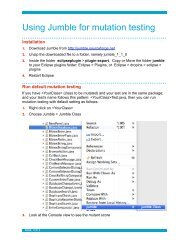
reAJAX - FBK | SE - Fondazione Bruno Kessler
reAJAX - FBK | SE - Fondazione Bruno Kessler
reAJAX - FBK | SE - Fondazione Bruno Kessler
- No tags were found...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
eAJAX: First-Use Example and Tutorial<br />
by Alessandro Marchetto<br />
<strong>reAJAX</strong> is a Mozilla Firefox extension available at http://selab.fbk.eu/marchetto/tools/ajax/<strong>reAJAX</strong>.<br />
<strong>reAJAX</strong> is a research tool. Hence, it is a prototype tool that is continuously under maintenance and<br />
evolution. In the rest of this tutorial we try to explain how to use the tool by means of a practical<br />
example.<br />
Other similar Firefox extensions can be found at https://addons.mozilla.org/it/firefox/ while details,<br />
tutorial and examples about Firefox extension development and usage can be found at<br />
https://developer.mozilla.org/en/Extensions. It is important to notice that these extensions (i.e.,<br />
included <strong>reAJAX</strong>) can be used only with the Mozilla browser.<br />
<strong>reAJAX</strong> is distributed as a unique .XPI executable file. An .XPI file is a “special” container of files<br />
organized in an ad-hoc structure that is recognized by the Mozilla browser.Figure 1 shows the<br />
structure of the XPI file of <strong>reAJAX</strong>. In the main directory reajax2 there is the chrome directory that<br />
is organized into: content, locale and skin. The most relevant directory is content, it contains the<br />
logic of the extension in terms of HTML and Javascript file while additional RDF are used to<br />
configure the extension and to transmit to the browser configuration information about the software.<br />
Figure 1: Structure of a Mozilla Firefox Extension<br />
To install a Firefox extension such as <strong>reAJAX</strong> it is sufficient to follow three main steps: 1. open a<br />
new browser window; 2. drop the .XPI file into the window; and 3. follow the few and simple steps<br />
guided by some browser wizard used by the Firefox browser to install all the extensions and to be<br />
able to manage and execute them. Please, note that in the first installation of <strong>reAJAX</strong>, we suggest to<br />
try <strong>reAJAX</strong> into a new user profiler of the browser and install <strong>reAJAX</strong> into the standard profile just<br />
when we are sure that no conflict or problem are related to <strong>reAJAX</strong> and the curent browser<br />
configuration and version. When the <strong>reAJAX</strong> installation has been finished the extension will<br />
appear in the list of “Added Components” of the menu “Tools” of the Mozilla browser.<br />
<strong>reAJAX</strong> has been tested with different version of Mozilla 2.x – 3.x in both Windows (2000, XP)<br />
and Linux like operating systems and no problems happen.
When <strong>reAJAX</strong> has been correctly installed, the browser list of “Tools” contains <strong>reAJAX</strong> and it<br />
provides the following set of commands:<br />
1. MutatorsInspectos<br />
2. ABS<br />
3. Tracer<br />
6. BuildFSM<br />
7. Close<br />
While the Tracer has 2 sub-menu commands:<br />
4. Tracer Start<br />
5. Tracer Stop<br />
In the rest of this tutorial we show a scenario of the <strong>reAJAX</strong> use. The scenario is based on the Cart<br />
application implementation (source code are downloadable at the <strong>reAJAX</strong> page) and it is used to<br />
show how to execute all main features of <strong>reAJAX</strong> to analyze a Web application and generate its<br />
Finite State Machine. <strong>reAJAX</strong> can be applied to fully and single-page AJAX Web application, to<br />
Web applications that partially use AJAX (e.g., in part of this GUI); and also in conventional (e.g.,<br />
not AJAX-based) application. However, we recall that its natural use and its main goal are to<br />
analyze full-AJAX application.<br />
The first step of each <strong>reAJAX</strong> execution consists in loading the stating page of the target application<br />
into the Mozilla browser enriched with the <strong>reAJAX</strong> extension. Then the execution scenario can<br />
proceed identifying the following five main steps:<br />
1a. Section of the inspector elements in the DOM of the application page;<br />
1b Selection of the GUI-events that must be monitorized since they can change the<br />
state of the selected mutator elements in the pages;<br />
2 For each inspector, definition of its abstraction function (ABS) that will be used by<br />
<strong>reAJAX</strong> to record the value reached at runtime by each inspector;<br />
3 Application execution tracing by starting and stopping the <strong>reAJAX</strong> tracer;<br />
4 Construction of the Finite State Machine (FSM) by using the collected execution<br />
traces;<br />
5 (extra <strong>reAJAX</strong>) Visualization of the generated FSM in the DOTTY<br />
( http://www.graphviz.org/ ) viewer;<br />
Notice that the steps 1a, 1b, 2, and 3 can be iteratively executed (also in different sequences) and<br />
that it is possible to go through these different steps and go back without any kind of problem<br />
and/or limitation and in which moment.
