=SHA1<br />
ECDHE-RSA-AES128-SHA Kx=ECDH Au=RSA Enc=AES-CBC(128) Mac=SHA1<br />
ECDHE-RSA-AES256-SHA Kx=ECDH Au=RSA Enc=AES-CBC(256) Mac=SHA1
DES-CBC3-SHA Kx=RSA Au=RSA Enc=3DES-CBC(168) Mac=SHA1<br />
AES128-SHA Kx=RSA Au=RSA Enc=AES-CBC(128) Mac=SHA1<br />
AES256-SHA Kx=RSA Au=RSA Enc=AES-CBC(256) Mac=SHA1<br />
CAMELLIA128-SHA Kx=RSA Au=RSA Enc=Camellia-CBC(128) Mac=SHA1<br />
CAMELLIA256-SHA Kx=RSA Au=RSA Enc=Camellia-CBC(256) Mac=SHA1<br />
The fields above are :<br />
{OpenSSL ciphername}<br />
Kx={key exchange}<br />
Au={authentication}<br />
Enc={symmetric encryption method}<br />
Mac={message authentication code}<br />
{export flag}
Security Notes found on port/service "110 / tcp / pop3"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"SSL Cipher Suites Supported"<br />
Category<br />
Priority<br />
"General "<br />
"Low Priority<br />
Synopsis The remote service encrypts communications using SSL.<br />
Description This plugin detects which SSL ciphers are supported by the remote service for encrypting communications.<br />
See also:<br />
https://<strong>www</strong>.openssl.org/docs/manmaster/apps/ciphers.html<br />
http://<strong>www</strong>.nessus.org/u?7d537016<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output Here is the list of SSL ciphers supported by the remote server :<br />
Each group is reported per SSL Version.<br />
SSL Version : TLSv12<br />
High Strength Ciphers (>= 112-bit key)<br />
EDH-RSA-DES-CBC3-SHA Kx=DH Au=RSA Enc=3DES-CBC(168) Mac=SHA1<br />
DHE-RSA-AES128-SHA Kx=DH Au=RSA Enc=AES-CBC(128) Mac=SHA1<br />
DHE-RSA-AES256-SHA Kx=DH Au=RSA Enc=AES-CBC(256) Mac=SHA1<br />
DHE-RSA-CAMELLIA128-SHA Kx=DH Au=RSA Enc=Camellia-CBC(128) Mac=SHA1<br />
DHE-RSA-CAMELLIA256-SHA Kx=DH Au=RSA Enc=Camellia-CBC(256) Mac=SHA1<br />
DES-CBC3-SHA Kx=RSA Au=RSA Enc=3DES-CBC(168) Mac=SHA1<br />
AES128-SHA Kx=RSA Au=RSA Enc=AES-CBC(128) Mac=SHA1<br />
AES256-SHA Kx=RSA Au=RSA Enc=AES-CBC(256) Mac=SHA1<br />
CAMELLIA128-SHA Kx=RSA Au=RSA Enc=Camellia-CBC(128) Mac=SHA1<br />
CAMELLIA256-SHA Kx=RSA Au=RSA Enc=Camellia-CBC(256) Mac=SHA1<br />
DHE-RSA-AES128-SHA256 Kx=DH Au=RSA Enc=AES-CBC(128) Mac=SHA256<br />
DHE-RSA-AES256-SHA256 Kx=DH Au=RSA Enc=AES-CBC(256) Mac=SHA256<br />
RSA-AES128-SHA256 Kx=RSA Au=RSA Enc=AES-CBC(128) Mac=SHA256
RSA-AES256-SHA256 Kx=RSA Au=RSA Enc=AES-CBC(256) Mac=SHA256<br />
DHE-RSA-AES128-SHA256 Kx=DH Au=RSA Enc=AES-GCM(128) Mac=SHA256<br />
DHE-RSA-AES256-SHA384 Kx=DH Au=RSA Enc=AES-GCM(256) Mac=SHA384<br />
RSA-AES128-SHA256 Kx=RSA Au=RSA Enc=AES-GCM(128) Mac=SHA256<br />
RSA-AES256-SHA384 Kx=RSA Au=RSA Enc=AES-GCM(256) Mac=SHA384<br />
SSL Version : TLSv11<br />
High Strength Ciphers (>= 112-bit key)<br />
EDH-RSA-DES-CBC3-SHA Kx=DH Au=RSA Enc=3DES-CBC(168) Mac=SHA1<br />
DHE-RSA-AES128-SHA Kx=DH Au=RSA Enc=AES-CBC(128) Mac=SHA1<br />
DHE-RSA-AES256-SHA Kx=DH Au=RSA Enc=AES-CBC(256) Mac=SHA1<br />
DHE-RSA-CAMELLIA128-SHA Kx=DH Au=RSA Enc=Camellia-CBC(128) Mac=SHA1<br />
DHE-RSA-CAMELLIA256-SHA Kx=DH Au=RSA Enc=Camellia-CBC(256) Mac=SHA1<br />
DES-CBC3-SHA Kx=RSA Au=RSA Enc=3DES-CBC(168) Mac=SHA1<br />
AES128-SHA Kx=RSA Au=RSA Enc=AES-CBC(128) Mac=SHA1<br />
AES256-SHA Kx=RSA Au=RSA Enc=AES-CBC(256) Mac=SHA1<br />
CAMELLIA128-SHA Kx=RSA Au=RSA Enc=Camellia-CBC(128) Mac=SHA1<br />
CAMELLIA256-SHA Kx=RSA Au=RSA Enc=Camellia-CBC(256) Mac=SHA1<br />
SSL Version : TLSv1<br />
High Strength Ciphers (>= 112-bit key)<br />
EDH-RSA-DES-CBC3-SHA Kx=DH Au=RSA Enc=3DES-CBC(168) Mac=SHA1<br />
DHE-RSA-AES128-SHA Kx=DH Au=RSA Enc=AES-CBC(128) Mac=SHA1<br />
DHE-RSA-AES256-SHA Kx=DH Au=RSA Enc=AES-CBC(256) Mac=SHA1<br />
DHE-RSA-CAMELLIA128-SHA Kx=DH Au=RSA Enc=Camellia-CBC(128) Mac=SHA1<br />
DHE-RSA-CAMELLIA256-SHA Kx=DH Au=RSA Enc=Camellia-CBC(256) Mac=SHA1<br />
DES-CBC3-SHA Kx=RSA Au=RSA Enc=3DES-CBC(168) Mac=SHA1<br />
AES128-SHA Kx=RSA Au=RSA Enc=AES-CBC(128) Mac=SHA1<br />
AES256-SHA Kx=RSA Au=RSA Enc=AES-CBC(256) Mac=SHA1<br />
CAMELLIA128-SHA Kx=RSA Au=RSA Enc=Camellia-CBC(128) Mac=SHA1<br />
CAMELLIA256-SHA Kx=RSA Au=RSA Enc=Camellia-CBC(256) Mac=SHA1
The fields above are :<br />
{OpenSSL ciphername}<br />
Kx={key exchange}<br />
Au={authentication}<br />
Enc={symmetric encryption method}<br />
Mac={message authentication code}<br />
{export flag}
Security Notes found on port/service "25 / tcp / smtp"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"SSL Cipher Suites Supported"<br />
Category<br />
Priority<br />
"General "<br />
"Low Priority<br />
Synopsis The remote service encrypts communications using SSL.<br />
Description This plugin detects which SSL ciphers are supported by the remote service for encrypting communications.<br />
See also:<br />
https://<strong>www</strong>.openssl.org/docs/manmaster/apps/ciphers.html<br />
http://<strong>www</strong>.nessus.org/u?7d537016<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output Here is the list of SSL ciphers supported by the remote server :<br />
Each group is reported per SSL Version.<br />
SSL Version : TLSv12<br />
Low Strength Ciphers (= 112-bit key)<br />
EDH-RSA-DES-CBC3-SHA Kx=DH Au=RSA Enc=3DES-CBC(168) Mac=SHA1<br />
DHE-RSA-AES128-SHA Kx=DH Au=RSA Enc=AES-CBC(128) Mac=SHA1
DHE-RSA-AES256-SHA Kx=DH Au=RSA Enc=AES-CBC(256) Mac=SHA1<br />
DHE-RSA-CAMELLIA128-SHA Kx=DH Au=RSA Enc=Camellia-CBC(128) Mac=SHA1<br />
DHE-RSA-CAMELLIA256-SHA Kx=DH Au=RSA Enc=Camellia-CBC(256) Mac=SHA1<br />
DHE-RSA-SEED-SHA Kx=DH Au=RSA Enc=SEED-CBC(128) Mac=SHA1<br />
ADH-DES-CBC3-SHA Kx=DH Au=None Enc=3DES-CBC(168) Mac=SHA1<br />
ADH-AES128-SHA Kx=DH Au=None Enc=AES-CBC(128) Mac=SHA1<br />
ADH-AES256-SHA Kx=DH Au=None Enc=AES-CBC(256) Mac=SHA1<br />
ADH-CAMELLIA128-SHA Kx=DH Au=None Enc=Camellia-CBC(128) Mac=SHA1<br />
ADH-CAMELLIA256-SHA Kx=DH Au=None Enc=Camellia-CBC(256) Mac=SHA1<br />
ADH-RC4-MD5 Kx=DH Au=None Enc=RC4(128) Mac=MD5<br />
ADH-SEED-SHA Kx=DH Au=None Enc=SEED-CBC(128) Mac=SHA1<br />
ECDHE-RSA-DES-CBC3-SHA Kx=ECDH Au=RSA Enc=3DES-CBC(168) Mac=SHA1<br />
ECDHE-RSA-AES128-SHA Kx=ECDH Au=RSA Enc=AES-CBC(128) Mac=SHA1<br />
ECDHE-RSA-AES256-SHA Kx=ECDH Au=RSA Enc=AES-CBC(256) Mac=SHA1<br />
ECDHE-RSA-RC4-SHA Kx=ECDH Au=RSA Enc=RC4(128) Mac=SHA1<br />
AECDH-DES-CBC3-SHA Kx=ECDH Au=None Enc=3DES-CBC(168) Mac=SHA1<br />
AECDH-AES128-SHA Kx=ECDH Au=None Enc=AES-CBC(128) Mac=SHA1<br />
AECDH-AES256-SHA Kx=ECDH Au=None Enc=AES-CBC(256) Mac=SHA1<br />
AECDH-RC4-SHA Kx=ECDH Au=None Enc=RC4(128) Mac=SHA1<br />
DES-CBC3-SHA Kx=RSA Au=RSA Enc=3DES-CBC(168) Mac=SHA1<br />
AES128-SHA Kx=RSA Au=RSA Enc=AES-CBC(128) Mac=SHA1<br />
AES256-SHA Kx=RSA Au=RSA Enc=AES-CBC(256) Mac=SHA1<br />
CAMELLIA128-SHA Kx=RSA Au=RSA Enc=Camellia-CBC(128) Mac=SHA1<br />
CAMELLIA256-SHA Kx=RSA Au=RSA Enc=Camellia-CBC(256) Mac=SHA1<br />
IDEA-CBC-SHA Kx=RSA Au=RSA Enc=IDEA-CBC(128) Mac=SHA1<br />
RC4-MD5 Kx=RSA Au=RSA Enc=RC4(128) Mac=MD5<br />
RC4-SHA Kx=RSA Au=RSA Enc=RC4(128) Mac=SHA1<br />
SEED-SHA Kx=RSA Au=RSA Enc=SEED-CBC(128) Mac=SHA1<br />
DHE-RSA-AES128-SHA256 Kx=DH Au=RSA Enc=AES-CBC(128) Mac=SHA256<br />
DHE-RSA-AES256-SHA256 Kx=DH Au=RSA Enc=AES-CBC(256) Mac=SHA256<br />
DH-AES128-SHA256 Kx=DH Au=None Enc=AES-CBC(128) Mac=SHA256<br />
DH-AES256-SHA256 Kx=DH Au=None Enc=AES-CBC(256) Mac=SHA256<br />
ECDHE-RSA-AES128-SHA256 Kx=ECDHE Au=RSA Enc=AES-CBC(128) Mac=SHA256<br />
ECDHE-RSA-AES256-SHA384 Kx=ECDHE Au=RSA Enc=AES-CBC(256) Mac=SHA384
RSA-AES128-SHA256 Kx=RSA Au=RSA Enc=AES-CBC(128) Mac=SHA256<br />
RSA-AES256-SHA256 Kx=RSA Au=RSA Enc=AES-CBC(256) Mac=SHA256<br />
DHE-RSA-AES128-SHA256 Kx=DH Au=RSA Enc=AES-GCM(128) Mac=SHA256<br />
DHE-RSA-AES256-SHA384 Kx=DH Au=RSA Enc=AES-GCM(256) Mac=SHA384<br />
DH-AES128-SHA256 Kx=DH Au=None Enc=AES-GCM(128) Mac=SHA256<br />
DH-AES256-SHA384 Kx=DH Au=None Enc=AES-GCM(256) Mac=SHA384<br />
