Y om T o v Sheni Yom Tov Sheni - Chidushei Torah@NDS
Y om T o v Sheni Yom Tov Sheni - Chidushei Torah@NDS
Y om T o v Sheni Yom Tov Sheni - Chidushei Torah@NDS
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
Y<strong>om</strong> <strong>Tov</strong> <strong>Sheni</strong><br />
16<br />
messenger was able to reach within 10 days for Tishrei and 14 days<br />
for Nissan. Another problem the use of messengers presented fr<strong>om</strong><br />
the security standpoint was their susceptibility to bribery. Such a<br />
case was documented in the Talmud 23 . As a result, the sages gave<br />
the messengers a written certificate fr<strong>om</strong> the Beit Din to prove their<br />
authenticity to the towns they reached 24 .<br />
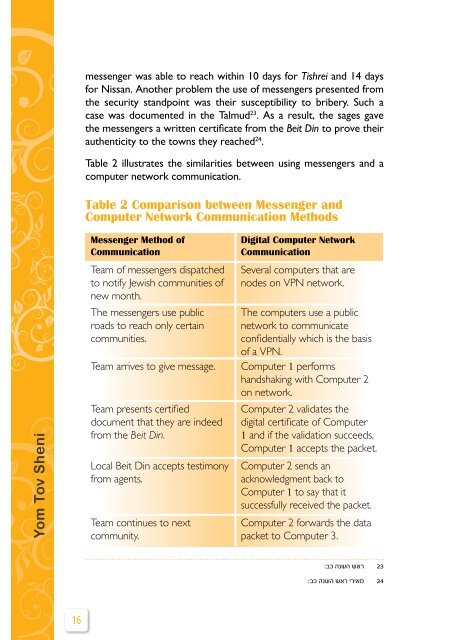
Table 2 illustrates the similarities between using messengers and a<br />
c<strong>om</strong>puter network c<strong>om</strong>munication.<br />
Table 2 C<strong>om</strong>parison between Messenger and<br />
C<strong>om</strong>puter Network C<strong>om</strong>munication Methods<br />
Messenger Method of<br />
C<strong>om</strong>munication<br />
Team of messengers dispatched<br />
to notify Jewish c<strong>om</strong>munities of<br />
new month.<br />
The messengers use public<br />
roads to reach only certain<br />
c<strong>om</strong>munities.<br />
Digital C<strong>om</strong>puter Network<br />
C<strong>om</strong>munication<br />
Several c<strong>om</strong>puters that are<br />
nodes on VPN network.<br />
The c<strong>om</strong>puters use a public<br />
network to c<strong>om</strong>municate<br />
confidentially which is the basis<br />
of a VPN.<br />
Team arrives to give message. C<strong>om</strong>puter 1 performs<br />
handshaking with C<strong>om</strong>puter 2<br />
on network.<br />
Team presents certified<br />
document that they are indeed<br />
fr<strong>om</strong> the Beit Din.<br />
Local Beit Din accepts testimony<br />
fr<strong>om</strong> agents.<br />
Team continues to next<br />
c<strong>om</strong>munity.<br />
C<strong>om</strong>puter 2 validates the<br />
digital certificate of C<strong>om</strong>puter<br />
1 and if the validation succeeds,<br />
C<strong>om</strong>puter 1 accepts the packet.<br />
C<strong>om</strong>puter 2 sends an<br />
acknowledgment back to<br />
C<strong>om</strong>puter 1 to say that it<br />
successfully received the packet.<br />
C<strong>om</strong>puter 2 forwards the data<br />
packet to C<strong>om</strong>puter 3.<br />
:בכ הנשה שאר 23<br />
:בכ הנשה שאר יריאמ 24