Apr-May-Jun 2021
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
NETWORKcomputing<br />
I N F O R M A T I O N A N D C O M M U N I C A T I O N S – N E T W O R K E D www.networkcomputing.co.uk<br />
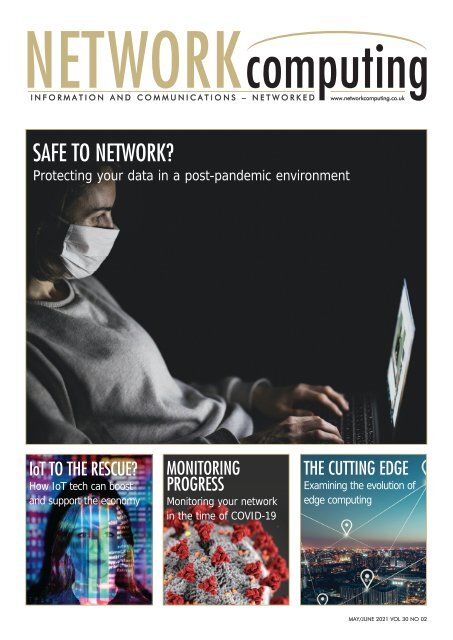
SAFE TO NETWORK?<br />
Protecting your data in a post-pandemic environment<br />
IoT TO THE RESCUE?<br />
How IoT tech can boost<br />
and support the economy<br />
MONITORING<br />
PROGRESS<br />
Monitoring your network<br />
in the time of COVID-19<br />
THE CUTTING EDGE<br />
Examining the evolution of<br />
edge computing<br />
MAY/JUNE <strong>2021</strong> VOL 30 NO 02
We will be opening nominations soon for the <strong>2021</strong> Awards. Once again, we will be asking you<br />
to tell us which products, companies and individuals have impressed you. Look out for further<br />
announcements from us over the coming weeks.<br />
ATTENTION VENDORS:<br />
There is still time - if you are quick - to ensure that your chosen solutions join the list of<br />
contenders in the BENCH TESTED PRODUCT OF THE YEAR category. You will need to book<br />
them in to be independently reviewed for Network Computing as soon as possible and ensure<br />
that the solution can be made available to a reviewer from that moment.<br />
We also want to hear about impressive work you have done to help your customers so we may<br />
consider it for the NETWORK PROJECT OF THE YEAR.<br />
Finally, there will also be opportunities to be involved as a sponsor.<br />
To discuss any of the above , please contact dave.bonner@btc.co.uk<br />
WWW.NETWORKCOMPUTINGAWARDS.CO.UK
COMMENT<br />
COMMENT<br />
NEW THREATS IN THE PIPELINE<br />
At the time of going to press the US fuel pipeline operated by Colonial Pipeline has been<br />
taken offline due to a ransomware attack by the hacking group DarkSide. The cyberattack<br />
was so significant (Colonial has never taken its entire network offline before) that it<br />
was addressed directly by President Biden, who said that his administration "will be pursuing a<br />
global effort of ransomware attacks by transnational criminals who often use global moneylaundering<br />
networks to carry them out." The pipeline supplies millions of gallons of fuel a day,<br />
and it appears that the hacking group stole around 100 gigabytes of data before encrpyting<br />
Colonial's network. It's still unclear whether any of the ransom has actually been paid, but<br />
DarkSide subsequently posted a press release on their website stating that "Our goal is to make<br />
money, and not creating problems for society." So that's alright then...<br />
Commenting on the attack Andy Norton, European Cyber Risk Officer at Armis said: "These<br />
'Cyber Physical' attacks are a big deal, because they demonstrate just how fragile the provision<br />
of critical services are into society. A few weeks ago a water treatment plant was compromised<br />
leading to the potential for poisoning of the water. Now, 45% of the US oil energy provision has<br />
been switched off to the East coast. Prolonged shortages in critical services lead to civil unrest,<br />
economic pressures, and a general lack of confidence in public administration. What is equally<br />
troubling is the lack of progress critical infrastructure providers seem to be making in being<br />
resilient to these attacks."<br />
For some this attack is another high profile indication of how cybercrime has both flourished<br />
and expanded its attack vectors during the pandemic. "We used to separate cybercrime versus<br />
physical world crime and view the impact differently. Even legislation is more documented for<br />
physical crime, compared to cybercrime where we are now slowly maturing," said Calvin Gan,<br />
Senior Manager with F-Secure's Tactical Defense Unit. "However, if there's one thing the pandemic<br />
has changed, it's the acceleration rate of cybercrime. With convergence of technologies being<br />
connected through the Internet, we now have a concrete view of how cybercrime impact has<br />
spread not only across the Internet but also to the physical world. Attacks such as ransomware<br />
on Critical National Infrastructure is just one example of how cybercrime can affect people<br />
directly or indirectly. With emergency laws needed to be passed to respond to cyber attacks, this<br />
is a clear sign that there is now increased interest by attackers to target these industries."<br />
To this end you'll find a number of articles in this issue that explore how we can best safeguard<br />
our data: from the importance of cloud backups to the value of prioritising data security over<br />
network security, and the ramifications of potential real-world disasters such as the recent fire at<br />
the OVHCloud data centre in Strasbourg. Back in 2017 The Economist famously stated that<br />
"The world's most valuable resource is no longer oil, but data." Is your business prepared for the<br />
threats coming down the pipeline? NC<br />
REVIEWS:<br />
Dave Mitchell<br />
DEPUTY EDITOR: Mark Lyward<br />
(netcomputing@btc.co.uk)<br />
PRODUCTION: Abby Penn<br />
(abby.penn@btc.co.uk)<br />
DESIGN: Ian Collis<br />
(ian.collis@btc.co.uk<br />
SALES:<br />
David Bonner<br />
(david.bonner@btc.co.uk)<br />
Julie Cornish<br />
(julie.cornish@btc.co.uk)<br />
SUBSCRIPTIONS: Christina Willis<br />
(christina.willis@btc.co.uk)<br />
PUBLISHER: John Jageurs<br />
(john.jageurs@btc.co.uk)<br />
Published by Barrow & Thompkins<br />
Connexion Ltd (BTC)<br />
35 Station Square,<br />
Petts Wood, Kent, BR5 1LZ<br />
Tel: +44 (0)1689 616 000<br />
Fax: +44 (0)1689 82 66 22<br />
SUBSCRIPTIONS:<br />
UK £35/year, £60/two years,<br />
£80/three years;<br />
Europe:<br />
£48/year, £85/two years £127/three years;<br />
ROW:<br />
£62/year, £115/two years, £168/three years;<br />
Subscribers get SPECIAL OFFERS — see subscriptions<br />
advertisement; Single copies of<br />
Network Computing can be bought for £8;<br />
(including postage & packing).<br />
© <strong>2021</strong> Barrow & Thompkins<br />
Connexion Ltd.<br />
All rights reserved.<br />
No part of the magazine may be<br />
reproduced without prior consent, in<br />
writing, from the publisher.<br />
GET FUTURE COPIES FREE<br />
BY REGISTERING ONLINE AT<br />
WWW.NETWORKCOMPUTING.CO.UK/REGISTER<br />
WWW.NETWORKCOMPUTING.CO.UK @NCMagAndAwards<br />
MAY/JUNE <strong>2021</strong> NETWORKcomputing 03
CONTENTS<br />
CONTENTS<br />
M A Y / J U N E 2 0 2 1<br />
A CRITICAL TEST....................8<br />
The NetAlly LinkSprinter® Pocket Network<br />
Tester has enabled a non-profit healthcare<br />
organisation to provide assured connectivity<br />
into its critical patient bedside monitoring<br />
VLAN for COVID-19 patients<br />
COMMENT.....................................3<br />
New threats in the pipeline<br />
INDUSTRY NEWS.............................6<br />
The latest networking news<br />
ARTICLES<br />
REDEFINING ENTERPRISE<br />
NETWORKS.......................................9<br />
By Alan Hayward at SEH Technology<br />
5G: THE YEAR AHEAD.......................10<br />
By Jeremy Spencer at BT Enterprise<br />
DEVICE MANAGEMENT IN A<br />
CORPORATE ENVIRONMENT...........12<br />
By Nadav Avni at Radix Technology<br />
ENSURING SD-WAN CONVERSION<br />
SUCCESS........................................14<br />
By Sanjay Radia at NETSCOUT<br />
DATA PROTECTION.............16<br />
Our data protection feature considers the<br />
growing importance of cloud backup for SMBs<br />
and the value of prioritising data security over<br />
that of the network. Will our data protection<br />
policies need to adapt post-pandemic?<br />
MONITORING PROGRESS...27<br />
If 2020 taught us anything it's that network<br />
monitoring has become more important than<br />
ever, writes Mark Towler at Progress<br />
EDGE AND IoT........................22<br />
Is Network-as-a-Service set to redefine<br />
edge computing, and how will the growth<br />
of IoT and edge devices impact businesses<br />
moving forward? Read our feature in this<br />
issue to find out<br />
THE CONNECTIVITY<br />
CONUNDRUM......................30<br />
Lee Wade of Exponential-e explains why<br />
connectivity is the final piece in the home<br />
working productivity puzzle<br />
THE CLOUD BACKUP OPPORTUNITY<br />
FOR MSPS.........................................16<br />
By Carl Oliver at Giacom<br />
WHY THE SECURITY INDUSTRY IS<br />
PROTECTING THE WRONG THING...18<br />
By Paul German at Certes Networks<br />
DATA PROTECTION IN A POST-<br />
PANDEMIC ENVIRONMENT............20<br />
By Adam Strange at Titus<br />
NOW’S THE TIME FOR NAAS............22<br />
By Simon Wilson at Aruba UK&I<br />
IoT TO THE RESCUE?......................24<br />
By Nick Sacke at Comms365<br />
CLOSER TO THE EDGE...................26<br />
By Simon Michie at Pulsant<br />
THE VISIBLE BENEFITS OF<br />
AUTOMATION..............................28<br />
By Adrian Rowley at Gigamon<br />
THE DIGITAL TRANSFORMATION<br />
DILEMMA......................................29<br />
By The Workforce Institute at UKG<br />
THE WEAK LINK IN THE CHAIN.......32<br />
By Steph Charbonneau at HelpSystems<br />
IS YOUR DATA FIREPROOF?...........34<br />
By Stephen Young at AssureStor<br />
PRODUCT REVIEW<br />
WHATSUP GOLD <strong>2021</strong>......................15<br />
EXAGRID TIERED BACKUP STORAGE....21<br />
04 NETWORKcomputing MAY/JUNE <strong>2021</strong> @NCMagAndAwards<br />
WWW.NETWORKCOMPUTING.CO.UK
INDUSTRYNEWS<br />
NEWS NEWS NEWS<br />
NEWS NEWSNEWS<br />
NEWS<br />
NEWS<br />
Palo Alto forms new cybersecurity consulting group<br />
Palo Alto Networks is establishing a new cybersecurity<br />
consulting group to help enterprises respond to emerging<br />
threats as they navigate an increase in costly, crippling<br />
cyberattacks. The newly expanded Unit 42 combines formerly<br />
Crypsis security consultants, who respond to 1,300+ incidents a<br />
year, with the company's veteran Unit 42 threat research team,<br />
which has been fighting emerging cyberthreats since 2014.<br />
Together, they will help organisations tackle the most complex<br />
cyberthreats, from ransomware to state-sponsored espionage.<br />
Wendi Whitmore,<br />
Palo Alto Networks<br />
Since it was founded in 2014, Unit 42 has produced more<br />
than 650 reports and regularly partners with governments<br />
around the globe to fight cybercrime. "Our increasing reliance<br />
on technology has turned cybersecurity into an existential<br />
matter," said Wendi Whitmore, senior vice president of cyber<br />
consulting and threat intelligence at Palo Alto Networks. "We<br />
wake up every day focused on collecting and analysing the<br />
most up-to-date threat intelligence and applying our analysis to<br />
respond to cyberattacks."<br />
Velociraptor adds bite to Rapid7<br />
Rapid7 has acquired Velociraptor, a leading open-source<br />
technology and community used for endpoint monitoring,<br />
digital forensics, and incident response. Velociraptor was<br />
developed for digital forensics and incident response (DFIR)<br />
professionals who need a powerful and efficient way to hunt for<br />
and monitor malicious activities across endpoints.<br />
Velociraptor's community-driven approach allows the collective<br />
wisdom of the DFIR community to be gathered in one place and<br />
made accessible to others. Velociraptor is unique in that it allows<br />
custom detections, collections and analyses capabilities to be<br />
written in queries, rather than code. Those queries can then<br />
easily be shared, strengthening the knowledge of the community<br />
and allowing teams to hunt for new threats more quickly.<br />
Network security issues prolong pandemic downtime<br />
More than a year after the mass shift to remote working, over<br />
half (54%) of organisations are still suffering downtime and<br />
disruption as a result of network security issues, according to new<br />
data from the Neustar International Security Council (NISC).<br />
Surveying security professionals across EMEA and the US, 61% of<br />
respondents reported suffering either significant or moderate<br />
downtime or disruption in the first six months of the pandemic,<br />
caused by employees having to work from home. However the<br />
majority of respondents (89%) agreed that the challenges posed<br />
by the pandemic have strengthened their organisation's network<br />
security against potential future attacks. In addition, 79% believed<br />
that the situation over the last year has triggered an improvement<br />
to their corporate VPNs to make them more secure.<br />
"The challenge with using VPNs to allow approximately 95% of<br />
the workforce to log on remotely is that cybercriminals<br />
understand that the hardening of connectivity from a denial-ofservice<br />
point of view hasn't always been done," Joffe continued.<br />
"A DDoS attack that is encapsulated in a VPN packet will only<br />
be revealed when the packet reaches the VPN server and is<br />
opened up – by then, it's too late. For this reason, VPNs will<br />
continue to be the target of choice, it's down to the organisation<br />
itself to make them as secure as possible."<br />
iTrinegy receives Queen's Award for Enterprise<br />
itrinegy has been honoured with a Queen's Award for<br />
Enterprise for International Trade. Stevenage-based iTrinegy is<br />
one of a few organisations to be recognised with the annual<br />
Queen's Award for Enterprise which is the UK's most prestigious<br />
award for business success and presented by Her Majesty The<br />
Queen on the advice of the Prime Minister. iTrinegy was set up in<br />
2006 and its Software Defined Test Networks (Network<br />
Emulation) technology provides organisations with a way to<br />
create real-world network conditions in which to analyse, predict<br />
and verify application performance before deploying<br />
applications into potentially challenging network environments.<br />
"We are thrilled to have been chosen for this award," said<br />
Graham Wood, Director at iTrinegy. "Although iTrinegy has been<br />
widely recognised for our technical achievements and is the<br />
proud recipient of many awards over the years, we are a<br />
business and can only be successful if our technology is valued<br />
by our customers resulting in sales growth. The Queen's Award<br />
for Enterprise: International Trade <strong>2021</strong> is a fantastic<br />
endorsement for iTrinegy as a successful business as well as a<br />
great technology company."<br />
06 NETWORKcomputing MAY/JUNE <strong>2021</strong> @NCMagAndAwards<br />
WWW.NETWORKCOMPUTING.CO.UK
INDUSTRYNEWS<br />
Consortium established to test IoT network security<br />
Acisco-led consortium of partners will demonstrate how<br />
artificial intelligence and blockchain can robustly secure<br />
Internet of Things (IoT) networks through i-Trace, a partgovernment<br />
funded, co-innovation project that will serve as a<br />
step forward in the digital transformation of national<br />
infrastructure. Integrated smart infrastructure solutions<br />
company, Costain, has joined the i-Trace consortium to<br />
conduct real-world cybersecurity trials in construction machine<br />
telematics and connected sites sensing and monitoring.<br />
Using real-world data from live Costain project sites, the<br />
project will demonstrate how the unique i-Trace solution brings<br />
together two complementary technologies to secure critical<br />
data. Firstly, using machine learning systems to detect security<br />
threats on IoT devices via the network. Secondly, using<br />
distributed ledger technology (DLT) to guarantee that the data<br />
generated by these IoT devices is tamperproof and immutable,<br />
wherever it is in the network. These technologies will be<br />
deployed across Costain's networks to secure M2M telematics,<br />
connected IoT sensors and monitoring equipment. The<br />
consortium is comprised of experts from Cisco, BT, Senseon,<br />
the Warwick Manufacturing Group (WMG) at the University of<br />
Warwick, and Costain. i-Trace is part-government funded<br />
through Innovate UK and the UKRI's Strategic Priorities Fund.<br />
UK Department for Education loses nearly 200 devices<br />
The Department for Education (DFE) has seen nearly 200<br />
devices including laptops and mobile phones lost or stolen<br />
over the last two years, according to official figures. The data,<br />
which was obtained under a Freedom of Information (FOI) Act<br />
inquiry by the Parliament Street think tank has revealed the<br />
number of lost and stolen gadgets since 2019. Overseen by<br />
Secretary of State for Education Gavin Williamson, the DFE is<br />
responsible for child protection, education, apprenticeships,<br />
and wider skills in England, and has seen remote working surge<br />
due to the Covid-19 pandemic. Of the total 196 devices<br />
reported missing, mobile phones were the most common, with<br />
145 missing in total since 2019, 22 of which were Blackberries.<br />
In <strong>Apr</strong>il 2020 the Department for Education launched a free<br />
online learning platform to help people pick up digital and<br />
cyber skills while in lockdown. The DFE has also dispatched<br />
1.29 million laptops and tablets as part of a scheme to provide<br />