ECDHE-RSA-AES128-SHA256 Kx=ECDHE Au=RSA Enc=AES-GCM(128) Mac=SHA256<br />
ECDHE-RSA-AES256-SHA384 Kx=ECDHE Au=RSA Enc=AES-GCM(256) Mac=SHA384<br />
RSA-AES128-SHA256 Kx=RSA Au=RSA Enc=AES-GCM(128) Mac=SHA256<br />
RSA-AES256-SHA384 Kx=RSA Au=RSA Enc=AES-GCM(256) Mac=SHA384<br />
SSL Version : TLSv11<br />
Low Strength Ciphers (= 112-bit key)<br />
EDH-RSA-DES-CBC3-SHA Kx=DH Au=RSA Enc=3DES-CBC(168) Mac=SHA1<br />
DHE-RSA-AES128-SHA Kx=DH Au=RSA Enc=AES-CBC(128) Mac=SHA1<br />
DHE-RSA-AES256-SHA Kx=DH Au=RSA Enc=AES-CBC(256) Mac=SHA1<br />
DHE-RSA-CAMELLIA128-SHA Kx=DH Au=RSA Enc=Camellia-CBC(128) Mac=SHA1<br />
DHE-RSA-CAMELLIA256-SHA Kx=DH Au=RSA Enc=Camellia-CBC(256) Mac=SHA1<br />
DHE-RSA-SEED-SHA Kx=DH Au=RSA Enc=SEED-CBC(128) Mac=SHA1<br />
ADH-DES-CBC3-SHA Kx=DH Au=None Enc=3DES-CBC(168) Mac=SHA1<br />
ADH-AES128-SHA Kx=DH Au=None Enc=AES-CBC(128) Mac=SHA1<br />
ADH-AES256-SHA Kx=DH Au=None Enc=AES-CBC(256) Mac=SHA1
ADH-CAMELLIA128-SHA Kx=DH Au=None Enc=Camellia-CBC(128) Mac=SHA1<br />
ADH-CAMELLIA256-SHA Kx=DH Au=None Enc=Camellia-CBC(256) Mac=SHA1<br />
ADH-RC4-MD5 Kx=DH Au=None Enc=RC4(128) Mac=MD5<br />
ADH-SEED-SHA Kx=DH Au=None Enc=SEED-CBC(128) Mac=SHA1<br />
ECDHE-RSA-DES-CBC3-SHA Kx=ECDH Au=RSA Enc=3DES-CBC(168) Mac=SHA1<br />
ECDHE-RSA-AES128-SHA Kx=ECDH Au=RSA Enc=AES-CBC(128) Mac=SHA1<br />
ECDHE-RSA-AES256-SHA Kx=ECDH Au=RSA Enc=AES-CBC(256) Mac=SHA1<br />
ECDHE-RSA-RC4-SHA Kx=ECDH Au=RSA Enc=RC4(128) Mac=SHA1<br />
AECDH-DES-CBC3-SHA Kx=ECDH Au=None Enc=3DES-CBC(168) Mac=SHA1<br />
AECDH-AES128-SHA Kx=ECDH Au=None Enc=AES-CBC(128) Mac=SHA1<br />
AECDH-AES256-SHA Kx=ECDH Au=None Enc=AES-CBC(256) Mac=SHA1<br />
AECDH-RC4-SHA Kx=ECDH Au=None Enc=RC4(128) Mac=SHA1<br />
DES-CBC3-SHA Kx=RSA Au=RSA Enc=3DES-CBC(168) Mac=SHA1<br />
AES128-SHA Kx=RSA Au=RSA Enc=AES-CBC(128) Mac=SHA1<br />
AES256-SHA Kx=RSA Au=RSA Enc=AES-CBC(256) Mac=SHA1<br />
CAMELLIA128-SHA Kx=RSA Au=RSA Enc=Camellia-CBC(128) Mac=SHA1<br />
CAMELLIA256-SHA Kx=RSA Au=RSA Enc=Camellia-CBC(256) Mac=SHA1<br />
IDEA-CBC-SHA Kx=RSA Au=RSA Enc=IDEA-CBC(128) Mac=SHA1<br />
RC4-MD5 Kx=RSA Au=RSA Enc=RC4(128) Mac=MD5<br />
RC4-SHA Kx=RSA Au=RSA Enc=RC4(128) Mac=SHA1<br />
SEED-SHA Kx=RSA Au=RSA Enc=SEED-CBC(128) Mac=SHA1<br />
SSL Version : TLSv1<br />
Low Strength Ciphers (
High Strength Ciphers (>= 112-bit key)<br />
EDH-RSA-DES-CBC3-SHA Kx=DH Au=RSA Enc=3DES-CBC(168) Mac=SHA1<br />
DHE-RSA-AES128-SHA Kx=DH Au=RSA Enc=AES-CBC(128) Mac=SHA1<br />
DHE-RSA-AES256-SHA Kx=DH Au=RSA Enc=AES-CBC(256) Mac=SHA1<br />
DHE-RSA-CAMELLIA128-SHA Kx=DH Au=RSA Enc=Camellia-CBC(128) Mac=SHA1<br />
DHE-RSA-CAMELLIA256-SHA Kx=DH Au=RSA Enc=Camellia-CBC(256) Mac=SHA1<br />
DHE-RSA-SEED-SHA Kx=DH Au=RSA Enc=SEED-CBC(128) Mac=SHA1<br />
ADH-DES-CBC3-SHA Kx=DH Au=None Enc=3DES-CBC(168) Mac=SHA1<br />
ADH-AES128-SHA Kx=DH Au=None Enc=AES-CBC(128) Mac=SHA1<br />
ADH-AES256-SHA Kx=DH Au=None Enc=AES-CBC(256) Mac=SHA1<br />
ADH-CAMELLIA128-SHA Kx=DH Au=None Enc=Camellia-CBC(128) Mac=SHA1<br />
ADH-CAMELLIA256-SHA Kx=DH Au=None Enc=Camellia-CBC(256) Mac=SHA1<br />
ADH-RC4-MD5 Kx=DH Au=None Enc=RC4(128) Mac=MD5<br />
ADH-SEED-SHA Kx=DH Au=None Enc=SEED-CBC(128) Mac=SHA1<br />
ECDHE-RSA-DES-CBC3-SHA Kx=ECDH Au=RSA Enc=3DES-CBC(168) Mac=SHA1<br />
ECDHE-RSA-AES128-SHA Kx=ECDH Au=RSA Enc=AES-CBC(128) Mac=SHA1<br />
ECDHE-RSA-AES256-SHA Kx=ECDH Au=RSA Enc=AES-CBC(256) Mac=SHA1<br />
ECDHE-RSA-RC4-SHA Kx=ECDH Au=RSA Enc=RC4(128) Mac=SHA1<br />
AECDH-DES-CBC3-SHA Kx=ECDH Au=None Enc=3DES-CBC(168) Mac=SHA1<br />
AECDH-AES128-SHA Kx=ECDH Au=None Enc=AES-CBC(128) Mac=SHA1<br />
AECDH-AES256-SHA Kx=ECDH Au=None Enc=AES-CBC(256) Mac=SHA1<br />
AECDH-RC4-SHA Kx=ECDH Au=None Enc=RC4(128) Mac=SHA1<br />
DES-CBC3-SHA Kx=RSA Au=RSA Enc=3DES-CBC(168) Mac=SHA1<br />
AES128-SHA Kx=RSA Au=RSA Enc=AES-CBC(128) Mac=SHA1<br />
AES256-SHA Kx=RSA Au=RSA Enc=AES-CBC(256) Mac=SHA1<br />
CAMELLIA128-SHA Kx=RSA Au=RSA Enc=Camellia-CBC(128) Mac=SHA1<br />
CAMELLIA256-SHA Kx=RSA Au=RSA Enc=Camellia-CBC(256) Mac=SHA1<br />
IDEA-CBC-SHA Kx=RSA Au=RSA Enc=IDEA-CBC(128) Mac=SHA1<br />
RC4-MD5 Kx=RSA Au=RSA Enc=RC4(128) Mac=MD5<br />
RC4-SHA Kx=RSA Au=RSA Enc=RC4(128) Mac=SHA1<br />
SEED-SHA Kx=RSA Au=RSA Enc=SEED-CBC(128) Mac=SHA1
SSL Version : SSLv3<br />
Low Strength Ciphers (= 112-bit key)<br />
EDH-RSA-DES-CBC3-SHA Kx=DH Au=RSA Enc=3DES-CBC(168) Mac=SHA1<br />
DHE-RSA-AES128-SHA Kx=DH Au=RSA Enc=AES-CBC(128) Mac=SHA1<br />
DHE-RSA-AES256-SHA Kx=DH Au=RSA Enc=AES-CBC(256) Mac=SHA1<br />
DHE-RSA-CAMELLIA128-SHA Kx=DH Au=RSA Enc=Camellia-CBC(128) Mac=SHA1<br />
DHE-RSA-CAMELLIA256-SHA Kx=DH Au=RSA Enc=Camellia-CBC(256) Mac=SHA1<br />
DHE-RSA-SEED-SHA Kx=DH Au=RSA Enc=SEED-CBC(128) Mac=SHA1<br />
ADH-DES-CBC3-SHA Kx=DH Au=None Enc=3DES-CBC(168) Mac=SHA1<br />
ADH-AES128-SHA Kx=DH Au=None Enc=AES-CBC(128) Mac=SHA1<br />
ADH-AES256-SHA Kx=DH Au=None Enc=AES-CBC(256) Mac=SHA1<br />
ADH-CAMELLIA128-SHA Kx=DH Au=None Enc=Camellia-CBC(128) Mac=SHA1<br />
ADH-CAMELLIA256-SHA Kx=DH Au=None Enc=Camellia-CBC(256) Mac=SHA1<br />
ADH-RC4-MD5 Kx=DH Au=None Enc=RC4(128) Mac=MD5<br />
ADH-SEED-SHA Kx=DH Au=None Enc=SEED-CBC(128) Mac=SHA1<br />
ECDHE-RSA-DES-CBC3-SHA Kx=ECDH Au=RSA Enc=3DES-CBC(168) Mac=SHA1<br />
ECDHE-RSA-AES128-SHA Kx=ECDH Au=RSA Enc=AES-CBC(128) Mac=SHA1<br />
ECDHE-RSA-AES256-SHA Kx=ECDH Au=RSA Enc=AES-CBC(256) Mac=SHA1<br />
ECDHE-RSA-RC4-SHA Kx=ECDH Au=RSA Enc=RC4(128) Mac=SHA1<br />
AECDH-DES-CBC3-SHA Kx=ECDH Au=None Enc=3DES-CBC(168) Mac=SHA1<br />
AECDH-AES128-SHA Kx=ECDH Au=None Enc=AES-CBC(128) Mac=SHA1<br />
AECDH-AES256-SHA Kx=ECDH Au=None Enc=AES-CBC(256) Mac=SHA1<br />
AECDH-RC4-SHA Kx=ECDH Au=None Enc=RC4(128) Mac=SHA1
DES-CBC3-SHA Kx=RSA Au=RSA Enc=3DES-CBC(168) Mac=SHA1<br />
AES128-SHA Kx=RSA Au=RSA Enc=AES-CBC(128) Mac=SHA1<br />
AES256-SHA Kx=RSA Au=RSA Enc=AES-CBC(256) Mac=SHA1<br />
CAMELLIA128-SHA Kx=RSA Au=RSA Enc=Camellia-CBC(128) Mac=SHA1<br />
CAMELLIA256-SHA Kx=RSA Au=RSA Enc=Camellia-CBC(256) Mac=SHA1<br />
IDEA-CBC-SHA Kx=RSA Au=RSA Enc=IDEA-CBC(128) Mac=SHA1<br />
RC4-MD5 Kx=RSA Au=RSA Enc=RC4(128) Mac=MD5<br />
RC4-SHA Kx=RSA Au=RSA Enc=RC4(128) Mac=SHA1<br />
SEED-SHA Kx=RSA Au=RSA Enc=SEED-CBC(128) Mac=SHA1<br />
SSL Version : SSLv2<br />
Low Strength Ciphers (= 112-bit key)<br />
DES-CBC3-MD5 Kx=RSA Au=RSA Enc=3DES-CBC(168) Mac=MD5<br />
IDEA-CBC-MD5 Kx=RSA Au=RSA Enc=IDEA-CBC(128) Mac=MD5<br />
RC2-CBC-MD5 Kx=RSA Au=RSA Enc=RC2-CBC(128) Mac=MD5<br />
RC4-MD5 Kx=RSA Au=RSA Enc=RC4(128) Mac=MD5<br />
The fields above are :<br />
{OpenSSL ciphername}<br />
Kx={key exchange}<br />
Au={authentication}<br />
Enc={symmetric encryption method}<br />
Mac={message authentication code}<br />
{export flag}
Security Notes found on port/service "8880 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"HTTP X-Frame-Options Response Header Usage"<br />
Category<br />
"CGI abuses "<br />
Priority "Low Priority<br />
Synopsis The remote web server does not take steps to mitigate a class of web application vulnerabilities.<br />
Description The remote web server in some responses sets a permissive X-Frame-Options response header or does not set one<br />
at all.<br />
The X-Frame-Options header has been proposed by Microsoft as a way to mitigate clickjacking attacks and is currently<br />
supported by all major browser vendors<br />
See also:<br />
http://en.wikipedia.org/wiki/Clickjacking<br />
http://<strong>www</strong>.nessus.org/u?399b1f56<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
The following pages do not set a X-Frame-Options response header or set a permissive policy:<br />
- http://<strong>www</strong>.takti.co.il:8880/sitebuilder/<br />
Solution Set a properly configured X-Frame-Options header for all requested resources.
