CFOP 50-22, Acceptable Use of Information Technology - Florida ...
CFOP 50-22, Acceptable Use of Information Technology - Florida ...
CFOP 50-22, Acceptable Use of Information Technology - Florida ...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
This operating procedure supersedes <strong>CFOP</strong> <strong>50</strong>-<strong>22</strong> dated May 27, 2008.<br />
OPR: ITS<br />
DISTRIBUTION: A<br />
<strong>CFOP</strong> <strong>50</strong>-<strong>22</strong><br />
STATE OF FLORIDA<br />
DEPARTMENT OF<br />
CF OPERATING PROCEDURE CHILDREN AND FAMILIES<br />
NO. <strong>50</strong>-<strong>22</strong> TALLAHASSEE, December 1, 2011<br />
Systems Management<br />
ACCEPTABLE USE OF INFORMATION TECHNOLOGY RESOURCES<br />
This operating procedure establishes acceptable use <strong>of</strong> Department-owned information technology<br />
resources for Department employees, other personnel services (OPS), community-based providers<br />
connecting to the department’s network, as well as contractors and subcontractors. It further outlines<br />
the responsibilities <strong>of</strong> employees, other personnel services (OPS), community-based providers<br />
connecting to the department’s network, and contractors and subcontractors in ensuring the protection<br />
<strong>of</strong> confidential information.<br />
BY DIRECTION OF THE SECRETARY:<br />
(Signed original copy on file)<br />
SCOTT STEWART<br />
Assistant Secretary for<br />
Administration<br />
SUMMARY OF REVISED, DELETED, OR ADDED MATERIAL<br />
The operating procedure has been greatly expanded to provide a complete and concise description <strong>of</strong><br />
the acceptable use <strong>of</strong> information technology resources.
December 1, 2011 <strong>CFOP</strong> <strong>50</strong>-<strong>22</strong><br />
CONTENTS<br />
Paragraph<br />
Chapter 1 – GENERAL<br />
Purpose ...................................................................................................................... 1-1<br />
Scope ......................................................................................................................... 1-2<br />
Authority ..................................................................................................................... 1-3<br />
Definitions .................................................................................................................. 1-4<br />
Policy Statement ........................................................................................................ 1-5<br />
Basic Principles .......................................................................................................... 1-6<br />
Monitoring <strong>of</strong> Employee <strong>Use</strong> <strong>of</strong> Agency <strong>Information</strong> <strong>Technology</strong> Resources ............ 1-7<br />
Chapter 2 – USE OF THE INTERNET AND E-MAIL<br />
Purpose ...................................................................................................................... 2-1<br />
<strong>Use</strong> <strong>of</strong> the Internet on Departmental <strong>Information</strong> <strong>Technology</strong> Resources ................. 2-2<br />
<strong>Use</strong> <strong>of</strong> E-mail .............................................................................................................. 2-3<br />
Chapter 3 – USE AND PROTECTION OF CONFIDENTIAL INFORMATION<br />
Purpose ...................................................................................................................... 3-1<br />
Guiding Principles ...................................................................................................... 3-2<br />
Types <strong>of</strong> Protected <strong>Information</strong> .................................................................................. 3-3<br />
Conditions <strong>of</strong> <strong>Use</strong> ....................................................................................................... 3-4<br />
Release <strong>of</strong> <strong>Information</strong> ............................................................................................... 3-5<br />
Sanctions and Other Consequences for Misuse ........................................................ 3-6<br />
ii
December 1, 2011 <strong>CFOP</strong> <strong>50</strong>-<strong>22</strong><br />
Chapter 1<br />
GENERAL<br />
1-1. Purpose. This operating procedure establishes the Department’s policy for the use <strong>of</strong><br />
Department-owned information technology resources (e.g., desktop computers, laptops, tablets,<br />
Blackberries, smartphones and associated devices). This operating procedure applies to Department<br />
employees, other personnel services (OPS), community-based providers connecting to the<br />
Department’s network, consultants, contractors and subcontractors (hereinafter collectively referred to<br />
as employees). This operating procedure outlines acceptable use <strong>of</strong> Department information<br />
technology resources, the responsibilities <strong>of</strong> employees in ensuring the security and confidentiality <strong>of</strong><br />
Department data and outlines employee responsibilities in the event <strong>of</strong> a security incident.<br />
1-2. Scope. This operating procedure applies to all employees accessing Department information<br />
technology resources at any location. (71A-1.019(1))<br />
