ScanAlert - Report - Thane
ScanAlert - Report - Thane
ScanAlert - Report - Thane
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
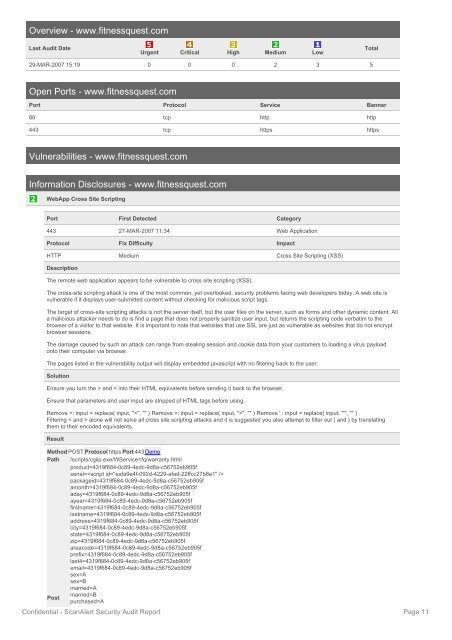
Overview - www.fitnessquest.com<br />
Last Audit Date<br />
Urgent Critical High Medium Low<br />
Total<br />
29-MAR-2007 15:19 0 0 0 2 3 5<br />
Open Ports - www.fitnessquest.com<br />
Port Protocol Service Banner<br />
80 tcp http http<br />
443 tcp https https<br />
Vulnerabilities - www.fitnessquest.com<br />
Information Disclosures - www.fitnessquest.com<br />
WebApp Cross Site Scripting<br />
Port First Detected Category<br />
443 27-MAR-2007 11:34 Web Application<br />
Protocol Fix Difficulty Impact<br />
HTTP Medium Cross Site Scripting (XSS)<br />
Description<br />
The remote web application appears to be vulnerable to cross site scripting (XSS).<br />
The cross-site scripting attack is one of the most common, yet overlooked, security problems facing web developers today. A web site is<br />
vulnerable if it displays user-submitted content without checking for malicious script tags.<br />
The target of cross-site scripting attacks is not the server itself, but the user files on the server, such as forms and other dynamic content. All<br />
a malicious attacker needs to do is find a page that does not properly sanitize user input, but returns the scripting code verbatim to the<br />
browser of a visitor to that website. It is important to note that websites that use SSL are just as vulnerable as websites that do not encrypt<br />
browser sessions.<br />
The damage caused by such an attack can range from stealing session and cookie data from your customers to loading a virus payload<br />
onto their computer via browser.<br />
The pages listed in the vulnerability output will display embedded javascript with no filtering back to the user.<br />
Solution<br />
Ensure you turn the > and < into their HTML equivalents before sending it back to the browser.<br />
Ensure that parameters and user input are stripped of HTML tags before using.<br />
Remove : input = replace( input, ">", "" ) Remove ' : input = replace( input, "'", "" )<br />
Filtering < and > alone will not solve all cross site scripting attacks and it is suggested you also attempt to filter out ( and ) by translating<br />
them to their encoded equivalents.<br />
Result<br />
Method POST Protocol https Port 443 Demo<br />
Path /scripts/cgiip.exe/WService=fq/warranty.html<br />
product=4319f684-0c89-4edc-9d8a-c56752eb905f<br />
serial=<br />
packageid=4319f684-0c89-4edc-9d8a-c56752eb905f<br />
amonth=4319f684-0c89-4edc-9d8a-c56752eb905f<br />
aday=4319f684-0c89-4edc-9d8a-c56752eb905f<br />
ayear=4319f684-0c89-4edc-9d8a-c56752eb905f<br />
firstname=4319f684-0c89-4edc-9d8a-c56752eb905f<br />
lastname=4319f684-0c89-4edc-9d8a-c56752eb905f<br />
address=4319f684-0c89-4edc-9d8a-c56752eb905f<br />
city=4319f684-0c89-4edc-9d8a-c56752eb905f<br />
state=4319f684-0c89-4edc-9d8a-c56752eb905f<br />
zip=4319f684-0c89-4edc-9d8a-c56752eb905f<br />
areacode=4319f684-0c89-4edc-9d8a-c56752eb905f<br />
prefix=4319f684-0c89-4edc-9d8a-c56752eb905f<br />
last4=4319f684-0c89-4edc-9d8a-c56752eb905f<br />
email=4319f684-0c89-4edc-9d8a-c56752eb905f<br />
sex=A<br />
sex=B<br />
married=A<br />
married=B<br />
Post<br />
purchased=A<br />
Confidential - <strong>ScanAlert</strong> Security Audit <strong>Report</strong><br />
Page 11