over 1.3 million devices to disadvantaged and vulnerable<br />
children and young people with devices and connectivity to<br />
access remote learning during the 2020/21 academic year.<br />
Edward Blake, Area Vice President, Absolute Software UK&I<br />
comments: "For under-pressure IT teams, managing and<br />
ensuring each and every device is cyber secure and accounted<br />
for is no easy task. Therefore, it is more critical than ever to<br />
have a permanent digital connection to every endpoint, as well<br />
as the ability to lock, freeze or wipe the device if it is at risk of<br />
being compromised. Young people must be able to learn<br />
remotely without risk of cyber attack."<br />
Fluke Networks launches LinkIQ Cable+Network tester<br />
Fluke Networks has launched the LinkIQ Cable+Network<br />
tester, which combines switch diagnostics with state-of-theart<br />
cable measurement technology to enable installers, system<br />
integrators and network support professionals to easily<br />
troubleshoot network cabling and/or connect Power over<br />
Ethernet (PoE) devices to the network. The product provides<br />
simple pass/fail test reports using the company's innovative<br />
LinkWare PC Cable Test Management Software. It can also<br />
verify the performance of switches, including those that provide<br />
Power over Ethernet.<br />
The LinkIQ is based on a single-test approach that<br />
automatically provides the appropriate measurements based on<br />
what is at the other end of the cable. For an open cable, it shows<br />
the length and pairing. If this is terminated with the supplied<br />
remote, the test result shows the maximum data rate the cable<br />
can support – up to 10 Gb/s. However, if the cable is connected<br />
to a switch port, LinkIQ will show the name of the switch plus the<br />
port name, VLAN, speed, and duplex. If PoE is advertised, it will<br />
display the power and class (up to 90 W or Class 8) and then<br />
load the switch to verify the power can be delivered.<br />
The LinkIQ uses LinkWare PC, Fluke Networks' reporting<br />
software, which is the industry's de facto standard reporting<br />
solution. The simplest way to manage report data is with a free<br />
copy of LinkWare. The results from a wide variety of Fluke<br />
products can be stored and accessed, or PDF reports may be<br />
generated using the software.<br />
NEWS NEWSNEWS<br />
NEWS<br />
NEWS NEWS NEWS NEWS NEWS<br />
NEWS<br />
WWW.NETWORKCOMPUTING.CO.UK @NCMagAndAwards<br />
MAY/JUNE <strong>2021</strong> NETWORKcomputing 07
CASESTUDY<br />
COVID IMPACTS REQUIRE ACCURATE NETWORK TESTING<br />
THE NETALLY LINKSPRINTER POCKET NETWORK TESTER HAS ENABLED A NON-PROFIT HEALTHCARE<br />
ORGANISATION TO PROVIDE ASSURED CONNECTIVITY INTO ITS CRITICAL PATIENT BEDSIDE MONITORING<br />
VLAN FOR COVID-19 PATIENTS<br />
the critical slot/port and VLAN<br />
configuration<br />
DHCP and DNS network services<br />
Connectivity to user-defined internal or<br />
external resources<br />
WWith the COVID-19 pandemic,<br />
healthcare systems around the world<br />
needed to rapidly expand capacity to<br />
effectively treat a large number of critical care<br />
patients. With this possible exponential growth<br />
in the numbers of patients needing treatment,<br />
this healthcare provider embarked on a plan<br />
to convert standard patient wards in their<br />
hospitals to ICU-level (intensive care unit)<br />
emergency overflow wards.<br />
While many departments rely on bedside<br />
telemetry systems that can utilise Wi-Fi<br />
networks for connectivity, COVID-19 surge<br />
patients require full bedside monitors (and the<br />
respirator systems needed for treatment of<br />
COVID-19) that rely on wired network<br />
connections to meet the standard for ICU-level<br />
care. That link must provide assured<br />
connectivity into the critical patient bedside<br />
monitoring VLAN.<br />
The provider's biomedical device technicians<br />
needed the ability to effectively and quickly<br />
survey the available network connections in the<br />
wards that were being converted. This involved<br />
identifying which switch/slot/port served each<br />
jack in the ward that would be utilised for the<br />
bedside systems, and creating a document of<br />
the current configuration which would be<br />
supplied to their network operations team so<br />
that the proper port reassignment work could<br />
be completed.<br />
The problem was that they had no quick and<br />
easy way to identify the port assignments.<br />
Manual methods, such as utilising a<br />
cumbersome laptop, hand-writing the<br />
information (including the room, wall-plate,<br />
and jack numbers), and collating that data for<br />
the report to the network team was time<br />
consuming and open to error. In the delivery of<br />
patient care, errors are simply unacceptable.<br />
SOLUTION<br />
Their biomed technician team turned to the<br />
NetAlly LinkSprinter® Pocket Network Tester<br />
and the secure Link-Live cloud service. As a<br />
small device, LinkSprinter is easily carried to<br />
and around the wards. One-button<br />
automation ensures that every test is executed<br />
consistently, across the entire team of<br />
technicians, and a comprehensive connectivity<br />
test is completed in less than 10 seconds. This<br />
test returns data about:<br />
Power over Ethernet (PoE) if present<br />
Ethernet link speed and duplex<br />
Connected switch information, including<br />
The technicians can verify the progress of the<br />
testing with the unit's color-coded test icons,<br />
and view detailed test data by connecting their<br />
phone to the embedded Wi-Fi radio. The test<br />
result is annotated with the patient room<br />
number, and jack identification. The<br />
LinkSprinter was able to assess the hospital's<br />
network port configurations quickly and<br />
accurately, automatically uploading results into<br />
the Link-Live Cloud Service.<br />
Best of all, the test results are automatically<br />
uploaded to the secure Link-Live cloud portal,<br />
where centralised job supervisors can easily<br />
see and manage the progress of the testing,<br />
and quickly create accurate documentation for<br />
the change order needed by network<br />
operations. Once the port assignments have<br />
been changed, LinkSprinter provides the team<br />
with a fast way to verify that the port is up,<br />
assigned to the critical VLAN, with connectivity<br />
to essential services.<br />
RESULTS<br />
"With the segmentation of the biomedical<br />
equipment on these special VLANs, we have to<br />
be very precise on connectivity," explains their<br />
Medical Device Integration Manager. "Using<br />
LinkSprinter with the data upload and reporting<br />
in Link-Live eliminates the margin of error,<br />
which is critical in this environment. The time<br />
savings is huge, and the data quality prevents<br />
mistakes - we love it!" NC<br />
For more information on the NetAlly<br />
LinkSprinter® Pocket Tester visit:<br />
www.netally.com/products/linksprinter/<br />
08 NETWORKcomputing MAY/JUNE <strong>2021</strong> @NCMagAndAwards<br />
WWW.NETWORKCOMPUTING.CO.UK
OPINION<br />
REDEFINING ENTERPRISE NETWORKS<br />
IT'S NOW TIME TO TAKE THE LESSONS LEARNT IN THE PANDEMIC<br />
AND LOOK FORWARD TO NEW ENTERPRISE NETWORK TRENDS,<br />
ACCORDING TO ALAN HAYWARD, SALES & MARKETING MANAGER<br />
AT SEH TECHNOLOGY<br />
The coronavirus has changed the way we<br />
work forever. With most employees now<br />
working from home, we have seen the<br />
rise of online workspaces. In this new digital<br />
age, technologies have been vital in improving<br />
communication and collaboration, to ensure<br />
workers can complete their work as effectively<br />
and efficiently as they would have in the office<br />
environment. These include cloud-based<br />
communication and data solutions which<br />
allow businesses to run from anywhere in the<br />
world, with ease.<br />
Many companies have been maximising the<br />
benefits of using cloud-based solutions as they<br />
create secure environments to easily access<br />
and share data, as well as facilitating the tools<br />
needed to communicate with colleagues in<br />
real time. As a result, employees have been<br />
able to better adapt to working remotely using<br />
devices like laptops or desktops at home.<br />
The recent Future Forum Research from<br />
Slack found that out of 4,700 knowledge<br />
workers surveyed, the majority never want to<br />
return to their old ways of working. In fact,<br />
only 12% want to return to full-time office<br />
work and a staggering 72% want their<br />
employers to implement a hybrid remoteoffice<br />
model moving forward. This puts more<br />
pressure on companies to meet the increasing<br />
'work-from-anywhere' expectations, and it's<br />
likely that we will see more businesses<br />
investing in resources to safely simplify and<br />
automate network complexity.<br />
INCREASING SECURITY MEASURES<br />
Many traditional network infrastructures were<br />
not created to support rapidly developing<br />
digital ecosystems, and can no longer provide<br />
the levels of security and control required. With<br />
traffic no longer from one central company<br />
data centre, but multiple cloud-based<br />
locations and virtual workspaces, it has<br />
become increasingly difficult to manage.<br />
Businesses should take a step back to consider<br />
the emerging security risks of working from<br />
home, in terms of systems access, internal<br />
network infrastructures and bandwidth. One of<br />
the easiest ways that organisations can secure<br />
data as it moves from internal systems to<br />
external devices is to deploy a VPN. This<br />
provides an additional layer of security by<br />
hiding the user's IP address and encrypting<br />
data transfers in transit.<br />
It's also important to make sure up-to-date<br />
security protection is installed and active on all<br />
devices used by employees at home and in the<br />
office. This includes virus checkers, firewalls<br />
and device encryption. Businesses may also<br />
consider running an audit on employee<br />
passcodes, to ensure that all are reset and<br />
redefined in line with the company's security<br />
policy. Alphanumeric codes and two-factor<br />
authentication are recommended as this<br />
applies the strongest possible security<br />
protection across all employee devices.<br />
INVESTING IN A REMOTE ACCESS<br />
SOLUTIONS<br />
When employees are working from the<br />
office, it's easy for them to access the<br />
company's network. However, with remote<br />
working becoming a more permanent<br />
solution, employees will continue to require<br />
access to resources from home, meaning<br />
many companies are considering tools that<br />
offer scalability and flexibility as we move<br />
into <strong>2021</strong>.<br />
Dongle servers will easily allow employees to<br />
access their work from home and share USB<br />
dongle devices via the network. Not only can<br />
dongles be used via LAN connections, but also<br />
via VPN, VLAN, and the Internet. This ensures<br />
employees can stay productive whether they<br />
are working from home or in the office. With<br />
an encrypted point-to-point connection<br />
between the user and the dongle server,<br />
businesses can dynamically assign which<br />
employee is authorised to access each dongle,<br />
ensuring everyone can retrieve everything they<br />
need. Users can also request access as soon<br />
as a license becomes available, and once the<br />
software has been used by that individual, it<br />
will be securely relocated to the next in line.<br />
FUTURE OF ENTERPRISE NETWORKS<br />
The COVID-19 pandemic has changed the<br />
way that businesses operate, and its effects will<br />
last for the foreseeable future. At the start of<br />
the coronavirus, many companies were left<br />
grappling to adapt to remote working<br />
environments and unprecedented<br />
circumstances. While the new normal is still on<br />
the horizon, it's time to look to the future and<br />
adjust to new enterprise network trends.<br />
The biggest ongoing challenge will be<br />
facilitating the demand for remote working,<br />
as most employees have now become<br />
accustomed to the flexibility and convenience<br />
that it brings. We can expect to see a rise in<br />
hybrid working, as COVID-19 has clearly<br />
demonstrated that work can happen<br />
anywhere when it's digitised and connected.<br />
Hybrid environments will support flexible<br />
arrangements, replace dedicated offices and<br />
allow resources to be deployed when<br />
necessary. As a result, it's important for<br />
businesses to make sure that they have the<br />
right software and hardware tools available<br />
to support their enterprise networks, in<br />
addition to solid security measures and<br />
remote access capabilities. NC<br />
WWW.NETWORKCOMPUTING.CO.UK @NCMagAndAwards<br />
MAY/JUNE <strong>2021</strong> NETWORKcomputing 09
OPINION<br />
5G: THE YEAR AHEAD<br />
JEREMY SPENCER, GENERAL MANAGER OF CORPORATE<br />
PROPOSITIONS, BT ENTERPRISE, EXPLAINS HOW 5G CAN BETTER<br />
ENABLE THE DIGITAL TRANSFORMATION JOURNEY<br />
For the past decade, 5G, as with many<br />
emerging technologies, has often fallen<br />
into the trap of being seen as more of a<br />
buzzword than a technology with true business<br />
impact. In fact, recent research conducted by<br />
BT highlights that many business leaders are<br />
still unclear on how the technology can be best<br />
leveraged, and importantly, how it can tie into<br />
and support core organisational and<br />
commercial goals. Of the 1,000 UK business<br />
leaders we surveyed, only 11% of respondents<br />
said they are currently using 5G.<br />
But as the rollout of the 5G network continues<br />
across the UK this year, there will be no doubt<br />
that when adopted and implemented in the<br />
right way, 5G will bring enormous and exciting<br />
potential to save time, boost productivity,<br />
unlock innovation and contribute to a<br />
sustainable business future. The main<br />
challenge for businesses over the coming year<br />
will be for leaders to make the link between 5G<br />
adoption and their strategic objectives.<br />
Outside of enterprise, 5G adoption is steadily<br />
on the rise. Recent research from CCS Insight<br />
suggests that by next year, almost two-thirds of<br />
new phones in <strong>2021</strong> will be 5G-enabled. This<br />
is relevant, as it is widespread consumer<br />
acceptance and adoption which will lay the<br />
foundations for the same uptake in an<br />
enterprise setting. Over the past couple of<br />
years, 5G testbeds have been emerging across<br />
the country as businesses across all sectors start<br />
to experiment with the technology to test its<br />
potential and seek an early adopter advantage<br />
over their competitors. This year we can expect<br />
to see this trial and testing phase evolve into<br />
widespread commercial deployment of the<br />
technology, as businesses from all sectors look<br />
to capitalise on the benefits that ultrafast,<br />
uninterrupted connectivity can bring them.<br />
5G IN MANUFACTURING<br />
The work we're doing with the Worcestershire<br />
5G Testbed (W5G) is a fantastic example of<br />
how the technology can be used, and what it<br />
can power. We're working to accelerate the<br />
testbed's vision of smart manufacturing -<br />
delivered through the UK's first live 5G factory<br />
installation. By creating a smart factory where<br />
machines can learn and adapt to changes on<br />
the factory floor as they happen, productivity<br />
will be boosted through instant, autonomous<br />
decisions which will benefit the production line.<br />
The insight gleaned from the W5G will be used<br />
to stimulate innovation across the<br />
manufacturing sector in the region and beyond.<br />
SMART DEVICES TOP THE AGENDA<br />
With the introduction of 5G-enabled smart<br />
devices, such as collision detection sensors,<br />
the emerging technology will provide an<br />
almost immediate benefit to the<br />
manufacturing industry, but other sectors will<br />
be able to learn and benefit from these<br />
testbeds too. As commercial adoption of 5G<br />
increases, retailers can look to leverage the<br />
emerging technology to provide a more<br />
personalised experience for consumers via<br />
mobile applications and potentially even<br />
smart glasses.<br />
Experiential shopping is a major draw for<br />
consumers, particularly as brick-and-mortar<br />
stores find themselves under pressure from<br />
declining footfall amidst Covid-19. Adoption<br />
of 5G-connected smart glasses could one day<br />
offer consumers the ability to view items such<br />
as clothing without having to try them on.<br />
APPLYING 5G TO HEALTHCARE<br />
Once widespread adoption levels have been<br />
reached, 5G is going to revolutionise the<br />
healthcare industry. We are beginning to see this<br />
take place already. Last year, BT demonstrated a<br />
powerful example of how 5G can transform<br />
healthcare and emergency services, with the<br />