1-3. Authority. Section 282.318, <strong>Florida</strong> Statutes, “Security <strong>of</strong> Data and <strong>Information</strong> <strong>Technology</strong><br />
Resources,” Chapter 815, <strong>Florida</strong> Statutes, “<strong>Florida</strong> Computer Crimes Act,” and, <strong>Florida</strong> Administrative<br />
Code, Chapter 71A-1, “<strong>Florida</strong> <strong>Information</strong> Resource Security Policies and Standards.”<br />
1-4. Definitions.<br />
a. Automatic E-mail Forwarding. Defining a rule within an e-mail account that forwards some or<br />
all e-mails received to another e-mail account.<br />
b. Auto Responder. A computer program that automatically answers e-mail sent to it.<br />
c. Bandwidth. Refers to how much data can be sent or received through a network connection<br />
given an amount <strong>of</strong> time.<br />
d. Blog. A type <strong>of</strong> website or part <strong>of</strong> a website usually maintained by an individual with regular<br />
entries <strong>of</strong> commentary, descriptions <strong>of</strong> events, or other material such as graphics or video. Entries are<br />
commonly displayed in reverse-chronological order.<br />
e. Blocked Web Site. A web site to which a system administrator has refused users' access.<br />
f. Brief and Occasional <strong>Use</strong> <strong>of</strong> E-mails. Brief refers to the size <strong>of</strong> the message sent, received or<br />
downloaded. Usually, a message less than 300 words is considered brief. Occasional use means<br />
once in a while for a short period <strong>of</strong> time, similar to the occasional use <strong>of</strong> the telephone for personal use<br />
or the occasional trip to a cafeteria or vending machine.<br />
g. Browsing <strong>of</strong> Data. To inspect, read or look through information with no specific work<br />
purpose.<br />
h. Chain Letter E-mail. A message that attempts to induce the recipient to make a number <strong>of</strong><br />
copies <strong>of</strong> the e-mail and then pass them on to other recipients.<br />
i. Chat Room. An interactive, online discussion (by keyboard) about a specific topic hosted on<br />
the Internet.<br />
j. Confidential <strong>Information</strong>. <strong>Information</strong> that has specific statutory exemption from the public<br />
records laws. Specific requirements for appropriate levels <strong>of</strong> data security remain under the purview <strong>of</strong><br />
each agency.<br />
1-1
December 1, 2011 <strong>CFOP</strong> <strong>50</strong>-<strong>22</strong><br />
k. Data. A collection <strong>of</strong> facts; numeric, alphabetic and special characters which are processed<br />
or produced by a computer.<br />
l. Data Streaming (or Streaming Data/Multimedia). Streaming media technology allows real<br />
time or on-demand delivery <strong>of</strong> multimedia content (e.g., YouTube). The media (video, voice, data) is<br />
received in a simultaneous, continuous stream rather than downloaded all at once then displayed later.<br />
m. E-Mail Bomb. A form <strong>of</strong> e-mail abuse consisting <strong>of</strong> sending huge volumes <strong>of</strong> e-mail to an<br />
address in an attempt to overflow the mailbox or overwhelm the server where the e-mail address is<br />
hosted.<br />
n. Employee. Department employees, other personnel services (OPS), community-based<br />
providers connecting to the Department’s network, consultants, contractors, subcontractors, volunteers<br />
and non-paid staff.<br />
o. Exempt or Exemption. A provision <strong>of</strong> general law which provides that a specified record, or<br />
portion there<strong>of</strong>, is not subject to the access requirements <strong>of</strong> s. 119.07(1), s. 286.011, or s. 24, Art. I <strong>of</strong><br />
the State Constitution.<br />
p. Firewall. A computer or computer s<strong>of</strong>tware that prevents unauthorized access to private<br />
data (as on a company's local area network or Intranet) by outside computer users (as on the Internet).<br />
q. E-Greeting Card. Electronic greeting card message sent via e-mail; an electronic message<br />
that looks like a greeting card requesting the recipient to download or install a computer file or visit a<br />
site.<br />
r. Inappropriate E-Mail. An e-mail message and/or attachment that contains <strong>of</strong>fensive material.<br />
This material may include but is not limited to cartoons, messages, jokes, pictures, or stories that make<br />
fun <strong>of</strong> or insult a person because <strong>of</strong> his or her race, color, religion, gender, national origin, disability,<br />
marital status, or age; fully or partially nude images; pornography; or messages designed to promote a<br />
particular religion or political activity.<br />
s. Internet. A global system <strong>of</strong> interconnected computer networks that are linked together by a<br />
broad array <strong>of</strong> electronic, wireless and optical networking technologies and carrying a vast array <strong>of</strong><br />
information resources and services such as hypertext documents; the World Wide Web and the<br />
infrastructure to support electronic mail.<br />
t. Inappropriate (Internet) Website. A website that contains <strong>of</strong>fensive material. This material<br />
may include but is not limited to cartoons, messages, jokes, pictures, or stories that make fun <strong>of</strong> or<br />
