Targeting the iOS Kernel - Reverse Engineering Mac OS X
Targeting the iOS Kernel - Reverse Engineering Mac OS X
Targeting the iOS Kernel - Reverse Engineering Mac OS X
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
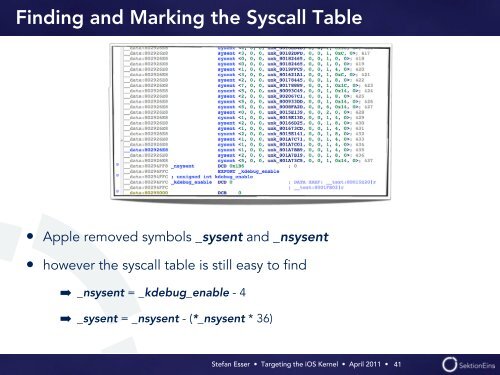
Finding and Marking <strong>the</strong> Syscall Table<br />
• Apple removed symbols _sysent and _nsysent<br />
• however <strong>the</strong> syscall table is still easy to find<br />
➡ _nsysent = _kdebug_enable - 4<br />
➡ _sysent = _nsysent - (*_nsysent * 36)<br />
Stefan Esser • <strong>Targeting</strong> <strong>the</strong> <strong>i<strong>OS</strong></strong> <strong>Kernel</strong> • April 2011 •<br />
41