UK's first remote-controlled ultrasound scan<br />
over a public 5G network. In practice, this<br />
means that an ultrasound could be performed<br />
by a paramedic inside a moving ambulance.<br />
Remote, real-time diagnostics is a key trend<br />
we can expect to see develop in <strong>2021</strong>, as 5G<br />
adoption increases, and consumers become<br />
more and more familiar and comfortable with<br />
remote interaction, a familiarity that will extend<br />
to critical sectors such as healthcare.<br />
However, there is still much work to be done.<br />
Excluding VOIP, nearly half (48%) of our survey<br />
respondents said they aren't using any of the<br />
emerging technologies we listed - including 5G<br />
- with 38% saying they don't have a plan to<br />
adopt any of them in the next five years. The<br />
healthcare sector is under more pressure than<br />
ever, and technology should play a key role in<br />
making its work more efficient and effective.<br />
CHANGE BEGINS AT THE TOP<br />
<strong>2021</strong> will see 5G shift from a boardroom<br />
buzzword to the subject of a more meaningful<br />
conversation around how it can help achieve<br />
business priorities. Covid-19 has ushered in a<br />
huge wave of digital transformation, as<br />
businesses race to meet rapidly shifting<br />
customer and employee expectations. If<br />
businesses want to keep up with the times, and<br />
continue to deliver value, adoption of emerging<br />
technologies, particularly 5G, will help them on<br />
their journey. NC<br />
10 NETWORKcomputing MAY/JUNE <strong>2021</strong> @NCMagAndAwards<br />
WWW.NETWORKCOMPUTING.CO.UK
One Platform for<br />
Digital Business<br />
• Process<br />
• Content<br />
• Governance<br />
Modern Architecture<br />
• Developer-friendly<br />
• Open<br />
• Cloud-ready<br />
Faster Time to Value<br />
• Deploy<br />
• Adopt<br />
• Build<br />
Learn more at alfresco.com | Contact us at info@alfresco.com<br />
Alfresco EMEA: +44 (0) 1628 876 500 | Alfresco Americas: +1 888 317 3395<br />
Alfresco Asia Pacific: +61 2 8607 8539
OPINION<br />
OPTIMISING AND SECURING DEVICE<br />
MANAGEMENT IN A CORPORATE<br />
ENVIRONMENT<br />
IS THERE A DEVICE MANAGEMENT SOLUTION POWERFUL<br />
ENOUGH TO SUPPORT YOUR CORPORATE NEEDS? NADAV<br />
AVNI AT RADIX TECHNOLOGY OFFERS A GUIDE<br />
The proliferation of digital devices used<br />
in every organisation has only grown in<br />
the past few years. Digital devices<br />
provide greater flexibility and mobility for<br />
companies, but they also create more of a<br />
burden on IT teams and administrators to<br />
manage it all. Mobile devices have more<br />
capabilities than ever before - and they're<br />
accessing more sensitive and property data,<br />
too. In fact, 42% of enterprises now<br />
consider themselves mobile-first. As more<br />
employees moved to remote work, it<br />
underscored the need for greater security. At<br />
the same time, it made device management<br />
more difficult for IT teams.<br />
Mobile Device Management (MDM) allows<br />
the remote management of every device in<br />
an organisation's fleet from a centralised<br />
platform that's accessible from anywhere. It<br />
gives complete control of devices and<br />
provides a way to manage settings, policies,<br />
and security in one place.<br />
THE IMPORTANCE OF MDM<br />
Nearly three-quarters (74%) of CFOs said<br />
they expect to keep some employees<br />
working from home and shift others to<br />
remote work permanently. The need to<br />
manage devices remotely isn't going away<br />
even when the pandemic is over. Even when<br />
employees are working on-site, they still use<br />
mobile devices.<br />
Smartphones, laptops, tablets, and other<br />
single-use devices all need management.<br />
Workers may be in different locations than<br />
IT administrators. MDM allows efficient<br />
remote management of every device in the<br />
fleet regardless of the administrators' and<br />
employees' location.<br />
Some of the core functions of mobile<br />
device management include:<br />
Managing setting and policies<br />
Monitoring app usage and performance<br />
Updating equipment, software, and<br />
applications<br />
Monitoring health of equipment<br />
Monitoring equipment location, status,<br />
and activity<br />
Remote device control for diagnosis and<br />
troubleshooting<br />
Encryption of email and files<br />
Segregation for work and personal<br />
device use, creating separate and<br />
secured environments for work data.<br />
MORE THAN SECURITY<br />
Most MDM solutions focus mainly on<br />
Enterprise Mobility Management (EMM) and<br />
the security layer. A fully-featured<br />
MDM/EMM system adds another layer that<br />
provides comprehensive device<br />
management. This gives IT administrators<br />
the ability to manage nearly every type of<br />
device running on every major operating<br />
system from one platform.<br />
Flexible solutions can be installed as an<br />
on-premises solution or in the cloud for<br />
reduced latency, redundancy, and end-toend<br />
security with encryption. When you're<br />
running a mobile device management<br />
platform in the cloud, the service provider<br />
automatically applies updates and<br />
patches. Hence, it's one more thing you<br />
won't need to worry about. It also makes it<br />
easier for administrators to access the<br />
platform remotely.<br />
MANAGING COMPLIANCE<br />
Mobile devices increase the possibility of<br />
data breaches or leaks. Besides the<br />
possibility of cyber-attacks, a staggering<br />
number of laptops and smartphones are lost<br />
or stolen. On average, 70 million devices<br />
are lost or stolen annually, with less than<br />
10% ever being recovered. This is an<br />
exceptionally big problem for managing<br />
12 NETWORKcomputing MAY/JUNE <strong>2021</strong> @NCMagAndAwards<br />
WWW.NETWORKCOMPUTING.CO.UK
OPINION<br />
compliance in regulated industries, such as<br />
healthcare, financial, and other businesses.<br />
A robust MDM/EMM software provides<br />
end-to-end security and encryption to protect<br />
data. Devices can be tracked with geofence<br />
and anti-theft filters. If a device leaves an<br />
authorised area, it triggers a warning note to<br />
administrators, who can remotely lock the<br />
device or wipe the data. MDM/EMM apps<br />
with advanced security features also create<br />
snapshots on the fly even while devices are<br />
running to make restoring or recovery from<br />
virus attacks or system crashes easier.<br />
Besides automated data audits, these<br />
functions help organisations comply with<br />
even the most stringent compliance<br />
regulations, including GDPR, the EU's<br />
General Data Privacy Regulations. It also<br />
acts as an essential element in complying<br />
with HIPAA, SOX, FISMA, PCI DSS, and<br />
other regulations.<br />
MORE EFFICIENT DEPLOYMENT<br />
Devices can be deployed in batches with<br />
preset configuration, settings, and corporate<br />
policies. By automating enrollment tasks, the<br />
devices can be up and running in your<br />
environment without user intervention. It all<br />
happens in the background the first time a<br />
device is fired up and connected to a network.<br />
Besides the platform's native and priority<br />
enrollment modules, devices can also be<br />
deployed using a range of platforms. This<br />
provides an extremely friendly out-of-box<br />
experience (OOBE) for employees without<br />
tying up IT teams for hours to configure<br />
new devices.<br />
TOOLS FOR ALL STAKEHOLDERS<br />
Modern MDM/EMM tools also provide<br />
sophisticated reporting tools to all<br />
stakeholders in the organisation. IT teams<br />
can manage the entire device fleet<br />
holistically or drill down to any individual<br />
device. Managers can look at adoption and<br />
usage rates. CFOs can look at the ROI.<br />
Each automated report can be customised to<br />
show what each group of stakeholders needs<br />
to make data-driven business decisions.<br />
TOOLS FOR OEMS AND VENDORS<br />
APIs are usually available for solution<br />
developers. That means the platform can be<br />
embedded in device firmware and integrated<br />
at the factory level for OEMs. System-level<br />
integration is also possible, so mobile device<br />
management software can be pre-installed<br />
and ready to go upon device delivery.<br />
MANAGING USE AND CONTENT<br />
Not every employee needs every functionality<br />
on every device. MDM software allows you<br />
to apply single-app or multi-app kiosk mode.<br />
This creates an encapsulated environment<br />
with access to the functionality and apps you<br />
determine. It creates a consistent look and<br />
feel for devices and control device elements,<br />
such as locking down external ports or<br />
preventing unauthorised interaction of noncompany<br />
installed apps. You can limit<br />
external internet use or enable/disable Wi-Fi<br />
or Bluetooth connections.<br />
DEVICE MANAGEMENT SOLUTION<br />
One of the biggest barriers to continued<br />
remote work is the lack of technology and<br />
infrastructure to allow remote employees to<br />
work productively. Therefore, implementing<br />
a modular and flexible MDM/EMM solution<br />
is key to successfully and efficiently<br />
managing your devices. Look for one that<br />
not only accomplishes the points listed<br />
above but one that also allows<br />
customisation for just about any use case.<br />
Take control of your entire mobile device<br />
fleet and gain the ability to finally manage<br />
nearly every aspect with ease. NC<br />
WWW.NETWORKCOMPUTING.CO.UK @NCMagAndAwards<br />
MAY/JUNE <strong>2021</strong> NETWORKcomputing 13
OPINION<br />
ENSURING SD-WAN CONVERSION SUCCESS<br />
SANJAY RADIA, SALES ENGINEERING MANAGER AT NETSCOUT,<br />
EXPLAINS HOW TO DEPLOY AN SD-WAN WITHOUT INTERRUPTING<br />
BUSINESS CONTINUITY<br />
It has been a year since lockdown<br />
restrictions forced businesses to shift their<br />
entire workforces to remote working<br />
overnight. Some businesses were more<br />
prepared than others, having already enabled<br />
a level of remote working or having expanded<br />
to multiple locations, both of which require<br />
remote-office network changes. However, very<br />
few businesses were prepared for the sheer<br />
scale of the changes and demands that workfrom-home<br />
orders put on the network.<br />
To ensure the continued operation of<br />
businesses, overcoming these challenges and<br />
assuring reliable business service access for<br />
at-home workers became the key theme of<br />
2020. Many businesses opted for softwaredefined<br />
WAN (SD-WAN) solutions as a more<br />
cost effective and performant solution than<br />
traditional hardware-based WAN operations<br />
that were holding them back. However,<br />
although SD-WAN can reduce complexity,<br />
making the transition to SD-WAN is by no<br />
means a simple one.<br />
ASSURING SD-WAN CONVERSION<br />
SUCCESS<br />
A seamless transition to working from home<br />
involves the use and interaction of many<br />
different technologies to keep business<br />
running as usual. These include expanded<br />
virtual private networks (VPN) and virtual<br />
desktop infrastructure (VDI) deployments, as<br />
well as Voice Over IP (VoIP) services. However,<br />
SD-WAN services do not always support these<br />
critical services.<br />
The first step to converting from a<br />
hardware-based WAN to SD-WAN solution<br />
is to identify the solution that will work best<br />
for the requirements of the business. The aim<br />
is generally for this process to be as lighttouch<br />
as possible to ensure a smooth<br />
deployment with minimal hands-on<br />
involvement. With this in mind, it is common<br />
for businesses to look for an SD-WAN<br />
solution that already packages up the<br />
offerings of multiple technology vendors,<br />
such as VoIP services and Virtual Network<br />
Function (VNF) vendor solutions.<br />
However, despite all best intentions and<br />
research, it is possible for issues to arise as IT<br />
teams start to test the solution as part of the<br />
pre-deployment process. For example, the<br />
VoIP technology may not perform reliably over<br />
SD-WAN and the testing might produce false<br />
negatives. As we've all experienced over the<br />
past year, VoIP is critical for businesses to<br />
function remotely, so an issue arising at this<br />
stage could be devastating for a company,<br />
especially considering the time and money<br />
that will have already been invested in the SD-<br />
WAN conversion.<br />
VIRTUAL VISIBILITY TO THE RESCUE<br />
The scenario described above is a worst-case<br />
example, the good news is that this example<br />
was missing the vital component in SD-WAN<br />
conversion: visibility. With visibility this situation<br />
would not have occurred because the<br />
company's IT team would have been able to<br />
troubleshoot and resolve the VoIP over SD-<br />
WAN testing issues.<br />
Virtual visibility can identify the causes of<br />
problems that IT are not able to spot<br />
themselves. For instance, with the above<br />
example, visibility would reveal that the false<br />
negatives occurring during the testing were<br />
related to the IP address being used for the<br />
VoIP scripting data.<br />
Another problem that can arise in the<br />
process of conversion is that the business<br />
applications may be sensitive to data transfer<br />
processes on SD-WAN. This is where unified<br />
communications (UC) analytics can provide<br />
real-time monitoring of the issue and inform<br />
the fine-tuning that the IT team need to make.<br />
Virtual visibility and unified communications<br />
(UC) analytics are vital for troubleshooting<br />
and monitoring the conversion process. With<br />
these tools, IT teams can resolve issues in the<br />
virtual testing environment and fix them before<br />
the roll out process.<br />
Converting to SD-WAN is advisable for the<br />
many businesses adapting to the 'new normal'<br />
as well as ensuring future proofing. But only<br />
virtual visibility and UC analytics will assure<br />
conversion success and delivery of<br />
uninterrupted business services. NC<br />
14 NETWORKcomputing MAY/JUNE <strong>2021</strong> @NCMagAndAwards<br />
WWW.NETWORKCOMPUTING.CO.UK
PRODUCTREVIEW<br />
Progress Software<br />
WhatsUp Gold <strong>2021</strong><br />
PRODUCT REVIEW<br />
PRODUCT<br />
REVIEWPRODUCT RE<br />
Progress Software's WhatsUp Gold (WUG)<br />
is a great network monitoring choice for<br />
SMBs and enterprises and this latest<br />
version aims to make it even more appealing.<br />
WUG <strong>2021</strong> introduces enhanced log<br />
management and has the ability to collect<br />
Windows Event Logs plus Syslog events and<br />
present all the information in its main web<br />
console for easy analysis.<br />
WhatsUp Gold <strong>2021</strong> integrates tightly with the<br />
Elasticsearch analytics engine and provides<br />
extensive log search, filtering and export<br />
facilities. You can choose what events you want<br />
to collect, link events, conditions or trends with<br />
alerts and actions and create customisable<br />
dashboards in the main console for at-a-glance<br />
log status views.<br />
The simple points-based system employed by<br />
WUG <strong>2021</strong> takes all the guesswork out of<br />
licensing costs. Each device, regardless of the<br />
number of network interfaces, CPUs and so on<br />
is considered one element and costs one point<br />
while each monitored application or log<br />
management source costs ten points.<br />
Two versions are available with the Premium<br />
edition providing core functions such as<br />
discovery, interactive mapping, alerting and<br />
reporting plus cloud, device, network, storage<br />
and wireless monitoring. Optional add-on<br />
modules are available for virtualisation and<br />
application monitoring, network traffic analysis<br />
(NTA) and log management, which are all<br />
included in the Total Plus version.<br />
Installing WUG <strong>2021</strong> on a Windows Server<br />
2019 host was simple and the routine also<br />
loaded SQL Server 2017 Express and IIS. You<br />
don't have to do anything for your first network<br />
discovery as it runs this for on your local IP<br />
subnet and populates its dashboard with all<br />
network devices.<br />
Elasticsearch installation is included in the<br />
initial routine and you can choose the basic<br />
OSS version, which only accepts connections<br />
from the WUG <strong>2021</strong> host. If you want the<br />
version with authentication and encryption, you'll<br />
need to source and install this separately and<br />
point the WUG host at it.<br />
The WhatsUp Gold console is easy to use as it<br />
presents four menu options in its upper ribbon bar.<br />
You can swiftly run discoveries, view all network<br />
devices, pull up a wealth of analysis dashboards<br />
and access all WUG and add-on module settings.<br />
Analysis dashboards are a great feature as you<br />
can create multiple custom views, add columns<br />
and choose what you want to see. Anything<br />