insult a person because <strong>of</strong> his or her race, color, religion, gender, national origin, disability, marital<br />
status, or age; fully or partially nude images; pornography; gambling sites; messages designed to<br />
promote a particular religion or political activity; or sites that utilize an excessive amount <strong>of</strong> bandwidth<br />
such as online radio, television, or movies for purposes other than work.<br />
u. <strong>Information</strong> Security Manager. The person designated by the Secretary <strong>of</strong> the Department to<br />
administer the Department’s data and information technology resource security program.<br />
v. <strong>Information</strong> <strong>Technology</strong> Resources. Data processing hardware (including desktop<br />
computers, laptops, tablets, Blackberries, smartphones and associated devices), s<strong>of</strong>tware and<br />
services, supplies, personnel, facility resources, maintenance, training, or other related resources.<br />
w. Mailbot. A s<strong>of</strong>tware agent in a mail server that is typically used to send an automatic<br />
response to the sender.<br />
1-2
December 1, 2011 <strong>CFOP</strong> <strong>50</strong>-<strong>22</strong><br />
x. Malware. Programming (code, scripts, active content, and other s<strong>of</strong>tware) designed to<br />
disrupt or deny operation, gather information that leads to loss <strong>of</strong> privacy or exploitation, gain<br />
unauthorized access to system resources, and other abusive behavior. A general term used to mean a<br />
variety <strong>of</strong> forms <strong>of</strong> hostile, intrusive, or annoying s<strong>of</strong>tware or program code.<br />
y. News Group and Bulletin Board Service (BBS). A discussion group on the Internet in which<br />
participants with similar interests leave messages or other information for participants to read.<br />
z. Non-Work Hours. Before and after the employee’s supervisor-approved work schedule and<br />
during the employee’s scheduled lunch.<br />
aa. Occasional Personal <strong>Use</strong> (<strong>of</strong> e-mail, the Internet, or Department computer-related<br />
equipment). Occasional personal use is the infrequent or limited use <strong>of</strong> Department e-mail or access <strong>of</strong><br />
the Internet through the Department’s network, and/or Department owned computer-related equipment.<br />
For example, receiving or sending an e-mail from/to your child’s school to schedule a teacher<br />
conference is an occasional and appropriate use <strong>of</strong> the Department’s e-mail. Similarly, reading an<br />
online article published by the local newspaper is an example <strong>of</strong> an occasional and appropriate use <strong>of</strong><br />
the Department’s network to access the Internet.<br />
bb. Privately-Owned Devices. <strong>Information</strong> technology resources that are not the property <strong>of</strong> the<br />
Department.<br />
cc. Proxy Server. A device that allows other devices to connect to the Internet. It sits between<br />
information technology resources on a network and the Internet allowing for a secure connection and<br />
allowing only certain kinds <strong>of</strong> connections to exist. Proxy servers can be used to log Internet use and<br />
block access to banned sites.<br />
dd. Push <strong>Technology</strong>. The prearranged updating <strong>of</strong> news, weather, or other selected<br />
information on a computer user's desktop through periodic and unobtrusive transmission over the<br />
Internet.<br />
ee. Social Networking Sites and Social Media. Social media and Web 2.0 are umbrella terms<br />
that define the various activities that integrate technology, social interaction, and content creation.<br />
Through social media, individuals or collaborations <strong>of</strong> individuals create web content, organize content,<br />
edit or comment on content, combine content, and share content. Social media and Web 2.0 use many<br />
technologies and forms, including RSS and other syndicated web feeds, blogs, wikis, photo–sharing,<br />
video–sharing, podcasts, social networking, social bookmarking, mashups, widgets, virtual worlds,<br />
micro–blogs, and more. Also an Internet-based social site such as LinkedIn, Facebook, and Twitter<br />
that allows users to build virtual communities for communicating and sharing information.<br />
ff. Social Security Administration Data. Data provided to the Department by the Social Security<br />
Administration to help determine eligibility, among other uses. This includes Personally Identifiable<br />
<strong>Information</strong> including information used to distinguish or trace an individual’s identity (e.g., name, social<br />
security number, biometric records, or when combined with other personal or identifying information,<br />
which is linked or linkable to a specific individual, such as date, place <strong>of</strong> birth or mother’s maiden<br />
name).<br />
gg. System Owner(s). The entity that owns the data and has the primary responsibility for<br />
decisions relating to a particular data processing system’s specification and usage.<br />
hh. System <strong>Use</strong>rs. Any person or employee who, through State employment, contractual<br />
arrangement, charitable service, or any other service arrangement and with appropriate approvals,<br />
would have access to the Department’s facilities, the Department’s information technology resources,<br />