Step 1a. Section of the inspector elements in the DOM of the application page<br />
First of all, we recall that an inspector element is an element of the DOM structure of an HTML<br />
page (like a list, a field, an area, a graphical element, a container element, etc.) that is related to the<br />
application domain and so that represents a state variable for the application state. Those inspector<br />
elements must be selected by the user by means of the DOM-viewer provided by <strong>reAJAX</strong>. These<br />
inspectors will be the DOM element that will be monitorized and evaluated at runtime by <strong>reAJAX</strong><br />
to infer the state of the application.<br />
With the aim of selecting the set of inspectors, <strong>reAJAX</strong> provides an enriched DOM-viewer. The<br />
viewer is a software module that add to the current page (of the target application) a draggable<br />
popup in which <strong>reAJAX</strong> shows the complete list of HTML elements of the current page (and<br />
ordered list of HTML tag related to the element of the DOM structure of the target page). Figure<br />
Figure 2 shows the popup with the list of HTML element (, etc. in the left of the popup) for<br />
the starting page of Cart. To focus and simplify the management of this list, <strong>reAJAX</strong> provides a<br />
filter capability feature that can be used to filter out some non-relevant DOM elements. By using<br />
the filter, the user can limit the type of the element shown in the DOM list by the DOM-viewer. A<br />
list of HTML tag (e.g., “button, input, a”) can be used to filter the viewer element while by using<br />
the “*” all elements of the current will be viewed in the list at each moment. In the figure, a <br />
filter has been applied to the current page.<br />
When the user passes the mouse over an element of the DOM list (see Figure 2 in which a <br />
element is highlighted), <strong>reAJAX</strong> highlights the graphical element in the target page by means of a<br />
dashed red square (see Figure 2 what happens for the selected example). So that the user<br />
can see in the current page the element and its position. When the highlighted element is selected<br />
(by using a mouse click) by the user some information (mainly its id/name and its XPath address in<br />
the DOM page) are stored in the list of inspector elements for the current page. The list is shown in<br />
the right part of the <strong>reAJAX</strong> popup. The list of selected inspectors can be stored at each time in a<br />
file so that <strong>reAJAX</strong> can reload that inspector list at each moment without the needs to re-applying<br />
all the selection<br />
Figure 2: Mutators Selection for Cart
Step 1b Selection of the GUI-events that must be monitorized since they can change the state<br />
of the selected mutator elements in the pa<br />
Section of the events in the GUI of the target application that can have some impact in the state of<br />
the inspector elements selected in the previous steps. Those events are called mutator elements for<br />
the target application. The selection of these elements is performed at the same time, by means of<br />
the same DOM-viewer and in the same way in which the inspector elements are selected. The<br />
difference is that when selecting a mutator element, the user is asked to click on the mouse three<br />
times in the selected element (i.e., one click to define the current element as an inspector; two clicks<br />
to define it as inspector and mutator, at the same time; and three clicks to select it as mutator).<br />
Step 2 For each inspector, definition of its abstraction function (ABS) that will be used by<br />
<strong>reAJAX</strong> to record the value reached at runtime by each inspector;<br />
When selected inspector and mutator elements, the next step consists in identifying the correct<br />
abstraction function for each selected inspector. Notice that at least one inspector and one mutator<br />
must be selected otherwise <strong>reAJAX</strong> does not allow the user to define the abstraction function and so<br />
trace application executions. If the user starts the ABS definition by means of the related <strong>reAJAX</strong><br />
menu, for each selected inspector, <strong>reAJAX</strong> shows a popup with two different areas:<br />
- left: it contains the list of the inspectors selected for which an abstraction must be<br />
defined. Notice that a checkbox is used by <strong>reAJAX</strong> to show whether the abstraction<br />
function for a given inspector element has been defined;<br />
- right: it contains several different types of abstraction functions (see below) provided by<br />
