Deadlocks The Deadlock Problem Bridge Crossing Example System ...
Deadlocks The Deadlock Problem Bridge Crossing Example System ...
Deadlocks The Deadlock Problem Bridge Crossing Example System ...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
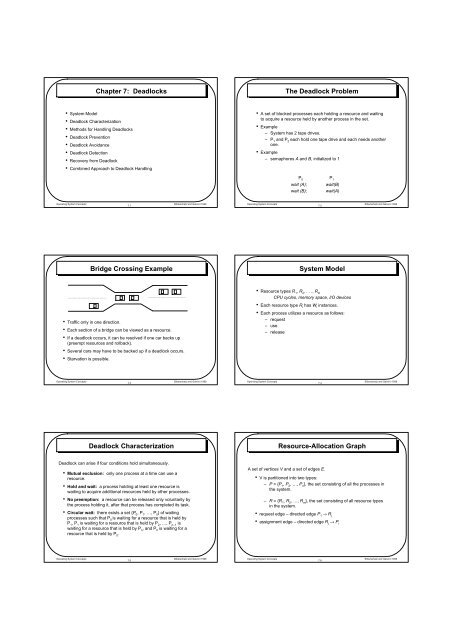
Operating <strong>System</strong> ConceptsChapter 7: <strong><strong>Deadlock</strong>s</strong><strong>The</strong> <strong>Deadlock</strong> <strong>Problem</strong>• <strong>System</strong> Model• <strong>Deadlock</strong> Characterization• Methods for Handling <strong><strong>Deadlock</strong>s</strong>• <strong>Deadlock</strong> Prevention• <strong>Deadlock</strong> Avoidance• <strong>Deadlock</strong> Detection• Recovery from <strong>Deadlock</strong>• Combined Approach to <strong>Deadlock</strong> Handling• A set of blocked processes each holding a resource and waitingto acquire a resource held by another process in the set.• <strong>Example</strong>– <strong>System</strong> has 2 tape drives.– P 1 and P 2 each hold one tape drive and each needs anotherone.• <strong>Example</strong>– semaphores A and B, initialized to 1P 0 P 1wait (A); wait(B)wait (B); wait(A)7.1Silberschatz and Galvin©1999Operating <strong>System</strong> Concepts7.2Silberschatz and Galvin©1999<strong>Bridge</strong> <strong>Crossing</strong> <strong>Example</strong><strong>System</strong> Model• Traffic only in one direction.• Each section of a bridge can be viewed as a resource.• If a deadlock occurs, it can be resolved if one car backs up(preempt resources and rollback).• Several cars may have to be backed up if a deadlock occurs.• Starvation is possible.• Resource types R 1 , R 2 , . . ., R mCPU cycles, memory space, I/O devices• Each resource type R i has W i instances.• Each process utilizes a resource as follows:– request– use– releaseOperating <strong>System</strong> Concepts7.3Silberschatz and Galvin©1999Operating <strong>System</strong> Concepts7.4Silberschatz and Galvin©1999<strong>Deadlock</strong> CharacterizationResource-Allocation Graph<strong>Deadlock</strong> can arise if four conditions hold simultaneously.• Mutual exclusion: only one process at a time can use aresource.• Hold and wait: a process holding at least one resource iswaiting to acquire additional resources held by other processes.• No preemption: a resource can be released only voluntarily bythe process holding it, after that process has completed its task.• Circular wait: there exists a set {P 0 , P 1 , …, P 0 } of waitingprocesses such that P 0 is waiting for a resource that is held byP 1 , P 1 is waiting for a resource that is held by P 2 , …, P n–1 iswaiting for a resource that is held by P n , and P 0 is waiting for aresource that is held by P 0 .A set of vertices V and a set of edges E.• V is partitioned into two types:– P = {P 1 , P 2 , …, P n }, the set consisting of all the processes inthe system.– R = {R 1 , R 2 , …, R m }, the set consisting of all resource typesin the system.• request edge – directed edge P 1 → R j• assignment edge – directed edge R j → P iOperating <strong>System</strong> Concepts7.5Silberschatz and Galvin©1999Operating <strong>System</strong> Concepts7.6Silberschatz and Galvin©1999