or the Department’s data for the purpose <strong>of</strong> conducting business or providing services.<br />
1-3
December 1, 2011 <strong>CFOP</strong> <strong>50</strong>-<strong>22</strong><br />
ii. Trojan Horse. A program in which malicious or harmful code is contained inside seemingly<br />
harmless programming or data in such a way that it can get control and do its chosen form <strong>of</strong> damage.<br />
jj. Virus. Programming code usually disguised as something else that causes an unexpected<br />
and usually undesirable event. Many viruses are designed to automatically spread to other computers.<br />
Viruses can be passed on as attachments to an e-mail, as downloads, or introduced on a non-<br />
Department media device.<br />
kk. Work Hours. An employee’s supervisor-approved work schedule, including breaks.<br />
1-5. Policy Statement.<br />
a. Employees may be provided access to Department-owned information technology resources<br />
for Department business purposes. Except as provided herein, all Department data, information, and<br />
technology resources shall only be used for <strong>of</strong>ficial Department business.<br />
b. Inappropriate use <strong>of</strong> information technology resources, the Internet, Department e-mail, or<br />
the Department or State’s automated applications and the data contained therein will subject<br />
employees to disciplinary action, up to and including dismissal as well as criminal charges.<br />
(71A-1.019(2))<br />
c. Inappropriate use <strong>of</strong> Department owned information technology resources, the Internet,<br />
Department e-mail, or the Department or State’s automated applications and the data contained therein<br />
by contracted employees is sufficient cause to terminate the contractual relationship and may result in<br />
criminal charges. The <strong>Florida</strong> Computer Crimes Act, Chapter 815, <strong>Florida</strong> Statutes, addresses the<br />
unauthorized change, destruction, disclosure, or taking <strong>of</strong> information resources.<br />
d. Any requests for exception to any portion <strong>of</strong> this policy must be in writing, approved by the<br />
employee’s supervisor and forwarded to the Office <strong>of</strong> the Chief <strong>Information</strong> Officer for approval.<br />
1-6. Basic Principles.<br />
a. Access to the Internet, Intranet, and e-mail may be granted to an employee as a part <strong>of</strong> their<br />
employment. Employees must adhere to all applicable State policies, Department policies and<br />
procedures, Federal regulations, as well as State and local laws. (71A-1.019(24))<br />
b. Employees may use the Internet to access sites for personal use during work and non-work<br />
hours, provided use is brief, the content is appropriate, and the employee adheres to the guidelines<br />
contained herein. (71A-1.019(27))<br />
c. Only Department approved s<strong>of</strong>tware shall be installed on Department information technology<br />
devices.<br />
(1) Employees are prohibited from using the Department’s Internet or e-mail facilities to<br />
knowingly download or deliver s<strong>of</strong>tware or data files. Violations <strong>of</strong> any s<strong>of</strong>tware license agreements or<br />
information services contracts by the unauthorized duplication <strong>of</strong> s<strong>of</strong>tware, files, operating instructions<br />
or reference manuals is prohibited. Employees will not download or install s<strong>of</strong>tware unless approved by<br />
the Department’s Office <strong>of</strong> <strong>Information</strong> <strong>Technology</strong> Services. Contact the <strong>Information</strong> <strong>Technology</strong><br />
Services Help Desk with questions about downloading or installing s<strong>of</strong>tware. (71A-1.019(31))<br />
(2) Any s<strong>of</strong>tware or files approved for downloading onto Department information<br />
technology resources become the property <strong>of</strong> the Department.<br />
1-4
December 1, 2011 <strong>CFOP</strong> <strong>50</strong>-<strong>22</strong><br />
(3) Any files or s<strong>of</strong>tware approved for downloading and installation may be used only in<br />
ways that are consistent with license and copyright.<br />
d. Employees are prohibited from duplicating licensed s<strong>of</strong>tware. (71A-1.019(32))<br />
e. Employees will protect information from unauthorized change, destruction, or disclosure, and<br />
will safeguard sensitive and confidential information.<br />
f. Employees will not attempt to access information technology resources and information to<br />
which they do not have authorization or explicit consent. (71A-1.019(35))<br />
g. Employees must obtain documented authorization before taking information technology<br />
resources, s<strong>of</strong>tware, or information away from an agency facility. (71A-1.019(5))<br />
h. No privately-owned devices shall be connected to Department-owned information technology<br />
resources without documented agency authorization. (71A-1.019(33))<br />
i. Employees are prohibited from disabling or modifying the installed configuration <strong>of</strong> encryption<br />
s<strong>of</strong>tware, anti-virus protection and personal firewall s<strong>of</strong>tware on Department-owned information<br />
technology resources.<br />
1-7. Monitoring Employee <strong>Use</strong> <strong>of</strong> Agency <strong>Information</strong> <strong>Technology</strong> Resources.<br />
