Global Phishing Survey: Trends and Domain Name Use in 2H2012
Global Phishing Survey: Trends and Domain Name Use in 2H2012
Global Phishing Survey: Trends and Domain Name Use in 2H2012
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
<strong>Global</strong> <strong>Phish<strong>in</strong>g</strong> <strong>Survey</strong> <strong>2H2012</strong>:<br />
<strong>Trends</strong> <strong>and</strong> <strong>Doma<strong>in</strong></strong> <strong>Name</strong> <strong>Use</strong><br />
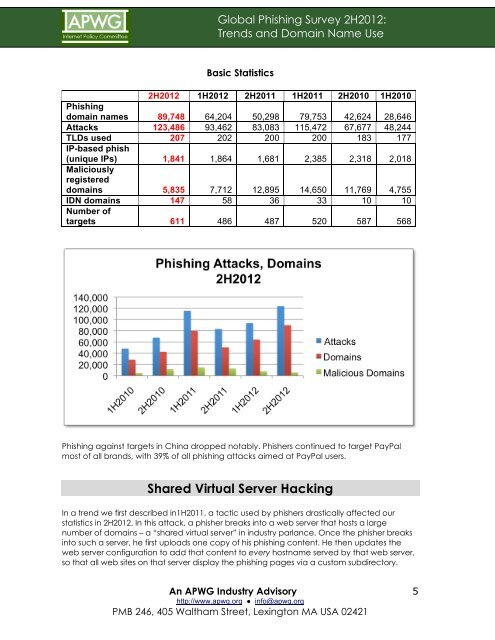
Basic Statistics<br />
<strong>2H2012</strong> 1H2012 2H2011 1H2011 2H2010 1H2010<br />
<strong>Phish<strong>in</strong>g</strong><br />
doma<strong>in</strong> names 89,748 64,204 50,298 79,753 42,624 28,646<br />
Attacks 123,486 93,462 83,083 115,472 67,677 48,244<br />
TLDs used<br />
IP-based phish<br />
207 202 200 200 183 177<br />
(unique IPs)<br />
Maliciously<br />
registered<br />
1,841 1,864 1,681 2,385 2,318 2,018<br />
doma<strong>in</strong>s 5,835 7,712 12,895 14,650 11,769 4,755<br />
IDN doma<strong>in</strong>s<br />
Number of<br />
147 58 36 33 10 10<br />
targets 611 486 487 520 587 568<br />
<strong>Phish<strong>in</strong>g</strong> aga<strong>in</strong>st targets <strong>in</strong> Ch<strong>in</strong>a dropped notably. Phishers cont<strong>in</strong>ued to target PayPal<br />
most of all br<strong>and</strong>s, with 39% of all phish<strong>in</strong>g attacks aimed at PayPal users.<br />
Shared Virtual Server Hack<strong>in</strong>g<br />
In a trend we first described <strong>in</strong>1H2011, a tactic used by phishers drastically affected our<br />
statistics <strong>in</strong> <strong>2H2012</strong>. In this attack, a phisher breaks <strong>in</strong>to a web server that hosts a large<br />
number of doma<strong>in</strong>s – a “shared virtual server” <strong>in</strong> <strong>in</strong>dustry parlance. Once the phisher breaks<br />
<strong>in</strong>to such a server, he first uploads one copy of his phish<strong>in</strong>g content. He then updates the<br />
web server configuration to add that content to every hostname served by that web server,<br />
so that all web sites on that server display the phish<strong>in</strong>g pages via a custom subdirectory.<br />
An APWG Industry Advisory<br />
http://www.apwg.org ● <strong>in</strong>fo@apwg.org<br />
PMB 246, 405 Waltham Street, Lex<strong>in</strong>gton MA USA 02421<br />
5