Security Notes found on port/service "8880 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"HTTP X-Content-Security-Policy Response Header Usage"<br />
Category<br />
"CGI abuses "<br />
Priority "Low Priority<br />
Synopsis The remote web server does not take steps to mitigate a class of web application vulnerabilities.<br />
Description The remote web server in some responses sets a permissive Content-Security-Policy (CSP) response header or does<br />
not set one at all.<br />
The CSP header has been proposed by the W3C Web Application Security Working Group as a way to mitigate crosssite<br />
scripting and clickjacking attacks.<br />
See also:<br />
http://content-security-policy.com/<br />
https://<strong>www</strong>.w3.org/TR/CSP2/<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
The following pages do not set a Content-Security-Policy response header or set a permissive policy:<br />
- http://<strong>www</strong>.takti.co.il:8880/sitebuilder/<br />
Solution Set a properly configured Content-Security-Policy header for all requested resources.
Security Notes found on port/service "443 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"HTTP X-Content-Security-Policy Response Header Usage"<br />
Category<br />
"CGI abuses "<br />
Priority "Low Priority<br />
Synopsis The remote web server does not take steps to mitigate a class of web application vulnerabilities.<br />
Description The remote web server in some responses sets a permissive Content-Security-Policy (CSP) response header or does<br />
not set one at all.<br />
The CSP header has been proposed by the W3C Web Application Security Working Group as a way to mitigate crosssite<br />
scripting and clickjacking attacks.<br />
See also:<br />
http://content-security-policy.com/<br />
https://<strong>www</strong>.w3.org/TR/CSP2/<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
The following pages do not set a Content-Security-Policy response header or set a permissive policy:<br />
- https://<strong>www</strong>.takti.co.il/<br />
- https://<strong>www</strong>.takti.co.il/BuildaGate5/<br />
- https://<strong>www</strong>.takti.co.il/BuildaGate5/general2/<br />
- https://<strong>www</strong>.takti.co.il/BuildaGate5/general2/company_search_tree.php<br />
- https://<strong>www</strong>.takti.co.il/BuildaGate5/portals/<br />
- https://<strong>www</strong>.takti.co.il/BuildaGate5/portals/takti/<br />
- https://<strong>www</strong>.takti.co.il/cal/<br />
- https://<strong>www</strong>.takti.co.il/demo/<br />
- https://<strong>www</strong>.takti.co.il/demo/1.html<br />
- https://<strong>www</strong>.takti.co.il/demo/2.html<br />
- https://<strong>www</strong>.takti.co.il/demo/3.html<br />
- https://<strong>www</strong>.takti.co.il/demo/4.html
- https://<strong>www</strong>.takti.co.il/demo/index.html<br />
- https://<strong>www</strong>.takti.co.il/images/<br />
- https://<strong>www</strong>.takti.co.il/test/<br />
- https://<strong>www</strong>.takti.co.il/webalizer/<br />
Solution Set a properly configured Content-Security-Policy header for all requested resources.
Security Notes found on port/service "80 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"HTTP X-Content-Security-Policy Response Header Usage"<br />
Category<br />
"CGI abuses "<br />
Priority "Low Priority<br />
Synopsis The remote web server does not take steps to mitigate a class of web application vulnerabilities.<br />
Description The remote web server in some responses sets a permissive Content-Security-Policy (CSP) response header or does<br />
not set one at all.<br />
The CSP header has been proposed by the W3C Web Application Security Working Group as a way to mitigate crosssite<br />
scripting and clickjacking attacks.<br />
See also:<br />
http://content-security-policy.com/<br />
https://<strong>www</strong>.w3.org/TR/CSP2/<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
The following pages do not set a Content-Security-Policy response header or set a permissive policy:<br />
- http://<strong>www</strong>.takti.co.il/<br />
- http://<strong>www</strong>.takti.co.il/BuildaGate5/<br />
- http://<strong>www</strong>.takti.co.il/BuildaGate5/general2/<br />
- http://<strong>www</strong>.takti.co.il/BuildaGate5/general2/company_search_tree.php<br />
- http://<strong>www</strong>.takti.co.il/BuildaGate5/portals/<br />
- http://<strong>www</strong>.takti.co.il/BuildaGate5/portals/takti/<br />
- http://<strong>www</strong>.takti.co.il/cal/<br />
- http://<strong>www</strong>.takti.co.il/demo/<br />
- http://<strong>www</strong>.takti.co.il/demo/1.html<br />
- http://<strong>www</strong>.takti.co.il/demo/2.html<br />
- http://<strong>www</strong>.takti.co.il/demo/3.html<br />
- http://<strong>www</strong>.takti.co.il/demo/4.html
- http://<strong>www</strong>.takti.co.il/demo/index.html<br />
- http://<strong>www</strong>.takti.co.il/images/<br />
- http://<strong>www</strong>.takti.co.il/test/<br />
- http://<strong>www</strong>.takti.co.il/webalizer/<br />
Solution Set a properly configured Content-Security-Policy header for all requested resources.
Security Notes found on port/service "443 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"TLS NPN Supported Protocol Enumeration"<br />
Category<br />
"Misc. "<br />
Priority "Low Priority<br />
Synopsis The remote host supports the TLS NPN extension.<br />
Description The remote host supports the TLS NPN (Transport Layer Security Next Protocol Negotiation) extension. This plugin<br />
enumerates the protocols the extension supports.<br />
See also:<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
NPN Supported Protocols:<br />
http/1.1<br />
https://tools.ietf.org/id/draft-agl-tls-nextprotoneg-03.html
Security Notes found on port/service "110 / tcp / pop3"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"POP3 Service STLS Command Support"<br />
Category<br />
"Misc. "<br />
Priority "Low Priority<br />
Synopsis The remote mail service supports encrypting traffic.<br />
Description The remote POP3 service supports the use of the 'STLS' command to switch from a cleartext to an encrypted<br />
communications channel.<br />
See also:<br />
http://en.wikipedia.org/wiki/STARTTLS<br />
http://tools.ietf.org/html/rfc2595<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
Here is the POP3 server's SSL certificate that Nessus was able to<br />
collect after sending a 'STLS' command :<br />
------------------------------ snip ------------------------------<br />
Subject Name:<br />
Country: US<br />
State/Province: Virginia<br />
Locality: Herndon<br />
Organization: Parallels<br />
Organization Unit: Parallels Panel<br />
Common Name: Parallels Panel<br />
Email Address: info@parallels.com<br />
Issuer Name:<br />
Country: US
State/Province: Virginia<br />
Locality: Herndon<br />
Organization: Parallels<br />
Organization Unit: Parallels Panel<br />
Common Name: Parallels Panel<br />
Email Address: info@parallels.com<br />
Serial Number: 55 2B 60 34<br />
Version: 1<br />
Signature Algorithm: SHA-1 With RSA Encryption<br />
Not Valid Before: Apr 13 06:20:36 2015 GMT<br />
Not Valid After: Apr 12 06:20:36 2016 GMT<br />
Public Key Info:<br />
Algorithm: RSA Encryption<br />
Key Length: 2048 bits<br />
Public Key: 00 A6 AD 66 0F 5D A6 09 2C 92 16 06 ED 1E D4 95 D2 10 34 BA<br />
FE 8C A9 25 25 66 15 01 CE 32 8B C2 CE BD 17 87 B1 DD AB 88<br />
61 EA 30 02 F5 5A EE 98 88 0C 52 C3 E0 A0 2A 9D FC 06 1F FD<br />
BE FD 46 20 C0 A9 48 BB 2A B3 FD B3 E6 90 48 44 45 F1 60 BC<br />
CE FA 8A CF E7 44 11 D0 71 20 53 28 28 E4 0C CF A1 57 41 E8<br />
AA 0F A2 55 6E DE B0 1D DC EB 9A 86 21 55 23 31 7D 11 4E 3A<br />
CC 7F 51 8E 68 8E B2 B7 F0 7A A5 7B C0 C9 CC 6F 9D 99 A0 DD<br />
EB 81 C1 20 93 1B 18 70 BE C9 C1 5E FE D3 38 60 07 81 67 F6<br />
A0 1D 9C 96 5F D3 8C 32 E7 5C 3A 2C FA 5E 92 B9 85 1D 84 F7<br />
49 20 9C D1 98 B8 8E BE E1 D6 72 45 E8 50 20 82 09 4E 8A 0B<br />
C7 2D F6 8D 10 FB 31 37 B7 D0 68 DB 02 37 0B 57 0F 62 1C 57<br />
C1 16 3F 24 6A 1F C0 55 10 92 6C 0B 21 0E 41 67 1A 86 EC 9E<br />
EE CF C8 BF 19 3D 68 89 06 D0 43 56 B6 B6 AF 3F E7<br />
Exponent: 01 00 01
Signature Length: 256 bytes / 2048 bits<br />
Signature: 00 40 63 59 39 62 79 E0 E2 5A 04 8B EB CA 6D 60 A9 2E AB D5<br />
8F DB 56 8A C8 19 B1 62 8E 7A 88 85 F6 C1 E5 18 C1 6B C9 6A<br />
30 76 B1 DA 92 38 E8 CF D6 A3 94 D2 72 10 89 C8 89 60 C4 52<br />
D2 79 6E 99 BD CA 45 B1 00 56 8B F0 11 41 46 53 F3 D0 FA 42<br />
32 44 6D D2 46 E1 D0 06 DE 8D 2D 82 78 DF 89 32 D2 10 57 73<br />
4A B8 CB 69 1B 1B 4E FD F0 DD 15 3B F2 B5 E2 FE F4 75 2A FD<br />
6F CB A2 3D 6F DD EA 96 D2 CA 74 61 0D 41 35 1C 38 A2 C1 83<br />
D0 91 64 EC E2 0B 0B 3D B6 90 98 2A 02 B7 AA EB 06 B8 3E 7B<br />
5D A7 F3 80 DC 39 84 39 34 1B 1D 66 FD 98 D6 DC 6D 33 EF 6C<br />
12 70 62 AF 74 17 7C 94 9D FB 9A 41 21 AC 5A 4B 9F 43 36 7C<br />
CE E6 73 4B BB 23 74 88 1D 96 9A 28 EA 1D B7 A5 F5 D3 FA 68<br />
BE 42 E6 4D 11 DF F9 DD D2 5D E7 DB CD 90 05 25 E0 17 14 6A<br />
21 67 C3 68 BF 8B D8 1F 49 D0 EF 1B 57 12 03 70 2A<br />
------------------------------ snip ------------------------------
Security Notes found on port/service "80 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"CGI Generic Injectable Parameter"<br />