a. The Department may check, log, and/or audit Internet activity, e-mail use, and the use <strong>of</strong><br />
Department information technology resources. Employees shall have no expectation <strong>of</strong> privacy in their<br />
use <strong>of</strong> Department information technology resources and the use <strong>of</strong> Department information technology<br />
resources constitutes consent to monitoring activities with or without a warning and monitoring and<br />
auditing may take place without the employee’s knowledge. (71A-1.019(20), 71A-1.019(<strong>22</strong>), and<br />
71A-1.019(23))<br />
b. The Department may inspect files stored on any network or local computer system, including<br />
removable media. Employees shall have no expectation <strong>of</strong> privacy <strong>of</strong> documents created, stored, sent,<br />
received, or deleted on Department’s information technology resources (including business and<br />
personal external and internal e-mails), or any other information technology resource related activity.<br />
(71A-1.019(21))<br />
c. The Department has installed firewalls, proxy servers, Internet web site blocking, reporting<br />
programs and other security systems to assure the safety and security <strong>of</strong> the Department network. Any<br />
employee who attempts to disable, defeat or evade any Department security feature without<br />
authorization from the Chief <strong>Information</strong> Officer may be subject to disciplinary action, up to and<br />
including dismissal. (71A-1.019(2))<br />
d. <strong>Information</strong> technology security activities such as network monitoring, sniffing, penetration<br />
testing and related security activities shall be performed only by Department <strong>Information</strong> <strong>Technology</strong><br />
Services employees or those under the direct authority <strong>of</strong> the Chief <strong>Information</strong> Officer.<br />
(71A-1.019(34))<br />
1-5
December 1, 2011 <strong>CFOP</strong> <strong>50</strong>-<strong>22</strong><br />
Chapter 2<br />
USE OF THE INTERNET AND E-MAIL<br />
2-1. Purpose. This chapter establishes the Department’s policy for the use <strong>of</strong> Department-owned<br />
information technology resources by employees when accessing and using the Internet and e-mail for<br />
business or personal use. (71A-1.019(6), 71A-1.019(7))<br />
2-2. <strong>Use</strong> <strong>of</strong> the Internet on Departmental <strong>Information</strong> <strong>Technology</strong> Resources.<br />
a. During non-work hours, such as lunch break or before/after scheduled work hours,<br />
employees may access the Internet for personal use by means <strong>of</strong> the Department network and<br />
Department information technology resources provided such use is not inappropriate as described<br />
herein.<br />
(1) Personal use must not interfere with or disrupt the normal performance <strong>of</strong> the<br />
employee’s job duties. (71A-1.019(8))<br />
(2) Usage must not consume significant amounts <strong>of</strong> IT resources (e.g., bandwidth,<br />
storage) or compromise the normal functionality <strong>of</strong> the Department’s systems. (71A-1.019(9))<br />
(3) Personal use must not result in any additional cost to the Department.<br />
b. Examples <strong>of</strong> Internet activities that are inappropriate and may subject the employee to<br />
disciplinary action include, but are not limited to, the following:<br />
activities.<br />
(1) Engaging in any illegal activities or behavior. (71A-1.019(28))<br />
(2) Conducting activities related to the employee’s outside business or commercial<br />
(3) Using Department-owned information technology resources or the Internet for<br />
matters directed toward the success or failure <strong>of</strong> a political party, candidate for political <strong>of</strong>fice, or<br />
partisan political advocacy group. (71A-1.019(28))<br />
(4) Using the Internet or any Department-owned information technology resource for<br />
personal financial gain. (71A-1.019(36))<br />
(5) Using Department information technology resources to harass, threaten, or abuse<br />
others. (71A-1.019(38))<br />
(6) Disrupting or causing security breaches to network communication, or<br />
circumvention, reconfiguration, or other subversion <strong>of</strong> system and network security measures.<br />
(71A-1.019(40))<br />
(7) Unauthorized access <strong>of</strong> hacker web-sites/s<strong>of</strong>tware. (71A-1.019(28))<br />
(8) Unauthorized access <strong>of</strong> peer-to-peer file sharing web-sites/s<strong>of</strong>tware.<br />
(71A-1.019(28))<br />
(9) Editing, posting comments, providing information, or engaging in any interactive<br />
online discussions or blogs.<br />
(10) Access to or joining non-business related chat rooms, singles clubs, bulletin<br />
boards, or dating services. (71A-1.019(28))<br />
2-1
December 1, 2011 <strong>CFOP</strong> <strong>50</strong>-<strong>22</strong><br />
(11) Intentionally accessing, installing, introducing, downloading, or distributing:<br />
(a) Viruses, worms, Trojan horses, e-mail bombs, malware, or any unauthorized<br />
files from the Internet. Files obtained from sources <strong>of</strong>f the Department’s network should be scanned for<br />
viruses before use or distribution. No file received from an unknown source should be opened,<br />