WUG is capable of monitoring can be included<br />
making it easy to create NOC (network<br />
operations center) views for your support teams.<br />
Adding Windows and Syslog log data sources<br />
is a breeze as you choose monitored devices<br />
from the log settings page. For Windows Event<br />
Log sources, you can gather application, system<br />
and security logs and decide whether you want<br />
critical, error and warning levels as well.<br />
WhatsUp Gold's viewer window reveals all the<br />
log action over the selected time period and its<br />
search facility quickly finds a log of interest.<br />
Advanced filters can be used to fine-tune the<br />
information further by applying sets of log type<br />
criteria and you can add alert thresholds to<br />
provide notifications of unusual activity.<br />
Log management isn't the only new feature, as<br />
WUG's inbound REST API performance monitor<br />
has been enhanced with an outbound version<br />
allowing you to send information to WUG from<br />
third-party apps such as Microsoft 365 and<br />
Salesforce. Reporting also gets a boost with the<br />
improved rendering engine notably improving<br />
its appearance, and there's also a new<br />
application performance monitor (APM) profile<br />
for MySQL 8.0.<br />
WhatsUpGold <strong>2021</strong> is a sophisticated network<br />
monitoring solution that delivers an impressive<br />
range of tools integrated seamlessly into a single<br />
console. The simplified licensing schemes make<br />
it very affordable for SMBs, it's scalable enough<br />
for enterprises and the new log management<br />
features add even more versatility. NC<br />
Product: WhatsUp Gold <strong>2021</strong><br />
Supplier: Progress Software Ltd<br />
Tel: +44 (0)1344 360444<br />
Web site: www.whatsupgold.com<br />
Price: Premium - 25 devices from $2,740<br />
WWW.NETWORKCOMPUTING.CO.UK @NCMagAndAwards<br />
MAY/JUNE <strong>2021</strong> NETWORKcomputing 15
OPINION<br />
THE CLOUD BACKUP OPPORTUNITY FOR MSPs<br />
CARL OLIVER, PRODUCT MANAGER, GIACOM EXPLAINS WHY<br />
CLOUD BACKUP IS INCREASINGLY IMPORTANT FOR SMBS,<br />
AND WHERE THE OPPORTUNITY LIES FOR MANAGED SERVICE<br />
PROVIDERS<br />
Depending on who you talk to,<br />
digitalisation across the globe has<br />
been accelerated by around five to<br />
eight years because of Covid-19.<br />
Transitioning towards the use of cloud-based<br />
technologies has formed a key component of<br />
this transformation. But, as organisations<br />
shift from using on-premise solutions to the<br />
cloud, many will not have considered that<br />
data - despite being located in the cloud -<br />
still needs to be backed up. This is<br />
particularly true of the SMB market.<br />
The channel, therefore, needs to educate<br />
and support SMB organisations as they<br />
develop and deploy their cloud strategies. But,<br />
it also means that ITCs need to work with their<br />
CSP partners to capitalise on the potential<br />
recurring revenue generating opportunities<br />
that backup provisioning can offer.<br />
ON-PREMISE BACK-UP SOLUTIONS<br />
AREN'T FAIL SAFE<br />
It won't come as a surprise to the IT channel<br />
that protecting data and backing it up is<br />
critical. But, what is the difference between<br />
backing up data on-premise compared with<br />
cloud backup solutions?<br />
As you can imagine, an on-premises backup<br />
solution stores data securely on officebased<br />
hard drives. In principle, this is a<br />
feasible option, but what if a natural disaster<br />
occurs such as a pandemic, flood or fire?<br />
Accessing data becomes problematic and<br />
depending on the situation, data could be<br />
lost forever. A case in point is this last year,<br />
as pandemic work-from-home restrictions<br />
prevented many people from working in<br />
offices, making the idea of accessing office<br />
technology and IT backups difficult. So,<br />
many businesses turned to the cloud for<br />
support. Which, rightly, highlighted the need<br />
for cloud data security.<br />
HOW SECURE IS DATA WHEN<br />
STORED IN THE CLOUD?<br />
There's a common misconception that, just<br />
because you shift your applications and<br />
workloads into the cloud, all of your data is<br />
completely secure. While the cloud offers<br />
many benefits, including the availability of<br />
data, it doesn't entirely protect organisations<br />
from data loss or corruption alone.<br />
For instance, a recent study by SkyKick<br />
found that 32 percent of companies using<br />
cloud had experienced data loss in the cloud<br />
across numerous threats. It points out that 64<br />
percent of this data loss was accidental and<br />
that 20 percent was down to malicious<br />
intent. Worse yet, the average cost of this<br />
data loss without a backup solution in place<br />
equates to almost $4,000 - not counting the<br />
potential reputational damage and fines<br />
from regulators. So, while cloud has enabled<br />
businesses to evolve and thrive, especially<br />
through the current pandemic, it's clear that<br />
data stored in the cloud still needs to be<br />
backed up via a dedicated method.<br />
This is why it is important for organisations<br />
to factor cloud backup solutions into their<br />
long-term cloud and data protection<br />
strategies. They are crucial and help address<br />
this growing risk of data loss that takes<br />
place, be that through accidental or<br />
malicious means.<br />
ADVANTAGES OF CLOUD BACKUP<br />
SOLUTIONS<br />
Using cloud backup solutions offers<br />
organisations a host of benefits too. Many<br />
modern backup tools include enhanced<br />
security features and the ability to scale<br />
backups as required. They also generally<br />
offer quicker recovery times if and when<br />
backed up data is needed. Further, better<br />
security protocols, encryption, software<br />
patches and updates mean that there are<br />
more effective security options for ITCs to<br />
provide to their end user customers in the<br />
cloud too.<br />
16 NETWORKcomputing MAY/JUNE <strong>2021</strong> @NCMagAndAwards<br />
WWW.NETWORKCOMPUTING.CO.UK
OPINION<br />
Moreover, by using the cloud,<br />
organisations can scale more easily too.<br />
They have the option and capability to move<br />
their data efficiently and quickly across the<br />
world. However, as with all technology there<br />
are security risks to consider, which ITCs<br />
need to advise clients on.<br />
This is where the relationship between CSP<br />
and ITC is important. Modern and effective<br />
CSPs work with their ITCs to support them<br />
with cloud deployment consultancy and<br />
execution to customers. This usually<br />
includes providing collaborative insights<br />
about managing data privacy, security and<br />
infrastructure maintenance. Equally, this is<br />
an area where the SMB market requires<br />
more support - since 37 percent of SMBs,<br />
according to Forrester, are not adopting<br />
cloud due to security concerns.<br />
SUPPORTING SMBs WITH CLOUD<br />
BACKUP IN A COVID WORLD<br />
Through the pandemic, many organisations<br />
turned to remote working to maintain<br />
productivity. Many of these applications are<br />
cloud-based; and for some, this meant that<br />
their IT estate had to evolve. There was an<br />
explosion in the use of collaboration<br />
technologies across the world, and this is<br />
set to continue. Research from the Cloud<br />
Industry Forum indicates that 88 percent of<br />
organisations expect their adoption of<br />
cloud services to increase in the next 12<br />
months.<br />
This trend towards cloud application<br />
adoption amplifies the need to move away<br />
from depending on on-premise backups<br />
towards relying on cloud backup solutions<br />
instead. Further, since technology operates<br />
in an 'always on' state of play, businesses<br />
can't afford to wait for someone to<br />
physically attend an on-premise site to<br />
perform maintenance, especially during a<br />
pandemic.<br />
Aside from this, it is crucial to note that<br />
during any crisis malevolent actors will seek<br />
to cause mayhem and exploit vulnerable<br />
situations. For instance, according to the<br />
Office of National Statistics cybercrime<br />
greatly increased during the last year -<br />
added to that, not a week goes by either<br />
without hearing about a high-profile<br />
cybersecurity incident. For instance,<br />
recently, North Korean hackers attacked<br />
Pfizer and Serco experienced a cyber-attack<br />
related to NHS Test and Trace.<br />
Clearly, Covid-19 has created the perfect<br />
situation for cybercriminals to exploit. With<br />
many IT teams stretched - either by work at<br />
home restrictions, cloud/digital<br />
transformation projects or cyber-attacks -<br />
they have their work cut out for them. The<br />
pressure they face is unprecedented, and<br />
emphasises the importance of putting in<br />
place robust data recovery and business<br />
continuity strategies to support their<br />
businesses. Evidently, there is a significant<br />
opportunity for the channel to step in and<br />
provide advisory and execution support and<br />
services to SMB customers.<br />
CONCLUSION<br />
Even though cloud solves many problems<br />
for organisations, it does come with data<br />
protection challenges. One answer to this<br />
problem involves using dedicated cloud<br />
backup solutions to protect data. The other<br />
answer lies in market education about how<br />
best to secure cloud applications and data.<br />
Within this scenario, CSPs and ITCs must<br />
work together to educate the market -<br />
especially SMBs - about how to secure and<br />
back up data effectively. By doing this, ITCs<br />
can take advantage of their CSP partner's<br />
knowledge - positioning themselves as trusted<br />
advisors to clients - and also take advantage<br />
of the available lucrative recurring revenue<br />
generating opportunity. NC<br />
WWW.NETWORKCOMPUTING.CO.UK @NCMagAndAwards<br />
MAY/JUNE <strong>2021</strong> NETWORKcomputing 17
FEATUREDATA PROTECTION<br />
THREE REASONS WHY THE SECURITY INDUSTRY IS PROTECTING THE<br />
WRONG THING<br />
WHY IS IT THAT THE SECURITY INDUSTRY TALKS ABOUT NETWORK SECURITY, BUT NOT DATA<br />
BREACHES? IT'S CLEAR THAT SOMETHING NEEDS TO CHANGE, AND ACCORDING TO PAUL GERMAN,<br />
CEO, CERTES NETWORKS, THE CHANGE IS SIMPLE<br />
For too long now, organisations have<br />
been focusing on protecting their<br />
network, when in fact they should<br />
have been protecting their data. Paul<br />
outlines three reasons why the security<br />
industry has been protecting the wrong<br />
thing and what they can do to secure their<br />
data as we move into <strong>2021</strong>.<br />
REASON ONE: THEY'RE CALLED<br />
DATA BREACHES, NOT NETWORK<br />
BREACHES, FOR A REASON<br />
Looking back on some of the biggest data<br />
breaches the world has ever seen, it's clear<br />
that cyber hackers always seem to be one<br />
step ahead of organisations that seemingly<br />
have sufficient protection and technology<br />
in place. From the Adobe data breach way<br />
back in 2013 that resulted in 153 million<br />
user records stolen, to the Equifax data<br />
breach in 2017 that exposed the data of<br />
147.9 million consumers, the lengthy<br />
Marriott International data breach that<br />
compromised the data from 500 million<br />
customers over four years, to the recent<br />
SolarWinds data breach at the end of<br />
2020, over time it's looked like no<br />
organisation is exempt from the<br />
devastating consequences of a cyber hack.<br />
When these breaches hit the media<br />
headlines, they're called 'data breaches',<br />
18 NETWORKcomputing MAY/JUNE <strong>2021</strong> @NCMagAndAwards<br />
WWW.NETWORKCOMPUTING.CO.UK
FEATUREDATA PROTECTION<br />
yet the default approach to data security<br />
for all these organisations has been<br />
focused on protecting the network - to little<br />
effect. In many cases, these data breaches<br />
have seen malicious actors infiltrate the<br />
organisation's network, sometimes for long<br />
periods of time, and then have their pick of<br />
the data that's left unprotected right in front<br />
of them.<br />
So what's the rationale behind<br />
maintaining this flawed approach to data<br />
protection? The fact is that current<br />
approaches mean it is simply not possible<br />
to implement the level of security that<br />
sensitive data demands while it is in transit<br />
without compromising network<br />
performance. Facing an either/or decision,<br />
companies have blindly followed the same<br />
old path of attempting to secure the<br />
network perimeter, and hoping that they<br />
won't suffer the same fate as so many<br />
before them.<br />
However, consider separating data<br />
security from the network through an<br />
encryption-based information assurance<br />
overlay. By doing so organisations can<br />
seamlessly ensure that even when<br />
malicious actors enter the network, the<br />
data will still be unattainable and<br />
unreadable, keeping the integrity,<br />
authentication and confidentiality of the<br />
data intact without impacting overall<br />
performance of the underlying<br />
infrastructure.<br />
REASON TWO: REGULATIONS AND<br />
COMPLIANCE REVOLVE AROUND<br />
DATA<br />
Back in 2018, GDPR caused many<br />
headaches for businesses across the world.<br />
There are numerous data regulations<br />
businesses must adhere to, but GDPR in<br />
particular highlighted how important it is<br />
for organisations to protect their sensitive<br />
data. In the case of GDPR, organisations<br />
are not fined based on a network breach;<br />
in fact, if a cyber hacker were to enter an<br />
organisation's network but not compromise<br />
any data, the organisation wouldn't actually<br />
be in breach of the regulation at all.<br />
GDPR, alongside many other regulations<br />
such as HIPAA, CCPA, CJIS or PCI-DSS, is<br />
concerned with protecting data, whether it's<br />
financial data, healthcare data or law<br />
enforcement data. The point is: it all<br />
revolves around data, but the way in which<br />
data needs to be protected will depend on<br />
business intent. With new regulations<br />
constantly coming into play and<br />
compliance another huge concern for<br />
organisations as we continue into <strong>2021</strong>,<br />
protecting data has never been more<br />
important, but by developing an intentbased<br />
policy, organisations can ensure<br />
their data is being treated and secured in a<br />
way that will meet business goals and<br />
deliver provable and measurable<br />
outcomes, rather than with a one-size-fitsall<br />
approach.<br />
REASON THREE: NETWORK<br />
BREACHES ARE INEVITABLE, BUT<br />
DATA BREACHES ARE NOT<br />
Data has become extremely valuable<br />
across all business sectors and the increase<br />
in digitisation means that there is now<br />
more data available to waiting malicious<br />
actors. From credit card information to<br />
highly sensitive data held about law<br />
enforcement cases and crime scenes, to<br />
data such as passport numbers and social<br />
ID numbers in the US, organisations are<br />
responsible for keeping this data safe for<br />
their customers, but many are falling short<br />
of this duty.<br />
With the high price tag that data now has,<br />
doing everything possible to keep data<br />
secure seems like an obvious task for every<br />
CISO and IT Manager to prioritise, yet the<br />
constant stream of data breaches shows<br />
this isn't the case.<br />
But what can organisations do to keep this<br />
data safe? To start with, a change in<br />
mindset is needed to truly put data at the<br />
forefront of all cybersecurity decisions and<br />
investments. Essential questions a CISO<br />
must ask include: Will this solution protect<br />
my data as it travels throughout the<br />
network? Will this technology enable data<br />
to be kept safe, even if hackers are able to<br />
infiltrate the network? Will this strategy<br />
ensure the business is compliant with<br />
regulations regarding data security, and that<br />
if a network breach does occur, the business<br />
won't risk facing any fines? The answer to<br />
these questions must be yes in order for any<br />
CISO to trust that their data is safe and that<br />
their IT security policy is effective.<br />
Furthermore, with such a vast volume of<br />
data to protect, real-time monitoring of the<br />
organisation's information assurance<br />
posture is essential in order to react to an<br />
issue, and remediate it, at lightning speed.<br />
With real-time, contextual meta-data, any<br />
non-compliant traffic flows or policy<br />
changes can be quickly detected on a<br />
continuous basis to ensure the security<br />
posture is not affected, so that even if an<br />
inevitable network breach occurs, a data<br />
breach does not follow in its wake.<br />
TRUSTING INFORMATION<br />
ASSURANCE<br />
An information assurance approach that<br />
removes the misdirected focus on<br />
protecting an organisation's network and<br />
instead looks at protecting data, is the only<br />
way that the security industry can move<br />
