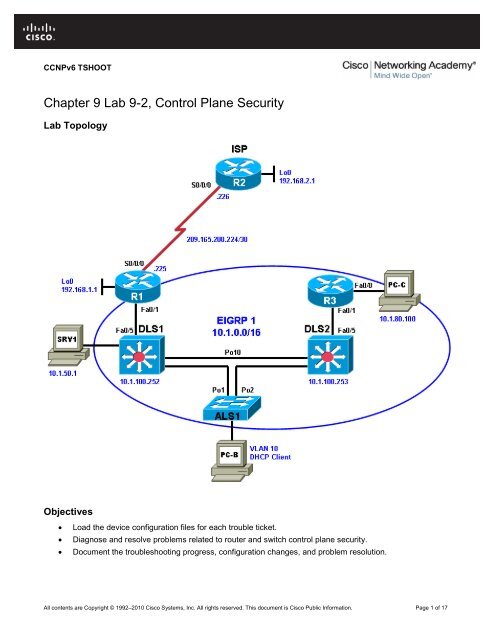
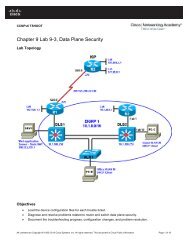
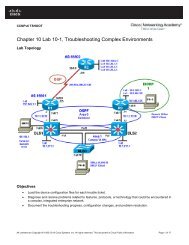
Chapter 3 Lab A - Securing Administrative Access Using AAA and ...
Chapter 3 Lab A - Securing Administrative Access Using AAA and ...
Chapter 3 Lab A - Securing Administrative Access Using AAA and ...
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
CCNPv6 TSHOOTDeviceActions <strong>and</strong> ResultsStep 7: Document trouble ticket debrief notes.Use this space to make notes of the key learning points that you picked up during the discussion of thistrouble ticket with your instructor. The notes can include problems encountered, solutions applied, usefulcomm<strong>and</strong>s employed, alternate solutions, methods, <strong>and</strong> processes, <strong>and</strong> procedure <strong>and</strong> communicationimprovements._________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________________All contents are Copyright © 1992–2010 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 7 of 17
CCNPv6 TSHOOTSection 2 Troubleshooting Reference InformationGeneral Troubleshooting ProcessAs a general guideline, you can use the following general troubleshooting process described in the course.1. Define the problem (symptoms).2. Gather information.3. Analyze the information.4. Propose a hypothesis (possible cause).5. Test the hypothesis.6. Eliminate or accept the hypothesis.7. Solve the problem.8. Document the problem.Comm<strong>and</strong> SummaryThe table lists useful comm<strong>and</strong>s for this lab. The sample output is shown on following pages.Comm<strong>and</strong>show ip dhcp snoopingdebug ip dhcp snooping packetdebug ip dhcp server packetshow ip eigrp neighborssh ip eigrp interfacesshow ip eigrp interfaces detaildebug eigrp packetsKey Information DisplayedDisplays snooping status (enabled or not) <strong>and</strong>, ifenabled, on which VLANs. Also shows which interfacesare trusted.Displays real-time information on DHCP snooping activity<strong>and</strong> the client/server exchange.Displays real-time information on DHCP on theclient/server exchange from the server perspective.Displays the IP address of EIGRP neighbors <strong>and</strong> theinterface on which they were learned.Displays all interfaces participating in EIGRP for each AS<strong>and</strong> the number of peers associated with each interface.Displays all interfaces participating in EIGRP for each ASalong with the number of peers, hello interval, <strong>and</strong> thetype of authentication (if configured).Displays real-time information on types of EIGRPpackets exchange, which include authenticationinformation.All contents are Copyright © 1992–2010 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 8 of 17
