Cyber Defense eMagazine September Edition for 2022 #CDM
#CYBERDEFENSEMAG @CyberDefenseMag by @Miliefsky a world-renowned cyber security expert and the Publisher of Cyber Defense Magazine as part of the Cyber Defense Media Group as well as Yan Ross, Editor-in-Chief and many more writers, partners and supporters who make this an awesome publication! Thank you all and to our readers! OSINT ROCKS! #CDM #CDMG #OSINT #CYBERSECURITY #INFOSEC #BEST #PRACTICES #TIPS #TECHNIQUES
#CYBERDEFENSEMAG @CyberDefenseMag by @Miliefsky a world-renowned cyber security expert and the Publisher of Cyber Defense Magazine as part of the Cyber Defense Media Group as well as Yan Ross, Editor-in-Chief and many more writers, partners and supporters who make this an awesome publication! Thank you all and to our readers! OSINT ROCKS! #CDM #CDMG #OSINT #CYBERSECURITY #INFOSEC #BEST #PRACTICES #TIPS #TECHNIQUES
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
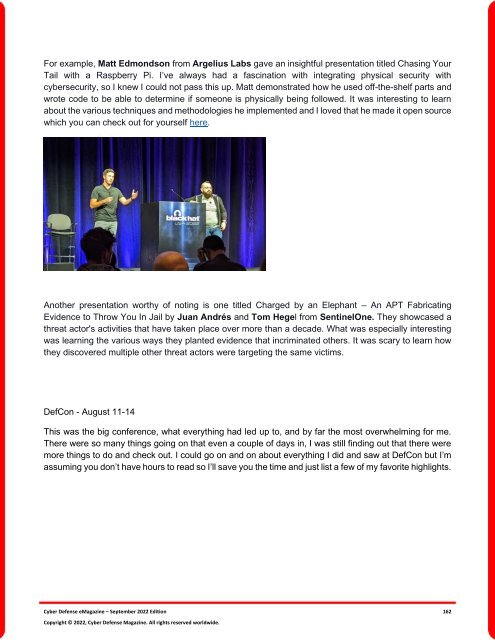
For example, Matt Edmondson from Argelius Labs gave an insightful presentation titled Chasing Your<br />
Tail with a Raspberry Pi. I’ve always had a fascination with integrating physical security with<br />
cybersecurity, so I knew I could not pass this up. Matt demonstrated how he used off-the-shelf parts and<br />
wrote code to be able to determine if someone is physically being followed. It was interesting to learn<br />
about the various techniques and methodologies he implemented and I loved that he made it open source<br />
which you can check out <strong>for</strong> yourself here.<br />
Another presentation worthy of noting is one titled Charged by an Elephant – An APT Fabricating<br />
Evidence to Throw You In Jail by Juan Andrés and Tom Hegel from SentinelOne. They showcased a<br />
threat actor's activities that have taken place over more than a decade. What was especially interesting<br />
was learning the various ways they planted evidence that incriminated others. It was scary to learn how<br />
they discovered multiple other threat actors were targeting the same victims.<br />
DefCon - August 11-14<br />
This was the big conference, what everything had led up to, and by far the most overwhelming <strong>for</strong> me.<br />
There were so many things going on that even a couple of days in, I was still finding out that there were<br />
more things to do and check out. I could go on and on about everything I did and saw at DefCon but I’m<br />
assuming you don’t have hours to read so I’ll save you the time and just list a few of my favorite highlights.<br />
<strong>Cyber</strong> <strong>Defense</strong> <strong>eMagazine</strong> – <strong>September</strong> <strong>2022</strong> <strong>Edition</strong> 162<br />
Copyright © <strong>2022</strong>, <strong>Cyber</strong> <strong>Defense</strong> Magazine. All rights reserved worldwide.