away from the damaging data breaches of<br />
the past. There really is no reason for these<br />
data breaches to continue hitting the<br />
media headlines; the technology needed to<br />
keep data secure is ready and waiting for<br />
the industry to take advantage of.<br />
In the same way that no one would leave<br />
their finest jewellery on display in the<br />
kitchen window, or leave their passport<br />
out for the postman to see, organisations<br />
must safeguard their most valuable asset<br />
and protect themselves and their<br />
reputation from suffering the same fate as<br />
all those other organisations that have not<br />
protected their data. NC<br />
WWW.NETWORKCOMPUTING.CO.UK @NCMagAndAwards<br />
MAY/JUNE <strong>2021</strong> NETWORKcomputing 19
FEATUREDATA PROTECTION<br />
DATA PROTECTION IN A POST-PANDEMIC<br />
ENVIRONMENT<br />
ADAM STRANGE, A DATA CLASSIFICATION SPECIALIST AT TITUS,<br />
IDENTIFIES THE KEY PROCESSES AND TECHNOLOGIES BUSINESS<br />
MUST ADOPT IN THE WAKE OF COVID-19<br />
The rapid rise in remote working under<br />
COVID-19 delivered far-reaching<br />
changes in how we do business, with<br />
significant implications for CISOs, Compliance<br />
and Data Governance Officers. With<br />
accessibility, bandwidth, data volumes and<br />
usage demands surging under the pandemic,<br />
the challenge to keep data safe, whilst<br />
facilitating access and usability for multiple<br />
external user groups, became a core concern<br />
for data leaders. Now, as data from multiple<br />
and often external sources continues to grow in<br />
volume, issues around data management,<br />
control and protection are a priority concern<br />
for business.<br />
The forward-thinking companies, with<br />
technology development strategies already in<br />
place, were able to quickly adapt under the<br />
pandemic and act on the clear business<br />
opportunity to "reinvent" data protection and<br />
flexible user access. But the organisations that<br />
maintained a fixed mindset on data protection<br />
are today finding it more difficult to recover and<br />
harder to provide their users with the tools<br />
required to do their jobs safely.<br />
SUPPORTING REMOTE WORKING<br />
With the expectation that post-pandemic<br />
remote working will almost double from prepandemic<br />
levels, maintaining a centrally driven<br />
robust data governance strategy that prioritises<br />
data security and regulatory requirements<br />
whilst ensuring appropriate and safe access to<br />
information, whenever and wherever needed,<br />
is a must. Businesses must recognise the data<br />
protection lessons learnt and move beyond<br />
short-term security compromises to a futureproofed<br />
data governance protocol that is<br />
technology and user-centric. As a starting<br />
point, data protection must adapt to the new<br />
workplace environment. It is likely that in the<br />
post-pandemic environment, employees will<br />
split their working hours between home and<br />
office permanently. So organisations must<br />
look at the impact of high-volume remote<br />
working and what this means to their existing<br />
security controls.<br />
A reinforcement of corporate policies around<br />
data creation and linked protection facilities,<br />
such as Data Loss Prevention (DLP) technology,<br />
will be critical to facilitate large remote<br />
workforces, to reduce accidental failings and<br />
to ensure that data transfer is confined to<br />
authorised recipients only. By identifying the<br />
true value and protection requirements of<br />
data, organisations will be able to make<br />
intelligent decisions on how to safely handle it.<br />
All data must be classified so it can be<br />
managed and handled appropriately, with<br />
robust classification facilities.<br />
AUTOMATING DATA CLASSIFICATION<br />
Businesses that adapt best to the post-pandemic<br />
era will use automation, data-driven digital<br />
access technologies and cloud to effect<br />
improved operations and efficiencies. All<br />
organisations will need to focus on the resultsdriven<br />
benefits that new and extended working<br />
practices can provide and enabling safe user<br />
and data access must be at the heart of these<br />
strategies. Automation will help improve<br />
processing efficiency and reduce the burden on<br />
frontline security and data management staff. To<br />
drive integration and automation as quickly as<br />
possible, data classification tools will not only<br />
help organisations to protect their data by<br />
applying appropriate security labels but will also<br />
help educate users to understand how to treat<br />
different types of data with different levels of<br />
classification and sensitivity.<br />
ESTABLISH A DATA SECURITY CULTURE<br />
Businesses must apply and enforce PII data<br />
protection rules to safeguard personal data.<br />
Data leaders must be able to identify it,<br />
classify its sensitivity and level of threat were it<br />
to be lost in any way, apply acceptable usage<br />
policies and appropriate levels of protection.<br />
Establishing a PII culture must be gradual and<br />
based on buy-in and defined responsibilities<br />
that are recognised and accepted from the<br />
top down.<br />
Given employees play such a vital role in<br />
ensuring that business maintains a strong data<br />
privacy posture, the ability to work with<br />
stakeholders and users to understand data<br />
protection requirements and policies is key.<br />
Security and data protection education must be<br />
conducted company-wide and must exist at a<br />
level that is workable and sustainable. Regular<br />
security awareness training and a companywide<br />
inclusive security culture within the firm will<br />
ensure that data security becomes a part of<br />
everyday working practice, embedded into all<br />
actions and the very heart of the business.<br />
A robust data protection protocol is critical<br />
for all organisations, and will particularly be<br />
the case as we move beyond COVID-19.<br />
Delivering optimal operational efficiencies,<br />
data management and data classification<br />
provision under post-pandemic budget<br />
constraints will be an ongoing business-critical<br />
challenge. Data leaders must be selective and<br />
identify the combination of technologies,<br />
processes and people investments that will<br />
deliver the greatest security controls to meet<br />
new productivity targets, to extend and support<br />
remote-working strategies and to adequately<br />
support the ever-increasing volumes of data,<br />
now and into the future. NC<br />
20 NETWORKcomputing MAY/JUNE <strong>2021</strong> @NCMagAndAwards<br />
WWW.NETWORKCOMPUTING.CO.UK
PRODUCTREVIEW<br />
ExaGrid Tiered<br />
Backup Storage -<br />
Retention Time-Lock<br />
for Ransomware<br />
Recovery<br />
PRODUCT REVIEW<br />
PRODUCT<br />
REVIEWPRODUCT RE<br />
Ransomware attacks are proving to be<br />
extremely profitable for hackers, and<br />
organisations that think their backups<br />
provide sufficient protection could be in for a<br />
nasty surprise. These attacks are constantly<br />
evolving and the latest threats specifically<br />
target backup applications with the aim of<br />
deleting all backups before the primary<br />
storage encryption process is triggered.<br />
ExaGrid's Tiered Backup Storage offers a<br />
unique approach that protects backups from<br />
ransomware and provides fast recovery services<br />
in the event of an attack. Included with all<br />
ExaGrid EX appliances, the Retention Time-<br />
Lock feature takes advantage of their two-tier<br />
architecture to place an air gap between the<br />
network-facing tier and non-network-facing tier.<br />
ExaGrid's Tiered Backup Storage uses<br />
patented Landing Zone and Adaptive<br />
Deduplication features to provide fast<br />
backups and restores without the<br />
performance impact of data deduplication<br />
from which traditional data reduction<br />
solutions suffer. It's highly scalable as a site<br />
supports up to 32 EX appliances (a 2.7PB full<br />
backup) and each is a complete system with<br />
its own storage, CPU, memory and<br />
networking, so compute power and network<br />
bandwidth increase in step with capacity.<br />
Data received from the backup application is<br />
written directly to a disk cache in<br />
undeduplicated format. As backups complete,<br />
the data in the Landing Zone is 'tiered' and<br />
written to a separate long-term retention<br />
repository where it is compressed and<br />
deduplicated.<br />
ExaGrid's Retention Time-Lock feature comes<br />
into play by delaying delete requests to the<br />
deduplicated long-term retention data in the<br />
offline repository. Delete requests will be<br />
carried out in the repository, but only once the<br />
time-lock period has expired, so that there is<br />
no impact on the desired long-term retention<br />
in the repository. It's more cost-effective than<br />
solutions that use additional hardware as it<br />
only requires about 10% of an existing storage<br />
repository to be allocated to it. The Retention<br />
Time-Lock period defaults to 10 days but can<br />
be as long as 30 days, and this delayed<br />
delete setting is separate from the system's<br />
backup retention policy that can be any<br />
number of days, weeks, months or years.<br />
ExaGrid's scale-out sites are managed from a<br />
central console which provides colour-coded<br />
status views of site capacities and free space<br />
plus Landing Zone and retention repository<br />
utilisation. To configure a site Retention Time-<br />
Lock period you simply click on its icon in the<br />
main dashboard and enter the value in days.<br />
Even the Retention Time-Lock setting is<br />
protected as changes to this must be verified<br />
by a user with the ExaGrid Security Officer<br />
role. Any attempts to change it result in a<br />
request being sent to this user where it appears<br />
in their console awaiting approval.<br />
If an attack is detected, the ExaGrid system<br />
issues warnings and allows administrators to<br />
respond immediately by suspending all further<br />
share access and taking them offline. And if<br />
the attack does succeed in encrypting data,<br />
ExaGrid has immutable data objects that are<br />
not modified or overwritten so all previous<br />
retention does not change.<br />
It's a simple process to recover from a<br />
ransomware attack as you browse the<br />
retention repository for the latest unencrypted<br />
backup. Selecting a date and time enables all<br />
previous backups from that period and<br />
initiating a recovery makes the selected pointin-time<br />
backup available to the application for<br />
subsequent restoration.<br />
Ransomware threats are becoming more<br />
devious, but ExaGrid's Tiered Backup Storage<br />
and its innovative Retention Time-Lock feature<br />
deliver essential protection with a secure, airgapped<br />
retention repository, delayed deletes<br />
and immutable data objects. It ensures critical<br />
backups are safe from malicious deletion and<br />
even if an attack does succeed in encrypting<br />
primary data, ExaGrid's highly efficient<br />
recovery services will have you up and running<br />
in no time. NC<br />
Product: Retention Time-Lock for<br />
Ransomware Recovery<br />
Supplier: ExaGrid<br />
Web site: www.exagrid.com<br />
Tel: +44 (0) 1189 497 051<br />
WWW.NETWORKCOMPUTING.CO.UK @NCMagAndAwards<br />
MAY/JUNE <strong>2021</strong> NETWORKcomputing 21
FEATUREEDGE<br />
NOW'S THE TIME FOR NAAS<br />
NETWORK-AS-A-SERVICE (NAAS) IS POISED TO RESHAPE<br />
EXPERIENCES AT THE EDGE, ACCORDING TO SIMON WILSON,<br />
CTO AT ARUBA UK&I<br />
Flexible consumption services for storage<br />
and compute power seem to be<br />
mainstream today, with customers taking<br />
"as a Service" approaches more often than not -<br />
and it's easy to see why. Even prior to the<br />
COVID-19 pandemic, organisations were<br />
pushed to address fluctuating markets and<br />
economic uncertainty.<br />
CAPEX planning has long been known to<br />
leave organisations with long product lifecycles<br />
and an inability to pivot quickly, locking<br />
businesses into costly spending patterns and<br />
damaging their capacity to meet today's shifting<br />
business dynamics. Enter OPEX, the<br />
subscription approach that brings flexibility and<br />
fluidity to operating expenses and on-demand<br />
payments, underscoring business agility.<br />
While flexible financing is one of the core<br />
reasons for the uptake in as-a-service models,<br />
there are a number of other factors deemed as,<br />
if not more, important than cost alone. We now<br />
see that NaaS is gaining traction, with the latest<br />
IDC 'IT Procurement Trends and Consumption<br />
Models' Survey, reporting that flexible<br />
consumption models for enterprise networking<br />
software and hardware continue to gain favour<br />
in the market.<br />
LEVERAGING IT STAFF TO SPEND MORE<br />
TIME ON WHAT MATTERS<br />
Within IDC's report, the desire to reduce IT staff<br />
workloads came out as one of the top factors<br />
driving as-a-service deployments - this is<br />
particularly relevant for networks. More<br />
frequently than not, IT teams find their days<br />
filled with requests to address network<br />
problems. Resources, time and expenses are<br />
focused on troubleshooting, finding the root<br />
cause, and remediating the latest network event<br />
or breach, leaving IT teams unable to focus on<br />
more critical and strategic tasks.<br />
The rollout of subscription offerings across key<br />
departments, including deployment and<br />
decommissioning, means that IT staff can spend<br />
more time on complex, value-adding tasks for<br />
the business. This means truly optimising staff<br />
with the right tools to improve business and<br />
drive new outcomes.<br />
Network-as-a-Service includes data analytics,<br />
expanded telemetry, artificial intelligence and<br />
automation, which come together to deliver<br />
critical efficiency gains in network operations.<br />
With network management increasingly<br />
complex in the new age of remote working,<br />
replacing manual interventions with advanced<br />
automation and analytics also provides<br />
increased visibility from a security perspective<br />
from usage through to bandwidth.<br />
HAVING AN EXTRA PAIR OF EYES ON<br />
SECURITY ISSUES<br />
As the pandemic has pushed networks to<br />
support remote workforces over the past year,<br />
increased security remains a top priority for<br />
businesses. With NaaS, most providers can rely<br />
on the security of the entire voice and data<br />
network so that all transactions, applications,<br />
and data are kept safe and secure. The number<br />
of IoT devices in particular are growing at an<br />
exponential rate, especially during this new<br />
working paradigm. Control and visibility issues<br />
are heightening risks and leaving networks more<br />
vulnerable than ever to potential breaches. But if<br />
IT staff are spending their time troubleshooting,<br />
they won't be able to protect their network<br />
properly and detect threats in real-time.<br />
NaaS deployment can provide an extra pair of<br />
hands for IT staff by running the most up-todate<br />
versions of security software and ensuring<br />
that hotfixes are installed as soon as they<br />
become available. For small businesses in<br />
particular, the ability to scale up and down as<br />
needed, depending on networking capacity, has<br />
been helpful as business needs have changed.<br />
MEETING EXPECTATIONS AT THE EDGE<br />
As organisations increase their reliance on<br />
cloud services, they have also needed their<br />
networks to extend beyond the perimeter of the<br />
office walls. Networks must now embrace the<br />
Edge - the place where data is created,<br />
captured, stored, and processed.<br />
Businesses that are able to connect to the<br />
Edge efficiently and securely, and leverage the<br />
data they collect, will be well positioned for the<br />
future. Research even shows that 72% of global<br />
IT leaders are actively using Edge technologies<br />
to deliver new outcomes. Those with more<br />
mature Edge deployments are even increasing<br />
their business value from that data. Coupled<br />
with the expansion of the enterprise network that<br />
accompanies Edge activity, strain legacy<br />
network operations and management, NaaS<br />
presents an opportunity for businesses to<br />
outsource the day-to-day management of the<br />
network and gain access to the most advanced<br />
hardware and software technology.<br />
We can expect NaaS to be a critical enabling<br />
platform for extending enterprise networks to the<br />
Edge in the coming months and years. This<br />
business model is increasingly being<br />
championed for its flexible approach and the<br />
subscription service is becoming highly<br />
recognised for a wealth of reasons.<br />
Organisations are waking up to the impact<br />
that NaaS deployment can have on IT staff<br />
workloads, its ability to stabilise security<br />