CCNPv6 TSHOOTSample Troubleshooting OutputDHCP Snooping-related Comm<strong>and</strong>sThe following comm<strong>and</strong>s <strong>and</strong> outputs are provided as samples from the devices in this lab.ALS1#show ip dhcp snoopingSwitch DHCP snooping is enabledDHCP snooping is configured on following VLANs:10DHCP snooping is operational on following VLANs:10DHCP snooping is configured on the following L3 Interfaces:Insertion of option 82 is enabledcircuit-id format: vlan-mod-portremote-id format: MACOption 82 on untrusted port is not allowedVerification of hwaddr field is enabledVerification of giaddr field is enabledDHCP snooping trust/rate is configured on the following Interfaces:Interface Trusted Rate limit (pps)------------------------ ------- ----------------FastEthernet0/1 yes unlimitedFastEthernet0/2 yes unlimitedFastEthernet0/3 yes unlimitedFastEthernet0/4 yes unlimitedPort-channel1 yes unlimitedPort-channel2 yes unlimitedIn the above example, DHCP snooping is operational on ALS1 VLAN 10, <strong>and</strong> Fa0/1 through Fa0/4 (port channelsPo1 <strong>and</strong> Po2) are trusted.DLS1#show ip dhcp snoopingSwitch DHCP snooping is disabledDHCP snooping is configured on following VLANs:noneDHCP snooping is operational on following VLANs:noneDHCP snooping is configured on the following L3 Interfaces:Insertion of option 82 is enabledcircuit-id format: vlan-mod-portremote-id format: MACOption 82 on untrusted port is not allowedVerification of hwaddr field is enabledVerification of giaddr field is enabledDHCP snooping trust/rate is configured on the following Interfaces:Interface Trusted Rate limit (pps)------------------------ ------- ----------------In the above example, Option 82 on untrusted port is not allowed, <strong>and</strong> no interfaces are trusted.All contents are Copyright © 1992–2010 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 9 of 17
CCNPv6 TSHOOTALS1#debug ip dhcp snooping packetDHCP Snooping Packet debugging is onALS1#*Mar 1 09:04:48.215: DHCPSNOOP(hlfm_set_if_input): Setting if_input to Fa0/18 for pak. Was not set*Mar 1 09:04:48.215: DHCPSNOOP(hlfm_set_if_input): Clearing if_input for pak.Was Fa0/18*Mar 1 09:04:48.215: DHCPSNOOP(hlfm_set_if_input): Setting if_input to Fa0/18 for pak. Was not set*Mar 1 09:04:48.215: DHCP_SNOOPING: received new DHCP packet from input interface (FastEthernet0/18)*Mar 1 09:04:48.215: DHCP_SNOOPING: process new DHCP packet, message type: DHCPDISCOVER, input interface: Fa0/18, MAC da: ffff.ffff.ffff, MAC sa: 000b.db04.a5cd,IP da: 255.255.255.255, IP sa: 0.0.0.0, DHCP ciaddr: 0.0.0.0, DHCP yiaddr: 0.0.0.0, DHCP siaddr: 0.0.0.0, DHCP giaddr: 0.0.0.0, DHCP chaddr: 000b.db04.a5cd*Mar 1 09:04:48.215: DHCP_SNOOPING: add relay information option.*Mar 1 09:04:48.215: DHCP_SNOOPING_SW: Encoding opt82 CID in vlan-mod-port format*Mar 1 09:04:48.215: DHCP_SNOOPING_SW: Encoding opt82 RID in MAC address format*Mar 1 09:04:48.215: DHCP_SNOOPING: binary dump of relay info option, length: 20data:0x52 0x12 0x1 0x6 0x0 0x4 0x0 0xA 0x1 0x12 0x2 0x8 0x0 0x6 0x0 0x1B 0xC 0x6D 0x8F 0x0*Mar 1 09:04:48.215: DHCP_SNOOPING_SW: bridge packet get invalid mat entry: FFFF.FFFF.FFFF, packet is flooded to ingress VLAN: (10)ALS1#In the above example, a DHCP DISCOVER message with option 82 <strong>and</strong> GIADDR of 0.0.0.0 was sent to DLS1but, because DLS1 does not trust this relay information a reply was not received from the DLS1 DHCP server.ALS1#debug ip dhcp snooping packetDHCP Snooping Packet debugging is onALS1#*Mar 1 09:10:36.904: DHCPSNOOP(hlfm_set_if_input): Setting if_input to Fa0/18 for pak. Was not set*Mar 1 09:10:36.904: DHCPSNOOP(hlfm_set_if_input): Clearing