sKyWIper (a.k.a. Flame a.k.a. Flamer): A complex ... - CrySyS Lab
sKyWIper (a.k.a. Flame a.k.a. Flamer): A complex ... - CrySyS Lab
sKyWIper (a.k.a. Flame a.k.a. Flamer): A complex ... - CrySyS Lab
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
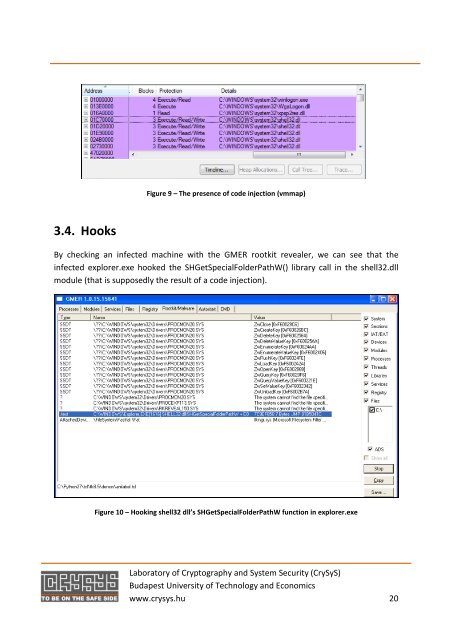
3.4. Hooks<br />
Figure 9 – The presence of code injection (vmmap)<br />
By checking an infected machine with the GMER rootkit revealer, we can see that the<br />
infected explorer.exe hooked the SHGetSpecialFolderPathW() library call in the shell32.dll<br />
module (that is supposedly the result of a code injection).<br />
Figure 10 – Hooking shell32 dll’s SHGetSpecialFolderPathW function in explorer.exe<br />
<strong>Lab</strong>oratory of Cryptography and System Security (<strong>CrySyS</strong>)<br />
Budapest University of Technology and Economics<br />
www.crysys.hu 20