concerns, and unlock the true potential of Edge<br />
technologies - now and in the future. NC<br />
22 NETWORKcomputing MAY/JUNE <strong>2021</strong> @NCMagAndAwards<br />
WWW.NETWORKCOMPUTING.CO.UK
NETWORKcomputing<br />
We introduced the Network Computing "Masterclass" into the magazine a few years back. A<br />
Masterclass series in the magazine run for at least a year. Some have successfully run for longer. This<br />
concept enables us, with the help of a an expert vendor, to cover a subject area in a far more<br />
detailed way than could ever be covered in a single article. We feel that the Masterclasses we have<br />
carried have done a valuable job in guiding readers through many of the issues that they need to be<br />
aware of - issues that are perhaps not being talked about elsewhere. Vendor branding appears on<br />
the Masterclass page to distinguish a Masterclass article from the many "one-off" articles that we<br />
carry in Network Computing.<br />
We have identified a number of key subject areas which we feel would benefit from a Masterclass.<br />
These are:<br />
Network Testing and Monitoring<br />
Cabling and cable management<br />
Network access control<br />
Powering a Network<br />
The transition to unified comms<br />
Desktop virtualisation<br />
Traffic management<br />
Using a Data Centre<br />
Advantages and challenges of relying on an increasingly mobile workforce<br />
Cloud security<br />
Education and training<br />
If any of these subject areas are to be covered in a Masterclass we will be<br />
seeking a Partner to work with. A Masterclass Partner will ideally be a vendor<br />
with a track record of expertise in the particular area. Are you a vendor<br />
who could help us in launching a Masterclass covering one of the subjects<br />
listed above ? Alternatively, could you recommend an organisation who<br />
could help us ? Your suggestions will be very welcome.<br />
Please contact david.bonner@btc.co.uk
FEATUREIOT<br />
IoT TO THE RESCUE?<br />
NICK SACKE, HEAD OF IoT AND PRODUCTS AT<br />
COMMS365 DISCUSSES HOW IoT TECHNOLOGIES<br />
AND THE USE OF DATA CAN BOOST AND SUPPORT<br />
INDUSTRIES AND THE WIDER ECONOMY<br />
With the UK going into its first<br />
financial recession since 2009 as a<br />
consequence of COVID-19, many<br />
businesses are struggling to stay alive in the<br />
current business climate. The economy has<br />
shrunk by 20.4% compared with the first three<br />
months of 2020 following months of<br />
businesses being forced to stay shut,<br />
furloughed workforces and a reduction in<br />
consumer expenditure. Additional restrictions<br />
in place at the time of writing are ratcheting<br />
up the financial pressure on multiple<br />
industries, with the prospect of a 'double-dip'<br />
recession an increasing prospect.<br />
Without the right technology and continuity<br />
processes in place, many organisations were<br />
unable to adapt their models quickly enough<br />
to survive when they needed to. Now it's a<br />
wake-up call to get the right solutions<br />
implemented to ride the waves of any future<br />
economic storms that come their way.<br />
COVID-19 has accelerated the need to work<br />
collaboratively and stay connected to protect<br />
both society and the economy.<br />
BIG DATA ANALYTICS AND IoT<br />
With the increase in the volume of data that is<br />
being produced, identifying, analysing and<br />
using the useful information that is scattered<br />
around an organisation is a key business<br />
challenge, but also an opportunity. This can<br />
be addressed by the optimal use of data,<br />
deploying innovative IoT technologies<br />
including sensors, and targeted insights from<br />
'Big Data' analytics systems.<br />
Key information (data) is vital to ensuring<br />
businesses have 24/7 insight across their<br />
operations so that pinch points and potential<br />
problems can be identified and remedied<br />
almost in real-time. A good example of this is<br />
in the freight and cargo industry, where realtime<br />
monitoring of consignments using<br />
sensors can be analysed and used by<br />
operations executives to identify problems in<br />
the flow of goods, so that service level<br />
agreement can be met, and 'just in time'<br />
economic models can be reinforced.<br />
IoT, smart sensors and connected<br />
technologies are starting to play a key role in<br />
providing valuable data for effective decision<br />
making across all industries. Improving<br />
products and processes through data<br />
collection and analysis is now necessary for<br />
companies to future-proof their businesses in<br />
a highly volatile global market and identify<br />
additional revenue streams or alternative<br />
routes to market to soften the blow from any<br />
economic fallout. The more data we gather,<br />
the more centralised and secure organisations<br />
can become to limit the potentially devastating<br />
impact of future pandemics.<br />
DATA IN HEALTHCARE<br />
As part of the fight against the pandemic, the<br />
healthcare industry had to quickly adapt and<br />
digitally transform in order to continue the<br />
provision of healthcare services to patients<br />
across the world. Moreover, to understand the<br />
nature of the virus and curb its spread, the<br />
NHS was required to streamline the way it<br />
used data in order to make informed<br />
decisions. One element of this approach was<br />
the development of the NHS' data platform to<br />
provide national organisations with secure,<br />
reliable and timely data. By storing masses of<br />
information about those infected with COVID-<br />
19, this data can be effectively used for<br />
spotting trends, case identification, allocating<br />
resources and implementing national<br />
lockdowns in areas with rising cases.<br />
COVID-SAFE TECHNOLOGIES<br />
Elements that have had a significant impact<br />
on the economy are the need for social<br />
distancing measures, restrictions in gatherings<br />
and other safety elements that have had to be<br />
implemented. Particularly for industries such<br />
24 NETWORKcomputing MAY/JUNE <strong>2021</strong> @NCMagAndAwards<br />
WWW.NETWORKCOMPUTING.CO.UK
FEATUREIOT<br />
as manufacturing, retail and logistics, with<br />
less staff able to be present within the same<br />
environment, organisations faced significant<br />
challenges to meet demand. But this is where<br />
IoT technology is playing a vital role,<br />
especially once businesses start preparing for<br />
employees to return to their original work<br />
environments.<br />
The use of IoT technology can support<br />
additional sanitisation measures and the<br />
automation of shared touchpoints needed to<br />
limit cross-contamination. For example,<br />
detecting sanitiser bottle fill levels, monitoring<br />
the distance between people via infrared<br />
beams, alerting when social distancing<br />
thresholds are crossed, and analysing<br />
movement around working spaces with<br />
thermal imaging camera systems. By<br />
deploying innovative technologies such as<br />
these, businesses can still operate safely and<br />
more productively while generating revenue<br />
to remain operational and ultimately, boost<br />
the economy.<br />
GREEN AGENDA<br />
Sustainable supply chains can help to futureproof<br />
businesses and provide long-term<br />
resilience for organisations during challenging<br />
times. By taking a circular economy approach,<br />
which is an economic system which keeps<br />
resources in use for as long as possible,<br />
extracts the maximum value from them whilst<br />
in use, then recover and regenerate products<br />
and materials at the end of each service life<br />
(Wrap), organisations can reduce waste,<br />
extract the most value and obtain cost savings<br />
by optimising their use of resources.<br />
Advanced digital technologies can help to<br />
unlock the benefits from the circularity of<br />
resources. Through the collection and<br />
analysis of data, digital technology such as<br />
intelligent, interconnected devices, have the<br />
potential to identify challenges, outline the key<br />
areas of waste of resources and inform more<br />
effective decision-making on how to address<br />
these issues as they occur. By capitalising on<br />
innovation which will underpin sustained<br />
growth, businesses can benefit from a rise of<br />
new economic opportunities, such as<br />
substantial savings, mitigation of supply risks<br />
and long-term resilience of the economy,<br />
while ensuring that assets are used to their<br />
maximum potential and value.<br />
Moreover, particularly in a manufacturing<br />
environment, by having visual insight into the<br />
location and the condition and availability of<br />
each asset, this overview is of value to<br />
businesses to enhance their productivity<br />
through factors such as predictive<br />
maintenance. Overall, this helps to make<br />
products and services more effective and<br />
efficient, while reducing costs and waste in the<br />
supply chain. Initiatives supporting a circular<br />
economy offers businesses a more resilient<br />
and sustainable future, potentially creating<br />
over 500,000 more jobs and saving EU<br />
businesses 8% of their annual turnover.<br />
5G AND CONNECTIVITY<br />
Parts of our global critical infrastructure<br />
remain siloed, unconnected or with varying<br />
connectivity quality. In a pandemic when<br />
social distancing measures are in place, and<br />
workforces are remote, it's vital for businesses<br />
to have a robust, high-quality Internet<br />
connection and IoT connected devices on-site<br />
in factories, warehouses, construction sites,<br />
power plants, transport grids, hospitals,<br />
schools, government buildings and utility<br />
distribution networks. This will provide visibility<br />
on-site and remote access as required,<br />
resulting in reducing the need for engineers<br />
and IT teams to make unnecessary and<br />
potentially risky site visits.<br />
The deployment of 5G will help to increase<br />
network capacity and data flow; supporting<br />
connections of one million devices per<br />
square kilometre. By supercharging the<br />
potential of IoT with new 5G networks,<br />
connected buildings, vehicles, transport<br />
infrastructure and healthcare devices could<br />
all benefit from the value this enhanced<br />
connectivity will bring.<br />
For example, 5G could help to revolutionise<br />
traffic and congestion management, in turn,<br />
reducing delays and allowing quicker access<br />
for emergency services. Smart buildings are<br />
the future, and post-COVID-19, can help to<br />
boost the economy by reducing the costs of<br />
running the public sector estate, such as the<br />
introduction of smart lighting and optimising<br />
the use of air conditioning.<br />
Optimisation of facilities management will<br />
be especially important now that the<br />
population is set to be a nation of remote<br />
workers for the foreseeable future - heating<br />
and cooling entire buildings is now<br />
unnecessary. Building managers should be<br />
able to rely on intuitive technology to heat<br />
and light only those areas that are in use to<br />
save money and help support environmental<br />
initiatives in the process. Ventilation is now<br />
acknowledged to be a critical factor in<br />
preventing the spread of viruses such as<br />
COVID-19 in buildings. The monitoring of<br />
indoor environmental conditions and<br />
ventilation systems will be another tool in the<br />
new facilities management service portfolio.<br />
CONCLUSION<br />
If businesses were to embrace innovative<br />
technology and use the data they collect and<br />
store in the right way, the 'new normal' post-<br />
COVID-19 may be a smoother transition for<br />
many, while preparing them for any future<br />
unprecedented crisis. The opportunity to<br />
deploy innovative sensor-based technologies<br />
and data analytics services has given a<br />
growing number of start-ups and small<br />
businesses entry to enterprise and government<br />
supply chains, and lucrative contracts to aid<br />
the collection and optimal use of data.<br />
By leveraging the most value from their data<br />
and resources, as well as the management<br />
and more efficient use of resources to meet<br />
green agenda objectives, organisations can<br />
help to keep their running costs low, which is<br />
particularly important during uncertain times<br />
with reduced services and furloughed staff.<br />
This preparation, in turn, will help businesses<br />
to ride the waves of uncertainty and keep<br />
them trading to ultimately boost the economy<br />
in both the short and long-term. NC<br />
WWW.NETWORKCOMPUTING.CO.UK @NCMagAndAwards<br />
MAY/JUNE <strong>2021</strong> NETWORKcomputing 25
OPINION<br />
CLOSER TO THE EDGE<br />
SIMON MICHIE, CTO, PULSANT OFFERS A GUIDE TO THE ROLE<br />
OF EDGE AND IoT IN MODERN DATA CENTRES<br />
Reflective of the exponential growth of<br />
data is the 200% increase from 2016<br />
of connected IoT devices that are<br />
predicted to become active this year. As IoT<br />
devices enter more industries such as<br />
agriculture, healthcare, IT and critical<br />
services, it’s imperative for businesses to<br />
harness these technologies to make more<br />
informed data decisions. The challenge<br />
though is how it is used and analysed for<br />
real-time decision making.<br />
The answer to this for many is connection to<br />
the digital edge, but this raises the question of<br />
the role that edge computing and IoT plays in<br />
the data centre and colocation space. With<br />
this in mind, there are a number of aspects for<br />
you to consider:<br />
The uptake of IoT – IoT has been heavily<br />
verticalised in recent years and centered<br />
around healthcare, retail and manufacturing. It<br />
is however now starting to benefit other sectors<br />
such as health and safety initiatives, including<br />
track-and-trace and smart building technology.<br />
The increasing maturity of 5G – While 5G<br />
brings great promise as its rollout across the<br />
UK continues, there is still not widespread<br />
coverage to fully support this advancement.<br />
The adoption of data analytics – In much the<br />
same way as IoT, data analytics represents<br />
tremendous potential. However, mirroring the<br />
uptake and optimisation of IoT, the opportunity<br />
around analytics is still largely limited to<br />
verticalised applications<br />
The viability of regional colocation for the<br />
edge – Mobilising location-specific edge<br />
instances and the ability to spin-up the<br />
required communications hinges on<br />
strategically placed regional data centre<br />
locations and mitigating the cost and<br />
performance restrictions of public cloud.<br />
The expansion of customer data lakes – The<br />
maturation of customer data lakes curated<br />
outside of cloud boundaries with the potential<br />
to support edge applications before wider<br />
consolidated cloud publishing.<br />
The location of edge requirements – Edge<br />
positioning, both in terms of its physical<br />
location and architecture, has a high<br />
economic weighting in this model.<br />
THE RELATIONSHIP BETWEEN THE<br />
DATA CENTRE AND THE EDGE<br />
The role that edge computing plays in data<br />
centre operations closely depends on the<br />
above elements in order to capture, transfer,<br />
process, store and manage data. As it stands<br />
in the industry, interaction between many of<br />
these factors is taking place, but consistent<br />
integration between them is needed to<br />
establish a business case for an edge instance<br />
for IoT.<br />
When analysing the location of edge<br />
requirements, it's increasingly the case that the<br />
edge could be anything from a plane to a<br />
temporary site. For data centre providers, it's<br />
imperative to think beyond infrastructure<br />
change and deploy facilities closer to the<br />
customer instance, enabling business users to<br />
benefit from lower latency.<br />
While extension of remote services is likely<br />
with managed service providers, the<br />
economics of location, latency and capacity<br />
are vital for data centre providers. In many<br />
cases, it is hoped that the infrastructure<br />
footprint of the colocation provider will be<br />
sufficient, but this doesn't form the foundation<br />
of a sustainable edge colocation business<br />
model. This requires an effective, responsive<br />
and economic mobilisation of<br />
communications, which will be time-bound in<br />
many instances.<br />
LOOKING FORWARD<br />
Without doubt, the expansion of IoT and edge<br />
devices will continue to have an impact on<br />
businesses moving forward. The role that it<br />
plays in the data centre and colocation market<br />
however is defined largely on the interplay<br />
between a number of elements that will shape<br />
the industry moving forward. From gradual<br />
adoption of 5G technologies to changing<br />
colocation models, the coming years will dictate<br />
whether IoT and resulting data lakes will truly<br />
transform the data centre as we know it. NC<br />