Operating <strong>System</strong> ConceptsResource-Allocation Graph (Cont.)<strong>Example</strong> of a Resource Allocation Graph• Process• Resource Type with 4 instances• P i requests instance of R jP iR j• P i is holding an instance of R jP i7.7R jOperating <strong>System</strong> Concepts Silberschatz and Galvin©1999Silberschatz and Galvin©19997.8Resource Allocation Graph With A <strong>Deadlock</strong>Resource Allocation Graph With A Cycle But No <strong>Deadlock</strong>Operating <strong>System</strong> Concepts7.9Silberschatz and Galvin©1999Operating <strong>System</strong> Concepts7.10Silberschatz and Galvin©1999Basic FactsMethods for Handling <strong><strong>Deadlock</strong>s</strong>• If graph contains no cycles ⇒ no deadlock.• If graph contains a cycle ⇒– if only one instance per resource type, then deadlock.– if several instances per resource type, possibility ofdeadlock.• Ensure that the system will never enter a deadlock state.• Allow the system to enter a deadlock state and then recover.• Ignore the problem and pretend that deadlocks never occur in thesystem; used by most operating systems, including UNIX.Operating <strong>System</strong> Concepts7.11Silberschatz and Galvin©1999Operating <strong>System</strong> Concepts7.12Silberschatz and Galvin©1999
Operating <strong>System</strong> Concepts<strong>Deadlock</strong> Prevention<strong>Deadlock</strong> Prevention (Cont.)Restrain the ways request can be made.• Mutual Exclusion – not required for sharable resources; musthold for nonsharable resources.• Hold and Wait – must guarantee that whenever a processrequests a resource, it does not hold any other resources.– Require process to request and be allocated all itsresources before it begins execution, or allow process torequest resources only when the process has none.– Low resource utilization; starvation possible.• No Preemption –– If a process that is holding some resources requestsanother resource that cannot be immediately allocated to it,then all resources currently being held are released.– Preempted resources are added to the list of resources forwhich the process is waiting.– Process will be restarted only when it can regain its oldresources, as well as the new ones that it is requesting.• Circular Wait – impose a total ordering of all resource types, andrequire that each process requests resources in an increasingorder of enumeration.7.13Silberschatz and Galvin©1999Operating <strong>System</strong> Concepts7.14Silberschatz and Galvin©1999<strong>Deadlock</strong> AvoidanceSafe StateRequires that the system has some additional a priori informationavailable.• Simplest and most useful model requires that each processdeclare the maximum number of resources of each type that itmay need.• <strong>The</strong> deadlock-avoidance algorithm dynamically examines theresource-allocation state to ensure that there can never be acircular-wait condition.• Resource-allocation state is defined by the number of availableand allocated resources, and the maximum demands of theprocesses.• When a process requests an available resource, system mustdecide if immediate allocation leaves the system in a safe state.• <strong>System</strong> is in safe state if there exists a safe sequence of allprocesses.• Sequence is safe if for each P i , the resourcesthat Pi can still request can be satisfied by currently availableresources + resources held by all the P j , with j