<strong>reAJAX</strong> and that can be customized by the user (note that this list of abstraction<br />
functions can be obtained by means of a double-click on one of the inspectors shown in<br />
the left side of this popup).<br />
Currently, <strong>reAJAX</strong> provides the following set of functions:<br />
NotNull: an element of a page exists at a given time (e.g., items of a list can<br />
be added at runtime);<br />
NotEmpty: an element is not empty at a given time (e.g., consider the text value of an<br />
element );<br />
Constant-value: strings and numbers in a textual field can assume a specific value or a<br />
range of specific values (e.g., a number can be greater or less than a constant).<br />
NumChildBool: true when an element contains a number (greater than 0) of other<br />
embedded elements (children in the DOM) of a specific type (e.g., a contains<br />
one or more rows);<br />
NumChildAbsolute: an element contains a given number of embedded elements of a<br />
specific type (e.g., a contains zero/one/two/etc. rows);<br />
RegularExpressionRules: the value of an element (e.g., its content or text) matches a<br />
regular expression. <strong>reAJAX</strong> allows to define an ordered set of pairs ``regular expression -<br />
abstract state value'' for each element of a page. If the value of an element matches one of<br />
the defined regular expressions its corresponding state-value is used to represent the<br />
current state of the element (e.g., the text into a can be composed only by<br />
lowercase letters ``[a-z]*'').<br />
For each type of inspector (i.e., HTML element) that can compose a Web page, a predefined<br />
abstraction is pre-configured by <strong>reAJAX</strong>. In this default configuration, the abstraction function can<br />
be used by the user without any additional effort. In the following we summarize the most frequent<br />
element types and their default abstraction provided by <strong>reAJAX</strong>:
DIV, SPAN, P, TEXTAREA, LI, and INPUT(of type text) NotEmpty<br />
FORM NumChildBool()<br />
OL, UL NumChildBool()<br />
TABLE NumChildBool()<br />
TR NumChildBool()<br />
<strong>SE</strong>LECT NumChildBool()<br />
A, INPUT(of type button), IMG}, and other NotNull<br />
Notice that the abstraction setting can be done iteratively when the user selects inspectors and<br />
mutators. Furthermore, at each time, the defined abstraction function can be saved in a<br />
configuration file that can be loaded in a second time.<br />
Figure 3 shows an instance of the abstraction function definition for the Cart application.<br />
Figure 3: Abstraction function definition for Cart
Step 3 Application execution tracing by starting and stopping the <strong>reAJAX</strong> tracer;<br />
When inspector and mutator elements are selected, the next step consists in activating the<br />
application execution instrumentation (it is highlighted by a <strong>reAJAX</strong> popup). Therefore, the next<br />
application execution will be traced and during this execution the state of the application will be<br />
recorded in a log file. To trace more executions into different log files it is sufficient to start and<br />
stop the <strong>reAJAX</strong> tracing (respectively) before and after each application execution. Figure 3 shows<br />
the activation of the <strong>reAJAX</strong> tracer for the Cart application.<br />
Figure 4: Cart execution tracing<br />
The execution tracing starts when the <strong>reAJAX</strong> tracer is activated and it stops when the same is<br />
deactivated (by means of the <strong>reAJAX</strong> menu). Each execution trace is stored in a log file such as the<br />
following (it is one execution of the Cart application):<br />
ONLOAD:__:HTTP://LOCALHOST:8080/CART/:__:[<br />
/HTML/BODY/DIV/DIV/UL[@ID='CONTENTS']=0 ;__;<br />
/HTML/BODY/DIV/DIV/SPAN[@ID='TOTAL']=NOTEMPTYMATCH<br />
]<br />
CLICK:__:CHA001_REM:__:[<br />
/HTML/BODY/DIV/DIV/UL[@ID='CONTENTS']=0 ;__;<br />
/HTML/BODY/DIV/DIV/SPAN[@ID='TOTAL']=NOTEMPTYMATCH<br />
]<br />
ONUNLOAD:__:HTTP://LOCALHOST:8080/CART/:__:[<br />
/HTML/BODY/DIV/DIV/UL[@ID='CONTENTS']=0 ;__;<br />
/HTML/BODY/DIV/DIV/SPAN[@ID='TOTAL']=NOTEMPTYMATCH<br />
]<br />
Each row of the log file contains three types of information (separated from special characters<br />
“:__:“ according to the following pattern:<br />
- executed event (e.g., click of the rem button);<br />
- id/name of the event or its Xpath address in the page (e.g., id of the activated button);<br />
- state of the page according to the selected GUI inspectors (e.g., the list of items in the cart).
