Global Phishing Survey: Trends and Domain Name Use in 2H2012
Global Phishing Survey: Trends and Domain Name Use in 2H2012
Global Phishing Survey: Trends and Domain Name Use in 2H2012
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
<strong>Global</strong> <strong>Phish<strong>in</strong>g</strong> <strong>Survey</strong> <strong>2H2012</strong>:<br />
<strong>Trends</strong> <strong>and</strong> <strong>Doma<strong>in</strong></strong> <strong>Name</strong> <strong>Use</strong><br />
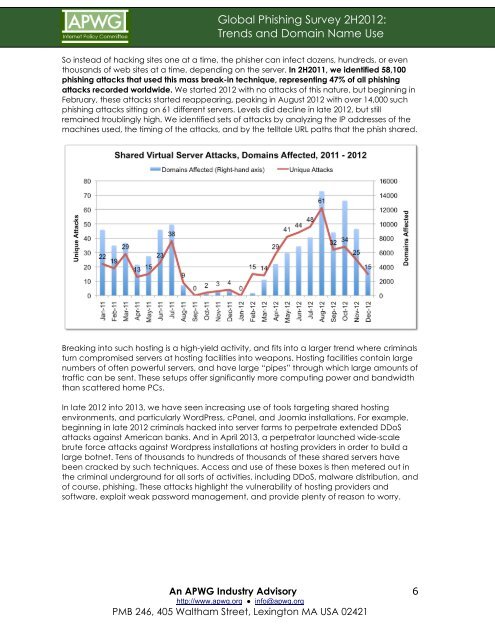
So <strong>in</strong>stead of hack<strong>in</strong>g sites one at a time, the phisher can <strong>in</strong>fect dozens, hundreds, or even<br />
thous<strong>and</strong>s of web sites at a time, depend<strong>in</strong>g on the server. In 2H2011, we identified 58,100<br />
phish<strong>in</strong>g attacks that used this mass break-<strong>in</strong> technique, represent<strong>in</strong>g 47% of all phish<strong>in</strong>g<br />
attacks recorded worldwide. We started 2012 with no attacks of this nature, but beg<strong>in</strong>n<strong>in</strong>g <strong>in</strong><br />
February, these attacks started reappear<strong>in</strong>g, peak<strong>in</strong>g <strong>in</strong> August 2012 with over 14,000 such<br />
phish<strong>in</strong>g attacks sitt<strong>in</strong>g on 61 different servers. Levels did decl<strong>in</strong>e <strong>in</strong> late 2012, but still<br />
rema<strong>in</strong>ed troubl<strong>in</strong>gly high. We identified sets of attacks by analyz<strong>in</strong>g the IP addresses of the<br />
mach<strong>in</strong>es used, the tim<strong>in</strong>g of the attacks, <strong>and</strong> by the telltale URL paths that the phish shared.<br />
Break<strong>in</strong>g <strong>in</strong>to such host<strong>in</strong>g is a high-yield activity, <strong>and</strong> fits <strong>in</strong>to a larger trend where crim<strong>in</strong>als<br />
turn compromised servers at host<strong>in</strong>g facilities <strong>in</strong>to weapons. Host<strong>in</strong>g facilities conta<strong>in</strong> large<br />
numbers of often powerful servers, <strong>and</strong> have large “pipes” through which large amounts of<br />
traffic can be sent. These setups offer significantly more comput<strong>in</strong>g power <strong>and</strong> b<strong>and</strong>width<br />
than scattered home PCs.<br />
In late 2012 <strong>in</strong>to 2013, we have seen <strong>in</strong>creas<strong>in</strong>g use of tools target<strong>in</strong>g shared host<strong>in</strong>g<br />
environments, <strong>and</strong> particularly WordPress, cPanel, <strong>and</strong> Joomla <strong>in</strong>stallations. For example,<br />
beg<strong>in</strong>n<strong>in</strong>g <strong>in</strong> late 2012 crim<strong>in</strong>als hacked <strong>in</strong>to server farms to perpetrate extended DDoS<br />
attacks aga<strong>in</strong>st American banks. And <strong>in</strong> April 2013, a perpetrator launched wide-scale<br />
brute force attacks aga<strong>in</strong>st Wordpress <strong>in</strong>stallations at host<strong>in</strong>g providers <strong>in</strong> order to build a<br />
large botnet. Tens of thous<strong>and</strong>s to hundreds of thous<strong>and</strong>s of these shared servers have<br />
been cracked by such techniques. Access <strong>and</strong> use of these boxes is then metered out <strong>in</strong><br />
the crim<strong>in</strong>al underground for all sorts of activities, <strong>in</strong>clud<strong>in</strong>g DDoS, malware distribution, <strong>and</strong><br />
of course, phish<strong>in</strong>g. These attacks highlight the vulnerability of host<strong>in</strong>g providers <strong>and</strong><br />
software, exploit weak password management, <strong>and</strong> provide plenty of reason to worry.<br />
An APWG Industry Advisory<br />
http://www.apwg.org ● <strong>in</strong>fo@apwg.org<br />
PMB 246, 405 Waltham Street, Lex<strong>in</strong>gton MA USA 02421<br />
6