Dirty Paper Coding using Sign-bit Shaping and LDPC Codes
Dirty Paper Coding using Sign-bit Shaping and LDPC Codes
Dirty Paper Coding using Sign-bit Shaping and LDPC Codes
You also want an ePaper? Increase the reach of your titles
YUMPU automatically turns print PDFs into web optimized ePapers that Google loves.
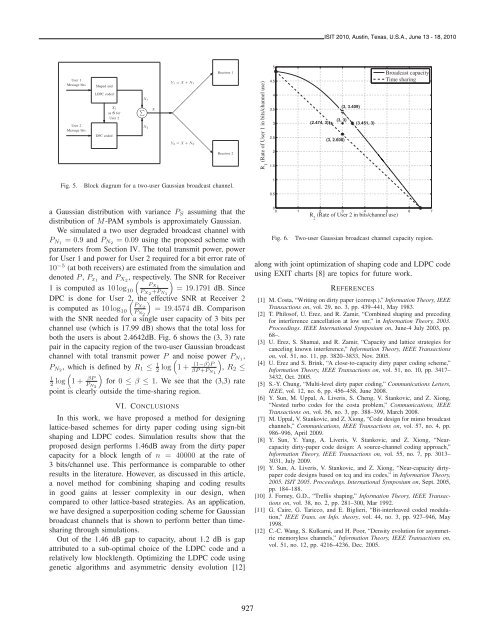
ISIT 2010, Austin, Texas, U.S.A., June 13 - 18, 2010User 1Message <strong>bit</strong>s Shaped <strong>and</strong>✲<strong>LDPC</strong> codedX1as S forUser 2❄User 2Message <strong>bit</strong>s✲ DPC codedX1✓✏ ❄ ∑ X✒✑✻X2 ✒Y1 = X + N1✲ ❅❅❅❅❅Y2 = X + N2 ❅❅❅❘Receiver 1Receiver 2R 1(Rate of User 1 in <strong>bit</strong>s/channel use)54.543.532.521.5(3, 3.409)(3, 3)(2.474, 3)(3.451, 3)(3, 2.608)Broadcast capacityTime sharingFig. 5.Block diagram for a two-user Gaussian broadcast channel.10.5a Gaussian distribution with variance P S assuming that thedistribution of M-PAM symbols is approximately Gaussian.We simulated a two user degraded broadcast channel withP N1 =0.9 <strong>and</strong> P N2 =0.09 <strong>using</strong> the proposed scheme withparameters from Section IV. The total transmit power, powerfor User 1 <strong>and</strong> power for User 2 required for a <strong>bit</strong> error rate of10 −5 (at both receivers) are estimated from the simulation <strong>and</strong>denoted P , P x1 <strong>and</strong> P X2 , respectively. ( ) The SNR for ReceiverPX11 is computed as 10 log 10 P X2 +P N1=19.1791 dB. SinceDPC is done for User 2, ( the)effective SNR at Receiver 2PX2is computed as 10 log 10 P N2=19.4574 dB. Comparisonwith the SNR needed for a single user capacity of 3 <strong>bit</strong>s perchannel use (which is 17.99 dB) shows that the total loss forboth the users is about 2.4642dB. Fig. 6 shows the (3, 3) ratepair in the capacity region of the two-user Gaussian broadcastchannel with total transmit power P <strong>and</strong> ( noise power P N1 ,P N2 , which is defined by R 1 ≤ 1 2 log 1+ (1−β)PβP+P N1), R 2 ≤( )12 log 1+ βPP N2for 0 ≤ β ≤ 1. We see that the (3,3) ratepoint is clearly outside the time-sharing region.VI. CONCLUSIONSIn this work, we have proposed a method for designinglattice-based schemes for dirty paper coding <strong>using</strong> sign-<strong>bit</strong>shaping <strong>and</strong> <strong>LDPC</strong> codes. Simulation results show that theproposed design performs 1.46dB away from the dirty papercapacity for a block length of n = 40000 at the rate of3 <strong>bit</strong>s/channel use. This performance is comparable to otherresults in the literature. However, as discussed in this article,a novel method for combining shaping <strong>and</strong> coding resultsin good gains at lesser complexity in our design, whencompared to other lattice-based strategies. As an application,we have designed a superposition coding scheme for Gaussianbroadcast channels that is shown to perform