Cyber Security Capability Framework & Mapping of ISM Roles - agimo
Cyber Security Capability Framework & Mapping of ISM Roles - agimo
Cyber Security Capability Framework & Mapping of ISM Roles - agimo
Create successful ePaper yourself
Turn your PDF publications into a flip-book with our unique Google optimized e-Paper software.
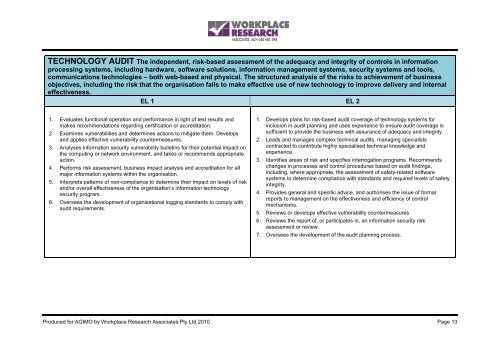
TECHNOLOGY AUDIT The independent, risk-based assessment <strong>of</strong> the adequacy and integrity <strong>of</strong> controls in informationprocessing systems, including hardware, s<strong>of</strong>tware solutions, information management systems, security systems and tools,communications technologies – both web-based and physical. The structured analysis <strong>of</strong> the risks to achievement <strong>of</strong> businessobjectives, including the risk that the organisation fails to make effective use <strong>of</strong> new technology to improve delivery and internaleffectiveness.EL 1 EL 21. Evaluates functional operation and performance in light <strong>of</strong> test results andmakes recommendations regarding certification or accreditation.2. Examines vulnerabilities and determines actions to mitigate them. Developsand applies effective vulnerability countermeasures.3. Analyses information security vulnerability bulletins for their potential impact onthe computing or network environment, and takes or recommends appropriateaction.4. Performs risk assessment, business impact analysis and accreditation for allmajor information systems within the organisation.5. Interprets patterns <strong>of</strong> non-compliance to determine their impact on levels <strong>of</strong> riskand/or overall effectiveness <strong>of</strong> the organisation’s information technologysecurity program.6. Oversees the development <strong>of</strong> organisational logging standards to comply withaudit requirements.1. Develops plans for risk-based audit coverage <strong>of</strong> technology systems forinclusion in audit planning and uses experience to ensure audit coverage issufficient to provide the business with assurance <strong>of</strong> adequacy and integrity.2. Leads and manages complex technical audits, managing specialistscontracted to contribute highly specialised technical knowledge andexperience.3. Identifies areas <strong>of</strong> risk and specifies interrogation programs. Recommendschanges in processes and control procedures based on audit findings,including, where appropriate, the assessment <strong>of</strong> safety-related s<strong>of</strong>twaresystems to determine compliance with standards and required levels <strong>of</strong> safetyintegrity.4. Provides general and specific advice, and authorises the issue <strong>of</strong> formalreports to management on the effectiveness and efficiency <strong>of</strong> controlmechanisms.5. Reviews or develops effective vulnerability countermeasures6. Reviews the report <strong>of</strong>, or participates in, an information security riskassessment or review.7. Oversees the development <strong>of</strong> the audit planning process.Produced for AGIMO by Workplace Research Associates Pty Ltd 2010 Page 13