Category<br />
"CGI abuses "<br />
Priority "Low Priority<br />
Synopsis Some CGIs are candidate for extended injection tests.<br />
Description Nessus was able to to inject innocuous strings into CGI parameters and read them back in the HTTP response.<br />
The affected parameters are candidates for extended injection tests like cross-site scripting attacks.<br />
This is not a weakness per se, the main purpose of this test is to speed up other scripts. The results may be useful for<br />
a human pen-tester.<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output Using the GET HTTP method, Nessus found that :<br />
+ The following resources may be vulnerable to injectable parameter :<br />
+ The 'FromRec' parameter of the /BuildaGate5/general2/company_search_tree.php CGI :<br />
/BuildaGate5/general2/company_search_tree.php?FromRec=bpwowf<br />
-------- output --------<br />
<br />
Security Notes found on port/service "443 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"CGI Generic Injectable Parameter"<br />
Category<br />
"CGI abuses "<br />
Priority "Low Priority<br />
Synopsis Some CGIs are candidate for extended injection tests.<br />
Description Nessus was able to to inject innocuous strings into CGI parameters and read them back in the HTTP response.<br />
The affected parameters are candidates for extended injection tests like cross-site scripting attacks.<br />
This is not a weakness per se, the main purpose of this test is to speed up other scripts. The results may be useful for<br />
a human pen-tester.<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output Using the GET HTTP method, Nessus found that :<br />
+ The following resources may be vulnerable to injectable parameter :<br />
+ The 'FromRec' parameter of the /BuildaGate5/general2/company_search_tree.php CGI :
BuildaGate5/general2/company_search_tree.php?FromRec=bpwowf<br />
-------- output --------<br />
<br />
Security Notes found on port/service "25 / tcp / smtp"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"SSL/TLS Diffie-Hellman Modulus
SSL/TLS version : SSLv3<br />
Cipher suite : TLS1_CK_DHE_RSA_WITH_CAMELLIA_128_CBC_SHA<br />
Diffie-Hellman MODP size (bits) : 1024<br />
Logjam attack difficulty : Hard (would require nation-state resources)<br />
SSL/TLS version : SSLv3<br />
Cipher suite : TLS1_CK_DHE_RSA_WITH_AES_256_CBC_SHA<br />
Diffie-Hellman MODP size (bits) : 1024<br />
Logjam attack difficulty : Hard (would require nation-state resources)<br />
SSL/TLS version : SSLv3<br />
Cipher suite : TLS1_CK_DHE_RSA_WITH_3DES_EDE_CBC_SHA<br />
Diffie-Hellman MODP size (bits) : 1024<br />
Logjam attack difficulty : Hard (would require nation-state resources)<br />
SSL/TLS version : SSLv3<br />
Cipher suite : TLS1_CK_DHE_RSA_WITH_DES_CBC_SHA<br />
Diffie-Hellman MODP size (bits) : 1024<br />
Logjam attack difficulty : Hard (would require nation-state resources)<br />
SSL/TLS version : SSLv3<br />
Cipher suite : TLS1_CK_DHE_RSA_WITH_SEED_CBC_SHA<br />
Diffie-Hellman MODP size (bits) : 1024<br />
Logjam attack difficulty : Hard (would require nation-state resources)<br />
SSL/TLS version : TLSv1.0<br />
Cipher suite : TLS1_CK_DHE_RSA_WITH_AES_128_CBC_SHA<br />
Diffie-Hellman MODP size (bits) : 1024<br />
Logjam attack difficulty : Hard (would require nation-state resources)<br />
SSL/TLS version : TLSv1.0<br />
Cipher suite : TLS1_CK_DHE_RSA_EXPORT_WITH_DES40_CBC_SHA<br />
Diffie-Hellman MODP size (bits) : 512<br />
Logjam attack difficulty : Easy (could be carried out by individuals)
SSL/TLS version : TLSv1.0<br />
Cipher suite : TLS1_CK_DHE_RSA_WITH_CAMELLIA_256_CBC_SHA<br />
Diffie-Hellman MODP size (bits) : 1024<br />
Logjam attack difficulty : Hard (would require nation-state resources)<br />
SSL/TLS version : TLSv1.0<br />
Cipher suite : TLS1_CK_DHE_RSA_WITH_CAMELLIA_128_CBC_SHA<br />
Diffie-Hellman MODP size (bits) : 1024<br />
Logjam attack difficulty : Hard (would require nation-state resources)<br />
SSL/TLS version : TLSv1.0<br />
Cipher suite : TLS1_CK_DHE_RSA_WITH_AES_256_CBC_SHA<br />
Diffie-Hellman MODP size (bits) : 1024<br />
Logjam attack difficulty : Hard (would require nation-state resources)<br />
SSL/TLS version : TLSv1.0<br />
Cipher suite : TLS1_CK_DHE_RSA_WITH_3DES_EDE_CBC_SHA<br />
Diffie-Hellman MODP size (bits) : 1024<br />
Logjam attack difficulty : Hard (would require nation-state resources)<br />
SSL/TLS version : TLSv1.0<br />
Cipher suite : TLS1_CK_DHE_RSA_WITH_DES_CBC_SHA<br />
Diffie-Hellman MODP size (bits) : 1024<br />
Logjam attack difficulty : Hard (would require nation-state resources)<br />
SSL/TLS version : TLSv1.0<br />
Cipher suite : TLS1_CK_DHE_RSA_WITH_SEED_CBC_SHA<br />
Diffie-Hellman MODP size (bits) : 1024<br />
Logjam attack difficulty : Hard (would require nation-state resources)<br />
SSL/TLS version : TLSv1.1<br />
Cipher suite : TLS1_CK_DHE_RSA_WITH_AES_128_CBC_SHA<br />
Diffie-Hellman MODP size (bits) : 1024
Logjam attack difficulty : Hard (would require nation-state resources)<br />
SSL/TLS version : TLSv1.1<br />
Cipher suite : TLS1_CK_DHE_RSA_EXPORT_WITH_DES40_CBC_SHA<br />
Diffie-Hellman MODP size (bits) : 512<br />
Logjam attack difficulty : Easy (could be carried out by individuals)<br />
SSL/TLS version : TLSv1.1<br />
Cipher suite : TLS1_CK_DHE_RSA_WITH_CAMELLIA_256_CBC_SHA<br />
Diffie-Hellman MODP size (bits) : 1024<br />
Logjam attack difficulty : Hard (would require nation-state resources)<br />
SSL/TLS version : TLSv1.1<br />
Cipher suite : TLS1_CK_DHE_RSA_WITH_CAMELLIA_128_CBC_SHA<br />
Diffie-Hellman MODP size (bits) : 1024<br />
Logjam attack difficulty : Hard (would require nation-state resources)<br />
SSL/TLS version : TLSv1.1<br />
Cipher suite : TLS1_CK_DHE_RSA_WITH_AES_256_CBC_SHA<br />
Diffie-Hellman MODP size (bits) : 1024<br />
Logjam attack difficulty : Hard (would require nation-state resources)<br />
SSL/TLS version : TLSv1.1<br />
Cipher suite : TLS1_CK_DHE_RSA_WITH_3DES_EDE_CBC_SHA<br />
Diffie-Hellman MODP size (bits) : 1024<br />
Logjam attack difficulty : Hard (would require nation-state resources)<br />
SSL/TLS version : TLSv1.1<br />
Cipher suite : TLS1_CK_DHE_RSA_WITH_DES_CBC_SHA<br />
Diffie-Hellman MODP size (bits) : 1024<br />
Logjam attack difficulty : Hard (would require nation-state resources)<br />
SSL/TLS version : TLSv1.1<br />
Cipher suite : TLS1_CK_DHE_RSA_WITH_SEED_CBC_SHA
Diffie-Hellman MODP size (bits) : 1024<br />
Logjam attack difficulty : Hard (would require nation-state resources)<br />
Addition<br />
Information<br />
CVE:<br />
http://cgi.nessus.org/cve.php3?cve=CVE-2015-4000<br />
BID : 74733 Other references { osvdb : 122331 }<br />
Solution Reconfigure the service to use a unique Diffie-Hellman moduli of 2048 bits or greater.
Security Notes found on port/service "25 / tcp / smtp"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"SSL RC4 Cipher Suites Supported"<br />
Category<br />
"General "<br />
Priority "Low Priority<br />
Synopsis The remote service supports the use of the RC4 cipher.<br />
Description The remote host supports the use of RC4 in one or more cipher suites.<br />
The RC4 cipher is flawed in its generation of a pseudo-random stream of bytes so that a wide variety of small biases<br />
are introduced into the stream, decreasing its randomness.<br />
If plaintext is repeatedly encrypted (e.g., HTTP cookies), and an attacker is able to obtain many (i.e., tens of millions)<br />
ciphertexts, the attacker may be able to derive the plaintext.<br />
See also:<br />
http://<strong>www</strong>.nessus.org/u?217a3666<br />
http://cr.yp.to/talks/2013.03.12/slides.pdf<br />
http://<strong>www</strong>.isg.rhul.ac.uk/tls/<br />
http://<strong>www</strong>.imperva.com/docs/HII_Attacking_SSL_when_using_RC4.pdf<br />
Risk factor CVE-2013-2566 - Low / CVSS BASE SCORE :2.6 CVSS2#(AV:N/AC:H/Au:N/C:P/I:N/A:N), LOW / CVSS BASE SCORE :2.6<br />
CVSS2#AV:N/AC:H/Au:N/C:P/I:N/A:N<br />
Plugin<br />
output List of RC4 cipher suites supported by the remote server :<br />
Low Strength Ciphers (
EXP-RC4-MD5 Kx=RSA(512) Au=RSA Enc=RC4(40) Mac=MD5 export<br />
High Strength Ciphers (>= 112-bit key)<br />
SSLv2<br />
RC4-MD5 Kx=RSA Au=RSA Enc=RC4(128) Mac=MD5<br />
TLSv1<br />
ADH-RC4-MD5 Kx=DH Au=None Enc=RC4(128) Mac=MD5<br />
ECDHE-RSA-RC4-SHA Kx=ECDH Au=RSA Enc=RC4(128) Mac=SHA1<br />
AECDH-RC4-SHA Kx=ECDH Au=None Enc=RC4(128) Mac=SHA1<br />
RC4-MD5 Kx=RSA Au=RSA Enc=RC4(128) Mac=MD5<br />
RC4-SHA Kx=RSA Au=RSA Enc=RC4(128) Mac=SHA1<br />
The fields above are :<br />
{OpenSSL ciphername}<br />
Kx={key exchange}<br />
Au={authentication}<br />
Enc={symmetric encryption method}<br />
Mac={message authentication code}<br />
{export flag}<br />
Addition<br />
Information<br />
CVE:<br />
http://cgi.nessus.org/cve.php3?cve=CVE-2015-2808<br />
http://cgi.nessus.org/cve.php3?cve=CVE-2013-2566<br />
BID : 58796, 73684 Other references { osvdb : 91162, 117855 }<br />
Solution Reconfigure the affected application, if possible, to avoid use of RC4 ciphers. Consider using TLS 1.2 with AES-GCM<br />
suites subject to browser and web server support.