26 NETWORKcomputing MAY/JUNE <strong>2021</strong> @NCMagAndAwards<br />
WWW.NETWORKCOMPUTING.CO.UK
OPINION<br />
MONITORING YOUR NETWORK IN THE TIME OF COVID-19<br />
BY MARK TOWLER, SENIOR PRODUCT MARKETING MANAGER, PROGRESS<br />
If 2020 taught us anything, it's that network<br />
monitoring is more important than ever.<br />
While there's always been the background<br />
awareness that network outages are expensive<br />
and the business can't run without a functioning<br />
network, the onslaught of COVID-19 brought<br />
that awareness firmly to the forefront.<br />
First off, everyone went home and network<br />
administrators had to cope - almost literally<br />
overnight - with supporting a remote workforce<br />
with the network they had. The VPN and the<br />
firewall systems suddenly became even more<br />
urgently critical resources than they'd been a<br />
week ago. For a few weeks administrators<br />
struggled to adapt, to support more remote<br />
workers than normal and to shore up systems<br />
that were suddenly under strain. Those with<br />
comprehensive network monitoring systems<br />
found this far easier to do than those without.<br />
However, once this task was complete there<br />
came months of adapting to the new reality.<br />
Workers literally could not work if they couldn't<br />
access the network. They couldn't just move to<br />
a different office, or an unused conference<br />
room or the cafeteria if they had network<br />
problems. They couldn't just walk down to the<br />
IT department to get a loaner laptop if their<br />
own stopped working. They couldn't even run<br />
down to the nearest coffee shop or library to<br />
use free WiFi. On top of all of this, every single<br />
employee was now consuming massive<br />
amounts of bandwidth for videoconferencing.<br />
Those smart enough to buy stock in Zoom<br />
were rewarded, but the network admins<br />
responsible for providing the stable<br />
connections that made it work found it a<br />
challenge. Again, those with a comprehensive<br />
network monitoring solution had an easier<br />
time of it. In fact, one of the key questions<br />
answered by network monitoring<br />
is, "Where is all my<br />
bandwidth going?"<br />
As a result, the<br />
organisations<br />
that adapted<br />
to the new<br />
COVID<br />
normal<br />
(and<br />
not<br />
all of them did) are now dealing with a world<br />
where the health of their network has become<br />
more important than ever. When an employee<br />
can't connect in order to do any work all day,<br />
the cost of network downtime escalates<br />
dramatically. As a result, we're seeing changes<br />
in the priorities of network monitoring<br />
customers. Solutions that simply monitor status<br />
and report upon it are no longer adequate;<br />
network administrators need to be alerted<br />
before network issues start to impact end-users<br />
so they can fix them.<br />
In addition, network monitoring systems that<br />
can apply 'self-healing' actions are becoming<br />
far more popular since they can automate<br />
responses to common issues. For example, if<br />
your network monitoring solution can<br />
automatically allocate more bandwidth to a<br />
server when traffic levels exceed 85%, that can<br />
mean the difference between an emergency<br />
midnight phone call and a minor notification<br />
the next day.<br />
Finally, the ongoing trend towards systems<br />
integration is reaching a tipping point. It's now<br />
easier than ever to integrate physical, virtual<br />
and cloud resources with any business system -<br />
and the advantages of doing so are legion.<br />
The network monitoring industry is keeping<br />
pace with a shift towards open APIs that allow<br />
easy integration and automation. Not only<br />
should your solution monitor these diverse<br />
environments, it should be able to feed<br />
monitoring data to any system that can use it.<br />
Similarly, other systems should be able to<br />
provide information to the network monitoring<br />
system so it can use that data to make<br />
changes to either the network itself, or how it<br />
monitors the network.<br />
Your organisation has become more agile and<br />
adaptable in the face of our new reality; your<br />
network monitoring system will need to do the<br />
same. NC<br />
WWW.NETWORKCOMPUTING.CO.UK @NCMagAndAwards<br />
MAY/JUNE <strong>2021</strong> NETWORKcomputing 27
OPINION<br />
THE VISIBLE BENEFITS OF AUTOMATION<br />
ADRIAN ROWLEY, SENIOR DIRECTOR EMEA, GIGAMON ON WHY<br />
NETWORK AUTOMATION AND VISIBILITY ARE KEY FOR DIGITAL<br />
TRANSFORMATION<br />
Just over a year ago, business leaders<br />
across the UK were forced to make tough<br />
decisions surrounding how to enable and<br />
secure their workforce in the mass shift to<br />
remote working. For some, the IT<br />
infrastructure was already in place to make<br />
the transition smooth, but 12 months of<br />
home working has stretched it to its limits. For<br />
others, with little digitisation to support them,<br />
quick responses were taken in a patchwork<br />
fashion, and the solution often became an<br />
acceleration towards hybrid cloud<br />
infrastructures.<br />
With such fast and dramatic changes,<br />
security risks increased, and network<br />
performance often suffered. What's more,<br />
visibility into data-in-motion became<br />
clouded, as networks were clogged up with<br />
an abundance of traffic from personal and<br />
unsecured devices, while the rapid growth in<br />
hybrid infrastructure created dangerous blind<br />
spots. Now, with fluid workforces set to stay,<br />
it is essential that businesses find ways to<br />
regain control over their increasingly<br />
complex networks.<br />
EMBRACE AUTOMATION<br />
Data volumes are growing far beyond the<br />
capacity for human analysis. Not only does<br />
5G have a role to play in this deluge of data,<br />
but the vast amounts of new traffic from<br />
personal devices will also have a detrimental<br />
effect on a business' network efficiency.<br />
Network automation is one way to solve this<br />
issue, and according to a recent survey, 97%<br />
of IT leaders agree that process automation is<br />
an essential part of digital transformation.<br />
However, what and how we automate has<br />
changed dramatically across the last ten years.<br />
Today, automating delivery of data to service<br />
triage and performance management tools is<br />
a simple process, despite its complexity in the<br />
past. Automating data intelligence has also<br />
become more popular for organisations<br />
looking for ways to free up their workforce,<br />
find potential bottlenecks in their infrastructure<br />
and mitigate the impact of cyberattacks.<br />
Ultimately, automation allows data-in-motion<br />
to be transformed into valuable insights that<br />
will improve processes and support the<br />
overstretched workforce, without the need for<br />
human intervention.<br />
INVEST IN PEOPLE AND ADJUST<br />
YOUR STRATEGY<br />
In a year where we have all been siloed and<br />
separated, working collaboratively is often no<br />
longer possible without technology as the<br />
enabler. However, this technology will not<br />
function efficiently without an experienced and<br />
skilled workforce behind it. While network<br />
automation supports IT teams as they struggle<br />
with the digital skills gap, organisations must<br />
ensure they have an expert team working<br />
alongside smart automation. With this<br />
combination, ROI becomes more measurable,<br />
and business processes begin to improve.<br />
The last 12 months have also demonstrated<br />
to many IT teams and C-suite leaders that<br />
organisations not only need to be willing to<br />
adjust their technology and infrastructure, but<br />
also change their policies and work processes.<br />
To meet the demand for a mass-shift to home<br />
working, many businesses had to change their<br />
approach, or risk losing staff and clients - it<br />
was a case of innovate or fail. The fluid<br />
workforce is looking set to stay, meaning<br />
companies must prioritise agility and be<br />
prepared to adapt their strategies, especially<br />
their cybersecurity defence systems, based on<br />
the current changeable climate.<br />
ALWAYS PRIORITISE VISIBILITY<br />
Regardless of whether visibility is needed to<br />
embrace automation or to bolster<br />
cybersecurity, establishing a clear view across<br />
a network is essential to regain control over<br />
data-in-motion and push forward with digital<br />
transformation initiatives. NetOps teams must<br />
be able to see into all on-premise, public,<br />
private and hybrid cloud infrastructure. No<br />
traffic - even encrypted data - should be out of<br />
view. To make this visibility possible, businesses<br />
should ensure they take a holistic approach to<br />
managing their IT infrastructure, monitoring all<br />
their technology assets as if through a single<br />
pane of glass. The level visibility will allow for<br />
more insights into network traffic that can<br />
improve business processes and ease the<br />
pressure on IT teams.<br />
NetOps teams are still facing the need to do<br />
more with less, as digital transformation<br />
initiatives continue but budgets remain tight.<br />
Network automation has therefore become a<br />
viable and valuable option for IT experts, and<br />
by ensuring that visibility is prioritised, these<br />
automation solutions can flourish. Business<br />
leaders must now understand that choosing<br />
whether or not to automate processes will<br />
significantly impact business success - or lack<br />
of - in the future. NC<br />
28 NETWORKcomputing MAY/JUNE <strong>2021</strong> @NCMagAndAwards<br />
WWW.NETWORKCOMPUTING.CO.UK
OPINION<br />
THE DIGITAL TRANSFORMATION DILEMMA<br />
U.K. EMPLOYEES WANT PANDEMIC-ERA TECH TO STAY, ACCORDING<br />
TO NEW RESEARCH FROM THE WORKFORCE INSTITUTE AT UKG<br />
As the U.K. prepares to return to normal<br />
in the coming months and industries<br />
reopen, research from The Workforce<br />
Institute at UKG reveals that as a result of the<br />
COVID-19 pandemic, 87% of U.K. workers<br />
have been propelled into the future of work<br />
by accelerating their digital transformation<br />
projects. Furthermore, 86% are enjoying the<br />
benefits of these new technologies, and 38%<br />
are fearful that their organisation will go back<br />
to the "old way" of doing things postpandemic.<br />
The global research commissioned by The<br />
Workforce Institute at UKG and conducted by<br />
Workplace Intelligence dissects the feelings of<br />
nearly 4,000 employees and business leaders<br />
across 11 countries to understand what digital<br />
transformation initiatives took place during the<br />
COVID-19 pandemic, how leaders and<br />
employees felt about these new technologies,<br />
and what they hope to see in the postpandemic<br />
world of work.<br />
ACCELERATED DIGITAL<br />
TRANSFORMATION<br />
The vast majority (87%) of U.K. decision<br />
makers said that digital transformation<br />
projects were sped up as a result of the<br />
pandemic. When asked to what degree they<br />
felt the pandemic accelerated these projects,<br />
75% said between 1 to 3 years!<br />
This is evidenced by more than three<br />
quarters (76%) of employees saying that they<br />
used at least one new technology or<br />
application during the crisis. Of those new<br />
technologies, more than a third (36%) started<br />
using mobile applications to complete some<br />
work activities and nearly a quarter (24%)<br />
were empowered to leverage more selfservice<br />
solutions.<br />
Reflecting on their preparation, leaders are<br />
varied on<br />
the actions<br />
they took during<br />
the crisis, with 34%<br />
accelerating a critical<br />
technology deployment, 30%<br />
deciding to replace a software vendor, and<br />
29% saying that they "found" budget to pursue<br />
a technology improvement that was previously<br />
thought to be too expensive or unnecessary.<br />
EMPLOYEES WELCOMED NEW<br />
TECHNOLOGIES<br />
These new technology implementations were<br />
well received, with 86% of U.K. employees<br />
giving their organisation a passing grade (A,<br />
B, or C) for its use or deployment of new<br />
technology during the COVID-19 pandemic<br />
to help them do their job more safely,<br />
efficiently, or from an alternative location.<br />
However, almost half (44%) of all U.K.<br />
workers regardless of level said that their<br />
company's pandemic response would have<br />
been smoother if they had implemented<br />
modern technologies as part of their standard<br />
strategy instead of waiting for the crisis to<br />
occur. And 42% feel that their organisation<br />
was slow to embrace new technologies prior<br />
to the pandemic.<br />
Looking to the future, employees hope to<br />
keep these technologies in their arsenal to<br />
better perform in their roles, as 60% hope<br />
their organisation keeps many of the<br />
technology and policy changes that were<br />
implemented during the COVID-19<br />
pandemic response. However, 38% believe<br />
their organisation will roll back the changes,<br />
going back to the "old way" of doing things.<br />
MODERN TECHNOLOGIES SHOW<br />
BENEFITS, DESPITE ROADBLOCKS<br />
Despite fear of rolling back technological<br />
improvements, U.K. workers remain optimistic<br />
about<br />
potential<br />
business benefits,<br />
with about half or<br />
more hoping their<br />
company's digital<br />
transformation efforts:<br />
create a better customer<br />
experience (54%);<br />
create a better employee experience<br />
(51%); and<br />
improve decision making (44%).<br />
Though they see barriers to these benefits,<br />
with more than one third feeling that their<br />
companies main challenge to selecting or<br />
implementing new technologies is:<br />
budget restraints (40%);<br />
security and privacy concerns (34%); and<br />
culture change and employee adoption<br />
(35%).<br />
"COVID-19 turned the world of work<br />
upside down and clearly forced the digital<br />
transformation hand in a very short period of<br />
time," said Peter Harte, group VP, EMEA,<br />
UKG. "Some organisations were simply<br />
trying to survive - and still are - but others<br />
have been thriving. One year later,<br />
organisations are seeing the fruits of their<br />
digital transformation labour.<br />
"It's now imperative to have a technology<br />
roadmap to aid them in thriving throughout<br />
the remainder of <strong>2021</strong> and into the future,<br />
to keep pace with developments to not only<br />
protect their bottom line, but also meet the<br />
needs of their people and customers." NC<br />
WWW.NETWORKCOMPUTING.CO.UK @NCMagAndAwards<br />
MAY/JUNE <strong>2021</strong> NETWORKcomputing 29
OPINION<br />
THE CONNECTIVITY CONUNDRUM<br />
LEE WADE, CEO OF EXPONENTIAL-E EXPLAINS WHY CONNECTIVITY IS THE FINAL PIECE IN THE HOME<br />
WORKING PRODUCTIVITY PUZZLE<br />
In our new world of work, lots of attention<br />
has been paid to how we connect<br />
individual employees and their homes to<br />
office networks. Why? So businesses can<br />
protect their bottom line. According to The<br />
World Economic Forum's Future of Jobs<br />
Report 2020, most business leaders believe<br />
their employees are less productive when out<br />
of the office. In fact, it says that 78% of<br />
business leaders think hybrid and homeworking<br />
will have a negative impact on<br />
employees' productivity.<br />
Understandably it's difficult to determine<br />
exactly how productive or efficient staff are at<br />
completing tasks when working from home.<br />
It's something that varies massively from one<br />
business to another, with the quality of<br />
technology provision a key determining factor.<br />
Whether business leaders like it or not, one<br />
thing is clear - hybrid working is here to stay.<br />
MAKING HOME WORKING WORK<br />
And it can't be all bad. If home working<br />
wasn't conducive to people doing their jobs,<br />
some of the world's most recognisable firms,<br />
including Spotify, Twitter and Microsoft<br />
wouldn't have committed to letting their<br />
employees work from home permanently<br />
should they choose to.<br />
Companies all around the world are<br />
considering following their lead, or at least<br />
guaranteeing the right to work from home for<br />
large portions of the week in employment<br />
contracts and workplace policies. But it's one<br />
thing to promise staff the benefit and another<br />
thing entirely to provide them with a set-up<br />
that ensures they are equally productive when<br />
working from home.<br />
That's where the need for constant<br />
connectivity comes in. Home networks need<br />
to provide an equal performance to that of<br />
company offices to make the current trend a<br />
consolidated reality. It's an achievable vision,<br />
and one that major firms such as Spotify<br />
begun to realise, thanks to their investment in<br />
best-in-class tech infrastructure.<br />
But for many firms, this vision remains a pipe<br />
