Security Automation - IAC - Defense Technical Information Center
Security Automation - IAC - Defense Technical Information Center
Security Automation - IAC - Defense Technical Information Center
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
include references to CVEs. By employing<br />
these SCAP standards, assets, events,<br />
and vulnerabilities can be quickly related<br />
to determine if configuration<br />
management modifications in the form<br />
of <strong>Information</strong> Assurance Vulnerability<br />
Alerts (IAVA) are needed.<br />
To realize this use case, the pilot<br />
identified authoritative data sources for<br />
vulnerabilities, assets, and events and<br />
then instrumented them with Web<br />
service interfaces to expose their data in<br />
accordance with CND data exchange<br />
standards. NIST’s National Vulnerability<br />
Database (NVD) provides vulnerability<br />
data. The Army’s Asset and Vulnerability<br />
Tracking Resource (A&VTR) provides<br />
asset and configuration data. The Navy’s<br />
Prometheus repository provides event<br />
data. Data from each of the sources is<br />
consumed and correlated within a<br />
lightweight Web-based CND workspace<br />
to provide authorized users visibility<br />
into the relationships between<br />
vulnerability, asset, and event data. The<br />
pilot correlates data from a variety of<br />
data sources and provides tailored views<br />
without manipulating the original data<br />
and without replicating the diverse data<br />
sets into a centralized repository.<br />
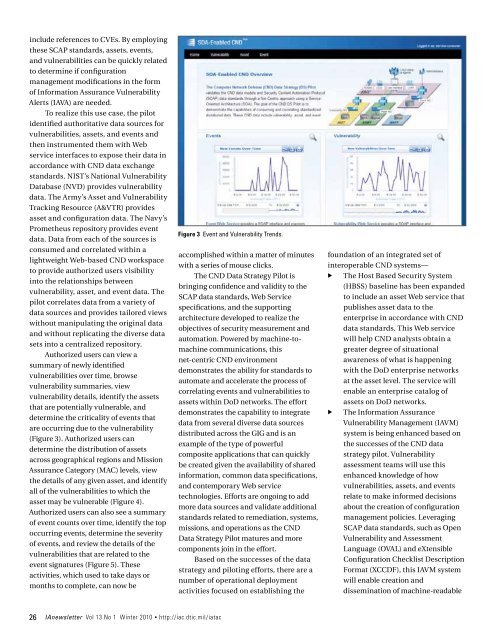
Authorized users can view a<br />
summary of newly identified<br />
vulnerabilities over time, browse<br />
vulnerability summaries, view<br />
vulnerability details, identify the assets<br />
that are potentially vulnerable, and<br />
determine the criticality of events that<br />
are occurring due to the vulnerability<br />
(Figure 3). Authorized users can<br />
determine the distribution of assets<br />
across geographical regions and Mission<br />
Assurance Category (MAC) levels, view<br />
the details of any given asset, and identify<br />
all of the vulnerabilities to which the<br />
asset may be vulnerable (Figure 4).<br />
Authorized users can also see a summary<br />
of event counts over time, identify the top<br />
occurring events, determine the severity<br />
of events, and review the details of the<br />
vulnerabilities that are related to the<br />
event signatures (Figure 5). These<br />
activities, which used to take days or<br />
months to complete, can now be<br />
Figure 3 Event and Vulnerability Trends.<br />
accomplished within a matter of minutes<br />
with a series of mouse clicks.<br />
The CND Data Strategy Pilot is<br />
bringing confidence and validity to the<br />
SCAP data standards, Web Service<br />
specifications, and the supporting<br />
architecture developed to realize the<br />
objectives of security measurement and<br />
automation. Powered by machine-tomachine<br />
communications, this<br />
net-centric CND environment<br />
demonstrates the ability for standards to<br />
automate and accelerate the process of<br />
correlating events and vulnerabilities to<br />
assets within DoD networks. The effort<br />
demonstrates the capability to integrate<br />
data from several diverse data sources<br />
distributed across the GIG and is an<br />
example of the type of powerful<br />
composite applications that can quickly<br />
be created given the availability of shared<br />
information, common data specifications,<br />
and contemporary Web service<br />
technologies. Efforts are ongoing to add<br />
more data sources and validate additional<br />
standards related to remediation, systems,<br />
missions, and operations as the CND<br />
Data Strategy Pilot matures and more<br />
components join in the effort.<br />
Based on the successes of the data<br />
strategy and piloting efforts, there are a<br />
number of operational deployment<br />
activities focused on establishing the<br />
foundation of an integrated set of<br />
interoperable CND systems—<br />
ff<br />
ff<br />
The Host Based <strong>Security</strong> System<br />
(HBSS) baseline has been expanded<br />
to include an asset Web service that<br />
publishes asset data to the<br />
enterprise in accordance with CND<br />
data standards. This Web service<br />
will help CND analysts obtain a<br />
greater degree of situational<br />
awareness of what is happening<br />
with the DoD enterprise networks<br />
at the asset level. The service will<br />
enable an enterprise catalog of<br />
assets on DoD networks.<br />
The <strong>Information</strong> Assurance<br />
Vulnerability Management (IAVM)<br />
system is being enhanced based on<br />
the successes of the CND data<br />
strategy pilot. Vulnerability<br />
assessment teams will use this<br />
enhanced knowledge of how<br />
vulnerabilities, assets, and events<br />
relate to make informed decisions<br />
about the creation of configuration<br />
management policies. Leveraging<br />
SCAP data standards, such as Open<br />
Vulnerability and Assessment<br />
Language (OVAL) and eXtensible<br />
Configuration Checklist Description<br />
Format (XCCDF), this IAVM system<br />
will enable creation and<br />
dissemination of machine-readable<br />
26 IAnewsletter Vol 13 No 1 Winter 2010 • http://iac.dtic.mil/iatac