Security Notes found on port/service "8880 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"HTTP Methods Allowed (per directory)"<br />
Category<br />
"Web Servers "<br />
Priority "Low Priority<br />
Synopsis This plugin determines which HTTP methods are allowed on various CGI directories.<br />
Description By calling the OPTIONS method, it is possible to determine which HTTP methods are allowed on each directory.<br />
As this list may be incomplete, the plugin also tests - if 'Thorough tests' are enabled or 'Enable web applications tests'<br />
is set to 'yes' in the scan policy - various known HTTP methods on each directory and considers them as unsupported<br />
if it receives a response code of 400, 403, 405, or 501.<br />
Note that the plugin output is only informational and does not necessarily indicate the presence of any security<br />
vulnerabilities.<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output Based on tests of each method :<br />
- HTTP methods ACL BCOPY BDELETE BMOVE BPROPFIND BPROPPATCH CHECKIN<br />
CHECKOUT CONNECT COPY DEBUG DELETE GET HEAD INDEX LABEL LOCK<br />
MERGE MKACTIVITY MKCOL MKWORKSPACE MOVE NOTIFY OPTIONS ORDERPATCH<br />
PATCH POLL POST PROPFIND PROPPATCH PUT REPORT RPC_IN_DATA<br />
RPC_OUT_DATA SEARCH SUBSCRIBE UNCHECKOUT UNLOCK UNSUBSCRIBE<br />
UPDATE are allowed on :<br />
/admin<br />
/admin-bak<br />
/admin-old<br />
/admin.back<br />
/admin_
administration<br />
/administrator<br />
/adminuser<br />
/adminweb<br />
/sitebuilder<br />
/sitebuildercontent<br />
/sitebuilderfiles<br />
/sitebuilderpictures<br />
- HTTP methods GET HEAD POST are allowed on :<br />
/<br />
/backup<br />
/images<br />
/javascript<br />
- Invalid/unknown HTTP methods are allowed on :<br />
/admin<br />
/admin-bak<br />
/admin-old<br />
/admin.back<br />
/admin_<br />
/administration<br />
/administrator<br />
/adminuser<br />
/adminweb<br />
/sitebuilder<br />
/sitebuildercontent<br />
/sitebuilderfiles<br />
/sitebuilderpictures
Security Notes found on port/service "80 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"HTTP Methods Allowed (per directory)"<br />
Category<br />
"Web Servers "<br />
Priority "Low Priority<br />
Synopsis This plugin determines which HTTP methods are allowed on various CGI directories.<br />
Description By calling the OPTIONS method, it is possible to determine which HTTP methods are allowed on each directory.<br />
As this list may be incomplete, the plugin also tests - if 'Thorough tests' are enabled or 'Enable web applications tests'<br />
is set to 'yes' in the scan policy - various known HTTP methods on each directory and considers them as unsupported<br />
if it receives a response code of 400, 403, 405, or 501.<br />
Note that the plugin output is only informational and does not necessarily indicate the presence of any security<br />
vulnerabilities.<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
Based on the response to an OPTIONS request :<br />
- HTTP methods GET HEAD OPTIONS POST are allowed on :<br />
/BuildaGate5<br />
/BuildaGate5/portals<br />
/BuildaGate5/portals/takti<br />
/cal<br />
/demo<br />
/error<br />
/icons<br />
/images<br />
/pipermail<br />
/test<br />
/tmp
webalizer<br />
Based on tests of each method :<br />
- HTTP methods ACL BCOPY BDELETE BMOVE BPROPFIND BPROPPATCH CHECKIN<br />
CHECKOUT COPY DEBUG DELETE GET HEAD INDEX LABEL LOCK MERGE<br />
MKACTIVITY MKCOL MKWORKSPACE MOVE NOTIFY OPTIONS ORDERPATCH PATCH<br />
POLL POST PROPFIND PROPPATCH PUT REPORT RPC_IN_DATA RPC_OUT_DATA<br />
SEARCH SUBSCRIBE UNCHECKOUT UNLOCK UNSUBSCRIBE UPDATE<br />
are allowed on :<br />
/cgi-bin<br />
/mailman<br />
- HTTP methods GET HEAD OPTIONS POST are allowed on :<br />
/<br />
/BuildaGate5<br />
/BuildaGate5/general2<br />
/BuildaGate5/portals<br />
/BuildaGate5/portals/takti<br />
/cal<br />
/demo<br />
/error<br />
/icons<br />
/images<br />
/pipermail<br />
/test<br />
/tmp<br />
/webalizer<br />
- Invalid/unknown HTTP methods are allowed on :
cgi-bin<br />
/mailman
Security Notes found on port/service "443 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"HTTP Methods Allowed (per directory)"<br />
Category<br />
"Web Servers "<br />
Priority "Low Priority<br />
Synopsis This plugin determines which HTTP methods are allowed on various CGI directories.<br />
Description By calling the OPTIONS method, it is possible to determine which HTTP methods are allowed on each directory.<br />
As this list may be incomplete, the plugin also tests - if 'Thorough tests' are enabled or 'Enable web applications tests'<br />
is set to 'yes' in the scan policy - various known HTTP methods on each directory and considers them as unsupported<br />
if it receives a response code of 400, 403, 405, or 501.<br />
Note that the plugin output is only informational and does not necessarily indicate the presence of any security<br />
vulnerabilities.<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
Based on the response to an OPTIONS request :<br />
- HTTP methods GET HEAD OPTIONS POST are allowed on :<br />
/BuildaGate5<br />
/BuildaGate5/portals<br />
/BuildaGate5/portals/takti<br />
/cal<br />
/demo<br />
/error<br />
/icons<br />
/images<br />
/pipermail<br />
/test<br />
/tmp
webalizer<br />
Based on tests of each method :<br />
- HTTP methods ACL BCOPY BDELETE BMOVE BPROPFIND BPROPPATCH CHECKIN<br />
CHECKOUT COPY DEBUG DELETE GET HEAD INDEX LABEL LOCK MERGE<br />
MKACTIVITY MKCOL MKWORKSPACE MOVE NOTIFY OPTIONS ORDERPATCH PATCH<br />
POLL POST PROPFIND PROPPATCH PUT REPORT RPC_IN_DATA RPC_OUT_DATA<br />
SEARCH SUBSCRIBE UNCHECKOUT UNLOCK UNSUBSCRIBE UPDATE<br />
are allowed on :<br />
/cgi-bin<br />
/mailman<br />
- HTTP methods GET HEAD OPTIONS POST are allowed on :<br />
/<br />
/BuildaGate5<br />
/BuildaGate5/general2<br />
/BuildaGate5/portals<br />
/BuildaGate5/portals/takti<br />
/cal<br />
/demo<br />
/error<br />
/icons<br />
/images<br />
/pipermail<br />
/test<br />
/tmp<br />
/webalizer<br />
- Invalid/unknown HTTP methods are allowed on :
cgi-bin<br />
/mailman
Security Notes found on port/service "443 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"Non-compliant Strict Transport Security (STS)"<br />
Category<br />
"Service detection "<br />
Priority "Low Priority<br />
Synopsis The remote web server implements Strict Transport Security incorrectly.<br />
Description The remote web server implements Strict Transport Security. However, it does not respect all the requirements of<br />
the STS draft standard.<br />
See also:<br />
http://<strong>www</strong>.nessus.org/u?2fb3aca6<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output The response from the web server listening on port 80 :<br />
- does not contain a Status-Code of 301.<br />
- does not contain a Location header field.<br />
The following are the headers received :<br />
HTTP/1.1 200 OK Server: nginx Date: Tue, 12 Jul 2016 07:50:54 GMT Content-Type: text/html; charset=utf-8 Transfer-<br />
Encoding: chunked Connection: keep-alive Expires: Thu, 19 Nov 1981 08:52:00 GMT Pragma: no-cache Cache-Control:<br />
private, max-age=10800, pre-check=10800 Set-Cookie: PHPSESSID=ao5kq83e9upktblbipmretc8g1; path=/; HttpOnly<br />
X-Frame-Options: SAMEORIGIN X-XSS-Protection: 1; mode=block X-Content-Type-Options: nosniff X-WebKit-CSP:<br />
default-src 'self' X-Permitted-Cross-Domain-Policies: master-only Strict-Transport-Security: max-age=15768000;<br />
includeSubDomains MS-Author-Via: DAV
Security Notes found on port/service "80 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"Non-compliant Strict Transport Security (STS)"<br />
Category<br />
"Service detection "<br />
Priority "Low Priority<br />
Synopsis The remote web server implements Strict Transport Security incorrectly.<br />
Description The remote web server implements Strict Transport Security. However, it does not respect all the requirements of<br />
the STS draft standard.<br />
See also:<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
http://<strong>www</strong>.nessus.org/u?2fb3aca6<br />
The Strict-Transport-Security header must not be sent over an<br />
unencrypted channel.
Security Notes found on port/service "80 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"Strict Transport Security (STS) Detection"<br />
Category<br />
"Service detection "<br />
Priority "Low Priority<br />
Synopsis The remote web server implements Strict Transport Security.<br />
Description The remote web server implements Strict Transport Security (STS).<br />
The goal of STS is to make sure that a user does not accidentally downgrade the security of his or her browser.<br />
All unencrypted HTTP connections are redirected to HTTPS. The browser is expected to treat all cookies as 'secure'<br />
and to close the connection in the event of potentially insecure situations.<br />
See also:<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output The STS header line is :<br />
http://<strong>www</strong>.nessus.org/u?2fb3aca6<br />
Strict-Transport-Security: max-age=15768000;includeSubDomains
Security Notes found on port/service "443 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"Strict Transport Security (STS) Detection"<br />
Category<br />
"Service detection "<br />
Priority "Low Priority<br />
Synopsis The remote web server implements Strict Transport Security.<br />
Description The remote web server implements Strict Transport Security (STS).<br />
The goal of STS is to make sure that a user does not accidentally downgrade the security of his or her browser.<br />
All unencrypted HTTP connections are redirected to HTTPS. The browser is expected to treat all cookies as 'secure'<br />
and to close the connection in the event of potentially insecure situations.<br />
See also:<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output The STS header line is :<br />
http://<strong>www</strong>.nessus.org/u?2fb3aca6<br />
Strict-Transport-Security: max-age=15768000;includeSubDomains
Security Notes found on port/service "80 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"Web Application Cookies Not Marked Secure"<br />
Category<br />
"Web Servers "<br />
Priority "Low Priority<br />
Synopsis HTTP session cookies might be transmitted in cleartext.<br />
Description The remote web application sets various cookies throughout a user's unauthenticated and authenticated session.<br />
However, there are instances where the application is running over unencrypted HTTP or the cookies are not marked<br />
'secure', meaning the browser could send them back over an unencrypted link under certain circumstances. As a<br />
result, it may be possible for a remote attacker to intercept these cookies.<br />
Note that this plugin detects all general cookies missing the 'secure' cookie flag, whereas plugin 49218 (Web<br />
Application Session Cookies Not Marked Secure) will only detect session cookies from an authenticated session<br />
missing the secure cookie flag.<br />
See also:<br />
https://<strong>www</strong>.owasp.org/index.php/SecureFlag<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output The following cookies do not set the secure cookie flag :<br />
Name : SBSESSION<br />
Path : /<br />
Value : 99b565da84db95ade87a5090ef15dcee<br />
Domain :<br />
Version : 1<br />
Expires :<br />
Comment :<br />
Secure : 0<br />
Httponly : 1<br />
Port :
Name : PHPSESSID<br />
Path : /<br />
Value : 4vnvsqdlplj4k261hr7021oec0<br />
Domain :<br />
Version : 1<br />
Expires :<br />
Comment :<br />
Secure : 0<br />
Httponly : 1<br />
Port :<br />
Solution Each cookie should be carefully reviewed to determine if it contains sensitive data or is relied upon for a security<br />
decision.<br />
If possible, ensure all communication occurs over an encrypted channel and add the 'secure' attribute to all session<br />
cookies or any cookies containing sensitive data.
Security Notes found on port/service "8880 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"Web Application Cookies Not Marked Secure"<br />
Category<br />
"Web Servers "<br />
Priority "Low Priority<br />
Synopsis HTTP session cookies might be transmitted in cleartext.<br />
Description The remote web application sets various cookies throughout a user's unauthenticated and authenticated session.<br />
However, there are instances where the application is running over unencrypted HTTP or the cookies are not marked<br />
'secure', meaning the browser could send them back over an unencrypted link under certain circumstances. As a<br />
result, it may be possible for a remote attacker to intercept these cookies.<br />
Note that this plugin detects all general cookies missing the 'secure' cookie flag, whereas plugin 49218 (Web<br />
Application Session Cookies Not Marked Secure) will only detect session cookies from an authenticated session<br />
missing the secure cookie flag.<br />
See also:<br />
https://<strong>www</strong>.owasp.org/index.php/SecureFlag<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output The following cookies do not set the secure cookie flag :<br />
Name : SBSESSION<br />
Path : /<br />
Value : 99b565da84db95ade87a5090ef15dcee<br />
Domain :<br />
Version : 1<br />
Expires :<br />
Comment :<br />
Secure : 0<br />
Httponly : 1<br />
Port :
Name : PHPSESSID<br />
Path : /<br />
Value : 4vnvsqdlplj4k261hr7021oec0<br />
Domain :<br />
Version : 1<br />
Expires :<br />
Comment :<br />
Secure : 0<br />
Httponly : 1<br />
Port :<br />
Solution Each cookie should be carefully reviewed to determine if it contains sensitive data or is relied upon for a security<br />
decision.<br />
If possible, ensure all communication occurs over an encrypted channel and add the 'secure' attribute to all session<br />
cookies or any cookies containing sensitive data.
Security Notes found on port/service "443 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"Web Application Cookies Not Marked Secure"<br />
Category<br />
"Web Servers "<br />
Priority "Low Priority<br />
Synopsis HTTP session cookies might be transmitted in cleartext.<br />
Description The remote web application sets various cookies throughout a user's unauthenticated and authenticated session.<br />
However, there are instances where the application is running over unencrypted HTTP or the cookies are not marked<br />
'secure', meaning the browser could send them back over an unencrypted link under certain circumstances. As a<br />
result, it may be possible for a remote attacker to intercept these cookies.<br />
Note that this plugin detects all general cookies missing the 'secure' cookie flag, whereas plugin 49218 (Web<br />
Application Session Cookies Not Marked Secure) will only detect session cookies from an authenticated session<br />
missing the secure cookie flag.<br />
See also:<br />
https://<strong>www</strong>.owasp.org/index.php/SecureFlag<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output The following cookies do not set the secure cookie flag :<br />
Name : SBSESSION<br />
Path : /<br />
Value : 99b565da84db95ade87a5090ef15dcee<br />
Domain :<br />
Version : 1<br />
Expires :<br />
Comment :<br />
Secure : 0<br />
Httponly : 1<br />
Port :
Name : PHPSESSID<br />
Path : /<br />
Value : 4vnvsqdlplj4k261hr7021oec0<br />
Domain :<br />
Version : 1<br />
Expires :<br />
Comment :<br />
Secure : 0<br />
Httponly : 1<br />
Port :<br />
Solution Each cookie should be carefully reviewed to determine if it contains sensitive data or is relied upon for a security<br />
decision.<br />
If possible, ensure all communication occurs over an encrypted channel and add the 'secure' attribute to all session<br />
cookies or any cookies containing sensitive data.