30 NETWORKcomputing MAY/JUNE <strong>2021</strong> @NCMagAndAwards<br />
WWW.NETWORKCOMPUTING.CO.UK
OPINION<br />
dream. Most of them still have network<br />
architecture, capacity and security policies in<br />
place that were designed and implemented to<br />
only serve a small number of remote workers<br />
on a 'management approval' basis, and<br />
prioritise the needs and demands travelling<br />
for business, rather than facilitate genuinely<br />
'flexible' working.<br />
These inadequate policies are either<br />
creating or exacerbating three common<br />
obstacles that are affecting staff's ability to<br />
work effectively when logging in from home:<br />
1. Bandwidth barriers<br />
With so many people at home all at the same<br />
time, competing over Wi-Fi bandwidth, lots of<br />
connections are crumbling under the heavy<br />
load. How many times have you been on a<br />
call where your camera has frozen or a bad<br />
connection has kicked you out?<br />
It's up to employers, not employees, to<br />
remedy this issue. Various software-defined<br />
networking solutions are available that<br />
automatically divide up, prioritise and<br />
distribute the bandwidth coming into homes<br />
and direct it to where it's needed, so<br />
employees' meetings run smoothly and aren't<br />
interrupted by their kids watching Disney+, or<br />
other family members listening in to the latest<br />
tunes via Alexa.<br />
2. Security concerns<br />
Home networks are inherently insecure, and<br />
often unprotected by firewalls. Cyber<br />
attackers can break into home networks easily<br />
- even through IP-enabled devices, like your<br />
fridge or your kettle - and once inside, tunnel<br />
and break into their employer's corporate<br />
network. Who knew making a cup of tea<br />
could be so damaging?<br />
Businesses need a solution that<br />
automatically extends corporate-level security<br />
into each employee's home, making all<br />
offices - whether at home or on-site - equally<br />
secure, and truly delivering peace of mind as<br />
a service. Tools like SD-WAN help deliver this<br />
by integrating on-premise level security, and<br />
zero-trust access control, so employees'<br />
homes - and all connected items within them<br />
- become a secure extension of the corporate<br />
or office networks. And yes, that does even<br />
include the games consoles that kids have<br />
been using when they were meant to be<br />
doing school-work.<br />
3. The constant connectivity conundrum<br />
Most companies' HR policies are closely<br />
linked with pastoral staff care, and health and<br />
wellbeing. And for good reason. Staff need to<br />
be given the tools and support needed to<br />
maintain their physical and mental wellbeing.<br />
No one should complain about being given<br />
occasional free drinks, yoga sessions, or<br />
subscriptions to mindfulness apps.<br />
But looking after employees is now about<br />
more than wellbeing perks. HR policies need<br />
to evolve to based on our new reality of home<br />
working, and incorporate constant<br />
connectivity as a key pillar. Having a<br />
productive home working environment is now<br />
critical to the wellbeing of every member of<br />
staff, as well as their livelihood. Because<br />
without it, not only might their client<br />
relationships, performance and the company's<br />
revenues be affected, but their home life<br />
could also suffer. Poor connectivity could even<br />
threaten employees' own sources of income if<br />
they can't do their work properly. Employers<br />
therefore need to make sure connectivity is a<br />
key HR priority, and their networks allow staff<br />
to not only fulfil, but surpass the expectations<br />
of their roles.<br />
It's a no-brainer to invest in a network that<br />
takes the office to your employees, and gives<br />
them the ingredients to succeed, in order to<br />
make a long-term success of home working.<br />
Regardless of when restrictions end,<br />
employees now expect and demand that their<br />
employers provide them with tech<br />
infrastructure that ensures they're productive,<br />
wherever they are working from. Employers<br />
need to wake up and prepare for it. Now.<br />
Otherwise, they might find they no longer<br />
have a workforce to return to the office, when<br />
the time is right. NC<br />
WWW.NETWORKCOMPUTING.CO.UK @NCMagAndAwards<br />
MAY/JUNE <strong>2021</strong> NETWORKcomputing 31
SECURITYUPDATE<br />
THE WEAK LINK IN THE CHAIN<br />
SECTOR ORGANISATIONS NEED TO ADOPT A ZERO-<br />
COMPROMISE APPROACH TO CYBERSECURITY ACCORDING<br />
TO STEPH CHARBONNEAU, SENIOR DIRECTOR OF PRODUCT<br />
STRATEGY, HELPSYSTEMS<br />
No organisation is immune from the<br />
risk of supply chain cyber-attacks and<br />
data breaches, but those with<br />
especially large and complex supplier<br />
ecosystems are much more vulnerable. This is<br />
particularly true of public sector organisations<br />
and even more so in the light of the<br />
challenges, these organisations have faced<br />
during the last 12 months as a result of the<br />
pandemic. As society has adjusted to the<br />
ongoing COVID-19 environment, public<br />
sector entities have had no option but to<br />
provide the majority of their services online.<br />
Whether it is local government, social<br />
services, law enforcement or emergency<br />
services, organisations across all disciplines<br />
that depended on in-person processes have<br />
been forced to pivot to digital alternatives at<br />
an uncomfortable speed.<br />
In the space of a year, society has<br />
transformed beyond recognition, and digitalfirst<br />
is now an imperative. However, not only<br />
do public sector organisations handle a<br />
wealth of sensitive personally identifiable<br />
information (PII) which makes them a target,<br />
but they typically have large, complex<br />
supplier ecosystems and, in the rush to pivot<br />
to deliver online services that have<br />
traditionally been human activated, this has<br />
left a window of opportunity for hackers.<br />
INCREASED THREAT CAUSED BY AN<br />
EXPANDED ATTACK SURFACE<br />
Likewise, the extended attack surface as a<br />
result of the new remote workforce is also<br />
creating opportunities for cybercriminals.<br />
Although the public sector has made great<br />
advances in cybersecurity over the past four<br />
or five years, in <strong>May</strong> 2020 we undertook<br />
research with public sector cybersecurity<br />
workers - and the findings from this were<br />
concerning.<br />
In general, we found a widespread lack of<br />
awareness around cybersecurity, with almost<br />
half of respondents having either not heard<br />
of, or not knowing what ransomware is.<br />
Outdated operating systems are a common<br />
point of entry for cybercriminals, and our<br />
research found that 11% of public sector<br />
employees were still using Windows 7 - which<br />
has not been supported by Microsoft since<br />
January 2020.<br />
This all makes very clear the requirement for<br />
training and best practice guidance for public<br />
sector employees, especially when dealing<br />
with the extended ecosystem of suppliers and<br />
parties that are deemed a trusted source. If<br />
an employee can at least recognise a<br />
malicious email, then they will be far less<br />
likely to click on a link or open a file or<br />
image containing ransomware.<br />
This is particularly important in the new work<br />
environment we now find ourselves in, as a<br />
distributed workforce lacks the usual corporate<br />
cybersecurity defences and is perhaps even<br />
more vulnerable when juggling work with<br />
home-schooling and other distractions.<br />
THE MOVE TO MICROSOFT 365<br />
Additionally, COVID-19 has accelerated the<br />
trend to digitisation, and one such digital<br />
transformation trend particularly common in<br />
public sector organisations is the move to<br />
Microsoft 365. The effectiveness of this<br />
collaboration suite is undeniable, with many<br />
public sector organisations benefitting from its<br />
cloud-based capabilities. But in the rush for<br />
cost-effective deployments, are organisations<br />
missing out on vital security for emails, for<br />
example, because the level they've bought<br />
into does not provide adequate protection for<br />
sensitive data or cyber-attacks?<br />
32 NETWORKcomputing MAY/JUNE <strong>2021</strong> @NCMagAndAwards<br />
WWW.NETWORKCOMPUTING.CO.UK
SECURITYUPDATE<br />
To avoid the risk of a data breach, public<br />
sector organisations need to fully secure their<br />
business communication channels to ensure<br />
that sensitive information is only shared<br />
between authorised parties and detect when<br />
malware exists in messages, documents, or<br />
image-based files. And while Microsoft 365<br />
offers various levels of email security, it does<br />
not deliver the deep content inspection<br />
required to automatically detect and remove<br />
sensitive information (such as PII data or<br />
payment card information), especially within<br />
screenshots or scanned documents. Even with<br />
sandboxing, protection against ransomware is<br />
limited because the malware threats designed<br />
to evade these systems can be hidden within<br />
documents or image-based files.<br />
It is all too easy to see an email from a trusted<br />
supplier or partner and assume that it is safe to<br />
open, therefore, only a zero-compromise<br />
approach will provide the level of protection<br />
needed in today's multi-vector environment.<br />
HOW TO NEUTRALISE SUPPLY<br />
CHAIN THREATS<br />
Public sector organisations need layered<br />
security defences to neutralise any threats<br />
coming from a supplier. It is essential that<br />
organisations are adequately protected from<br />
incoming malware, embedded Advanced<br />
Persistent Threats, or any other threat that<br />
could pose a risk to the business. At<br />
HelpSystems, we offer a Secure Email<br />
Gateway which works in conjunction with<br />
Microsoft 365, giving public sector<br />
organisations the missing element required for<br />
a robust, comprehensive security posture, one<br />
that takes into consideration the threat posed<br />
by the extended supplier ecosystem.<br />
Data classification tools are also critical to<br />
ensure that sensitive data is appropriately<br />
treated, stored, and disposed of during its<br />
lifetime in accordance with its importance to<br />
the organisation. Through appropriate<br />
classification, using visual labelling and<br />
metadata application to emails and<br />
documents, this protects the organisation from<br />
the risk of sensitive data being exposed to<br />
unauthorised organisations further down the<br />
line through the supply chain.<br />
Likewise, data that isn't properly encrypted in<br />
transit can be at risk of compromise, so<br />
public sector organisations should use a<br />
secure and compliant mechanism for<br />
transferring data within the supply chain to<br />
reduce risks. Here Managed File Transfer<br />
(MFT) software can facilitate the automated<br />
sharing of data with suppliers and provide a<br />
central platform for information exchanges<br />
and other file transfer protections.<br />
AN UNPRECEDENTED YEAR<br />
At the start of this year, the IT Governance<br />
blog logged 134 security incidents in<br />
December, which accounted for more than<br />
148 million breached records. According to IT<br />
Governance, this brings the total for 2020 to<br />
more than 20 billion breached data records,<br />
and unfortunately, public sector organisations<br />
were in the top three industries most<br />
commonly breached.<br />
Most of these breaches are not sophisticated<br />
attacks but are a result of either ransomware<br />
or internal human error, therefore it is<br />
imperative that public sector organisations<br />
have the right technologies, policies, and<br />
training programs in place. NC<br />
If you are interested in finding out more<br />
about protecting your supply chain you can<br />
download the HelpSystems eGuide<br />
"Managing Cybersecurity Risk in the Supply<br />
Chain" at: https://bit.ly/3dTC0fe<br />
WWW.NETWORKCOMPUTING.CO.UK @NCMagAndAwards<br />
MAY/JUNE <strong>2021</strong> NETWORKcomputing 33
FEATUREDATA PROTECTION<br />
LESSONS FROM A DATA CENTRE FIRE<br />
FOLLOWING THE FIRE AT OVHCLOUD'S DATA CENTRE IN<br />
STRASBOURG IN MARCH, STEPHEN YOUNG, DIRECTOR<br />
ASSURESTOR, OFFERS HIS TAKE ON THE KEY LEARNINGS FROM<br />
THE INCIDENT<br />
Earlier this year, the fire at the OVHCloud<br />
data centre caused widespread<br />
disruption and data loss for customers<br />
with servers hosted at the site. Many<br />
companies may have permanently lost data,<br />
impacting their business, a number of which<br />
appear to have been hosting their own<br />
physical servers or virtual private servers.<br />
Some of these customers believed that data<br />
centres were so safe and secure that a disaster<br />
like this was impossible, but that in the event<br />
there was an issue, their data was being<br />
backed up as part of the service. Others were<br />
carrying out some form of backup or<br />
replication to servers in the same data centre.<br />
What this means is that a complete loss of<br />
services can still happen regardless of where<br />
you are hosted and that responsibility for<br />
ensuring you can recover systems and data<br />
quickly falls to the customer.<br />
There's still a belief amongst users of data<br />
centres, cloud and SaaS providers, that their<br />
data is secure, is backed up, and will come<br />
back online quickly in the event of a disaster.<br />
But many providers may only provide a<br />
'reasonable endeavours' service to retrieve lost<br />
data - and it's not always prominent in the Ts &<br />
Cs. For this reason it's vital to know exactly<br />
what's being provided.<br />
Without their own disaster recovery (DR)<br />
provisions, users of physical servers don't even<br />
need their data centre to be destroyed by fire<br />
to lose their data; server failure on its own<br />
could have caused this disruption and loss, or<br />
even some form of malware could<br />
compromise their service.<br />
For many, a simple solution of off-site<br />
replication or backup to a cloud service, such<br />
as disaster recovery-as-a-service (DRaaS) or<br />
backup-as-a-service (BaaS) provided from<br />
another data centre, can minimise downtime<br />
and prevent data loss. The fact that their<br />
systems and data are being duplicated<br />
elsewhere provides assurance in knowing it's<br />
recoverable.<br />
Until data centre providers offer backups as<br />
standard to customers, consider taking these<br />
six steps:<br />
1. Consider what you deem to be a disaster.<br />
Some are satisfied knowing their data can<br />
be recovered from backup, even if it takes<br />
hours or days. Others cannot afford any<br />
downtime and need systems back online<br />
within minutes, even seconds.<br />
2. Having servers and critical data within a<br />
data centre environment does not mean<br />
your systems are impervious to downtime<br />
or data loss. A data centre brings<br />
heightened levels of security and resilience,<br />
but it's still a building that can be affected<br />
by fire, flood and cyber-attacks.<br />
3. Whatever solution you decide on to<br />
protect your data, ensure it's<br />
geographically diverse. A DR solution with<br />
an RPO (Recovery Point Objective) of<br />
seconds and RTO (Recovery Time<br />
Objective) of minutes is compromised if it's<br />
in the same data centre or a second<br />
location close by.<br />
4. Big-name SaaS platforms, such as<br />
Microsoft 365 and Google Workspace,<br />
typically include some level of backup<br />
protection. But many of these 'backup<br />
features' are designed with the SaaS<br />
provider in mind and may not meet your<br />
needs. Watch out for ambiguous SLAs and<br />
missing features, such as granular<br />
recovery and flexible retention - critical for<br />
a good backup platform.<br />
5. Ensure you have the knowledge and time<br />
to research the right DR solution for your<br />
requirements and build in tests regularly.<br />
While you can do this using internal<br />
resource, you get specialised expertise<br />
using a DRaaS or external partner to<br />
deliver data protection/recovery.<br />
6. Many systems cannot be fully tested<br />
replicating a true disaster scenario due to<br />
the disruption it causes. By securing your<br />
data recovery/backup services via DRaaS<br />
or an external partner, you're likely to have<br />
inherent DR testing as part of the service<br />
with the ability to emulate a complete<br />
service outage without disruption.<br />
Finally, do not assume your systems are<br />
protected, that your data cannot be lost, and<br />
your organisation can survive downtime with<br />
little or no business impact. An outage or loss<br />
of data can have a huge impact, not only in<br />
our ability to perform tasks, but also on the<br />
bottom line. NC<br />
34 NETWORKcomputing MAY/JUNE <strong>2021</strong> @NCMagAndAwards<br />
WWW.NETWORKCOMPUTING.CO.UK