Cyber Security Capability Framework & Mapping of ISM Roles - agimo
Cyber Security Capability Framework & Mapping of ISM Roles - agimo
Cyber Security Capability Framework & Mapping of ISM Roles - agimo
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
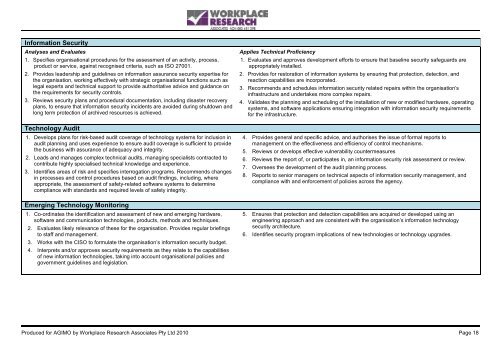
Information <strong>Security</strong>Analyses and Evaluates1. Specifies organisational procedures for the assessment <strong>of</strong> an activity, process,product or service, against recognised criteria, such as ISO 27001.2. Provides leadership and guidelines on information assurance security expertise forthe organisation, working effectively with strategic organisational functions such aslegal experts and technical support to provide authoritative advice and guidance onthe requirements for security controls.3. Reviews security plans and procedural documentation, including disaster recoveryplans, to ensure that information security incidents are avoided during shutdown andlong term protection <strong>of</strong> archived resources is achieved.Technology Audit1. Develops plans for risk-based audit coverage <strong>of</strong> technology systems for inclusion inaudit planning and uses experience to ensure audit coverage is sufficient to providethe business with assurance <strong>of</strong> adequacy and integrity.2. Leads and manages complex technical audits, managing specialists contracted tocontribute highly specialised technical knowledge and experience.3. Identifies areas <strong>of</strong> risk and specifies interrogation programs. Recommends changesin processes and control procedures based on audit findings, including, whereappropriate, the assessment <strong>of</strong> safety-related s<strong>of</strong>tware systems to determinecompliance with standards and required levels <strong>of</strong> safety integrity.Emerging Technology Monitoring1. Co-ordinates the identification and assessment <strong>of</strong> new and emerging hardware,s<strong>of</strong>tware and communication technologies, products, methods and techniques.2. Evaluates likely relevance <strong>of</strong> these for the organisation. Provides regular briefingsto staff and management.3. Works with the CISO to formulate the organisation’s information security budget.4. Interprets and/or approves security requirements as they relate to the capabilities<strong>of</strong> new information technologies, taking into account organisational policies andgovernment guidelines and legislation.Applies Technical Pr<strong>of</strong>iciency1. Evaluates and approves development efforts to ensure that baseline security safeguards areappropriately installed.2. Provides for restoration <strong>of</strong> information systems by ensuring that protection, detection, andreaction capabilities are incorporated.3. Recommends and schedules information security related repairs within the organisation’sinfrastructure and undertakes more complex repairs.4. Validates the planning and scheduling <strong>of</strong> the installation <strong>of</strong> new or modified hardware, operatingsystems, and s<strong>of</strong>tware applications ensuring integration with information security requirementsfor the infrastructure.4. Provides general and specific advice, and authorises the issue <strong>of</strong> formal reports tomanagement on the effectiveness and efficiency <strong>of</strong> control mechanisms.5. Reviews or develops effective vulnerability countermeasures6. Reviews the report <strong>of</strong>, or participates in, an information security risk assessment or review.7. Oversees the development <strong>of</strong> the audit planning process.8. Reports to senior managers on technical aspects <strong>of</strong> information security management, andcompliance with and enforcement <strong>of</strong> policies across the agency.5. Ensures that protection and detection capabilities are acquired or developed using anengineering approach and are consistent with the organisation’s information technologysecurity architecture.6. Identifies security program implications <strong>of</strong> new technologies or technology upgrades.Produced for AGIMO by Workplace Research Associates Pty Ltd 2010 Page 18