Review of evidence from the governance indicator against rating2004/2005 Opinion 2005/2006 OpinionUnqualifiedwithEmphasis ofMatterQualified withEmphasis ofMatterDisclaimerwithEmphasis ofMatterUnqualifiedwithEmphasis ofMatterQualified withEmphasis ofMatterDisclaimerwithEmphasis ofMatterSETACleanCleanAGRISETA* x 6BANK SETA X x 6CETA X x 1CHIETA X x 6CTFL X x 5ESETA x X 3ETDP SETA X x 5FASSET X X 6FIETA x X 5FOODBEV X X 6HWSETA X x 5INSETA X X 6ISETT x x 0LGSETA x x 4MAPPP X x 2MERSETA X x 5MQA X x 5SASSETA** x 3SERVICES X X 6TETA X x 5THETA X x 3WRSETA x X 5Overallratingbased on2004/2005&2005/2006OpinionsNote that DIDTETA, POSLEC, PAETA and SETASA only existed for 3 months into the second financial year, and for this reason we have notrated them. Instead we have focused on the two SETAs that were formed which includes SASSETA and AGRISETA as these are the SETAswhich we review across this report.4
Operating <strong>System</strong> ConceptsResource-Request Algorithm for Process P i<strong>Example</strong> of Banker’s AlgorithmRequest i = request vector for process P i . If Request i [j] = k thenprocess P i wants k instances of resource type R j.1. If Request i ≤ Need i go to step 2. Otherwise, raise errorcondition, since process has exceeded its maximum claim.2. If Request i ≤ Available, go to step 3. Otherwise P i mustwait, since resources are not available.3. Pretend to allocate requested resources to P i by modifyingthe state as follows:Available := Available = Request i ;Allocation i := Allocation i + Request i ;Need i := Need i – Request i;;• If safe ⇒ the resources are allocated to P i .• If unsafe ⇒ P i must wait, and the old resource-allocationstate is restored• 5 processes P 0 through P 4 ; 3 resource types A (10 instances),B (5instances, and C (7 instances).• Snapshot at time T 0 :Allocation Max AvailableA B C A B C A B CP 0 0 1 0 7 5 3 3 3 2P 1 2 0 0 3 2 2P 2 3 0 2 9 0 2P 3 2 1 1 2 2 2P 4 0 0 2 4 3 37.25Silberschatz and Galvin©1999Operating <strong>System</strong> Concepts7.26Silberschatz and Galvin©1999<strong>Example</strong> (Cont.)<strong>Example</strong> (Cont.): P 1 request (1,0,2)• <strong>The</strong> content of the matrix. Need is defined to be Max – Allocation.NeedA B CP 0 7 4 3P 1 1 2 2P 2 6 0 0P 3 0 1 1P 4 4 3 1• <strong>The</strong> system is in a safe state since the sequence < P 1 , P 3 , P 4 , P 2 , P 0 >satisfies safety criteria.• Check that Request ≤ Available (that is, (1,0,2) ≤ (3,3,2) ⇒ true.Allocation Need AvailableA B C A B C A B CP 0 0 1 0 7 4 3 2 3 0P 1 3 0 2 0 2 0P 2 3 0 1 6 0 0P 3 2 1 1 0 1 1P 4 0 0 2 4 3 1• Executing safety algorithm shows that sequence satisfies safety requirement.• Can request for (3,3,0) by P 4 be granted?• Can request for (0,2,0) by P 0 be granted?Operating <strong>System</strong> Concepts7.27Silberschatz and Galvin©1999Operating <strong>System</strong> Concepts7.28Silberschatz and Galvin©1999<strong>Deadlock</strong> DetectionSingle Instance of Each Resource Type• Allow system to enter deadlock state• Detection algorithm• Recovery scheme• Maintain wait-for graph– Nodes are processes.– P i → P j if P i is waiting for P j .• Periodically invoke an algorithm that searches for a cycle in thegraph.• An algorithm to detect a cycle in a graph requires an order of n 2operations, where n is the number of vertices in the graph.Operating <strong>System</strong> Concepts7.29Silberschatz and Galvin©1999Operating <strong>System</strong> Concepts7.30Silberschatz and Galvin©1999