if_input for pak.Was Fa0/18*Mar 1 09:10:36.904: DHCPSNOOP(hlfm_set_if_input): Setting if_input to Fa0/18 for pak. Was not set*Mar 1 09:10:36.904: DHCP_SNOOPING: received new DHCP packet from input interface (FastEthernet0/18)*Mar 1 09:10:36.904: DHCP_SNOOPING: process new DHCP packet, message type: DHCPDISCOVER, input interface: Fa0/18, MAC da: ffff.ffff.ffff, MAC sa: 000b.db04.a5cd,IP da: 255.255.255.255, IP sa: 0.0.0.0, DHCP ciaddr: 0.0.0.0, DHCP yiaddr: 0.0.0.0, DHCP siaddr: 0.0.0.0, DHCP giaddr: 0.0.0.0, DHCP chaddr: 000b.db04.a5cd*Mar 1 09:10:36.904: DHCP_SNOOPING: add relay information option.*Mar 1 09:10:36.904: DHCP_SNOOPING_SW: Encoding opt82 CID in vlan-mod-port format*Mar 1 09:10:36.904: DHCP_SNOOPING_SW: Encoding opt82 RID in MAC address format*Mar 1 09:10:36.904: DHCP_SNOOPING: binary dump of relay info option, length: 20data:0x52 0x12 0x1 0x6 0x0 0x4 0x0 0xA 0x1 0x12 0x2 0x8 0x0 0x6 0x0 0x1B 0xC 0x6D 0x8All contents are Copyright © 1992–2010 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 10 of 17
CCNPv6 TSHOOT*Mar 1 09:10:36.921: DHCPSNOOP(hlfm_set_if_input): Setting if_input to Po1 forpak. Was not set*Mar 1 09:10:36.921: DHCP_SNOOPING: received new DHCP packet from input interface (Port-channel1)*Mar 1 09:10:36.921: DHCP_SNOOPING: process new DHCP packet, message type: DHCPACK, input interface: Po1, MAC da: ffff.ffff.ffff, MAC sa: 0017.5a5b.b443, IP da: 255.255.255.255, IP sa: 10.1.10.252, DHCP ciaddr: 0.0.0.0, DHCP yiaddr: 10.1.10.1, DHCP siaddr: 0.0.0.0, DHCP giaddr: 0.0.0.0, DHCP chaddr:ALS1# 000b.db04.a5cd*Mar 1 09:10:36.921: DHCP_SNOOPING: binary dump of option 82, length: 20 data:0x52 0x12 0x1 0x6 0x0 0x4 0x0 0xA 0x1 0x12 0x2 0x8 0x0 0x6 0x0 0x1B 0xC 0x6D 0x8F 0x0*Mar 1 09:10:36.921: DHCP_SNOOPING: binary dump of extracted circuit id, length: 8 data:0x1 0x6 0x0 0x4 0x0 0xA 0x1 0x12*Mar 1 09:10:36.921: DHCP_SNOOPING: binary dump of extracted remote id, length:10 data:0x2 0x8 0x0 0x6 0x0 0x1B 0xC 0x6D 0x8F 0x0*Mar 1 09:10:36.921: DHCP_SNOOPING_SW: opt82 data indicates loALS1#cal packet*Mar 1 09:10:36.921: DHCP_SNOOPING_SW: opt82 data indicates local packet*Mar 1 09:10:36.921: DHCP_SNOOPING: remove relay information option.*Mar 1 09:10:36.921: DHCP_SNOOPING: direct forward dhcp reply to output port: FastEthernet0/18.ALS1#u allAll possible debugging has been turned offALS1#In the above example, the ip dhcp relay information trust-all comm<strong>and</strong> was issued on DLS1. TheDHCP DISCOVER message received on ALS1 interface Fa0/18 (from PC-B) <strong>and</strong> was forwarded to DLS1 tocomplete the DHCP exchange between PC-B <strong>and</strong> DLS1.DLS1#debug ip dhcp server packetDHCP server packet debugging is on.Dec 11 14:14:25.024: DHCPD: Reload workspace interface Vlan10 tableid 0.Dec 11 14:14:25.024: DHCPD: tableid for 10.1.10.252 on Vlan10 is 0Dec 11 14:14:25.024: DHCPD: client's VPN is .Dec 11 14:14:25.024: DHCPD: inconsistent relay information.Dec 11 14:14:25.024: DHCPD: relay information option exists, but giaddr is zeroIn the above example, with dhcp relay information from ALS1 <strong>and</strong> a GIADDR of 0.0.0.0, the relay information isinconsistent <strong>and</strong> DLS1 rejects the DHCP DISCOVER message from