Security Notes found on port/service "8880 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"Web Application Sitemap"<br />
Category<br />
Priority<br />
"Web Servers "<br />
"Low Priority<br />
Synopsis The remote web server hosts linkable content that can be crawled by Nessus.<br />
Description The remote web server contains linkable content that can be used to gather information about a target.<br />
See also:<br />
http://<strong>www</strong>.nessus.org/u?5496c8d9<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output The following sitemap was created from crawling linkable content on the target host :<br />
- http://<strong>www</strong>.takti.co.il:8880/sitebuilder/<br />
Attached is a copy of the sitemap file.
Security Notes found on port/service "443 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"Web Application Sitemap"<br />
Category<br />
Priority<br />
"Web Servers "<br />
"Low Priority<br />
Synopsis The remote web server hosts linkable content that can be crawled by Nessus.<br />
Description The remote web server contains linkable content that can be used to gather information about a target.<br />
See also:<br />
http://<strong>www</strong>.nessus.org/u?5496c8d9<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output The following sitemap was created from crawling linkable content on the target host :<br />
- https://<strong>www</strong>.takti.co.il/<br />
- https://<strong>www</strong>.takti.co.il/BuildaGate5/<br />
- https://<strong>www</strong>.takti.co.il/BuildaGate5/general2/<br />
- https://<strong>www</strong>.takti.co.il/BuildaGate5/general2/company_search_tree.php<br />
- https://<strong>www</strong>.takti.co.il/BuildaGate5/general2/styletakti.css<br />
- https://<strong>www</strong>.takti.co.il/BuildaGate5/portals/<br />
- https://<strong>www</strong>.takti.co.il/BuildaGate5/portals/takti/<br />
- https://<strong>www</strong>.takti.co.il/BuildaGate5/portals/takti/styleDefs.css<br />
- https://<strong>www</strong>.takti.co.il/cal/<br />
- https://<strong>www</strong>.takti.co.il/demo/<br />
- https://<strong>www</strong>.takti.co.il/demo/1.html<br />
- https://<strong>www</strong>.takti.co.il/demo/2.html<br />
- https://<strong>www</strong>.takti.co.il/demo/3.html<br />
- https://<strong>www</strong>.takti.co.il/demo/4.html<br />
- https://<strong>www</strong>.takti.co.il/demo/index.html<br />
- https://<strong>www</strong>.takti.co.il/images/<br />
- https://<strong>www</strong>.takti.co.il/test/<br />
- https://<strong>www</strong>.takti.co.il/webalizer/
Attached is a copy of the sitemap file.
Security Notes found on port/service "80 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"Web Application Sitemap"<br />
Category<br />
Priority<br />
"Web Servers "<br />
"Low Priority<br />
Synopsis The remote web server hosts linkable content that can be crawled by Nessus.<br />
Description The remote web server contains linkable content that can be used to gather information about a target.<br />
See also:<br />
http://<strong>www</strong>.nessus.org/u?5496c8d9<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output The following sitemap was created from crawling linkable content on the target host :<br />
- http://<strong>www</strong>.takti.co.il/<br />
- http://<strong>www</strong>.takti.co.il/BuildaGate5/<br />
- http://<strong>www</strong>.takti.co.il/BuildaGate5/general2/<br />
- http://<strong>www</strong>.takti.co.il/BuildaGate5/general2/company_search_tree.php<br />
- http://<strong>www</strong>.takti.co.il/BuildaGate5/general2/styletakti.css<br />
- http://<strong>www</strong>.takti.co.il/BuildaGate5/portals/<br />
- http://<strong>www</strong>.takti.co.il/BuildaGate5/portals/takti/<br />
- http://<strong>www</strong>.takti.co.il/BuildaGate5/portals/takti/styleDefs.css<br />
- http://<strong>www</strong>.takti.co.il/cal/<br />
- http://<strong>www</strong>.takti.co.il/demo/<br />
- http://<strong>www</strong>.takti.co.il/demo/1.html<br />
- http://<strong>www</strong>.takti.co.il/demo/2.html<br />
- http://<strong>www</strong>.takti.co.il/demo/3.html<br />
- http://<strong>www</strong>.takti.co.il/demo/4.html<br />
- http://<strong>www</strong>.takti.co.il/demo/index.html<br />
- http://<strong>www</strong>.takti.co.il/images/<br />
- http://<strong>www</strong>.takti.co.il/test/<br />
- http://<strong>www</strong>.takti.co.il/webalizer/
Attached is a copy of the sitemap file.
Security Notes found on port/service "25 / tcp / smtp"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"SMTP Server Detection"<br />
Category "Service detection "<br />
Priority "Low Priority<br />
Synopsis An SMTP server is listening on the remote port.<br />
Description The remote host is running a mail (SMTP) server on this port.<br />
Since SMTP servers are the targets of spammers, it is recommended you disable it if you do not use it.<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output Remote SMTP server banner :<br />
220 server.takti.co.il ESMTP Postfix<br />
Solution Disable this service if you do not use it, or filter incoming traffic to this port.
Security Notes found on port/service "25 / tcp / smtp"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"SMTP Service STARTTLS Command Support"<br />
Category<br />
"SMTP problems "<br />
Priority "Low Priority<br />
Synopsis The remote mail service supports encrypting traffic.<br />
Description The remote SMTP service supports the use of the 'STARTTLS' command to switch from a cleartext to an encrypted<br />
communications channel.<br />
See also:<br />
http://en.wikipedia.org/wiki/STARTTLS<br />
http://tools.ietf.org/html/rfc2487<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
Here is the SMTP service's SSL certificate that Nessus was able to<br />
collect after sending a 'STARTTLS' command :<br />
------------------------------ snip ------------------------------<br />
Subject Name:<br />
Country: US<br />
State/Province: Virginia<br />
Locality: Herndon<br />
Organization: Parallels<br />
Organization Unit: Parallels Panel<br />
Common Name: Parallels Panel<br />
Email Address: info@parallels.com<br />
Issuer Name:<br />
Country: US
State/Province: Virginia<br />
Locality: Herndon<br />
Organization: Parallels<br />
Organization Unit: Parallels Panel<br />
Common Name: Parallels Panel<br />
Email Address: info@parallels.com<br />
Serial Number: 55 2B 60 34<br />
Version: 1<br />
Signature Algorithm: SHA-1 With RSA Encryption<br />
Not Valid Before: Apr 13 06:20:36 2015 GMT<br />
Not Valid After: Apr 12 06:20:36 2016 GMT<br />
Public Key Info:<br />
Algorithm: RSA Encryption<br />
Key Length: 2048 bits<br />
Public Key: 00 A6 AD 66 0F 5D A6 09 2C 92 16 06 ED 1E D4 95 D2 10 34 BA<br />
FE 8C A9 25 25 66 15 01 CE 32 8B C2 CE BD 17 87 B1 DD AB 88<br />
61 EA 30 02 F5 5A EE 98 88 0C 52 C3 E0 A0 2A 9D FC 06 1F FD<br />
BE FD 46 20 C0 A9 48 BB 2A B3 FD B3 E6 90 48 44 45 F1 60 BC<br />
CE FA 8A CF E7 44 11 D0 71 20 53 28 28 E4 0C CF A1 57 41 E8<br />
AA 0F A2 55 6E DE B0 1D DC EB 9A 86 21 55 23 31 7D 11 4E 3A<br />
CC 7F 51 8E 68 8E B2 B7 F0 7A A5 7B C0 C9 CC 6F 9D 99 A0 DD<br />
EB 81 C1 20 93 1B 18 70 BE C9 C1 5E FE D3 38 60 07 81 67 F6<br />
A0 1D 9C 96 5F D3 8C 32 E7 5C 3A 2C FA 5E 92 B9 85 1D 84 F7<br />
49 20 9C D1 98 B8 8E BE E1 D6 72 45 E8 50 20 82 09 4E 8A 0B<br />
C7 2D F6 8D 10 FB 31 37 B7 D0 68 DB 02 37 0B 57 0F 62 1C 57<br />
C1 16 3F 24 6A 1F C0 55 10 92 6C 0B 21 0E 41 67 1A 86 EC 9E<br />
EE CF C8 BF 19 3D 68 89 06 D0 43 56 B6 B6 AF 3F E7<br />
Exponent: 01 00 01
Signature Length: 256 bytes / 2048 bits<br />
Signature: 00 40 63 59 39 62 79 E0 E2 5A 04 8B EB CA 6D 60 A9 2E AB D5<br />
8F DB 56 8A C8 19 B1 62 8E 7A 88 85 F6 C1 E5 18 C1 6B C9 6A<br />
30 76 B1 DA 92 38 E8 CF D6 A3 94 D2 72 10 89 C8 89 60 C4 52<br />
D2 79 6E 99 BD CA 45 B1 00 56 8B F0 11 41 46 53 F3 D0 FA 42<br />
32 44 6D D2 46 E1 D0 06 DE 8D 2D 82 78 DF 89 32 D2 10 57 73<br />
4A B8 CB 69 1B 1B 4E FD F0 DD 15 3B F2 B5 E2 FE F4 75 2A FD<br />
6F CB A2 3D 6F DD EA 96 D2 CA 74 61 0D 41 35 1C 38 A2 C1 83<br />
D0 91 64 EC E2 0B 0B 3D B6 90 98 2A 02 B7 AA EB 06 B8 3E 7B<br />
5D A7 F3 80 DC 39 84 39 34 1B 1D 66 FD 98 D6 DC 6D 33 EF 6C<br />
12 70 62 AF 74 17 7C 94 9D FB 9A 41 21 AC 5A 4B 9F 43 36 7C<br />
CE E6 73 4B BB 23 74 88 1D 96 9A 28 EA 1D B7 A5 F5 D3 FA 68<br />
BE 42 E6 4D 11 DF F9 DD D2 5D E7 DB CD 90 05 25 E0 17 14 6A<br />
21 67 C3 68 BF 8B D8 1F 49 D0 EF 1B 57 12 03 70 2A<br />
------------------------------ snip ------------------------------
Security Notes found on port/service "110 / tcp / pop3"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"POP3 Cleartext Logins Permitted"<br />
Category<br />
"Misc. "<br />
Priority "Low Priority<br />
Synopsis The remote POP3 daemon allows credentials to be transmitted in cleartext.<br />
Description The remote host is running a POP3 daemon that allows cleartext logins over unencrypted connections. An attacker<br />
can uncover user names and passwords by sniffing traffic to the POP3 daemon if a less secure authentication<br />
mechanism (eg, USER command, AUTH PLAIN, AUTH LOGIN) is used.<br />
See also:<br />
http://tools.ietf.org/html/rfc2222<br />
http://tools.ietf.org/html/rfc2595<br />
Risk factor LOW / CVSS BASE SCORE :2.6 CVSS2#AV:N/AC:H/Au:N/C:P/I:N/A:N<br />
Plugin<br />
output<br />
The following cleartext methods are supported :<br />
SASL LOGIN CRAM-MD5 CRAM-SHA1 CRAM-SHA256 PLAIN<br />
USER<br />
Solution Contact your vendor for a fix or encrypt traffic with SSL / TLS using stunnel.
Security Notes found on port/service "25 / tcp / smtp"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"SMTP Service Cleartext Login Permitted"<br />
Category<br />
"SMTP problems "<br />
Priority "Low Priority<br />
Synopsis The remote mail server allows cleartext logins.<br />
Description The remote host is running an SMTP server that advertises that it allows cleartext logins over unencrypted<br />
connections. An attacker may be able to uncover user names and passwords by sniffing traffic to the server if a less<br />
secure authentication mechanism (i.e. LOGIN or PLAIN) is used.<br />
See also:<br />
http://tools.ietf.org/html/rfc4422<br />
http://tools.ietf.org/html/rfc4954<br />
Risk factor LOW / CVSS BASE SCORE :2.6 CVSS2#AV:N/AC:H/Au:N/C:P/I:N/A:N<br />
Plugin<br />
output<br />
The SMTP server advertises the following SASL methods over an<br />
unencrypted channel :<br />
All supported methods : PLAIN, LOGIN, DIGEST-MD5, CRAM-MD5<br />
Cleartext methods : PLAIN, LOGIN<br />
Solution Configure the service to support less secure authentication mechanisms only over an encrypted channel.
