report - Light Reading
report - Light Reading
report - Light Reading
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
SECURITY FROM 3GPP IMS TO TISPAN NGN<br />
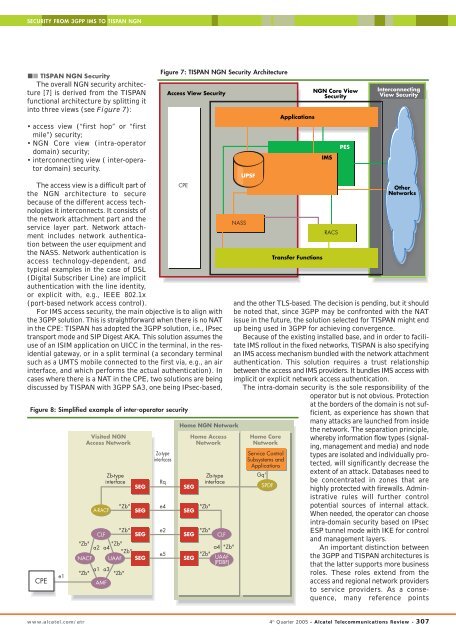
TISPAN NGN Security<br />
The overall NGN security architecture<br />
[7] is derived from the TISPAN<br />
functional architecture by splitting it<br />
into three views (see Figure 7):<br />
• access view (“first hop” or “first<br />
mile”) security;<br />
• NGN Core view (intra-operator<br />
domain) security;<br />
• interconnecting view ( inter-operator<br />
domain) security.<br />
Figure 7: TISPAN NGN Security Architecture<br />
Access View Security<br />
The access view is a difficult part of<br />
CPE<br />
the NGN architecture to secure<br />
because of the different access technologies<br />
it interconnects. It consists of<br />
the network attachment part and the<br />
service layer part. Network attachment<br />
includes network authentication<br />
between the user equipment and<br />
the NASS. Network authentication is<br />
access technology-dependent, and<br />
typical examples in the case of DSL<br />
(Digital Subscriber Line) are implicit<br />
authentication with the line identity,<br />
or explicit with, e.g., IEEE 802.1x<br />
(port-based network access control).<br />
For IMS access security, the main objective is to align with<br />
the 3GPP solution. This is straightforward when there is no NAT<br />
in the CPE: TISPAN has adopted the 3GPP solution, i.e., IPsec<br />
transport mode and SIP Digest AKA. This solution assumes the<br />
use of an ISIM application on UICC in the terminal, in the residential<br />
gateway, or in a split terminal (a secondary terminal<br />
such as a UMTS mobile connected to the first via, e.g., an air<br />
interface, and which performs the actual authentication). In<br />
cases where there is a NAT in the CPE, two solutions are being<br />
discussed by TISPAN with 3GPP SA3, one being IPsec-based,<br />
Figure 8: Simplified example of inter-operator security<br />
CPE<br />
e1<br />
Visited NGN<br />
Access Network<br />
A-RACF<br />
SEG<br />
SEG<br />
Za-type<br />
interfaces<br />
Home NGN Network<br />
SEG<br />
SEG<br />
Home Access<br />
Network<br />
"Zb"<br />
e2<br />
"Zb"<br />
CLF SEG<br />
SEG CLF<br />
"Zb" "Zb"<br />
a2 a4<br />
a4 "Zb"<br />
"Zb"<br />
e5<br />
"Zb"<br />
NACF UAAF SEG<br />
SEG UAAF<br />
(PDBF)<br />
"Zb" a1 a3 "Zb"<br />
AMF<br />
Zb-type<br />
interface<br />
"Zb"<br />
Rq<br />
e4<br />
Zb-type<br />
interface<br />
"Zb"<br />
NASS<br />
UPSF<br />
Applications<br />
Transfer Functions<br />
NGN Core View<br />
Security<br />
IMS<br />
RACS<br />
Other<br />
Networks<br />
and the other TLS-based. The decision is pending, but it should<br />
be noted that, since 3GPP may be confronted with the NAT<br />
issue in the future, the solution selected for TISPAN might end<br />
up being used in 3GPP for achieving convergence.<br />
Because of the existing installed base, and in order to facilitate<br />
IMS rollout in the fixed networks, TISPAN is also specifying<br />
an IMS access mechanism bundled with the network attachment<br />
authentication. This solution requires a trust relationship<br />
between the access and IMS providers. It bundles IMS access with<br />
implicit or explicit network access authentication.<br />
The intra-domain security is the sole responsibility of the<br />
operator but is not obvious. Protection<br />
at the borders of the domain is not sufficient,<br />
as experience has shown that<br />
Home Core<br />
Network<br />
Service Control<br />
Subsystems and<br />
Applications<br />
Gq'<br />
SPDF<br />
PES<br />
Interconnecting<br />
View Security<br />
many attacks are launched from inside<br />
the network. The separation principle,<br />
whereby information flow types (signaling,<br />
management and media) and node<br />
types are isolated and individually protected,<br />
will significantly decrease the<br />
extent of an attack. Databases need to<br />
be concentrated in zones that are<br />
highly protected with firewalls. Administrative<br />
rules will further control<br />
potential sources of internal attack.<br />
When needed, the operator can choose<br />
intra-domain security based on IPsec<br />
ESP tunnel mode with IKE for control<br />
and management layers.<br />
An important distinction between<br />
the 3GPP and TISPAN architectures is<br />
that the latter supports more business<br />
roles. These roles extend from the<br />
access and regional network providers<br />
to service providers. As a consequence,<br />
many reference points<br />
www.alcatel.com/atr 4 th Quarter 2005 - Alcatel Telecommunications Review - 307