Cyber Security Capability Framework & Mapping of ISM Roles - agimo
Cyber Security Capability Framework & Mapping of ISM Roles - agimo
Cyber Security Capability Framework & Mapping of ISM Roles - agimo
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
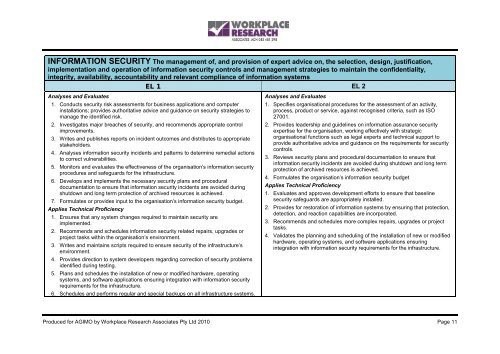
INFORMATION SECURITY The management <strong>of</strong>, and provision <strong>of</strong> expert advice on, the selection, design, justification,implementation and operation <strong>of</strong> information security controls and management strategies to maintain the confidentiality,integrity, availability, accountability and relevant compliance <strong>of</strong> information systemsEL 1 EL 2Analyses and Evaluates1. Conducts security risk assessments for business applications and computerinstallations; provides authoritative advice and guidance on security strategies tomanage the identified risk.2. Investigates major breaches <strong>of</strong> security, and recommends appropriate controlimprovements.3. Writes and publishes reports on incident outcomes and distributes to appropriatestakeholders.4. Analyses information security incidents and patterns to determine remedial actionsto correct vulnerabilities.5. Monitors and evaluates the effectiveness <strong>of</strong> the organisation’s information securityprocedures and safeguards for the infrastructure.6. Develops and implements the necessary security plans and proceduraldocumentation to ensure that information security incidents are avoided duringshutdown and long term protection <strong>of</strong> archived resources is achieved.7. Formulates or provides input to the organisation’s information security budget.Applies Technical Pr<strong>of</strong>iciency1. Ensures that any system changes required to maintain security areimplemented.2. Recommends and schedules information security related repairs, upgrades orproject tasks within the organisation’s environment.3. Writes and maintains scripts required to ensure security <strong>of</strong> the infrastructure’senvironment.4. Provides direction to system developers regarding correction <strong>of</strong> security problemsidentified during testing.5. Plans and schedules the installation <strong>of</strong> new or modified hardware, operatingsystems, and s<strong>of</strong>tware applications ensuring integration with information securityrequirements for the infrastructure.6. Schedules and performs regular and special backups on all infrastructure systems.Analyses and Evaluates1. Specifies organisational procedures for the assessment <strong>of</strong> an activity,process, product or service, against recognised criteria, such as ISO27001.2. Provides leadership and guidelines on information assurance securityexpertise for the organisation, working effectively with strategicorganisational functions such as legal experts and technical support toprovide authoritative advice and guidance on the requirements for securitycontrols.3. Reviews security plans and procedural documentation to ensure thatinformation security incidents are avoided during shutdown and long termprotection <strong>of</strong> archived resources is achieved.4. Formulates the organisation’s information security budgetApplies Technical Pr<strong>of</strong>iciency1. Evaluates and approves development efforts to ensure that baselinesecurity safeguards are appropriately installed.2. Provides for restoration <strong>of</strong> information systems by ensuring that protection,detection, and reaction capabilities are incorporated.3. Recommends and schedules more complex repairs, upgrades or projecttasks.4. Validates the planning and scheduling <strong>of</strong> the installation <strong>of</strong> new or modifiedhardware, operating systems, and s<strong>of</strong>tware applications ensuringintegration with information security requirements for the infrastructure.Produced for AGIMO by Workplace Research Associates Pty Ltd 2010 Page 11