Security Notes found on port/service "8880 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"Nessus SYN scanner"<br />
Category<br />
"Port scanners "<br />
Priority "Low Priority<br />
Synopsis It is possible to determine which TCP ports are open.<br />
Description This plugin is a SYN 'half-open' port scanner. It shall be reasonably quick even against a firewalled target.<br />
Note that SYN scans are less intrusive than TCP (full connect) scans against broken services, but they might cause<br />
problems for less robust firewalls and also leave unclosed connections on the remote target, if the network is loaded.<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
Port 8880/tcp was found to be open<br />
Solution Protect your target with an IP filter.
Security Notes found on port/service "443 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"Nessus SYN scanner"<br />
Category<br />
"Port scanners "<br />
Priority "Low Priority<br />
Synopsis It is possible to determine which TCP ports are open.<br />
Description This plugin is a SYN 'half-open' port scanner. It shall be reasonably quick even against a firewalled target.<br />
Note that SYN scans are less intrusive than TCP (full connect) scans against broken services, but they might cause<br />
problems for less robust firewalls and also leave unclosed connections on the remote target, if the network is loaded.<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
Port 443/tcp was found to be open<br />
Solution Protect your target with an IP filter.
Security Notes found on port/service "110 / tcp / pop3"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"Nessus SYN scanner"<br />
Category<br />
"Port scanners "<br />
Priority "Low Priority<br />
Synopsis It is possible to determine which TCP ports are open.<br />
Description This plugin is a SYN 'half-open' port scanner. It shall be reasonably quick even against a firewalled target.<br />
Note that SYN scans are less intrusive than TCP (full connect) scans against broken services, but they might cause<br />
problems for less robust firewalls and also leave unclosed connections on the remote target, if the network is loaded.<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
Port 110/tcp was found to be open<br />
Solution Protect your target with an IP filter.
Security Notes found on port/service "80 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"Nessus SYN scanner"<br />
Category<br />
"Port scanners "<br />
Priority "Low Priority<br />
Synopsis It is possible to determine which TCP ports are open.<br />
Description This plugin is a SYN 'half-open' port scanner. It shall be reasonably quick even against a firewalled target.<br />
Note that SYN scans are less intrusive than TCP (full connect) scans against broken services, but they might cause<br />
problems for less robust firewalls and also leave unclosed connections on the remote target, if the network is loaded.<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
Port 80/tcp was found to be open<br />
Solution Protect your target with an IP filter.
Security Notes found on port/service "25 / tcp / smtp"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"Nessus SYN scanner"<br />
Category<br />
"Port scanners "<br />
Priority "Low Priority<br />
Synopsis It is possible to determine which TCP ports are open.<br />
Description This plugin is a SYN 'half-open' port scanner. It shall be reasonably quick even against a firewalled target.<br />
Note that SYN scans are less intrusive than TCP (full connect) scans against broken services, but they might cause<br />
problems for less robust firewalls and also leave unclosed connections on the remote target, if the network is loaded.<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
Port 25/tcp was found to be open<br />
Solution Protect your target with an IP filter.
Security Notes found on port/service "25 / tcp / smtp"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"SMTP Authentication Methods"<br />
Category<br />
Priority<br />
"SMTP problems "<br />
"Low Priority<br />
Synopsis The remote mail server supports authentication.<br />
Description The remote SMTP server advertises that it supports authentication.<br />
See also:<br />
http://tools.ietf.org/html/rfc4422<br />
http://tools.ietf.org/html/rfc4954<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
The following authentication methods are advertised by the SMTP<br />
server without encryption :<br />
CRAM-MD5<br />
DIGEST-MD5<br />
LOGIN<br />
PLAIN<br />
The following authentication methods are advertised by the SMTP<br />
server with encryption :<br />
CRAM-MD5<br />
DIGEST-MD5<br />
LOGIN<br />
PLAIN<br />
Solution Review the list of methods and whether they're available over an encrypted channel.
Security Notes found on port/service "0 / tcp / "<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"Patch Report"<br />
Category<br />
"General "<br />
Priority "Low Priority<br />
Synopsis The remote host is missing several patches.<br />
Description The remote host is missing one or more security patches. This plugin lists the newest version of each patch to<br />
install to make sure the remote host is up-to-date.<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
. You need to take the following action :<br />
[ OpenSSL AES-NI Padding Oracle MitM Information Disclosure (91572) ]<br />
+ Action to take : Upgrade to OpenSSL version 1.0.1t / 1.0.2h or later.<br />
Solution Install the patches listed below.
Security Notes found on port/service "443 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"TLS Next Protocols Supported"<br />
Category<br />
"General "<br />
Priority "Low Priority<br />
Synopsis The remote service advertises one or more protocols as being supported over TLS.<br />
Description This script detects which protocols are advertised by the remote service to be encapsulated by TLS connections.<br />
Note that Nessus did not attempt to negotiate TLS sessions with the protocols shown. The remote service may be<br />
falsely advertising these protocols and / or failing to advertise other supported protocols.<br />
See also:<br />
http://tools.ietf.org/html/draft-agl-tls-nextprotoneg<br />
https://technotes.googlecode.com/git/nextprotoneg.html<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
The target advertises that the following protocols are<br />
supported over SSL / TLS :<br />
http/1.1
Security Notes found on port/service "443 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"SSL Certificate Chain Contains Unnecessary Certificates"<br />
Category<br />
"General "<br />
Priority "Low Priority<br />
Synopsis The X.509 certificate chain used by this service contains certificates that aren't required to form a path to the CA.<br />
Description At least one of the X.509 certificates sent by the remote host is not required to form a path from the server's own<br />
certificate to the CA. This may indicate that the certificate bundle installed with the server's certificate is for<br />
certificates lower in the certificate hierarchy.<br />
Some SSL implementations, often those found in embedded devices, cannot handle certificate chains with unused<br />
certificates.<br />
See also:<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
http://<strong>www</strong>.ietf.org/rfc/rfc4346.txt<br />
The following certificates were part of the certificate chain<br />
sent by the remote host, but are not necessary to building the<br />
certificate chain.<br />
|-Country: US<br />
|-Organization: GeoTrust Inc.<br />
|-Common Name: RapidSSL SHA256 CA - G3<br />
Solution Remove unnecessary certificates from the certificate chain.
Security Notes found on port/service "0 / tcp / "<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"OS Identification Failed"<br />
Category<br />
"General "<br />
Priority "Low Priority<br />
Synopsis It was not possible to determine the remote operating system.<br />
Description Using a combination of remote probes (TCP/IP, SMB, HTTP, NTP, SNMP, etc), it was possible to gather one or more<br />
fingerprints from the remote system. Unfortunately, though, Nessus does not currently know how to use them to<br />
identify the overall system.<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
If you think these signatures would help us improve OS fingerprinting,<br />
please send them to :<br />
os-signatures@nessus.org<br />
Be sure to include a brief description of the device itself, such as<br />
the actual operating system or product / model names.<br />
HTTP:!:Server: nginx<br />
SMTP:!:220 server.takti.co.il ESMTP Postfix<br />
SSLcert:!:i/CN:RapidSSL SHA256 CAi/O:GeoTrust Inc.s/CN:<strong>www</strong>.takti.co.il<br />
865c6be84d80b2911150619c0930ef84a7a21a9c<br />
i/CN:Para<br />
llels Paneli/O:Parallelsi/OU:Parallels Panels/CN:Parallels Panels/O:Parallelss/OU:Parallels Panel<br />
8b46c6563e400d0e59071cbf0edf7817746408e8<br />
i/CN:Parallels Paneli/O:Parallelsi/OU:Parallels Panels/CN:Parallels Panels/O:Parallelss/OU:Parallels Panel<br />
8b46c6563e400d0e59071cbf0edf7817746408e8
Security Notes found on port/service "25 / tcp / smtp"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"smtpscan SMTP Fingerprinting"<br />
Category<br />
"SMTP problems "<br />
Priority "Low Priority<br />
Synopsis It is possible to fingerprint the remote mail server.<br />
Description smtpscan is a SMTP fingerprinting tool written by Julien Bordet. It identifies the remote mail server even if the<br />
banners were changed.<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output This server could be fingerprinted as :<br />
Postfix 1.1.11
Security Notes found on port/service "8880 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"Web Server Directory Enumeration"<br />
Category<br />
"Web Servers "<br />
Priority "Low Priority<br />
Synopsis It is possible to enumerate directories on the web server.<br />
Description This plugin attempts to determine the presence of various common directories on the remote web server. By<br />
sending a request for a directory, the web server response code indicates if it is a valid directory or not.<br />
See also:<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
http://projects.webappsec.org/Predictable-Resource-Location<br />
The following directories were discovered:<br />
/admin, /admin-bak, /admin-old, /admin.back, /admin_, /administration, /administrator, /adminuser, /adminweb,<br />
/backup, /images, /javascript, /sitebuildercontent, /sitebuilderfiles, /sitebuilderpictures, /sitebuilder<br />
While this is not, in and of itself, a bug, you should manually inspect<br />
these directories to ensure that they are in compliance with company<br />
security standards
Security Notes found on port/service "80 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"Web Server Directory Enumeration"<br />
Category<br />
"Web Servers "<br />
Priority "Low Priority<br />
Synopsis It is possible to enumerate directories on the web server.<br />
Description This plugin attempts to determine the presence of various common directories on the remote web server. By<br />
sending a request for a directory, the web server response code indicates if it is a valid directory or not.<br />
See also:<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
http://projects.webappsec.org/Predictable-Resource-Location<br />
The following directories were discovered:<br />
/cgi-bin, /demo, /pipermail, /test, /tmp, /webalizer, /error, /icons, /images, /mailman, /cal<br />
While this is not, in and of itself, a bug, you should manually inspect<br />
these directories to ensure that they are in compliance with company<br />
security standards
Security Notes found on port/service "443 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"Web Server Directory Enumeration"<br />
Category<br />
"Web Servers "<br />
Priority "Low Priority<br />
Synopsis It is possible to enumerate directories on the web server.<br />
Description This plugin attempts to determine the presence of various common directories on the remote web server. By<br />
sending a request for a directory, the web server response code indicates if it is a valid directory or not.<br />
See also:<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
http://projects.webappsec.org/Predictable-Resource-Location<br />
The following directories were discovered:<br />
/cgi-bin, /demo, /pipermail, /test, /tmp, /webalizer, /error, /icons, /images, /mailman, /cal<br />
While this is not, in and of itself, a bug, you should manually inspect<br />
these directories to ensure that they are in compliance with company<br />
security standards
Security Notes found on port/service "443 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"HTTP X-Frame-Options Response Header Usage"<br />
Category<br />
"CGI abuses "<br />
Priority "Low Priority<br />
Synopsis The remote web server does not take steps to mitigate a class of web application vulnerabilities.<br />
Description The remote web server in some responses sets a permissive X-Frame-Options response header or does not set one<br />
at all.<br />
The X-Frame-Options header has been proposed by Microsoft as a way to mitigate clickjacking attacks and is currently<br />
supported by all major browser vendors<br />
See also:<br />
http://en.wikipedia.org/wiki/Clickjacking<br />
http://<strong>www</strong>.nessus.org/u?399b1f56<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
The following pages do not set a X-Frame-Options response header or set a permissive policy:<br />
- https://<strong>www</strong>.takti.co.il/BuildaGate5/portals/<br />
- https://<strong>www</strong>.takti.co.il/BuildaGate5/portals/takti/<br />
- https://<strong>www</strong>.takti.co.il/webalizer/<br />
Solution Set a properly configured X-Frame-Options header for all requested resources.
Security Notes found on port/service "80 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"HTTP X-Frame-Options Response Header Usage"<br />
Category<br />
"CGI abuses "<br />
Priority "Low Priority<br />
Synopsis The remote web server does not take steps to mitigate a class of web application vulnerabilities.<br />
Description The remote web server in some responses sets a permissive X-Frame-Options response header or does not set one<br />
at all.<br />
The X-Frame-Options header has been proposed by Microsoft as a way to mitigate clickjacking attacks and is currently<br />
supported by all major browser vendors<br />
See also:<br />
http://en.wikipedia.org/wiki/Clickjacking<br />
http://<strong>www</strong>.nessus.org/u?399b1f56<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
The following pages do not set a X-Frame-Options response header or set a permissive policy:<br />
- http://<strong>www</strong>.takti.co.il/BuildaGate5/portals/<br />
- http://<strong>www</strong>.takti.co.il/BuildaGate5/portals/takti/<br />
- http://<strong>www</strong>.takti.co.il/webalizer/<br />
Solution Set a properly configured X-Frame-Options header for all requested resources.
