Joint Publication 3-13, Information Operations - The Global ...
Joint Publication 3-13, Information Operations - The Global ...
Joint Publication 3-13, Information Operations - The Global ...
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
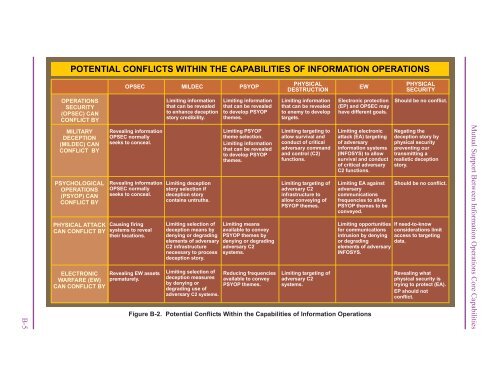
POTENTIAL CONFLICTS WITHIN THE CAPABILITIES OF INFORMATION OPERATIONS<br />
OPSEC MILDEC<br />
PSYOP<br />
PHYSICAL<br />
EW<br />
DESTRUCTION<br />
PHYSICAL<br />
SECURITY<br />
OPERATIONS<br />
SECURITY<br />
(OPSEC) CAN<br />
CONFLICT BY<br />
Limiting information<br />
that can be revealed<br />
to enhance deception<br />
story credibility.<br />
Limiting information<br />
that can be revealed<br />
to develop PSYOP<br />
themes.<br />
Limiting information<br />
that can be revealed<br />
to enemy to develop<br />
targets.<br />
Electronic protection<br />
(EP) and OPSEC may<br />
have different goals.<br />
Should be no conflict.<br />
B-5<br />
MILITARY<br />
DECEPTION<br />
(MILDEC) CAN<br />
CONFLICT BY<br />
PSYCHOLOGICAL<br />
OPERATIONS<br />
(PSYOP) CAN<br />
CONFLICT BY<br />
PHYSICAL ATTACK<br />
CAN CONFLICT BY<br />
ELECTRONIC<br />
WARFARE (EW)<br />
CAN CONFLICT BY<br />
Revealing information<br />
OPSEC normally<br />
seeks to conceal.<br />
Revealing information<br />
OPSEC normally<br />
seeks to conceal.<br />
Causing firing<br />
systems to reveal<br />
their locations.<br />
Revealing EW assets<br />
prematurely.<br />
Limiting deception<br />
story selection if<br />
deception story<br />
contains untruths.<br />
Limiting selection of<br />
deception means by<br />
denying or degrading<br />
elements of adversary<br />
C2 infrastructure<br />
necessary to process<br />
deception story.<br />
Limiting selection of<br />
deception measures<br />
by denying or<br />
degrading use of<br />
adversary C2 systems.<br />
Limiting PSYOP<br />
theme selection.<br />
Limiting information<br />
that can be revealed<br />
to develop PSYOP<br />
themes.<br />
Limiting means<br />
available to convey<br />
PSYOP themes by<br />
denying or degrading<br />
adversary C2<br />
systems.<br />
Reducing frequencies<br />
available to convey<br />
PSYOP themes.<br />
Limiting targeting to<br />
allow survival and<br />
conduct of critical<br />
adversary command<br />
and control (C2)<br />
functions.<br />
Limiting targeting of<br />
adversary C2<br />
infrastructure to<br />
allow conveying of<br />
PSYOP themes.<br />
Limiting targeting of<br />
adversary C2<br />
systems.<br />
Limiting electronic<br />
attack (EA) targeting<br />
of adversary<br />
information systems<br />
(INFOSYS) to allow<br />
survival and conduct<br />
of critical adversary<br />
C2 functions.<br />
Limiting EA against<br />
adversary<br />
communications<br />
frequencies to allow<br />
PSYOP themes to be<br />
conveyed.<br />
Limiting opportunities<br />
for communications<br />
intrusion by denying<br />
or degrading<br />
elements of adversary<br />
INFOSYS.<br />
Figure B-2. Potential Conflicts Within the Capabilities of <strong>Information</strong> <strong>Operations</strong><br />
Negating the<br />
deception story by<br />
physical security<br />
preventing our<br />
transmitting a<br />
realistic deception<br />
story.<br />
Should be no conflict.<br />
If need-to-know<br />
considerations limit<br />
access to targeting<br />
data.<br />
Revealing what<br />
physical security is<br />
trying to protect (EA).<br />
EP should not<br />
conflict.<br />
Mutual Support Between <strong>Information</strong> <strong>Operations</strong> Core Capabilities