including files attached to an e-mail message. Call the <strong>Information</strong> <strong>Technology</strong> Services Help Desk<br />
with any questions. 71A-1.019(26)<br />
(b) E-greeting cards, video files, audio files, screen savers, games, non-work<br />
related streaming data/multimedia including push technology, auto responder, mailbot, radio, or<br />
television. If there is a business related purpose to access streaming media or data, you must obtain<br />
approval from your supervisor and request an exception through your local Regional/Facility<br />
<strong>Information</strong> Systems Security Officer.<br />
(c) Sexually suggestive, sexually explicit, pornographic, <strong>of</strong>fensive, indecent,<br />
obscene or vulgar material (including <strong>of</strong>f-color jokes or images). (71A-1.019(28), 71A-1.019(37))<br />
(d) Material containing pr<strong>of</strong>anity or inappropriate language, including, but not<br />
limited to, obscene material, or material with racial, ethnic, gender or other discriminatory content.<br />
(e) Material relating to gambling, weapons, illegal drugs and/or drug<br />
paraphernalia, terrorist activities or violence. 71A-1.019(28)<br />
c. Although the Department may install filters to block access to inappropriate Internet sites, not<br />
every inappropriate site can be blocked by a filter. The items above identify examples <strong>of</strong> inappropriate<br />
activities and employees should apply careful judgment whenever using Department-owned information<br />
technology resources to access the Internet. If an employee is connected unintentionally to a site that<br />
contains inappropriate material (e.g., sexually explicit) the employee must disconnect from that site<br />
immediately and notify their supervisor.<br />
d. Social Networking Sites such as LinkedIn, Facebook, and Twitter allow users to build virtual<br />
communities for communicating and sharing information. <strong>Use</strong> <strong>of</strong> specific Social Networking Sites for<br />
Departmental purposes must demonstrate business value and be approved by the appropriate Director<br />
or Bureau Chief and Assistant Secretary with concurrence from the Office <strong>of</strong> the Chief <strong>Information</strong><br />
Officer. Permission to use Department information technology resources or networks to access<br />
individual social networking sites for non-business purposes, such as college or university sites like<br />
Blackboard or WebCT requires written authorization from the employee’s supervisor and/or director.<br />
2-3. <strong>Use</strong> <strong>of</strong> E-Mail. Business and personal e-mails sent/received from a Department e-mail account or<br />
information technology resource are public records. E-mails containing exempt or confidential<br />
information may be redacted pursuant to <strong>Florida</strong> statute but the e-mails are still public records.<br />
a. Confidentiality Notice on E-Mail. The following text is automatically included on all e-mail<br />
messages sent from the Department to external recipients:<br />
“CONFIDENTIALITY NOTICE: This message and any attachments are for the sole use<br />
<strong>of</strong> the intended recipient(s) and may contain confidential and privileged information that<br />
is exempt from public disclosure. Any unauthorized review, use, disclosure, or<br />
distribution is prohibited. If you have received this message in error please contact the<br />
sender (by phone or reply electronic mail) and then destroy all copies <strong>of</strong> the original<br />
message.”<br />
2-2
December 1, 2011 <strong>CFOP</strong> <strong>50</strong>-<strong>22</strong><br />
b. E-mails received that contain threats to the Department’s information technology resources<br />
should be reported to your immediate supervisor, <strong>Information</strong> <strong>Technology</strong> Services Help Desk, and the<br />
Office <strong>of</strong> the Inspector General.<br />
c. Examples <strong>of</strong> e-mail activities that are inappropriate and may subject the employee to<br />
disciplinary action include but are not limited to:<br />
(1) Participation in any e-mail communication from a Department e-mail account or<br />
personal Internet e-mail account on Department information technology resource by sending,<br />
forwarding, or storing any message:<br />
(a) Which supports a particular religious preference, belief or group.<br />
(b) That is harassing, intimidating, threatening, or disruptive. (71A-1.019(38))<br />
(c) That contains pr<strong>of</strong>anity or inappropriate language, including, but not limited<br />
to, sexually suggestive, sexually explicit, pornographic, obscene or vulgar (including <strong>of</strong>f-color jokes or<br />
images), or material with racial, ethnic, gender or other discriminatory content.<br />
activities or violence.<br />
(d) Related to gambling, weapons, illegal drugs or drug paraphernalia, terrorist<br />
(e) Directed toward the success or failure <strong>of</strong> a political party, candidate for<br />
political <strong>of</strong>fice, political campaign, fund raising or partisan political advocacy group. (71A-1.019(39))<br />
(f) Any chain letter e-mail. (71A-1.019(26))<br />
(2) Using a Department e-mail account to conduct activities concerning the employee’s<br />
outside business or commercial activities, including sending, storing, or forwarding any message for<br />
personal gain or associating in any way the employee’s Department e-mail account with an outside<br />