Security Notes found on port/service "443 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"CGI Generic Tests Load Estimation (all tests)"<br />
Category<br />
"CGI abuses "<br />
Priority "Low Priority<br />
Synopsis Load estimation for web application tests.<br />
Description This script computes the maximum number of requests that would be done by the generic web tests, depending on<br />
miscellaneous options. It does not perform any test by itself.<br />
The results can be used to estimate the duration of these tests, or the complexity of additional manual tests.<br />
Note that the script does not try to compute this duration based on external factors such as the network and web<br />
servers loads.<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
Here are the estimated number of requests in miscellaneous modes<br />
for one method only (GET or POST) :<br />
[Single / Some Pairs / All Pairs / Some Combinations / All Combinations]<br />
cross-site scripting (comprehensive test): S=420 SP=6006 AP=6006 SC=4472832 AC=4472832<br />
cross-site scripting (quick test) : S=220 SP=3146 AP=3146 SC=2342912 AC=2342912<br />
persistent XSS : S=80 SP=1144 AP=1144 SC=851968 AC=851968<br />
arbitrary command execution : S=440 SP=6292 AP=6292 SC=4685824 AC=4685824<br />
web code injection : S=20 SP=286 AP=286 SC=212992 AC=212992<br />
HTML injection : S=5 SP=5 AP=5 SC=5 AC=5<br />
arbitrary command execution (time based) : S=120 SP=1716 AP=1716 SC=1277952 AC=1277952<br />
script injection : S=1 SP=1 AP=1 SC=1 AC=1<br />
XML injection : S=20 SP=286 AP=286 SC=212992 AC=212992<br />
unseen parameters : S=700 SP=10010 AP=10010 SC=7454720 AC=7454720<br />
directory traversal (write access) : S=40 SP=572 AP=572 SC=425984 AC=425984<br />
SQL injection (2nd order) : S=20 SP=286 AP=286 SC=212992 AC=212992
on site request forgery : S=1 SP=1 AP=1 SC=1 AC=1<br />
blind SQL injection (4 requests) : S=80 SP=1144 AP=1144 SC=851968 AC=851968<br />
HTTP response splitting : S=9 SP=9 AP=9 SC=9 AC=9<br />
directory traversal (extended test) : S=1020 SP=14586 AP=14586 SC=10862592 AC=10862592<br />
header injection : S=2 SP=2 AP=2 SC=2 AC=2<br />
cookie manipulation : S=40 SP=572 AP=572 SC=425984 AC=425984<br />
injectable parameter : S=40 SP=572 AP=572 SC=425984 AC=425984<br />
local file inclusion : S=80 SP=1144 AP=1144 SC=851968 AC=851968<br />
directory traversal : S=580 SP=8294 AP=8294 SC=6176768 AC=6176768<br />
cross-site scripting (extended patterns) : S=7 SP=7 AP=7 SC=7 AC=7<br />
blind SQL injection : S=240 SP=3432 AP=3432 SC=2555904 AC=2555904<br />
SQL injection : S=580 SP=8294 AP=8294 SC=6176768 AC=6176768<br />
SSI injection : S=60 SP=858 AP=858 SC=638976 AC=638976<br />
format string : S=40 SP=572 AP=572 SC=425984 AC=425984<br />
All tests : S=4865 SP=69237 AP=69237 SC=51544089 AC=51544089<br />
Here are the estimated number of requests in miscellaneous modes<br />
for both methods (GET and POST) :<br />
[Single / Some Pairs / All Pairs / Some Combinations / All Combinations]<br />
cross-site scripting (comprehensive test): S=840 SP=12012 AP=12012 SC=8945664 AC=8945664<br />
cross-site scripting (quick test) : S=440 SP=6292 AP=6292 SC=4685824 AC=4685824<br />
persistent XSS : S=160 SP=2288 AP=2288 SC=1703936 AC=1703936<br />
arbitrary command execution : S=880 SP=12584 AP=12584 SC=9371648 AC=9371648<br />
web code injection : S=40 SP=572 AP=572 SC=425984 AC=425984<br />
HTML injection : S=10 SP=10 AP=10 SC=10 AC=10<br />
arbitrary command execution (time based) : S=240 SP=3432 AP=3432 SC=2555904 AC=2555904<br />
script injection : S=2 SP=2 AP=2 SC=2 AC=2<br />
XML injection : S=40 SP=572 AP=572 SC=425984 AC=425984<br />
unseen parameters : S=1400 SP=20020 AP=20020 SC=14909440 AC=14909440<br />
directory traversal (write access) : S=80 SP=1144 AP=1144 SC=851968 AC=851968<br />
SQL injection (2nd order) : S=40 SP=572 AP=572 SC=425984 AC=425984<br />
on site request forgery : S=2 SP=2 AP=2 SC=2 AC=2
lind SQL injection (4 requests) : S=160 SP=2288 AP=2288 SC=1703936 AC=1703936<br />
HTTP response splitting : S=18 SP=18 AP=18 SC=18 AC=18<br />
directory traversal (extended test) : S=2040 SP=29172 AP=29172 SC=21725184 AC=21725184<br />
header injection : S=4 SP=4 AP=4 SC=4 AC=4<br />
cookie manipulation : S=80 SP=1144 AP=1144 SC=851968 AC=851968<br />
injectable parameter : S=80 SP=1144 AP=1144 SC=851968 AC=851968<br />
local file inclusion : S=160 SP=2288 AP=2288 SC=1703936 AC=1703936<br />
directory traversal : S=1160 SP=16588 AP=16588 SC=12353536 AC=12353536<br />
cross-site scripting (extended patterns) : S=14 SP=14 AP=14 SC=14 AC=14<br />
blind SQL injection : S=480 SP=6864 AP=6864 SC=5111808 AC=5111808<br />
SQL injection : S=1160 SP=16588 AP=16588 SC=12353536 AC=12353536<br />
SSI injection : S=120 SP=1716 AP=1716 SC=1277952 AC=1277952<br />
format string : S=80 SP=1144 AP=1144 SC=851968 AC=851968<br />
All tests : S=9730 SP=138474 AP=138474 SC=103088178 AC=103088178<br />
Your mode : single, GET or POST, thorough tests, Paranoid.<br />
Maximum number of requests : 4865
Security Notes found on port/service "80 / tcp / <strong>www</strong>"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"CGI Generic Tests Load Estimation (all tests)"<br />
Category<br />
"CGI abuses "<br />
Priority "Low Priority<br />
Synopsis Load estimation for web application tests.<br />
Description This script computes the maximum number of requests that would be done by the generic web tests, depending on<br />
miscellaneous options. It does not perform any test by itself.<br />
The results can be used to estimate the duration of these tests, or the complexity of additional manual tests.<br />
Note that the script does not try to compute this duration based on external factors such as the network and web<br />
servers loads.<br />
Risk factor NONE / CVSS BASE SCORE :0.0 null<br />
Plugin<br />
output<br />
Here are the estimated number of requests in miscellaneous modes<br />
for one method only (GET or POST) :<br />
[Single / Some Pairs / All Pairs / Some Combinations / All Combinations]<br />
on site request forgery : S=1 SP=1 AP=1 SC=1 AC=1<br />
SQL injection : S=580 SP=8294 AP=8294 SC=6176768 AC=6176768<br />
unseen parameters : S=700 SP=10010 AP=10010 SC=7454720 AC=7454720<br />
local file inclusion : S=80 SP=1144 AP=1144 SC=851968 AC=851968<br />
web code injection : S=20 SP=286 AP=286 SC=212992 AC=212992<br />
cookie manipulation : S=40 SP=572 AP=572 SC=425984 AC=425984<br />
XML injection : S=20 SP=286 AP=286 SC=212992 AC=212992<br />
format string : S=40 SP=572 AP=572 SC=425984 AC=425984<br />
script injection : S=1 SP=1 AP=1 SC=1 AC=1<br />
cross-site scripting (comprehensive test): S=420 SP=6006 AP=6006 SC=4472832 AC=4472832<br />
injectable parameter : S=40 SP=572 AP=572 SC=425984 AC=425984<br />
cross-site scripting (extended patterns) : S=7 SP=7 AP=7 SC=7 AC=7
directory traversal (write access) : S=40 SP=572 AP=572 SC=425984 AC=425984<br />
SSI injection : S=60 SP=858 AP=858 SC=638976 AC=638976<br />
header injection : S=2 SP=2 AP=2 SC=2 AC=2<br />
directory traversal : S=580 SP=8294 AP=8294 SC=6176768 AC=6176768<br />
HTML injection : S=5 SP=5 AP=5 SC=5 AC=5<br />
cross-site scripting (quick test) : S=220 SP=3146 AP=3146 SC=2342912 AC=2342912<br />
arbitrary command execution (time based) : S=120 SP=1716 AP=1716 SC=1277952 AC=1277952<br />
SQL injection (2nd order) : S=20 SP=286 AP=286 SC=212992 AC=212992<br />
persistent XSS : S=80 SP=1144 AP=1144 SC=851968 AC=851968<br />
directory traversal (extended test) : S=1020 SP=14586 AP=14586 SC=10862592 AC=10862592<br />
arbitrary command execution : S=440 SP=6292 AP=6292 SC=4685824 AC=4685824<br />
blind SQL injection (4 requests) : S=80 SP=1144 AP=1144 SC=851968 AC=851968<br />
HTTP response splitting : S=9 SP=9 AP=9 SC=9 AC=9<br />
blind SQL injection : S=240 SP=3432 AP=3432 SC=2555904 AC=2555904<br />
All tests : S=4865 SP=69237 AP=69237 SC=51544089 AC=51544089<br />
Here are the estimated number of requests in miscellaneous modes<br />
for both methods (GET and POST) :<br />
[Single / Some Pairs / All Pairs / Some Combinations / All Combinations]<br />
on site request forgery : S=2 SP=2 AP=2 SC=2 AC=2<br />
SQL injection : S=1160 SP=16588 AP=16588 SC=12353536 AC=12353536<br />
unseen parameters : S=1400 SP=20020 AP=20020 SC=14909440 AC=14909440<br />
local file inclusion : S=160 SP=2288 AP=2288 SC=1703936 AC=1703936<br />
web code injection : S=40 SP=572 AP=572 SC=425984 AC=425984<br />
cookie manipulation : S=80 SP=1144 AP=1144 SC=851968 AC=851968<br />
XML injection : S=40 SP=572 AP=572 SC=425984 AC=425984<br />
format string : S=80 SP=1144 AP=1144 SC=851968 AC=851968<br />
script injection : S=2 SP=2 AP=2 SC=2 AC=2<br />
cross-site scripting (comprehensive test): S=840 SP=12012 AP=12012 SC=8945664 AC=8945664<br />
injectable parameter : S=80 SP=1144 AP=1144 SC=851968 AC=851968<br />
cross-site scripting (extended patterns) : S=14 SP=14 AP=14 SC=14 AC=14<br />
directory traversal (write access) : S=80 SP=1144 AP=1144 SC=851968 AC=851968
SSI injection : S=120 SP=1716 AP=1716 SC=1277952 AC=1277952<br />
header injection : S=4 SP=4 AP=4 SC=4 AC=4<br />
directory traversal : S=1160 SP=16588 AP=16588 SC=12353536 AC=12353536<br />
HTML injection : S=10 SP=10 AP=10 SC=10 AC=10<br />
cross-site scripting (quick test) : S=440 SP=6292 AP=6292 SC=4685824 AC=4685824<br />
arbitrary command execution (time based) : S=240 SP=3432 AP=3432 SC=2555904 AC=2555904<br />
SQL injection (2nd order) : S=40 SP=572 AP=572 SC=425984 AC=425984<br />
persistent XSS : S=160 SP=2288 AP=2288 SC=1703936 AC=1703936<br />
directory traversal (extended test) : S=2040 SP=29172 AP=29172 SC=21725184 AC=21725184<br />
arbitrary command execution : S=880 SP=12584 AP=12584 SC=9371648 AC=9371648<br />
blind SQL injection (4 requests) : S=160 SP=2288 AP=2288 SC=1703936 AC=1703936<br />
HTTP response splitting : S=18 SP=18 AP=18 SC=18 AC=18<br />
blind SQL injection : S=480 SP=6864 AP=6864 SC=5111808 AC=5111808<br />
All tests : S=9730 SP=138474 AP=138474 SC=103088178 AC=103088178<br />
Your mode : single, GET or POST, thorough tests, Paranoid.<br />
Maximum number of requests : 4865
Security Notes found on port/service "25 / tcp / smtp"<br />
Status<br />
Plugin<br />
Pass (This does not affect your device compliance).<br />
"SSL/TLS EXPORT_DHE
{export flag}<br />
Addition<br />
Information<br />
CVE:<br />
http://cgi.nessus.org/cve.php3?cve=CVE-2015-4000<br />
BID : 74733 Other references { osvdb : 122331 }<br />
Solution Reconfigure the service to remove support for EXPORT_DHE cipher suites.