Step 4 Construction of the Finite State Machine (FSM) by using the collected execution traces;<br />
By using the collected execution traces, the user can ask to <strong>reAJAX</strong> to generate the related FSM<br />
that will be stored in a text file by the tool by using a graphical representation (the Dotty format<br />
http://www.graphviz.org/ ). For instance, a FSM recovered for the Cart application is:<br />
DIGRAPH FSM {<br />
NODE [STYLE=ROUNDED]<br />
ST0[SHAPE="RECORD",LABEL="{ ST0| }"];<br />
ST1[SHAPE="RECORD",LABEL="{ ST1| /HTML/BODY/DIV/DIV/UL[@ID='CONTENTS']=0 |<br />
/HTML/BODY/DIV/DIV/SPAN[@ID='TOTAL']=0 }"];<br />
ST2[SHAPE="RECORD",LABEL="{ ST2| /HTML/BODY/DIV/DIV/UL[@ID='CONTENTS']\>0 |<br />
/HTML/BODY/DIV/DIV/SPAN[@ID='TOTAL']\>0 }"];<br />
ST3[SHAPE="RECORD",LABEL="{ ST3| }"];<br />
ST0->ST1[ARROWHEAD="VEE" ,LABEL="ONLOAD_HTTP://LOCALHOST:8080/CART"];<br />
ST1->ST2[ARROWHEAD="VEE" ,LABEL="ADD"];<br />
ST2->ST2[ARROWHEAD="VEE" ,LABEL="ADD"];<br />
ST1->ST1[ARROWHEAD="VEE" ,LABEL="EMPTY"];<br />
ST2->ST1[ARROWHEAD="VEE" ,LABEL="EMPTY"];<br />
ST2->ST1[ARROWHEAD="VEE" ,LABEL="REM"];<br />
ST2->ST2[ARROWHEAD="VEE" ,LABEL="REM"];<br />
ST2->ST3[ARROWHEAD="VEE" ,LABEL="ONUNLOAD_HTTP://LOCALHOST:8080/CART"];<br />
ST1->ST3[ARROWHEAD="VEE" ,LABEL="ONUNLOAD_HTTP://LOCALHOST:8080/CART"];<br />
}<br />
Step 5 (extra <strong>reAJAX</strong>) Visualization of the generated FSM in the DOTTY format<br />
The generated FSM can be visualized by using a Dotty-viewer. For instance, Figure 5 shows an<br />
example of FSM generated for the Cart application.<br />
Figure 5: FSM for Cart
Software License Agreement (BSD License)<br />
Copyright (c) 2009, <strong>Fondazione</strong> <strong>Bruno</strong> <strong>Kessler</strong>: Alessandro Marchetto<br />
All rights reserved.<br />
Redistribution and use of this software in source and binary forms, with or without modification,<br />
are permitted provided that the following conditions are met:<br />
* Redistributions of source code must retain the above copyright notice, this list of conditions and<br />
the following disclaimer.<br />
* Redistributions in binary form must reproduce the above copyright notice, this list of conditions<br />
and the following disclaimer in the documentation and/or other materials provided with the<br />
distribution.<br />
* Neither the name of <strong>FBK</strong> nor the names of its contributors may be used to endorse or promote<br />
products derived from this software without specific prior written permission of the authors.<br />
THIS SOFTWARE IS PROVIDED BY THE COPYRIGHT HOLDERS AND CONTRIBUTORS<br />
"AS IS" AND ANY EXPRESS OR IMPLIED WARRANTIES, INCLUDING, BUT NOT<br />
LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR<br />
A PARTICULAR PURPO<strong>SE</strong> ARE DISCLAIMED. IN NO EVENT SHALL THE COPYRIGHT<br />
OWNER OR CONTRIBUTORS BE LIABLE FOR ANY DIRECT, INDIRECT, INCIDENTAL,<br />
SPECIAL, EXEMPLARY, OR CON<strong>SE</strong>QUENTIAL DAMAGES (INCLUDING, BUT NOT<br />
LIMITED TO, PROCUREMENT OF SUBSTITUTE GOODS OR <strong>SE</strong>RVICES; LOSS OF U<strong>SE</strong>,<br />
DATA, OR PROFITS; OR BUSINESS INTERRUPTION) HOWEVER CAU<strong>SE</strong>D AND ON ANY<br />
THEORY OF LIABILITY, WHETHER IN CONTRACT, STRICT LIABILITY, OR TORT<br />
(INCLUDING NEGLIGENCE OR OTHERWI<strong>SE</strong>) ARISING IN ANY WAY OUT OF THE U<strong>SE</strong><br />
OF THIS SOFTWARE, EVEN IF ADVI<strong>SE</strong>D OF THE POSSIBILITY OF SUCH DAMAGE.<br />
© 2010 Marchetto Alessandro, <strong>Fondazione</strong> <strong>Bruno</strong> <strong>Kessler</strong>