business or commercial activity. (71A-1.019(36))<br />
(3) Automated forwarding <strong>of</strong> Department e-mail to a destination outside the<br />
Department’s Intranet. (71A-1.019(26))<br />
(4) Deceiving in order to appear as someone else's e-mail account (for example,<br />
misrepresent an e-mail address) or forging headers is prohibited. Capturing, altering, and<br />
retransmitting a communication stream in a way that misleads the recipient is prohibited.<br />
(71A-1.019(26))<br />
(5) Solicitations for activities that are not sponsored by the State or the Department.<br />
This includes, but is not limited to, the advertising or sale <strong>of</strong> personal property; announcing the sale <strong>of</strong><br />
cookies, candy, magazines, etc, on behalf <strong>of</strong> an organization or individual; or announcing personal<br />
events (weddings, showers, or events not related to work). Recognition <strong>of</strong> employment or retirement<br />
and ceremonies for employee award programs are State business related functions.<br />
(6) Sending or participation in any e-mail communication <strong>of</strong> unencrypted confidential<br />
client, employee, or Departmental data. (71A-1.019(25))<br />
(7) Further, using instant messaging, text messaging, SMS messaging or PIN<br />
messaging for Department business is prohibited<br />
2-3
December 1, 2011 <strong>CFOP</strong> <strong>50</strong>-<strong>22</strong><br />
c. Appropriate <strong>Use</strong> <strong>of</strong> Personal E-Mail.<br />
(1) During non-work hours, such as lunch break or before/after scheduled work hours,<br />
employees may access the personal email accounts such as Gmail or Yahoo for personal use by<br />
means <strong>of</strong> the Department network and Department information technology resources provided such<br />
use is not inappropriate as described herein. This privilege applies only to the browser-based e-mail<br />
functionality; employees shall not use Outlook, Outlook Express, Eudora, or any other e-mail clients to<br />
access non-Department e-mail.<br />
(2) Personal Internet e-mails sent from the Department’s network are permitted as long<br />
as they are brief, occasional, and not inappropriate. Personal e-mail use must not:<br />
(a) Interfere with the employee’s productivity or work performance.<br />
(b) Interfere or disrupt any other employee’s productivity or work performance.<br />
(c) Adversely affect the security or performance <strong>of</strong> the network.<br />
(d) Disclose any government or employer confidential data.<br />
(3) An employee should contact their Regional/Facilities <strong>Information</strong> Systems Security<br />
Officer if any personal or work-related e-mail is suspected <strong>of</strong> containing a virus.<br />
2-4
December 1, 2011 <strong>CFOP</strong> <strong>50</strong>-<strong>22</strong><br />
Chapter 3<br />
USE AND PROTECTION OF CONFIDENTIAL INFORMATION<br />
3-1. Purpose. This chapter establishes the Department’s policy for use and protection <strong>of</strong> confidential<br />
information including personally identifiable information from the Social Security Administration,<br />
protected health information, Federal tax information from the Internal Revenue Service, vital statistics<br />
information from the Department <strong>of</strong> Health, driver license information from the Department <strong>of</strong> Highway<br />
Safety and Motor Vehicles, and other confidential or protected information provided to Department<br />
employees to assist the public.<br />
3-2. Guiding Principles. The Department is guided by principles <strong>of</strong> common sense and good<br />
stewardship in this operating procedure. Employees are expected to help the people we serve, respect<br />
their rights to privacy and/or confidentiality, and adhere to State and Federal laws that protect those<br />
rights. Guided by these precepts, the Department sets the following direction for use <strong>of</strong> confidential or<br />
protected information:<br />
a. Employee responsibilities for maintaining confidentiality and security <strong>of</strong> information are<br />
defined in this operating procedure as well as required annual security awareness training and form<br />
CF 114 (available in DCF Forms). Employees are responsible for their use <strong>of</strong> confidential information<br />
and are expected to ask questions if they are uncertain about what they may access, how they may use<br />
information, or what they may share with co-workers, clients, and others. Employees are not to use<br />
confidential information for any purpose that conflicts with State policy (for example, checking<br />
information on family members, neighbors, acquaintances, or celebrities for purposes <strong>of</strong> personal<br />
curiosity, committing identity theft, or using information for other personal gain). The “browsing” <strong>of</strong><br />
confidential, sensitive, or personal information is prohibited and will result in disciplinary action up to<br />
and including dismissal.<br />
b. Employees shall notify their supervisor, <strong>Information</strong> Systems Security Officer, <strong>Information</strong><br />
Security Manager, or inspector general if they become aware <strong>of</strong> any actual or suspected misuse <strong>of</strong><br />
information.<br />