PC-B.DLS1#debug ip dhcp server packetDHCP server packet debugging is on.Dec 11 14:28:13.118: DHCPD: Reload workspace interface Vlan10 tableid 0.Dec 11 14:28:13.118: DHCPD: tableid for 10.1.10.252 on Vlan10 is 0Dec 11 14:28:13.118: DHCPD: client's VPN is .Dec 11 14:28:13.118: DHCPD: DHCPRELEASE message received from client 0100.0bdb.04a5.cd (10.1.10.1).Dec 11 14:28:15.542: DHCPD: Reload workspace interface Vlan10 tableid 0.Dec 11 14:28:15.542: DHCPD: tableid for 10.1.10.252 on Vlan10 is 0Dec 11 14:28:15.542: DHCPD: client's VPN is .Dec 11 14:28:15.542: DHCPD: using received relay info.Dec 11 14:28:15.542: DHCPD: DHCPDISCOVER received from client 0100.0bdb.04a5.cdon interface Vlan10.All contents are Copyright © 1992–2010 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 12 of 17
CCNPv6 TSHOOTDec 11 14:28:15.542: DHCPD: using received relay info.Dec 11 14:28:17.556: DHCPD: Sending DHCPOFFER to client 0100.0bdb.04a5.cd (10.1.10.1).Dec 11 14:28:17.556: DHCPD: Check for IPe on Vlan10Dec 11 14:28:17.556: DHCPD: creating ARP entry (10.1.10.1, 000b.db04.a5cd).Dec 11 14:28:17.556: DHCPD: unicasting BOOTREPLY to client 000b.db04.a5cd (10.1.10.1).Dec 11 14:28:17.556: DHCPD: Reload workspace interface Vlan10 tableid 0.Dec 11 14:28:17.556: DHCPD: tableid for 10.1.10.252 on Vlan10 is 0Dec 11 14:28:17.556: DHCPD: client's VPN is .Dec 11 14:28:17.556: DHCPD: DHCPREQUEST received from client 0100.0bdb.04a5.cd.Dec 11 14:28:17.556: DHCPD: Sending DHCPACK to client 0100.0bdb.04a5.cd (10.1.10.1).Dec 11 14:28:17.556: DHCPD: Check for IPe on Vlan10Dec 11 14:28:17.556: DHCPD: creating ARP entry (10.1.10.1, 000b.db04.a5cd).Dec 11 14:28:17.556: DHCPD: unicasting BOOTREPLY to client 000b.db04.a5cd (10.1.10.1).In the above example, with the ip dhcp relay information trust-all comm<strong>and</strong> issued on DLS1, theentire DHCP conversation between PC-B <strong>and</strong> the DLS1 server takes place, <strong>and</strong> PC-B is provided with an IPaddress.EIGRP Authentication-related Comm<strong>and</strong>sDLS2#show ip eigrp neighborsEIGRP-IPv4:(1) neighbors for process 1H Address Interface Hold Uptime SRTT RTO Q Seq(sec) (ms) Cnt Num1 10.1.2.14 Fa0/5 13 00:20:59 1 200 0 290 10.1.200.252 Vl200 14 05:31:25 2 200 0 45In the above example, DLS2 has two EIGRP neighbors, R3 (10.1.2.14) via Fa0/5 <strong>and</strong> DLS1 (10.1.200.252) viaVLAN 200.DLS2#show ip eigrp interfacesEIGRP-IPv4:(1) interfaces for process 1Xmit Queue Mean Pacing Time Multicast PendingInterface Peers Un/Reliable SRTT Un/Reliable Flow Timer RoutesVl200 1 0/0 2 0/1 50 0Fa0/5 1 0/0 1 0/1 50 0In the above example, DLS2 has two interfaces participating in the EIGRP process, VLAN 200 <strong>and</strong> Fa0/5. Bothinterfaces have a peer attached.DLS2#show ip eigrp interfaces detailEIGRP-IPv4:(1) interfaces for process 1Xmit Queue Mean Pacing Time Multicast PendingInterface Peers Un/Reliable SRTT Un/Reliable Flow Timer RoutesVl200 1 0/0 1 0/1 50 0Hello interval is 5 secNext xmit serial Un/reliable mcasts: 0/18 Un/reliable ucasts: 22/9Mcast exceptions: 1 CR packets: 1 ACKs suppressed: 1All contents are Copyright © 1992–2010 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 13 of 17
