Detecting and Defending against Malicious Attacks in the iTrust ...
Detecting and Defending against Malicious Attacks in the iTrust ...
Detecting and Defending against Malicious Attacks in the iTrust ...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
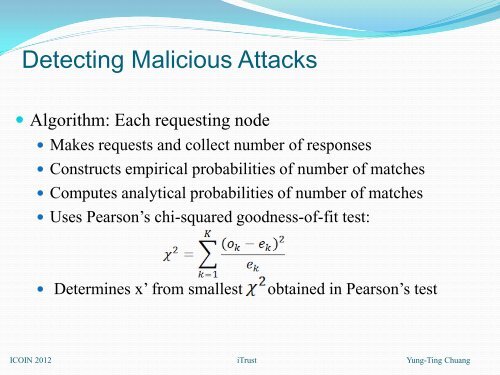
<strong>Detect<strong>in</strong>g</strong> <strong>Malicious</strong> <strong>Attacks</strong><br />
Algorithm: Each request<strong>in</strong>g node<br />
Makes requests <strong>and</strong> collect number of responses<br />
Constructs empirical probabilities of number of matches<br />
Computes analytical probabilities of number of matches<br />
Uses Pearson’s chi-squared goodness-of-fit test:<br />
Determ<strong>in</strong>es x’ from smallest obta<strong>in</strong>ed <strong>in</strong> Pearson’s test<br />
ICOIN 2012 <strong>iTrust</strong> Yung-T<strong>in</strong>g Chuang