Operating <strong>System</strong> ConceptsResource-Allocation Graph And Wait-for GraphSeveral Instances of a Resource Type• Available: A vector of length m indicates the number of availableresources of each type.• Allocation: An n x m matrix defines the number of resources ofeach type currently allocated to each process.• Request: An n x m matrix indicates the current request of eachprocess. If Request [i,j] = k, then process P i is requesting k moreinstances of resource type. R j .Resource-Allocation GraphCorresponding wait-for graph7.31Silberschatz and Galvin©1999Operating <strong>System</strong> Concepts7.32Silberschatz and Galvin©1999Detection AlgorithmDetection Algorithm (Cont.)1. Let Work and Finish be vectors of length m and n, respectivelyInitialize:(a) Work :- Available(b) For i = 1,2, …, n, if Allocation i ≠ 0, thenFinish[i] := false;otherwise, Finish[i] := true.2. Find an index i such that both:(a) Finish[i] = false(b) Request i ≤ WorkIf no such i exists, go to step 4.3. Work := Work + Allocation iFinish[i] := truego to step 2.4. If Finish[i] = false, for some i, 1 ≤ i ≤ n, then the system is indeadlock state. Moreover, if Finish[i] = false, then P i isdeadlocked.Algorithm requires an order of m x n 2 operations to detect whetherthe system is in deadlocked state.Operating <strong>System</strong> Concepts7.33Silberschatz and Galvin©1999Operating <strong>System</strong> Concepts7.34Silberschatz and Galvin©1999<strong>Example</strong> of Detection Algorithm<strong>Example</strong> (Cont.)• Five processes P 0 through P 4 ; three resource typesA (7 instances), B (2 instances), and C (6 instances).• Snapshot at time T 0 :Allocation Request AvailableA B C A B C A B CP 0 0 1 0 0 0 0 0 0 0P 1 2 0 0 2 0 2P 2 3 0 3 0 0 0P 3 2 1 1 1 0 0P 4 0 0 2 0 0 2• Sequence will result in Finish[i] = true for all i.• P 2 requests an additional instance of type C.RequestA B CP 0 0 0 0P 1 2 0 1P 2 0 0 1P 3 1 0 0P 4 0 0 2• State of system?– Can reclaim resources held by process P 0 , but insufficientresources to fulfill other processes; requests.– <strong>Deadlock</strong> exists, consisting of processes P 1 , P 2 , P 3 , and P 4 .Operating <strong>System</strong> Concepts7.35Silberschatz and Galvin©1999Operating <strong>System</strong> Concepts7.36Silberschatz and Galvin©1999
Operating <strong>System</strong> ConceptsDetection-Algorithm UsageRecovery from <strong>Deadlock</strong>: Process Termination• When, and how often, to invoke depends on:– How often a deadlock is likely to occur?– How many processes will need to be rolled back?✴ one for each disjoint cycle• If detection algorithm is invoked arbitrarily, there may be manycycles in the resource graph and so we would not be able to tellwhich of the many deadlocked processes “caused” the deadlock.• Abort all deadlocked processes.• Abort one process at a time until the deadlock cycle is eliminated.• In which order should we choose to abort?– Priority of the process.– How long process has computed, and how much longer tocompletion.– Resources the process has used.– Resources process needs to complete.– How many processes will need to be terminated.– Is process interactive or batch?7.37Silberschatz and Galvin©1999Operating <strong>System</strong> Concepts7.38Silberschatz and Galvin©1999Recovery from <strong>Deadlock</strong>: Resource PreemptionCombined Approach to <strong>Deadlock</strong> Handling• Selecting a victim – minimize cost.• Rollback – return to some safe state, restart process fro thatstate.• Starvation – same process may always be picked as victim,include number of rollback in cost factor.• Combine the three basic approaches– prevention– avoidance– detectionallowing the use of the optimal approach for each of resources inthe system.• Partition resources into hierarchically ordered classes.• Use most appropriate technique for handling deadlocks withineach class.Operating <strong>System</strong> Concepts7.39Silberschatz and Galvin©1999Operating <strong>System</strong> Concepts7.40Silberschatz and Galvin©1999