CCNPv6 TSHOOTrouteia - IS-IS inter area, * - c<strong>and</strong>idate default, U - per-user statico - ODR, P - periodic downloaded static routeGateway of last resort is 10.1.2.13 to network 0.0.0.010.0.0.0/8 is variably subnetted, 9 subnets, 3 masksD 10.1.10.0/24 [90/28416] via 10.1.2.13, 00:01:43, FastEthernet0/1C 10.1.2.12/30 is directly connected, FastEthernet0/1D 10.1.2.0/30 [90/30976] via 10.1.2.13, 00:01:43, FastEthernet0/1D 10.1.30.0/24 [90/28416] via 10.1.2.13, 00:01:43, FastEthernet0/1D 10.1.20.0/24 [90/28416] via 10.1.2.13, 00:01:43, FastEthernet0/1D 10.1.50.0/24 [90/28416] via 10.1.2.13, 00:01:43, FastEthernet0/1D 10.1.100.0/24 [90/28416] via 10.1.2.13, 00:01:43, FastEthernet0/1C 10.1.203.1/32 is directly connected, Loopback0D 10.1.200.0/24 [90/28416] via 10.1.2.13, 00:01:43, FastEthernet0/1D 192.168.1.0/24 [90/158976] via 10.1.2.13, 00:01:43, FastEthernet0/1D*EX 0.0.0.0/0 [170/2175232] via 10.1.2.13, 00:01:43, FastEthernet0/1In the above example, all expected routes are present in the R3 routing table. This does not prove thatauthentication is occurring. However, it does indicate that either authentication is configured correctly for bothadjacent interfaces, or it is not configured at all for both adjacent interfaces.All contents are Copyright © 1992–2010 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 15 of 17
CCNPv6 TSHOOTReferencesIf you need more information on the comm<strong>and</strong>s <strong>and</strong> their options, see the following references• IP Routing Protocolhttp://www.cisco.com/cisco/web/support/index.html• Cisco IOS IP Switchinghttp://www.cisco.com/en/US/docs/ios/ipswitch/comm<strong>and</strong>/reference/isw_book.html• Configuring DHCP Features on a Cisco 2960 Switchhttp://www.cisco.com/en/US/docs/switches/lan/catalyst2960/software/release/12.2_37_se/configuration/guide/swdhcp82.html• Configuring EIGRP Message Authenticationhttp://www.cisco.com/en/US/tech/tk365/technologies_configuration_example09186a00807f5a63.shtmlRouter Interface Summary TableRouter Model Ethernet Interface#11700 Fast Ethernet 0(FA0)1800 Fast Ethernet 0/0(FA0/0)2600 Fast Ethernet 0/0(FA0/0)2800 Fast Ethernet 0/0(FA0/0)Router Interface SummaryEthernet Interface#2Fast Ethernet 1(FA1)Fast Ethernet 0/1(FA0/1)Fast Ethernet 0/1(FA0/1)Fast Ethernet 0/1(FA0/1)Serial Interface#1Serial 0 (S0)Serial 0/0/0(S0/0/0)Serial 0/0 (S0/0)Serial 0/0/0(S0/0/0)Serial Interface#2Serial 1 (S1)Serial 0/0/1(S0/0/1)Serial 0/1 (S0/1)Serial 0/0/1(S0/0/1)Note: To find out how the router is configured, look at the interfaces to identify the type of router<strong>and</strong> how many interfaces the router has. Rather than try to list all the combinations ofconfigurations for each router class, this table includes identifiers for the possible combinations ofEthernet <strong>and</strong> serial interfaces in the device. The table does not include any other type of interface,even though a specific router might contain one. An example of this is an ISDN BRI interface. Thestring in parenthesis is the legal abbreviation that can be used in Cisco IOS comm<strong>and</strong>s torepresent the interface.All contents are Copyright © 1992–2010 Cisco Systems, Inc. All rights reserved. This document is Cisco Public Information. Page 17 of 17