c. Employees who violate confidentiality and security <strong>of</strong> information requirements will be subject<br />
to disciplinary and/or legal action in accordance with Department policy and State and Federal law.<br />
3-3. Types <strong>of</strong> Protected <strong>Information</strong>. The Department maintains multiple interagency information<br />
sharing agreements and obtains confidential information from many agencies, including:<br />
a. Social Security Administration. THE DEPARTMENT functions as the <strong>Florida</strong> “state transfer<br />
component” to share social security information, including personally identifiable information (PII) with<br />
other State and Federal agencies that have agreements with the Social Security Administration.<br />
b. Internal Revenue Service. The Department receives Federal tax information (FTI) for<br />
eligibility determination purposes for individuals who apply for public assistance.<br />
c. Department <strong>of</strong> Health. The Department has access to vital statistics information (birth,<br />
death, and cause <strong>of</strong> death data) for child welfare, adult protective services, criminal justice coordination,<br />
and substance abuse and mental health.<br />
d. Department <strong>of</strong> Highway Safety and Motor Vehicles. The Department has access to driver<br />
license information, including photographs, for human resources, child protective investigations, adult<br />
protective investigations, and public assistance eligibility purposes.<br />
3-1
December 1, 2011 <strong>CFOP</strong> <strong>50</strong>-<strong>22</strong><br />
3-4. Conditions <strong>of</strong> <strong>Use</strong>. The general conditions for using this information are specified in law, the<br />
employee code <strong>of</strong> conduct, Department security operating procedure <strong>CFOP</strong> <strong>50</strong>-2, the Department<br />
security agreement, Security Awareness training, HIPAA training, and individual applications for system<br />
access. The specific conditions are specified in State and/or Federal law, the Department security<br />
agreement, annual IT Security Training, applications for access, and this operating procedure.<br />
Employees are responsible for ensuring that they understand and comply with these conditions.<br />
3-5. Release <strong>of</strong> <strong>Information</strong>. The system owner will make any decisions relating to the release and<br />
distribution <strong>of</strong> information in any form (e.g., on-line inquiry, printed reports, micr<strong>of</strong>iche, or any magnetic<br />
media). No information will be released without the system owner’s prior approval. In an emergency<br />
situation, the Inspector General’s <strong>of</strong>fice may direct the Department Chief <strong>Information</strong> Officer (CIO) to<br />
release information.<br />
3-6. Sanctions and Other Consequences for Misuse. Employees who unlawfully inspect, disclose, or<br />
otherwise misuse confidential information are subject to disciplinary action by the Department as<br />
described in the employee code <strong>of</strong> conduct, and are subject to civil and criminal penalties under<br />
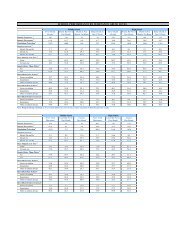
pertinent State and Federal laws. The table below shows the relevant State and Federal citations for<br />
misuse <strong>of</strong> information provided by the Internal Revenue Service, Social Security Administration,<br />
Department <strong>of</strong> Health, and Department <strong>of</strong> Highway Safety and Motor Vehicles:<br />
Data Source Data Type<br />
Social Security<br />
Administration<br />
Internal<br />
Revenue<br />
Service<br />
Department <strong>of</strong><br />
Health<br />
Department <strong>of</strong><br />
Highway Safety<br />
and Motor<br />
Vehicles<br />
Personally<br />
Identifiable<br />
<strong>Information</strong> (PII)<br />
Federal Tax<br />
<strong>Information</strong> (FTI)<br />
Department<br />
Sanctions<br />
• <strong>CFOP</strong> 60-5<br />
• <strong>CFOP</strong> 60-17<br />
• <strong>CFOP</strong> <strong>50</strong>-<strong>22</strong><br />
• <strong>CFOP</strong> 60-5<br />
• <strong>CFOP</strong> 60-17<br />
• <strong>CFOP</strong> <strong>50</strong>-<strong>22</strong><br />
Vital Statistics • <strong>CFOP</strong> 60-5<br />
• <strong>CFOP</strong> 60-17<br />
• <strong>CFOP</strong> <strong>50</strong>-<strong>22</strong><br />
Driver’s license<br />
information<br />
and/or<br />
photographs<br />
• <strong>CFOP</strong> 60-5<br />
• <strong>CFOP</strong> 60-17<br />
• <strong>CFOP</strong> <strong>50</strong>-<strong>22</strong><br />
3-2<br />
State Sanctions Federal Sanctions<br />
• Chapter 382,<br />
F.S.<br />
• Section<br />
119.10, F.S.<br />
• Section<br />
775.083, F.S.<br />
• Privacy Act <strong>of</strong> 1974 (5<br />
USC 552a) as amended<br />
by the Computer Matching<br />
and Privacy Protection Act<br />
<strong>of</strong> 1988<br />
• Federal <strong>Information</strong><br />
Security Management Act<br />
<strong>of</strong> 2002 (44 USC sections<br />
3541 et seq.)<br />
• IRC Sections 7431<br />
• IRC Section 6103 (l) (7)<br />
• IRC Sections 7213 and<br />
7213A, 18 USC Section<br />
1030 (a) (2)<br />
• IRC Section 7431<br />
• 45 CFR, Part 46 (Human<br />
Subjects Research)<br />
• Health <strong>Information</strong><br />
Portability and<br />
Accountability Act, or other<br />
sections.<br />
• Driver Privacy Protection<br />
Act (DPPA) (18 USC<br />
sections 2721 et seq.)