LNCS 2820 - Ambiguity Resolution via Passive OS Fingerprinting
LNCS 2820 - Ambiguity Resolution via Passive OS Fingerprinting
LNCS 2820 - Ambiguity Resolution via Passive OS Fingerprinting
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
196 G. Taleck<br />
IDS<br />
Client<br />
Server<br />
SYN<br />
SYNACK<br />
fragment 1 (24 bytes at offset 0)<br />
AAAABBBBCCCC_attack_code<br />
fragment 2 (20 bytes at offset 12)<br />
DDDDEEEEFFFFGGGGHHHH<br />
?<br />
2 possible resolutions of ambiguity by the IDS:<br />
AAAABBBBCCCCDDDDEEEEFFFFGGGGHHHH<br />
(Last Policy)<br />
AAAABBBBCCCC_attack_codeGGGGHHHH<br />
(First Policy)<br />
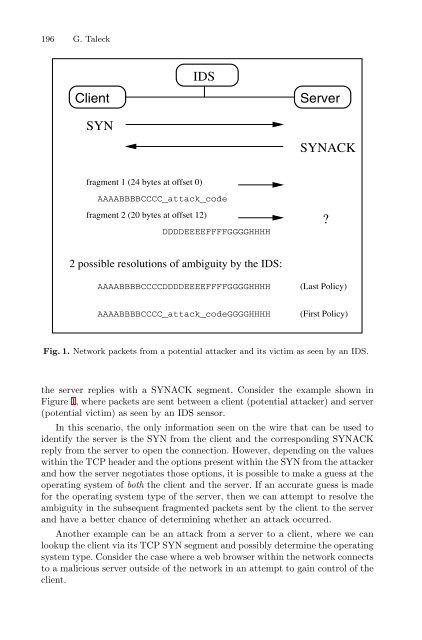
Fig. 1. Network packets from a potential attacker and its victim as seen by an IDS.<br />
the server replies with a SYNACK segment. Consider the example shown in<br />
Figure 1, where packets are sent between a client (potential attacker) and server<br />
(potential victim) as seen by an IDS sensor.<br />
In this scenario, the only information seen on the wire that can be used to<br />
identify the server is the SYN from the client and the corresponding SYNACK<br />
reply from the server to open the connection. However, depending on the values<br />
within the TCP header and the options present within the SYN from the attacker<br />
and how the server negotiates those options, it is possible to make a guess at the<br />
operating system of both the client and the server. If an accurate guess is made<br />
for the operating system type of the server, then we can attempt to resolve the<br />
ambiguity in the subsequent fragmented packets sent by the client to the server<br />
and have a better chance of determining whether an attack occurred.<br />
Another example can be an attack from a server to a client, where we can<br />
lookup the client <strong>via</strong> its TCP SYN segment and possibly determine the operating<br />
system type. Consider the case where a web browser within the network connects<br />
to a malicious server outside of the network in an attempt to gain control of the<br />
client.