TETRA Security
TETRA Security
TETRA Security
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
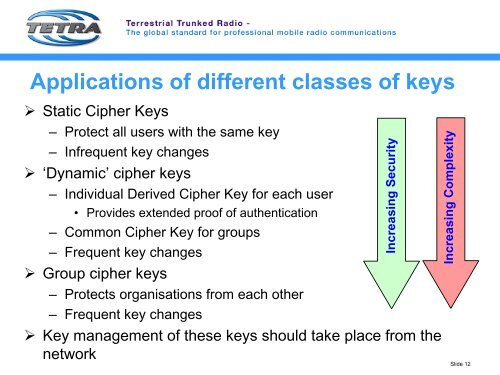
Applications of different classes of keys<br />
‣ Static Cipher Keys<br />
– Protect all users with the same key<br />
– Infrequent key changes<br />
‣ ‘Dynamic’ cipher keys<br />
– Individual Derived Cipher Key for each user<br />
• Provides extended proof of authentication<br />
– Common Cipher Key for groups<br />
– Frequent key changes<br />
‣ Group cipher keys<br />
– Protects organisations from each other<br />
– Frequent key changes<br />
‣ Key management of these keys should take place from the<br />
network<br />
Increasing <strong>Security</strong><br />
Increasing Complexity<br />
Slide 12