better than timesharingthrough simulations.Out of the 1.46 dB gap to capacity, about 1.2 dB is gapattributed to a sub-optimal choice of the <strong>LDPC</strong> code <strong>and</strong> arelatively low blocklength. Optimizing the <strong>LDPC</strong> code <strong>using</strong>genetic algorithms <strong>and</strong> asymmetric density evolution [12]00 1 2 3 4 5 6 7Fig. 6.R 2(Rate of User 2 in <strong>bit</strong>s/channel use)Two-user Gaussian broadcast channel capacity region.along with joint optimization of shaping code <strong>and</strong> <strong>LDPC</strong> code<strong>using</strong> EXIT charts [8] are topics for future work.REFERENCES[1] M. Costa, “Writing on dirty paper (corresp.),” Information Theory, IEEETransactions on, vol. 29, no. 3, pp. 439–441, May 1983.[2] T. Philosof, U. Erez, <strong>and</strong> R. Zamir, “Combined shaping <strong>and</strong> precodingfor interference cancellation at low snr,” in Information Theory, 2003.Proceedings. IEEE International Symposium on, June-4 July 2003, pp.68–.[3] U. Erez, S. Shamai, <strong>and</strong> R. Zamir, “Capacity <strong>and</strong> lattice strategies forcanceling known interference,” Information Theory, IEEE Transactionson, vol. 51, no. 11, pp. 3820–3833, Nov. 2005.[4] U. Erez <strong>and</strong> S. Brink, “A close-to-capacity dirty paper coding scheme,”Information Theory, IEEE Transactions on, vol. 51, no. 10, pp. 3417–3432, Oct. 2005.[5] S.-Y. Chung, “Multi-level dirty paper coding,” Communications Letters,IEEE, vol. 12, no. 6, pp. 456–458, June 2008.[6] Y. Sun, M. Uppal, A. Liveris, S. Cheng, V. Stankovic, <strong>and</strong> Z. Xiong,“Nested turbo codes for the costa problem,” Communications, IEEETransactions on, vol. 56, no. 3, pp. 388–399, March 2008.[7] M. Uppal, V. Stankovic, <strong>and</strong> Z. Xiong, “Code design for mimo broadcastchannels,” Communications, IEEE Transactions on, vol. 57, no. 4, pp.986–996, April 2009.[8] Y. Sun, Y. Yang, A. Liveris, V. Stankovic, <strong>and</strong> Z. Xiong, “Nearcapacitydirty-paper code design: A source-channel coding approach,”Information Theory, IEEE Transactions on, vol. 55, no. 7, pp. 3013–3031, July 2009.[9] Y. Sun, A. Liveris, V. Stankovic, <strong>and</strong> Z. Xiong, “Near-capacity dirtypapercode designs based on tcq <strong>and</strong> ira codes,” in Information Theory,2005. ISIT 2005. Proceedings. International Symposium on, Sept. 2005,pp. 184–188.[10] J. Forney, G.D., “Trellis shaping,” Information Theory, IEEE Transactionson, vol. 38, no. 2, pp. 281–300, Mar 1992.[11] G. Caire, G. Taricco, <strong>and</strong> E. Biglieri, “Bit-interleaved coded modulation,”IEEE Trans. on Info. theory, vol. 44, no. 3, pp. 927–946, May1998.[12] C.-C. Wang, S. Kulkarni, <strong>and</strong> H. Poor, “Density evolution for asymmetricmemoryless channels,” Information Theory, IEEE Transactions on,vol. 51, no. 12, pp. 4216–4236, Dec. 2005.927